History Comsec Ii.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Efficiency of Tuna Purse-Seiners and Effective Effort’ « Efficacité Des Senneurs Thoniers Et Efforts Réels » (ESTHER)
SCTB15 Working Paper FTWG–5 ‘Efficiency of Tuna Purse-Seiners and Effective Effort’ « Efficacité des Senneurs Thoniers et Efforts Réels » (ESTHER) 1 Selected Annotated Bibliography Marie-Christine REALES ESTHER Project Document Officer 1 To receive the complete ESTHER ANNEXE BIBLIOGRAPHIQUE, contact Daniel Gaertner, 1 Institute of Research for Develoment (IRD - UR 109), CHMT BP 171, 34203 Séte Cedex, France PROGRAMME DE RECHERCHES N° 98/061 IRD (Institut de Recherches pour le Développement) / IEO (Instituto Español de Oceanografía) ‘Efficiency of Tuna Purse-Seiners and Effective Effort’ « Efficacité des Senneurs Thoniers et Efforts Réels » (ESTHER) ANNEXE BIBLIOGRAPHIQUE Marie-Christine REALES Documentaliste du projet ESTHER 1 SOMMAIRE INTRODUCTION……………………………………………………………………p. 4 I.Méthodologie………………………………………………………..…………….…p. 5 I.1 Etablissement d'une liste de mots-clés……………………………………...………...p. 5 I.2 Sources utilisées………………………………………………………………………p. 5 I.3 Recherche et validation des résultats…………………………………………………p. 7 I.3.1 Interrogation des bases…………………………………………………………p. 7 I.3.2 Evolution de la liste de mots-clés………………………………………………p. 7 I.3.3 Validation des références…………………………………………………...….p. 9 I.3.4 Diffusion des références……………………………………………………..…p. 9 I.4 Transfert des références sous le logiciel bibliographique PROCITE……………….p. 10 II.Quelques adresses de sites sur Internet………………………………….…p. 23 CONCLUSION………………………………………………………….…….……..p. 26 * * * Bibliographie thématique…………………………………………………………p. 3 Fishing Fleet…………………………………………………………………….…….…p. 3 Purse Seiner Technology…………………………………………………….……..……p. 7 Fisher's Behavior…………………………………………………………………….......p. 13 Fish Catch Statistics……………………………………………………………………...p. 18 Fishing Operations……………………………………………………………..………...p. 30 Tuna Behaviour………………………………………………………………..………...p. 34 Models…………………………………………………………………………………...p. 39 2 Bibliographie Thématique FISHING FLEET Abrahams, M.V. ; Healey, M.C., 1993. Some consequences of variation in vessel density : a manipulative field experiment. Fisheries Research , 15 (4) : 315-322. -

Harris Sierra II, Programmable Cryptographic
TYPE 1 PROGRAMMABLE ENCRYPTION Harris Sierra™ II Programmable Cryptographic ASIC KEY BENEFITS When embedded in radios and other voice and data communications equipment, > Legacy algorithm support the Harris Sierra II Programmable Cryptographic ASIC encrypts classified > Low power consumption information prior to transmission and storage. NSA-certified, it is the foundation > JTRS compliant for the Harris Sierra II family of products—which includes two package options for the ASIC and supporting software. > Compliant with NSA’s Crypto Modernization Program The Sierra II ASIC offers a broad range of functionality, with data rates greater than 300 Mbps, > Compact form factor legacy algorithm support, advanced programmability and low power consumption. Its software programmability provides a low-cost migration path for future upgrades to embedded communications equipment—without the logistics and cost burden normally associated with upgrading hardware. Plus, it’s totally compliant with all Joint Tactical Radio System (JTRS) and Crypto Modernization Program requirements. The Sierra II ASIC’s small size, low power requirements, and high data rates make it an ideal choice for