Xton Access Manager User Manual
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Openflight® Scene Description Database Specification
OpenFlight® Scene Description Database Specification Version 15.7.0 April, 2000 USE AND DISCLOSURE OF DATA ©MultiGen-Paradigm® Inc., 2000. All rights reserved. MultiGen Inc. is the owner of all intellectual property rights, including but not limited to, copyrights in and to this book and its contents. The reader of this book is licensed to use said contents and in- tellectual property in any lawful manner and for any lawful purpose; said license is non-exclusive and royalty-free. This book may not be reproduced or distributed in any form, in whole or part, without the express written permission of MultiGen-Par- adigm Inc. 550 S. Winchester Blvd., Suite 500, San Jose, CA 95128 Phone (408) 261-4100 Fax (408) 261-4103 Copyright © 2000 MultiGen-Paradigm® Inc. All Rights Reserved. OpenFlight Scene Description Database Specification,v15.7.0 (April, 2000) MultiGen-Paradigm Inc. (MultiGen-Paradigm) provides this material as is, without warranty of any kind, either expressed or implied, including, but not limited to, the implied warranties of merchantability and fitness for a par- ticular purpose. MultiGen-Paradigm may make improvements and changes to the product described in this manual at any time without notice. MultiGen-Paradigm assumes no responsibility for the use of the product or this manual except as expressly set forth in the applicable MultiGen-Paradigm agreement or agreements and subject to terms and con- ditions set forth therein and applicable MultiGen-Paradigm policies and procedures. This manual may contain technical inaccuracies or typographical errors. Periodic changes are made to the information contained herein: these changes will be incorporated in new editions of the manual. -

Data Format for the Interchange of Biometric and Forensic Information
ANSI/NIST-ITL 1-2011 Data Format for the Interchange of Biometric and Forensic Information Foreword ...……………………………………………………………………………..vii 1 Introduction...................................................................................................... 1 1.1 Previous versions of the Standard ............................................................ 1 1.2 Summary of Changes for this Version of the Standard ............................. 1 2 Scope, purpose, and conformance ................................................................. 2 2.1 Scope ........................................................................................................ 2 2.2 Purpose..................................................................................................... 3 2.3 Conformance............................................................................................. 3 3 Encodings of the Standard.............................................................................. 3 4 Transmitted data conventions ......................................................................... 4 4.1 Friction Ridge Representation................................................................... 4 4.2 Byte and bit ordering ................................................................................. 4 4.3 Grayscale data .......................................................................................... 4 4.4 Binary data ................................................................................................ 5 4.5 Color data................................................................................................. -

Lightning Layout Tricks
Welcome to @NEDreamin #NEDreamin Manchester, NH 2018 Lightning Layout Tricks Tom Hoffman @NEDreamin #NEDreamin Manchester, NH 2018 Me (@AccidentalAdmin) • Practice Lead @ Spark.Orange • Co-founded Pittsburgh Non-Profit User Group, Current Admin User Group Leader • The Accidental Admins Blog • Very active in Answer Community • Dad, Husband & Hopeless Pirates Fan • Read at least one book a week, sometimes in a day. • Top Gun is the best movie ever made…prove me wrong. @NEDreamin #NEDreamin Manchester, NH 2018 Overview & Goals Baseline Experience Simplify Innovate Understand Lightning Identify ways to Recognize when Record detail tabs, pages & how they optimized the user Lightning Pages can conditional interact with other experience to gain reduce the need for components, $User aspects of Salesforce better adoption & record types, page filtered components, results layouts, & automation and more fun. @NEDreamin #NEDreamin Manchester, NH 2018 Forward-Looking Common Sense Statement • Probably going to see a few interesting things today (I hope…) • It’s ok to experiment, but Practice Safe UX – use a sandbox • Identify a good use case & test • Roll out to small group of test users, get feedback • If it makes tasks easier and/or users happier = good • If it makes you look really smart = great (as long as ^ is true too) Make sure it makes sense – just because you can, does not mean you should. @NEDreamin #NEDreamin Manchester, NH 2018 Audience Participation Round! How many of you are with organizations that have migrated to Lightning? @NEDreamin -
Linkedin Sales Navigator for Salesforce Installation Guide
LinkedIn Sales Navigator for Salesforce Installation Guide: Lightning View The installation process will take less than 30 minutes. Note: This guide is for Salesforce Lightning. If you need to install Classic, please review the guide here. The LinkedIn Sales Navigator for Salesforce Application • Allow Sales Navigator seat holders to search for people on LinkedIn and view profile details including photos, current roles, and work history from within Salesforce. • Uncover the best way to get introduced through TeamLink. • Find new leads directly in Salesforce with Lead Recommendations. • Get Account & Lead Updates including news mentions and job changes when viewing accounts in Salesforce. • Send InMail, messages, and customized connection requests from within Salesforce. Table of Contents • Before You Begin • Phase 1: Install the Application • Phase 2: Application Set Up • Phase 3: Test the Application • Additional Information and Troubleshooting Tips Recent Updates (This includes feature changes for Sales Navigator since the last Quarter Release) • Now available for Person Account types. Embedded profiles (Widget) will work for both Lightning and Classic versions of Salesforce. o Note: CRM Sync does not support Person Account types (inclusive of Write-back and Autosave Person Accounts as a contact). KEY CALLOUTS • Note: Installation of Sales Navigator will create new Record Types for Tasks and assign custom defaults. If you do not have “Task” Record Types created, this can cause Record Types for Global Actions (e.g. New Event, Log a Call, New Task, etc.) to default to "--Master--" which would remove existing Global Actions from the Activities list. • If after enablement you find that Global Actions are missing, please take the following steps: o To Start this process, navigate to Objects and Fields in the Setup menu using “Quick Find”. -

