Microworld Releases Mailscan 5.0
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

INSECURE-Mag-9.Pdf
Another year is almost over and a plethora of information security problems are behind us. To let 2006 go out in style, we bring you a feature packed issue of (IN)SECURE. As the feature interview for this issue we had the pleasure of talking with Kurt Sauer, the CSO at Skype, one of the most well-known companies in the digital world. We’ll be back next year with many new ideas in the pipeline. Stay tuned for coverage from a few conferences including the RSA Conference in San Francisco and the Black Hat Briefings &Training in Amsterdam. If you’re attending, be sure to drop me an e-mail and we’ll grab a drink. We wish you a safe 2007! Mirko Zorz Chief Editor Visit the magazine website at www.insecuremag.com (IN)SECURE Magazine contacts Feedback and contributions: Mirko Zorz, Chief Editor - [email protected] Marketing: Berislav Kucan, Director of Marketing - [email protected] Distribution (IN)SECURE Magazine can be freely distributed in the form of the original, non modified PDF document. Distribution of modified versions of (IN)SECURE Magazine content is prohibited without the explicit permission from the editor. For reprinting information please send an email to [email protected] or send a fax to 1-866-420-2598. Copyright HNS Consulting Ltd. 2006. www.insecuremag.com New enterprise single sign-on authentication software DigitalPersona announced the latest version of its award-winning enterprise product, DigitalPersona Pro 4.0. The new and improved software delivers a complete, accurate and trusted fingerprint Enterprise Single Sign-On (ESSO) solution with more secure authentication, improved manageability and the broadest support available for the world’s leading biometrically-enabled notebooks including models from Lenovo, HP, Dell, and Toshiba. -

HNS - Dnschanger Redirects Users to Fake Bank Websites
HNS - DNSChanger redirects users to fake bank websites Welcome to a new version of Help Net Security. Much has improved and more is on the way. Subscribe to our RSS feeds and stay updated! Off The Wire Latest Articles Windows Linux Security Reviews Vendor Advisories Webcasts Subscribe Current Mac OS X World Interviews Vulnerability Database Conferences Issue Archive Pocket PC Virus Book Chapters Center Federated identity: scenarios, architecture, and implementation Consultant breached FBI's computers Researcher vows to publish a browser bug a day for July McAfee sees 400,000 virus definitions by 2008 The hidden dangers of instant messaging Skype steps up security spin A day in the life of a security professional Double Password security manager announced ICICI Bank phishing scam targets customers in india Survey reveals end point security loophole 49% fail to lock down devices DNSChanger redirects users to fake bank websites The largest network security event in Asia Limiting Vulnerability Exposure Through Effective Patch Management Securing Wireless, Remote and Mobile Computing - Quick Fixes The Ten Most Critical Wireless and Mobile Security Vulnerabilities Striking the Balance Between Storage Security and Availability Security for Websites - Breaking Sessions to Hack Into a Machine Chronicle of malware detected in the first half of 2006 Sophos: because of malware home users should switch to Macs New worm holds no genuine http://www.net-security.org/secworld.php?id=4049 (1 of 3) [7/6/2006 4:18:20 PM] HNS - DNSChanger redirects users to -

Mobile Device Survery
Mobile Device Surveyrvey DRAFT NIST Interagency Report June 2002 Tom Karygiannis Wayne Jansen Vlad Korolev Serban Gavrila 1 Table of Contents 1. Introduction ........................................................................................................... 1 2. PDA Platform Families ......................................................................................... 1 2.1 Palm PDA........................................................................................................ 2 2.2 Pocket PC........................................................................................................ 3 2.3 Linux PDA ...................................................................................................... 4 3. Development Tools ................................................................................................ 8 3.1 Palm OS Development Tools........................................................................... 8 3.2 Pocket PC Development Tools......................................................................... 8 3.3 Linux PDA Development Tools....................................................................... 9 4. Commercial Security Solutions........................................................................... 11 4.1 Palm OS Security Mechanisms ...................................................................... 11 4.2 Pocket PC Security Mechanisms.................................................................... 15 4.3 Linux PDA Security Mechanisms ................................................................. -