battery-powered applications, including military radios, wireless LANs, remote sensors, guided munitions, UAVs and any other devices that require a low-power, programmable solution for encryption. Specifications for: Harris SIERRA II™ Programmable Cryptographic ASIC GENERAL BATON/MEDLEY SAVILLE/PADSTONE KEESEE/CRAYON/WALBURN Type 1 – Cryptographic GOODSPEED Algorithms* ACCORDION FIREFLY/Enhanced FIREFLY JOSEKI Decrypt High Assurance AES DES, Triple DES Type 3 – Cryptographic AES Algorithms* Digital Signature Standard (DSS) Secure Hash Algorithm (SHA) Type 4 – Cryptographic CITADEL® Algorithms* SARK/PARK (KY-57, KYV-5 and KG-84A/C OTAR) DS-101 and DS-102 Key Fill Key Management SINCGARS Mode 2/3 Fill Benign Key/Benign Fill *Other algorithms can be added later. -

Conclusions and Overall Assessment of the Bloody Sunday Inquiry Return to an Address of the Honourable the House of Commons Dated 15 June 2010 for The
Principal Conclusions and Overall Assessment of the Principal Conclusions and Overall Return to an Address of the Honourable the House of Commons dated 15 June 2010 for the Principal Conclusions and Overall Assessment of the Bloody Sunday Inquiry The Rt Hon The Lord Saville of Newdigate (Chairman) The Hon William Hoyt OC The Hon John Toohey AC Bloody Sunday Inquiry Published by TSO (The Stationery Office) and available from: The Principal Conclusions and Overall Assessment Online (Chapters 1–5 of the report) are reproduced in this volume www.tsoshop.co.uk This volume is accompanied by a DVD containing the full Mail, Telephone, Fax & E-mail TSO text of the report PO Box 29, Norwich NR3 1GN Telephone orders/General enquiries: 0870 600 5522 Order through the Parliamentary Hotline Lo-Call: 0845 7 023474 Fax orders: 0870 600 5533 E-mail: [email protected] Textphone: 0870 240 3701 The Parliamentary Bookshop 12 Bridge Street, Parliament Square, London SW1A 2JX Telephone orders/General enquiries: 020 7219 3890 Fax orders: 020 7219 3866 Email: [email protected] Internet: www.bookshop.parliament.uk TSO@Blackwell and other Accredited Agents Customers can also order publications from TSO Ireland 16 Arthur Street, Belfast BT1 4GD Telephone: 028 9023 8451 Fax: 028 9023 5401 HC30 £19.50 Return to an Address of the Honourable the House of Commons dated 15 June 2010 for the Principal Conclusions and Overall Assessment of the Bloody Sunday Inquiry The Rt Hon The Lord Saville of Newdigate (Chairman) The Hon William Hoyt OC The Hon John Toohey -

Volume I Return to an Address of the Honourable the House of Commons Dated 15 June 2010 for The
Report of the Return to an Address of the Honourable the House of Commons dated 15 June 2010 for the Report of the Bloody Sunday Inquiry The Rt Hon The Lord Saville of Newdigate (Chairman) Bloody Sunday Inquiry – Volume I Bloody Sunday Inquiry – Volume The Hon William Hoyt OC The Hon John Toohey AC Volume I Outline Table of Contents General Introduction Glossary Principal Conclusions and Overall Assessment Published by TSO (The Stationery Office) and available from: Online The Background to Bloody www.tsoshop.co.uk Mail, Telephone, Fax & E-mail Sunday TSO PO Box 29, Norwich NR3 1GN Telephone orders/General enquiries: 0870 600 5522 Order through the Parliamentary Hotline Lo-Call: 0845 7 023474 Fax orders: 0870 600 5533 E-mail: [email protected] Textphone: 0870 240 3701 The Parliamentary Bookshop 12 Bridge Street, Parliament Square, London SW1A 2JX This volume is accompanied by a DVD containing the full Telephone