Windows for Reverse Engineers (+ Rootkit Basics) T-110.6220 Reverse Engineering Malware Course Spring 2015 Windows Architecture
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Exploring the X64
Exploring the x64 Junichi Murakami Executive Officer, Director of Research Fourteenforty Research Institute, Inc. Who am I? • Junichi Murakami – @Fourteenforty Research Institute, Inc. – Both Windows and Linux kernel development – Reversing malware and P2P software, etc. – Speaker at: • Black Hat 2008 US and Japan, AVAR 2009, RSA Conference(2009-) – Instructor at Security & Programming Camp(2006-) 2 Environment • Windows 7 x64 Edition • Visual Studio 2008 • Windbg • IDA Pro Advanced – STD doesn’t support x64, an offering is needed! 4 Agenda • Windows x64 • ABI(Application Binary Interface) • API Hooking • Code Injection 5 Windows x64 • Native x64 and WoW64 • Virtual Address Space – 2^64 = 16 Exa Byte ( Exa: 10^18) – but, limited to 16TB by Microsoft • File/Registry reflection • New 64-bit APIs – IsWow64Process, GetNativeSystemInfo, etc. 6 ABI • Binary Format • Register • Calling Convention • Exception Handling • Systemcall(x64, WoW64) 11 Binary Format(Cont.) • Some fields were extended to 64-bits – IMAGE_NT_HEADERS.IMAGE_OPTIONAL_HEADER • ImageBase • SizeOfStackReserve • SizeOfStackCommit • SizeOfHeapReserve • SizeOfHeapCommit 13 Calling Convention • first 4 parameters are passed by RCX, RDX, R8, R9 – 5th and later are passed on the stack • caller allocates register home space on the stack • RAX is used for return values • leaf / non-leaf function – leaf function: never use stack – PE32+ contains non-leaf function’s information in its EXCEPTION DIRECTORY • Register’s volatility – volatile: RAX, RCX, RDX, R8-R11 15 Exception Handling • -

Through the Looking Glass: Webcam Interception and Protection in Kernel
VIRUS BULLETIN www.virusbulletin.com Covering the global threat landscape THROUGH THE LOOKING GLASS: and WIA (Windows Image Acquisition), which provides a WEBCAM INTERCEPTION AND still image acquisition API. PROTECTION IN KERNEL MODE ATTACK VECTORS Ronen Slavin & Michael Maltsev Reason Software, USA Let’s pretend for a moment that we’re the bad guys. We have gained control of a victim’s computer and we can run any code on it. We would like to use his camera to get a photo or a video to use for our nefarious purposes. What are our INTRODUCTION options? When we talk about digital privacy, the computer’s webcam The simplest option is just to use one of the user-mode APIs is one of the most relevant components. We all have a tiny mentioned previously. By default, Windows allows every fear that someone might be looking through our computer’s app to access the computer’s camera, with the exception of camera, spying on us and watching our every move [1]. And Store apps on Windows 10. The downside for the attackers is while some of us think this scenario is restricted to the realm that camera access will turn on the indicator LED, giving the of movies, the reality is that malware authors and threat victim an indication that somebody is watching him. actors don’t shy away from incorporating such capabilities A sneakier method is to spy on the victim when he turns on into their malware arsenals [2]. the camera himself. Patrick Wardle described a technique Camera manufacturers protect their customers by incorporating like this for Mac [8], but there’s no reason the principle into their devices an indicator LED that illuminates when can’t be applied to Windows, albeit with a slightly different the camera is in use. -

Operating System Boot from Fully Encrypted Device
Masaryk University Faculty of Informatics Operating system boot from fully encrypted device Bachelor’s Thesis Daniel Chromik Brno, Fall 2016 Replace this page with a copy of the official signed thesis assignment and the copy of the Statement of an Author. Declaration Hereby I declare that this paper is my original authorial work, which I have worked out by my own. All sources, references and literature used or excerpted during elaboration of this work are properly cited and listed in complete reference to the due source. Daniel Chromik Advisor: ing. Milan Brož i Acknowledgement I would like to thank my advisor, Ing. Milan Brož, for his guidance and his patience of a saint. Another round of thanks I would like to send towards my family and friends for their support. ii Abstract The goal of this work is description of existing solutions for boot- ing Linux and Windows from fully encrypted devices with Secure Boot. Before that, though, early boot process and bootloaders are de- scribed. A simple Linux distribution is then set up to boot from a fully encrypted device. And lastly, existing Windows encryption solutions are described. iii Keywords boot process, Linux, Windows, disk encryption, GRUB 2, LUKS iv Contents 1 Introduction ............................1 1.1 Thesis goals ..........................1 1.2 Thesis structure ........................2 2 Boot Process Description ....................3 2.1 Early Boot Process ......................3 2.2 Firmware interfaces ......................4 2.2.1 BIOS – Basic Input/Output System . .4 2.2.2 UEFI – Unified Extended Firmware Interface .5 2.3 Partitioning tables ......................5 2.3.1 MBR – Master Boot Record . -