Internet Technology and Web Programming
INTERNET TECHNOLOGY AND WEB PROGRAMMING 1 F.C Ledesma Avenue, San Carlos City, Negros Occidental Tel. #: (034) 312-6189/(034) 729-4327 CONTENTS LESSON I: Introduction to Networking · Networking concepts and Technology (LANs and WANs) . · Serial Networking (SLIP, PPP) . · Internet Protocol (IP) and Domain Name System (DNS) . · What is the Internet . LESSON II: Internet Access Hardware and Media · HARDWARE: Modems, Terminal Adapters, Routers . · MEDIA: PTSN, ISDN, Kilostream . LESSON III: Internet Services · Electronic Mail; Newsgroups . · File Transfer Protocol (FTP) and Hypertext Transfer Protocol (HTTP) . · Internet databases: WAIS, Archie, gopher, WWW search databases . LESSON IV: Using E-Mail and other Clients · Electronics Mail . · Other Internet Clients . · FTP . · Newsgroups . · Telnet . LESSON V: Media & Active Content · Object & Active Content . · Types of Browser Plug-ins . 2 F.C Ledesma Avenue, San Carlos City, Negros Occidental Tel. #: (034) 312-6189/(034) 729-4327 · Additional Media File Formats . · Images File Formats . LESSON VI: Internetworking Servers · Server Implementation . · Content Servers . · Performance Servers . · Database Servers . · Mirrored Servers . · Popular Server Products . LESSON VII: Web Servers and Databases · Databases . · Introduction to Database Gateways for Web Servers . · Common Gateway Interface (CGI) . · Server Application Programming Interfaces (SAPIs) . · JavaScript . · ASP . · PHP . · HTML . · Java & Java Service . · JSP . · ColdFusion . · Database Connectivity 3 F.C Ledesma Avenue, San Carlos City, Negros Occidental Tel. #: (034) 312-6189/(034) 729-4327 · ODBC . · JDBC . LESSON VIII: Internet Security · What is Security? . · The cracker Process . · Types of Attacks . · Defending Your Networks . · Firewalls . · Defending Your Computer . · Defending Your Transmitted Data . Lesson I: (Introduction to Networking) 1. Network concepts and Technology (LANs and WANs) 4 F.C Ledesma Avenue, San Carlos City, Negros Occidental Tel. -

A Worldwide Survey of Encryption Products
A Worldwide Survey of Encryption Products February 11, 2016 Version 1.0 Bruce Schneier Berkman Center for Internet & Society Harvard University [email protected] Kathleen Seidel Independent Researcher [email protected] Saranya Vijayakumar Harvard College [email protected] Introduction Data security is a worldwide problem, and there is a wide world of encryption solutions available to help solve this problem. Most of these products are developed and sold by for-profit entities, although some are created as free open-source projects. They are available, either for sale or free download, all over the world. In 1999, a group of researchers from George Washington University attempted to survey the worldwide market for encryption products [HB+99]. The impetus for their survey was the ongoing debate about US encryption export controls. By collecting information about 805 hardware and software encryption products from 35 countries outside the US, the researchers showed that restricting the export of encryption products did nothing to reduce their availability around the world, while at the same time putting US companies at a competitive disadvantage in the information security market. Seventeen years later, we have tried to replicate this survey. • • • • • • • • • A Worldwide Survey of Encryption Products • Feb 2016, v 1.0 1 Findings We collected information on as many encryption products as we could find anywhere in the world. This is a summary of our findings: • We have identified865 hardware or software products incorporating encryption from 55 different coun- tries. This includes 546 encryption products from outside the US, representing two-thirds of the total. Table 1 summarizes the number of products from each country. -

Team-Fly® Wireless Security Essentials Defending Mobile Systems from Data Piracy
Y L F M A E T Team-Fly® Wireless Security Essentials Defending Mobile Systems from Data Piracy Russell Dean Vines Wiley Publishing, Inc. Publisher: Robert Ipsen Editor: Margaret Eldridge Assistant Editor: Adaobi Obi Managing Editor: Micheline Frederick New Media Editor: Brian Snapp Text Design & Composition: Wiley Composition Services Designations used by companies to distinguish their products are often claimed as trade- marks. In all instances where Wiley Publishing, Inc., is aware of a claim, the product names appear in initial capital or ALL CAPITAL LETTERS. Readers, however, should contact the appro- priate companies for more complete information regarding trademarks and registration. This book is printed on acid-free paper. ∞ Copyright © 2002 by Russell Dean Vines. All rights reserved. Published by Wiley Publishing, Inc., Indianapolis, Indiana Published simultaneously in Canada No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning, or otherwise, except as permitted under Section 107 or 108 of the 1976 United States Copy- right Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, Inc., 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 750-4470. Requests to the Publisher for permission should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspointe Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4447, E-mail: [email protected]. Limit of Liability/Disclaimer of Warranty: While the publisher and author have used their best efforts in preparing this book, they make no representations or warranties with respect to the accuracy or completeness of the contents of this book and specifically disclaim any implied warranties of merchantability or fitness for a particular purpose. -