orders/General enquiries: 020 7219 3890 Fax orders: 020 7219 3866 text of the report Email: [email protected] Internet: www.bookshop.parliament.uk TSO@Blackwell and other Accredited Agents Customers can also order publications from £572.00 TSO Ireland 10 volumes 16 Arthur Street, Belfast BT1 4GD not sold Telephone: 028 9023 8451 Fax: 028 9023 5401 HC29-I separately Return to an Address of the Honourable the House of Commons dated 15 June 2010 for the Report of the Bloody Sunday Inquiry The Rt Hon The Lord Saville of Newdigate (Chairman) The Hon William Hoyt OC The Hon John Toohey AC Ordered by the House of Commons -

W^Ffs^Jlpâltlfmllpla^I N E, Frescos
Fundado em 1930 •• Ano XIX ¦¦ IN." 7880 A. DIÁRIO UE NOTICIAS- Tiragem da Propriedade da S. *'<>n>er» O Matutino de Maior O. R. Dantas, presidente; RI. Moreira. Capital da República leRoiirrire; Aurélio Silva, seeretmio. Dis- ASSINATURAS: Previsões ate. 2 horas de amanhã, no n TEMPO rom nebulosidade. »s- Federa!:' Tunnn nom XO.O0: Trim. Cr» ».i.IK, „.„„ Em elevaçüo. Venlns — Dr. Ano, Cri 100,00; Semestre. Crf vni>lrci. Temperatura W^ffS^JlpâltlfmllPla^i N E, frescos. Rep.B. Paulo: VY Farinello - 8. Bento, 220-3.» T. <-íBJi F,n. »E HOJE, 2 SEi;OEsTll PAUS - Cr* 0.50 Universidade Rural, ¦*'•*!'£• «.íi-- •1q1.15.2-; Penha, Rio de Janeiro, Sábado, 3 de Julho de 1918 «¦"-«••• 11 — Tel.: 42-2910 (Rede Interna) ^í^íBua^^-"*''^^"o***^--- ^r4..?jT"uo5"-.^»:i-.?i..M.,ep. Qú?«i«. Constituição, Éstralésia para enfrentar o bloqueio russo Marshall declara que os Estados Unidos, Inglaterra e APELAM PARA STÀLIN OS COMUNISTAS DA IUGOSLÁVIA combater a ati- França estão traçando planos para Quinze mil marxistas dirrçem-lhe um telegrama, solicitando que elimine as Resolveu não convocar o Congresso "falsas tude soviética em Berlim acusações" feitas pelo Cominform contra o mal. Tito e seu governo decisão do presiden- ação conjunta Oficialmente anunciada essa "amor "premier" — Declinou de revelar qualquer detalhe sobre a Protestaram ilimitado" ao russo Que- — considerada na Casa Branca acaoar com a das três potências Também ram «ue nao comparecerão*- rem que êste faça tudo ao seu alcance para o líder anunciado que » pre.lde»te - Ordens só dos russos, diz T ^v -'- (V '«• •'> - 1*1 ».fUda.n,e,,.e.. -
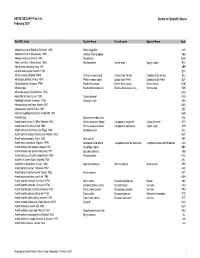
ASFIS ISSCAAP Fish List February 2007 Sorted on Scientific Name
ASFIS ISSCAAP Fish List Sorted on Scientific Name February 2007 Scientific name English Name French name Spanish Name Code Abalistes stellaris (Bloch & Schneider 1801) Starry triggerfish AJS Abbottina rivularis (Basilewsky 1855) Chinese false gudgeon ABB Ablabys binotatus (Peters 1855) Redskinfish ABW Ablennes hians (Valenciennes 1846) Flat needlefish Orphie plate Agujón sable BAF Aborichthys elongatus Hora 1921 ABE Abralia andamanika Goodrich 1898 BLK Abralia veranyi (Rüppell 1844) Verany's enope squid Encornet de Verany Enoploluria de Verany BLJ Abraliopsis pfefferi (Verany 1837) Pfeffer's enope squid Encornet de Pfeffer Enoploluria de Pfeffer BJF Abramis brama (Linnaeus 1758) Freshwater bream Brème d'eau douce Brema común FBM Abramis spp Freshwater breams nei Brèmes d'eau douce nca Bremas nep FBR Abramites eques (Steindachner 1878) ABQ Abudefduf luridus (Cuvier 1830) Canary damsel AUU Abudefduf saxatilis (Linnaeus 1758) Sergeant-major ABU Abyssobrotula galatheae Nielsen 1977 OAG Abyssocottus elochini Taliev 1955 AEZ Abythites lepidogenys (Smith & Radcliffe 1913) AHD Acanella spp Branched bamboo coral KQL Acanthacaris caeca (A. Milne Edwards 1881) Atlantic deep-sea lobster Langoustine arganelle Cigala de fondo NTK Acanthacaris tenuimana Bate 1888 Prickly deep-sea lobster Langoustine spinuleuse Cigala raspa NHI Acanthalburnus microlepis (De Filippi 1861) Blackbrow bleak AHL Acanthaphritis barbata (Okamura & Kishida 1963) NHT Acantharchus pomotis (Baird 1855) Mud sunfish AKP Acanthaxius caespitosa (Squires 1979) Deepwater mud lobster Langouste -