Time Matters and Billing Matters 11.1 User Guide Contents
Time Matters® and Billing Matters® 11.1 User Guide About this guide This guide provides steps to achieve basic, commonly performed tasks. For additional details, including interface elements and advanced tasks, see the Time Matters® Help. Copyright and Trademark LexisNexis, Lexis, and the Knowledge Burst logo are registered trademarks of Reed Elsevier Properties Inc., used under license. Time Matters and Billing Matters are registered trademarks of LexisNexis, a division of Reed Elsevier Inc. Other products and services may be trademarks or registered trademarks of their respective companies. Copyright 2012 LexisNexis, a division of Reed Elsevier Inc. All rights reserved. Version 2012.02.14.11.03 LexisNexis 2000 Regency Parkway Suite 600 Cary, North Carolina USA 27518 North America: 800.387.9785 Outside North America: 919.467.1221 Fax: 919.467.7181 http://www.lexisnexis.com/law‐firm‐practice‐management/time‐matters Time Matters and Billing Matters 11.1 User Guide Contents Login and Password Assistance ................................................................................................. 1 Start Time Matters ............................................................................................................................................. 1 Log in .................................................................................................................................................................. 1 Use Training Mode to practice using Time Matters .......................................................................................... -
Quick Actions Implementation Guide
Quick Actions Implementation Guide Salesforce, Winter ’22 @salesforcedocs Last updated: August 24, 2021 © Copyright 2000–2021 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of salesforce.com, inc., as are other names and marks. Other marks appearing herein may be trademarks of their respective owners. CONTENTS Quick Actions . 1 Default Actions . 3 Default Action Fields . 5 Mobile Smart Actions . 7 Setting Up Quick Actions . 9 Enable Actions in the Chatter Publisher . 9 Enable Feed Updates for Related Records . 10 Create Object-Specific Quick Actions . 11 Visualforce Pages as Object-Specific Custom Actions . 12 Prerequisites for Using Canvas Apps as Custom Actions . 14 Create Global Quick Actions . 15 Set Predefined Field Values for Quick Action Fields . 16 Notes on Predefined Field Values for Quick Actions . 16 Customize Actions with the Enhanced Page Layout Editor . 17 Global Publisher Layouts . 19 Create Global Publisher Layouts . 20 Add Actions to Global Publisher Layouts . 21 Assign Global Publisher Layouts to User Profiles . 23 Quick Actions and Record Types . 24 Actions Best Practices . 25 Troubleshooting Actions . 26 QUICK ACTIONS Quick actions enable users to do more in Salesforce and in the Salesforce mobile app. With custom EDITIONS quick actions, you can make your users’ navigation and workflow as smooth as possible by giving them convenient access to information that’s most important. For example, you can let users create Available in: both Salesforce or update records and log calls directly in their Chatter feed or from their mobile device. Classic (not available in all Quick actions can also invoke Lightning components, flows, Visualforce pages, or canvas apps with orgs) and Lightning functionality that you define. -

Suitescript Code Samples
SuiteScript Code Samples September 9, 2020 2020.2 Copyright © 2005, 2020, Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error- free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are "commercial computer software" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, use, duplication, disclosure, modification, and adaptation of the programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, shall be subject to license terms and license restrictions applicable to the programs. No other rights are granted to the U.S. Government. This software or hardware is developed for general use in a variety of information management applications. -