Cisco Anyconnect ISE Posture Windows Support Charts for Compliance Module V3.6.11428.2
Cisco AnyConnect ISE Posture Windows Support Charts for Compliance Module v3.6.11428.2 August 2, 2017 © 2017 Cisco and/or its affiliates. All rights reserved. This document is Cisco public. Page 1 of 65 Contents Anti-Virus .................................................................................................................................................................................... 3 Anti-Spyware ............................................................................................................................................................................ 43 Patch Management................................................................................................................................................................... 59 Disk Encryption ........................................................................................................................................................................ 61 ©2017 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 2 of 65 This document lists the Windows OS anti-virus, anti-spyware, patch management, and disk encryption products that are supported by the ISE Posture Agent. The Windows compliance modules are version 3.6.11428.2. Anti-Virus Definition State Product Name Product Version Live Update Min. Compliance Module Version Check 360Safe.com 360 Antivirus 1.x yes yes 3.4.16.1 360 Antivirus 3.x yes - 3.5.5767.2 360 Total Security 4.x yes - 3.6.9335.2 360 Total Security 5.x yes - 3.6.9872.2 360 Total Security 6.x yes - 3.6.9908.2 360 Total Security 7.x yes - 3.6.10231.2 360 Total Security 8.x yes - 3.6.10547.2 360天擎 6.x - - 3.6.11017.2 360杀毒 1.x yes - 3.4.13.1 360杀毒 2.x yes - 3.4.25.1 360杀毒 3.x - - 3.5.2101.2 360杀毒 4.x - - 3.5.6528.2 360杀毒 5.x yes - 3.6.8769.2 Other 360Safe.com Antivirus x - - 3.5.2101.2 AEC, spol. s r.o. Other AEC, spol. s r.o. Antivirus x - - 3.5.2101.2 TrustPort Antivirus 2.x - yes 3.4.8.1 Agnitum Ltd. -

Guide to Computer Forensics and Investigations
Information Security Web Site Resources www.cert.org - Computer Emergency Response Team Coordination www.fcc.gov - Federal Communications Commission www.vmware.com - Vmware Workstation Center (CERT/CC) www.hhs.gov/ocr/hipaa - Health Insurance Portability and www.grc.com/securable - Data Execution Prevention testing software www.ists.dartmouth.edu - Research and education for cyber security Accountability Act of 1996 (HIPAA) www.eicar.org/anti_virus_test_fi le.htm - EICAR AntiVirus test fi le www.fi rst.org - Organization of 170 incident response teams www.sec.gov/spotlight/sarbanes-oxley.htm - Sarbanes-Oxley Act of www.microsoft.com/downloads/details.aspx?FamilyID=a3d1bbed-7f35- www.sans.org - SysAdmin, Audit, Network, Security (SANS) Institute 2002 (Sarbox) 4e72-bfb5-b84a526c1565&displaylang=en - Microsoft Vista security www.infragard.net - Information sharing between private industry and www.ftc.gov/privacy/glbact/glbsub1.htm - Gramm-Leach-Bliley Act (GLBA) templates the U.S. government www.fi ncen.gov/statutes_regs/patriot/index.html - USA Patriot Act (2001) www.microsoft.com/technet/security/tools/mbsahome.mspx - Microsoft www.issa.org - Information Systems Security Association (ISSA) info.sen.ca.gov/pub/01-02/bill/sen/sb_1351-1400/sb_1386_ Baseline Security Analyzer (MBSA) nsi.org - Information about security vulnerabilities and threats bill_20020926_chaptered.html - California Database Security Breach www.wireshark.org - Wireshark protocol analyzer csrc.nist.gov/index.html - Computer Security Resource Center (CSRC) Act (2003) www.netstumbler.com -

A Worldwide Survey of Encryption Products
A Worldwide Survey of Encryption Products Bruce Schneier Kathleen Seidel Saranya Vijayakumar Berkman Center for Internet Independent Researcher Harvard College and Society [email protected] [email protected] Harvard University [email protected] February 11, 2016 Version 1.0 Introduction Data security is a worldwide problem, and there is a wide world of encryption solutions available to help solve this problem. Most of these products are developed and sold by for-profit entities, although some are created as free open-source projects. They are available, either for sale or free download, all over the world. In 1999, a group of researchers from George Washington University attempted to survey the worldwide market for encryption products [HB+99]. The impetus for their survey was the ongoing debate about US encryption export controls. By collecting information about 805 hardware and software encryption products from 35 countries outside the US, the researchers showed that restricting the export of encryption products did nothing to reduce their availability around the world, while at the same time putting US companies at a competitive disadvantage in the information security market. Seventeen years later, we have tried to replicate this survey. Findings We collected information on as many encryption products as we could find anywhere in the world. This is a summary of our findings: We have identified 865 hardware or software products incorporating encryption from 55 different countries. This includes 546 encryption products from outside the US, representing two-thirds of the total. Table 1 summarizes the number of products from each country. The most common non-US country for encryption products is Germany, with 112 products. -