Minimum Hardware and Operating System
Hardware and OS Specifications File Stream Document Management Software – System Requirements for v4.5 NB: please read through carefully, as it contains 4 separate specifications for a Workstation PC, a Web PC, a Server and a Web Server. Further notes are at the foot of this document. If you are in any doubt as to which specification is applicable, please contact our Document Management Technical Support team – we will be pleased to help. www.filestreamsystems.co.uk T Support +44 (0) 118 989 3771 E Support [email protected] For an in-depth list of all our features and specifications, please visit: http://www.filestreamsystems.co.uk/document-management-specification.htm Workstation PC Processor (CPU) ⁴ Supported AMD/Intel x86 (32bit) or x64 (64bit) Compatible Minimum Intel Pentium IV single core 1.0 GHz Recommended Intel Core 2 Duo E8400 3.0 GHz or better Operating System ⁴ Supported Windows 8, Windows 8 Pro, Windows 8 Enterprise (32bit, 64bit) Windows 10 (32bit, 64bit) Memory (RAM) ⁵ Minimum 2.0 GB Recommended 4.0 GB Storage Space (Disk) Minimum 50 GB Recommended 100 GB Disk Format NTFS Format Recommended Graphics Card Minimum 128 MB DirectX 9 Compatible Recommended 128 MB DirectX 9 Compatible Display Minimum 1024 x 768 16bit colour Recommended 1280 x 1024 32bit colour Widescreen Format Yes (minimum vertical resolution 800) Dual Monitor Yes Font Settings Only 96 DPI font settings are supported Explorer Internet Minimum Microsoft Internet Explorer 11 Network (LAN) Minimum 100 MB Ethernet (not required on standalone PC) Recommended -

Geekos Overview
CMSC 412 GeekOS overview GeekOS Overview A. Udaya Shankar [email protected] Jeffrey K. Hollingsworth [email protected] 2/12/2014 Abstract This document gives an overview of the GeekOS distribution (for 412- Spring 2014) and related background on QEMU and x86. It describes some operations in GeekOS in more detail, in particular, initialization, low-level interrupt handling and context switching, thread creation, and user program spawning. Contents 1. Introduction ..................................................................................................................................................................... 2 2. Qemu ............................................................................................................................................................................... 3 3. Intel x86 real mode .......................................................................................................................................................... 4 4. Intel x86 protected mode ................................................................................................................................................. 5 5. Booting and kernel initialization ...................................................................................................................................... 8 6. Context switching .......................................................................................................................................................... 11 6.1. Context state ............................................................................................................................................................. -

SOS Internals
Understanding a Simple Operating System SOS is a Simple Operating System designed for the 32-bit x86 architecture. Its purpose is to understand basic concepts of operating system design. These notes are meant to help you recall the class discussions. Chapter 1 : Starting Up SOS 3 Registers in the IA-32 x86 Architecture BIOS (Basic Input/Ouput System) Routines Real Mode Addressing Organization of SOS on Disk and Memory Master Boot Record SOS Startup A20 Line 32-bit Protected Mode Addressing Privilege Level Global Descriptor Table (GDT) More on Privilege Levels The GDT Setup Enabling Protected Mode Calling main() Chapter 2 : SOS Initializations 10 In main() Disk Initialization Display Initialization Setting Up Interrupt Handlers Interrupt Descriptor Table (IDT) A Default Interrupt Handler Load IDT The Programmable Interrupt Controller (PIC) The Keyboard Interrupt Handler Starting the Console Putting It All Together Chapter 3: SOS1 – Single-tasking SOS 16 Running User Programs GDT Entries Default Exception Handler User Programs Executable Format System Calls Creating User Programs The run Command Understanding a Simple Operating System The DUMB Memory Manager Program Address Space Process Control Block Switching to a User Program Kernel-Mode Stack Chapter 4 : SOS2 – Multi-tasking SOS 24 Running Multiple User Programs NAÏVE Memory Manager Programmable Interval Timer (PIT) Process States Timer Interrupt Handler Sleep System Call The run Command Process Queue The Scheduler The Complete Picture ps Command Chapter 5 : SOS3 – Paging in SOS 31 -
Assignment No. 6 Aim: Write X86/64 ALP To
Assignment No. 6 Att Perm Oral Total Sign (2) (5) (3) (10) Aim: Write X86/64 ALP to switch from real mode to protected mode and display the values of GDTR, LDTR, IDTR, TR and MSW Registers. 6.1 Theory: Real Mode: Real mode, also called real address mode, is an operating mode of all x86-compatible CPUs. Real mode is characterized by a 20-bit segmented memory address space (giving exactly 1 MiB of addressable memory) and unlimited direct software access to all addressable memory, I/O addresses and peripheral hardware. Real mode provides no support for memory protection, multitasking, or code privilege levels. Protected Mode: In computing, protected mode, also called protected virtual address mode is an operational mode of x86-compatible central processing units (CPUs). It allows system software to use features such as virtual memory, paging and safe multi-tasking designed to increase an operating system's control over application software. When a processor that supports x86 protected mode is powered on, it begins executing instructions in real mode, in order to maintain backward compatibility with earlier x86 processors. Protected mode may only be entered after the system software sets up several descriptor tables and enables the Protection Enable (PE) bit in the control register 0 (CR0). Control Register : Global Descriptor Table Register This register holds the 32-bit base address and 16-bit segment limit for the global descriptor table (GDT). When a reference is made to data in memory, a segment selector is used to find a segment descriptor in the GDT or LDT. -