523696 REF ID:A523696 {U) Chapter 16 Cryptology and the Watergate
DOCID: 523696 REF ID:A523696 lOP SECRET I::JMBM {U) Chapter 16 Cryptology and the Watergate Era (U) BACKGROUND TO SCANDAL (U) The greatest political scandal in American history originated with an obscure note in the Metro seetion of the Washington Post on Sunday, June 18, 1972. In it, two ~etro . section reporters, Bob Woodward and Carl Bernstein, cove~ed what appeared to be an amateurish break-in at the Democratic National Headquarters in the Watergate Hotel in downtown Washington. (U) The Nixon administration managed to cover over the politi~l effects of the break-in until after the elections in Novem~r. But when Congress returned in January, it was ready to investigate. In February 1973, the Senate voted to establish a Select Committee, commonly referred to as the Ervin Committee after Senator Sam Ervin, Democratic senator from North Carolina, to hold hearings. At the time, no one associated with the committee knew where they would get information, since the administration was keeping a tight lip, and· the . Watergate burglars weren't•talking. But on March 23, one of the burglars, James McCord, turned state's evidence: The federal judg~, John Sirica, had been pressuring the defendants by threatening lengthy prison terms if they did not cooperate. Now McCord was cooperating, and the entire thing began to unravel. The president, concerned with get~g on with his second term. tried to shush the (U) Prealclent Nixon an4 hlalDner circle, 1973 whole thing. (U) The scandal, of course, would not shush. Instead, it mushroomed, swallowing first Nixon's White House staff', then much of his cabinet, and imally the president himself. -

The Military's Role in Counterterrorism
The Military’s Role in Counterterrorism: Examples and Implications for Liberal Democracies Geraint Hug etortThe LPapers The Military’s Role in Counterterrorism: Examples and Implications for Liberal Democracies Geraint Hughes Visit our website for other free publication downloads http://www.StrategicStudiesInstitute.army.mil/ To rate this publication click here. hes Strategic Studies Institute U.S. Army War College, Carlisle, PA The Letort Papers In the early 18th century, James Letort, an explorer and fur trader, was instrumental in opening up the Cumberland Valley to settlement. By 1752, there was a garrison on Letort Creek at what is today Carlisle Barracks, Pennsylvania. In those days, Carlisle Barracks lay at the western edge of the American colonies. It was a bastion for the protection of settlers and a departure point for further exploration. Today, as was the case over two centuries ago, Carlisle Barracks, as the home of the U.S. Army War College, is a place of transition and transformation. In the same spirit of bold curiosity that compelled the men and women who, like Letort, settled the American West, the Strategic Studies Institute (SSI) presents The Letort Papers. This series allows SSI to publish papers, retrospectives, speeches, or essays of interest to the defense academic community which may not correspond with our mainstream policy-oriented publications. If you think you may have a subject amenable to publication in our Letort Paper series, or if you wish to comment on a particular paper, please contact Dr. Antulio J. Echevarria II, Director of Research, U.S. Army War College, Strategic Studies Institute, 632 Wright Ave, Carlisle, PA 17013-5046. -