Complete List of ALL File Extensions and Information - Botcrawl
Complete List of ALL File Extensions and Information - Botcrawl Extension Information A Image Alchemy File (Handmade Software, Inc.) A Unknown Apple II File (found on Golden Orchard Apple II CD Rom) A ADA Program A Free Pascal Archive File for Linux or DOS Version (FPC Development Team) a UNIX Static Object Code Library A Assembly Source Code (Macintosh) A00 Archive Section A01 ARJ Multi-volume Compressed Archive (can be 01 to 99) (also see .000) (can be 01 to 99) (also see .000) A01 OzWin CompuServe E-mail/Forum Access SYSOP File A01 Archive Section A02 Archive Section A02 OzWin CompuServe E-mail/Forum Access SYSOP File A03 Archive Section A03 annotare ava 04 Project File (annotare.net) A03 OzWin CompuServe E-mail/Forum Access SYSOP File A04 OzWin CompuServe E-mail/Forum Access SYSOP File A04 Archive Section A05 OzWin CompuServe E-mail/Forum Access SYSOP File A05 Archive Section A06 OzWin CompuServe E-mail/Forum Access SYSOP File A06 Archive Section A06 Lotto Pro 2002 Smart Number Ticket A07 OzWin CompuServe E-mail/Forum Access SYSOP File A07 Archive Section A07 TaxCalc Tax File (Acorah Software Products Ltd.) A08 OzWin CompuServe E-mail/Forum Access SYSOP File A08 Archive Section A09 OzWin CompuServe E-mail/Forum Access SYSOP File A09 Archive Section A1 Free Pascal Archive File for GO321v1 Platform (FPC Development Team) A1 Unknown Apple II File (found on Golden Orchard Apple II CD Rom) A10 OzWin CompuServe E-mail/Forum Access SYSOP File A11 AOL Instant Messenger (AIM) Graphic (America Online, Inc.) A2 Unknown Apple II File (found on -
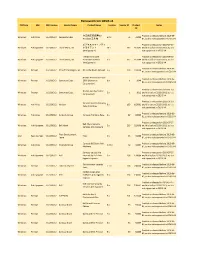
Removed from OESIS V4 Platform SDK SDK Version Vendor Name Product Name Version Vendor ID Product Notes ID
Removed from OESIS v4 Platform SDK SDK Version Vendor Name Product Name Version Vendor ID Product Notes ID 卡巴斯基反病毒6.0 Product is released before 2010-06- Windows Anti-Virus 3.6.10363.2 Kaspersky Labs 6.0.x 76 76008 Windows工作站 01, so it is not supported in OESIS V4 ビジネスセキュリティ Product is released on 2010-07-27 Windows Anti-Spyware 3.6.10363.2 Trend Micro, Inc. クライアント 16.x 167 167045 and it is before 2013-01-01, so it is (AntiSpyware) not supported in OESIS V4 Trend Micro Core Product is released on 2010-06-30 Windows Anti-Spyware 3.6.10363.2 Trend Micro, Inc. Protection Module 1.x 167 167044 and it is before 2013-01-01, so it is [AntiSpyware] not supported in OESIS V4 Product is released before 2010-06- Windows Firewall 3.6.10363.2 Kerio Technologies, Inc. Kerio WinRoute Firewall 6.x 203 203000 01, so it is not supported in OESIS V4 Norton Personal Firewall Product is released before 2010-06- Windows Firewall 3.6.10363.2 Symantec Corp. 2006 (Symantec 8.x 1 1049 01, so it is not supported in OESIS V4 Corporation) Product is released on 2010-11-30 Norton 360 (Symantec Windows Firewall 3.6.10363.2 Symantec Corp. 5.x 1 1013 and it is before 2013-01-01, so it is Corporation) not supported in OESIS V4 Product is released on 2010-06-30 Verizon Internet Security Windows Anti-Virus 3.6.10363.2 Verizon 9.x 169 169001 and it is before 2013-01-01, so it is Suite Anti-Virus not supported in OESIS V4 Product is released before 2010-06- Windows Anti-Virus 3.6.10363.2 Comodo Group Comodo AntiVirus Beta 2.x 92 92003 01, so it is not supported in OESIS V4