Server Support Interview Questions and Answers Guide
Server Support Interview Questions And Answers Guide. Global Guideline. https://www.globalguideline.com/ Server Support Interview Questions And Answers Global Guideline . COM Server Support Job Interview Preparation Guide. Question # 1 Tell me where are cluster logs stored? Answer:- Please share your answers. Read More Answers. Question # 2 What are the Logical / Physical Structures of the AD Environment? Answer:- Active Directory Logical components are Forests, Trees, Domains, OUs and Objects. Active Directory Physical components are Domain Controllers, Sites and subnets. Read More Answers. Question # 3 What applications or services use AD application partitions? Name a couple? Answer:- Application partition contains the information of application data and other data related to application as well. But it does not contain any data related AD object such as USER, COMPUTER and GROUP. The saved data will be replicated to some of the particular DC not to all the DCs. Read More Answers. Question # 4 What are the types of hard disks used in servers? Answer:- Mostly we use scsi hardrive in server due few reason to it, high scalability & flexibility in raid array, faster from other type of hdd interface like-sata,ata,ide also it reliable & compatible with older scsi devices Read More Answers. Question # 5 What are some of the command-line tools available for managing a Windows 2003 Server/Active Directory environment? Answer:- Command Line Tools 1) GPupdate 2) Where 3) SystemInfo 4) CSVDE 5) LDIFDE 6) CMDCONS 7) Ipconfig 8) RoboCopy 9) CMDHere 10) PathPing Read More Answers. Question # 6 What if a FSMO server role fails? Answer:- FSMO roles are important role in server . -

Programming Model Intel Itanium 64
11/11/2003 64-bit computing AMD Opteron 64 Application of Win32 Executable File Legacy 64 bit platforms Inbuilt 128-bit bus DDR memory controller with memory bandwidth speed up to 5.3GB/s. Infectors on Intel Itanium and AMD Benefits of 64-bit processors Opteron Based Win64 Systems Use of hyper transport protocol, “glueless” architecture. Oleg Petrovsky and Shali Hsieh Increased integer dynamic range Computer Associates International Inc. Available in up to 8 way configuration with the clock speeds 1 Computer Associates Plaza, Islandia, NY 11749, Much larger addressable memory space of 1.4 GHz, 1.6 GHz and 1.8 GHz . USA Benefits to database, scientific and cryptography Reuses already familiar 32-bit x86 instruction set and applications extends it to support 64-bit operands, registers and memory pointers. AMD64 Programming Model AMD64: Programming model Intel Itanium 64 X86 32-64 64 bit Itanium line of processors is being developed by Intel XMM8 X86 80-Bit Extends general use registers to 64-bit, adds additional eight 64-Bit X87 general purpose 64-bit registers. Itanium - 800 MHz, no on die L3 cache, Itanium 2 - 1GHz, RAX EAX AX 3MB L3 on die, Itanium 2003 (Madison) - 1.5 GHz, 6MB L3 on die cache, 410M transistors, largest integration on a RBX Reuses x86 instruction set. single silicon crystal today. XMM15 RCX Runs 32-bit code without emulation or translation to a native Itanium line of processors utilizes more efficient and robust XMM0 than legacy x86 instruction set architecture F instruction set. R8 L A Itanium has to use x86-to-IA-64 decoder a specifically Minimizes learning curve. -
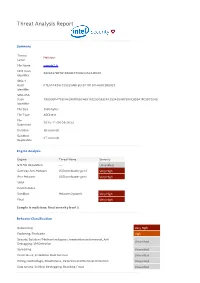
Sample2.Js Malware Summary
Threat Analysis Report Summary Threat Malicious Level File Name sample2.js MD5 Hash 580E637B97B16698CC750B445223D5C0 Identifier SHA-1 Hash 07E507426F72522DABFECF91181D7F64DC3B8D23 Identifier SHA-256 Hash 790999F47B2FA4396FF6B0A6916E295D832A12B3495A87590C859A1FE9D73245 Identifier File Size 3586 bytes File Type ASCII text File 2015-11-06 09:26:23 Submitted Duration 38 seconds Sandbox 27 seconds Replication Engine Analysis Engine Threat Name Severity GTI File Reputation --- Unverified Gateway Anti-Malware JS/Downloader.gen.f Very High Anti-Malware JS/Downloader.gen.f Very High YARA Custom Rules Sandbox Malware.Dynamic Very High Final Very High Sample is malicious: f inal severit y level 5 Behavior Classif icat ion Networking Very High Exploiting, Shellcode High Security Solution / Mechanism bypass, termination and removal, Anti Unverified Debugging, VM Detection Spreading Unverified Persistence, Installation Boot Survival Unverified Hiding, Camouflage, Stealthiness, Detection and Removal Protection Unverified Data spying, Sniffing, Keylogging, Ebanking Fraud Unverified Dynamic Analysis Action Severity Malware behavior: networking activities from non-executable file Very High ATTENTION: connection made to a malicious website (see Web/URL Very High reputation for details) Detected suspicious Java Script content High Downloaded data from a webserver Low Modified INTERNET_OPTION_CONNECT_RETRIES: number of times that Low WinInet attempts to resolve and connect to a host Connected to a specific service provider Low Cracks a URL into its component -