Central, Istrouma Grads Crowd NBR Reunion BATON ROUGE — More Than School Closed Two Years Ago Ovation
General Excellence Louisiana Press Association CENTRALCENTRAL CITYCITY National Newspaper Assn. High-Ranking Ex-City Official Issued Citation For Incident at Central City Hall Page 15 ® & The Leader NEWSNEWSJuly 2016 • Vol. 19, No. 7 • 16 Pages • Circulation 14,000 • 30,000 online • www.centralcitynews.us • 225-261-5055 City of Central • Founded July 11, 2005 City’s 11th AnniversaryCentral Family Fun Celebration At 6 p.m. Saturday at Stadium CENTRAL — Citizens of the City of Central and their friends are invited to help celebrate the 11th Anniver- sary of the founding of the City of Central this Satur- day at 6 p.m. at Wildcat Sta- WILLIE dium. Mayor Jr. Shelton is urg- ing families to come and AMITE COMITE enjoy themselves. He said the fireworks display will be the biggest in Central history. Participants are encour- aged to bring lawn chairs and blankets so they can sit on the football field. Stadi- um seating is also available. Congratulations, The program includes the Central! Kenny Fife and Bac Trac Band beginning at 6 p.m., You’re 11 Years Old! the Molly Ringwalls at 7:30, Birthday Bash and the fireworks at 9:30. 6 p.m. ANOTHER FOUR YEARS — Doug Welborn of Central was sworn in for another four-year term as A barbecue food truck East Baton Rouge Parish Clerk of Court on July 1 in ceremonies at the clerk’s office. Here he enjoys a will sell food, and the Kit- Saturday, July 16 laugh with former LSU football great and former head coach Jerry Stovall and Jodi Stovall. -

Initial List Alphabetically Listed by Initials 6.11.87
INITIAL LIST ALPHABETICALLY LISTED BY INITIALS INIT. NAHF SALESORG. flEEICf AA Andreassen, Asb]0rn HO S-1 1206 AAA Aas, Arild N B0 4114 AAAN Aanerud, Arne HO S-1 1202 AAB Borge, Aase HO S-2 1205 AABE Eker, Ase Briskodden N Asker 4419 AABK Kolstad, Ase Br0rby HO S-2 1101 AAF Foss, Ashild (30%) HO G-4 2303 AAG Gull, Aaron UK Newbury 2201 AAGR Grimseth, Ashild HO 5-1 1206 AAGU Gulbrandsen, Age HO M- 5 2215 AAH Hauger, Ase R. HO M-2 4406 AAJN Nordsteien, Asmund Johansen N Steinkjer 4109 AAL Albers, Anton D Bad Homb 3380 AALA Larsen, Age CN Z-4 6404 AAM Milne, Alec UK Newbury 3199 AAML Lunde, Ase M. HO Tr'heim 6127 AAN Andersen, Andreas HO R-5 2214 AANO Nord, Aage HO S-1 2104 AAO 0rstad, Aage-John N Z-5 4110 AAST Steen, Aase Marie HO 5- 1 1903 ABE Bergersen, Arne N Y-5 4103 ABF Frigaard, Anne Beate N Z-5 4110 ABGI Gingell, Andrew UK Newbury 1301 ABI Iversen, Anne Brit N Y-5 3123 ABO Olstad, Aud Bj0rhus N Y-6 3214 ABP Pughe, Arthur Brian (Brian) UK Manchester 3104 ABR Brunstad, Anne L. HO B-4 2205 ABS Solstad, Anna Brith N Troms0 4104 ABW Walestrand, Agnes Bergene{75% )H0 S-2 1910 ABWI Wiger, Anne Beth (50%) HO S - 3 6230 AC Clay, Anthony N Z-5 3201 ACDR Droste, Achim D Bad Homb. 5500 ACH Cheyne, Andrew UK Ney/bury AC I Ingvoldsen, Anita C. HO S-2 1910 ACL Loehr, Achim D Stuttgart 3370 ACLI Lindvald, Anna-Carin S Uppl.Vasby 4503 ACO Cokluk, Adnan (75%) HO K-3 6230 ACRC Chantler, Arthur (Chris) UK Newbury 3113 ACWH Whittle, Andrew C. -

David Sheldon Boone Charging Him with Selling the Security Apparatus
CHAPTER 2 INTRODUCTION In the early 1990s, the new Russian in the Leningrad KGB.1 Putin also quietly replaced counterintelligence service embarked on a mission fourteen presidential representatives in the regions to reclaim the former KGB’s internal security with former security offi cers. power, which had been diminished with the fall of the Soviet Union in 1991. A spate of press FSB director Patrushev said that, in 1999, his service articles in early 1996 by spokesmen for the Federal stopped the activities of 65 foreign individual Security Service (FSB) boasted the service’s role in offi cers and prevented 30 Russian citizens from protecting the state from foreign subversion. FSB passing secrets to foreign intelligence services. In offi cers noted that the service has the responsibility 1998, the FSB foiled the activities of 11 intelligence to monitor foreign astronauts at “Star City” and to offi cers and caught 19 Russian citizens attempting to prevent the emigration of Russian scientists. The sell classifi ed information to foreign secret services. FSB has also bragged about the arrest of Israeli, And in 1996, then-FSB chief Nikolai Kovalyov said Turkish, and North Korean spies and the expulsion the FSB had exposed 400 employees of foreign of a British businessman and an Israeli diplomat. intelligence services and 39 Russians working for The government moves against ecologists further them during the period 1994-96. revealed a resurgence of FSB internal power. The Sutyagin case follows the sentencing in Although there continues to be mutually benefi cial December 2000 of retired US Navy offi cer Edmund cooperation between Washington and Moscow, Pope to 20 years for spying. -

Conference Reports ELECTRONIC SUPPLEMENT
DECEMBER 2012 vOL. 37, NO. 6 Conference Reports ELECTRONIC SUPPLEMENT 21st USENIX Security Symposium (USENIX and that they also knew what the US was doing (capabilities) Security ’12) through the use of spies in the US and their interception of our ciphers (access). After considering all of these differ- Bellevue, WA August 8–10, 2012 ent criteria, cryptographers could then attempt to provide information assurance in the face of this particular enemy. Opening Remarks Again focusing on communications, they examined the Summarized by Rik Farrow ([email protected]) security of the SAVILLE cipher and its usage in the VINSON Program Chair Tadayoshi Kohno (University of Washing- hand-held radio. Additionally, they really had time to do it ton) opened the conference by telling us that there were 222 right: the SAVILLE cipher was developed in the 1950s, evalu- papers submitted and 42 accepted. By replacing four invited ated in the 1960s, and then finally implemented in VINSON talks sessions with paper presentations, more papers could and deployed in 1976; this meant that they could look closely be accepted than in the past. at both the algorithm and its implementation to try to find When the conference began, there were 484 attendees; 84 potential attacks. students received travel grants using money provided by the In modern times, the field has once again changed dramati- National Science Foundation, with Google and Microsoft cally. One of the main catalysts for these changes was the being the next largest sponsors. introduction of the Data Encryption Standard (DES), which Best Paper awards went to “Mining Your Ps and Qs: Detec- was created through a competition held by NIST.