How Will You Troubleshoot the Issue? What Are the Steps to Followed? A
1. A user in a corporate network contacts service desk saying he/she has lost network connectivity: How will you troubleshoot the issue? What are the steps to followed? A. First I will check the network cable is plugged in or not. Then check the network connections and the ip address is assigned or not. Then check connecting to website or not. IP conflict. 2. A User calls in and complains that her computer and network is running very slow. How would go about troubleshooting it? A. 3. How would you create an email account for a user already in AD? A. Open Microsoft Outlook if you are using office 2000, and click on "Tools" tab. Go to "Email Accounts". There you can find two option like Email and Directory. Click on "Add a new Account" and click next. If you are using Exchange Server then click over there, this depends on that particular Organization. According to the their setup you have to choose. And if you are using POP3 server then next popup will come along with your name, email address POP3 and SMTP IP address, Password etc. and after that click on Next and finish it..... 4. A PC did not receive an update from SMS. What steps would we take to resolve this? A. If SMS not updated in client system. 1. Need to check system getting IPaddress or not. 2. Need to check system in domain or not 3.Ensure that windows firewall should be off. 5. How do you set the IP address by using the command prompt A. -

Bringing Virtualization to the X86 Architecture with the Original Vmware Workstation
12 Bringing Virtualization to the x86 Architecture with the Original VMware Workstation EDOUARD BUGNION, Stanford University SCOTT DEVINE, VMware Inc. MENDEL ROSENBLUM, Stanford University JEREMY SUGERMAN, Talaria Technologies, Inc. EDWARD Y. WANG, Cumulus Networks, Inc. This article describes the historical context, technical challenges, and main implementation techniques used by VMware Workstation to bring virtualization to the x86 architecture in 1999. Although virtual machine monitors (VMMs) had been around for decades, they were traditionally designed as part of monolithic, single-vendor architectures with explicit support for virtualization. In contrast, the x86 architecture lacked virtualization support, and the industry around it had disaggregated into an ecosystem, with different ven- dors controlling the computers, CPUs, peripherals, operating systems, and applications, none of them asking for virtualization. We chose to build our solution independently of these vendors. As a result, VMware Workstation had to deal with new challenges associated with (i) the lack of virtual- ization support in the x86 architecture, (ii) the daunting complexity of the architecture itself, (iii) the need to support a broad combination of peripherals, and (iv) the need to offer a simple user experience within existing environments. These new challenges led us to a novel combination of well-known virtualization techniques, techniques from other domains, and new techniques. VMware Workstation combined a hosted architecture with a VMM. The hosted architecture enabled a simple user experience and offered broad hardware compatibility. Rather than exposing I/O diversity to the virtual machines, VMware Workstation also relied on software emulation of I/O devices. The VMM combined a trap-and-emulate direct execution engine with a system-level dynamic binary translator to ef- ficiently virtualize the x86 architecture and support most commodity operating systems.