The Microsoft Excel File Format"
OpenOffice.org's Documentation of the Microsoft Excel File Format Excel Versions 2, 3, 4, 5, 95, 97, 2000, XP, 2003 Author Daniel Rentz ✉ mailto:[email protected] http://sc.openoffice.org License Public Documentation License Contributors Yves Hiltpold, James J. Keene, Sami Kuhmonen, John Marmion, Alexander Mavrin, Josh Micich, Andrew C. Oliver, Mike Salter, Stefan Schmöcker, Charles Wyble Other sources Hyperlinks to Wikipedia ( http://www.wikipedia.org) for various extended information Mailing list ✉ mailto:[email protected] Subscription ✉ mailto:[email protected] Download PDF http://sc.openoffice.org/excelfileformat.pdf OpenOffice.org 1.x XML http://sc.openoffice.org/excelfileformat.sxw OpenOffice.org 2.x XML http://sc.openoffice.org/excelfileformat.odt Project started 2001-Jun-29 Last change 2008-Apr-02 Revision 1.42 Contents 1 Introduction ......................................................................................................... 6 1.1 License Notices 6 1.2 Abstract 7 1.3 Byte Order 9 2 Document Structure ........................................................................................... 10 2.1 Document Types 10 2.2 The Binary Interchange File Format 13 2.3 File Structure 14 2.4 BIFF Record Structure 16 2.5 Common Record Substructures 17 3 Formulas ............................................................................................................ 28 3.1 Common Formula Structure 28 3.2 Token Classes 32 3.3 Cell Addresses in Tokens 36 3.4 Token Overview 40 3.5 Unary Operator Tokens -

Utrex Specifications
UTREx Data Clearinghouse File Specification 2021-22 ADA Compliant: August 5, 2021 Table of Contents Introduction ............................................................................................................................................................................ 3 Recent Revisions: ..................................................................................................................................................................... 3 District Record (DI) .................................................................................................................................................................. 5 School Record (SC) .................................................................................................................................................................. 8 Student Record (S1) ............................................................................................................................................................... 16 SCRAM Record (S2) ............................................................................................................................................................... 95 Youth in Care (YIC) Record (S3) ........................................................................................................................................... 110 Section 504 Record (S4) ...................................................................................................................................................... 122 -
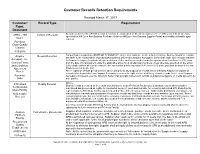
Download Customer Records Retention
Customer Records Retention Requirements Revised March 17, 2017 Customer/ Record Type Requirement Rqmt. Document APEX – HM Control of Records Records as defined by AS9100 section 4.2.4 must be maintained on file for calendar year + ten (10) years (unless otherwise specified by HM Dunn AeroSystems Purchase Order or HM Dunn AeroSystems Supplier Portal) and readily retrievable upon Dunn. request. Purchase Order Quality Clauses 3/10/2016 Arnprior Record Retention For purchases supporting ARNPRIOR AEROSPACE, Seller shall maintain, on file at Seller's facility, Quality Assurance records traceable to the conformance of product/part numbers delivered to Arnprior Aerospace. Seller shall make such records available Aerospace Inc. to Arnprior Aerospace's authorized representatives. Seller shall retain such records for a period of not less than ten (10) years General Terms from the date of final payment under the applicable Order for all product/part numbers unless otherwise specified on the Order. and Conditions Seller shall maintain all records related to the current first article inspection (FAI) for ten (10) years past final delivery of the last Agreement Product covered by the FAI. Rev. 8 At the expiration of such period set forth above and prior to any disposal of records, Seller will notify Arnprior Aerospace of records to be disposed of, and Arnprior Aerospace reserves the right to request delivery of such records. In the event Arnprior Purchase Aerospace chooses to exercise this right, Seller shall promptly deliver such records to Arnprior Aerospace on media agreed to by Order both parties. ATK Alliant Quality Records Q078 – Quality records generated as the results of performance to an ATK Mesa Facility issued purchase order/contract shall be Techsystems maintained and preserved as legible for a period of seven (7) years and available for review by authorized ATK Mesa Facility Mesa Facility representatives, ATK Mesa Facility customers, and/or Government representatives. -

VOA 2017 Compiled Rating List Data Specification
VOA 2017 Compiled Rating List Data Specification Contents Part one - About this guide ..................................................................... 3 Background ............................................................................................................................... 3 Introduction ............................................................................................................................... 3 Record formats.......................................................................................................................... 3 APIs ............................................................................................................................................ 3 Part two - Compiled rating list entry data .............................................. 5 List entry data explained .......................................................................................................... 5 Reference number and address ......................................................................................................... 5 Rateable value and effective date ...................................................................................................... 5 Descriptions, special category codes and valuation scheme references ............................................ 5 Valuation indicators............................................................................................................................ 5 Current vs historic list entries ............................................................................................................ -

Publication 28 Contents
Contents 1 Introduction. 1 11 Background . 1 111 Purpose . 1 112 Scope . 1 113 Additional Benefits . 1 12 Overview . 2 121 Address and List Maintenance . 2 122 List Correction. 2 123 Updates. 2 124 Address Output . 3 125 Deliverability . 3 13 Address Information Systems Products and Services . 3 2 Postal Addressing Standards . 5 21 General . 5 211 Standardized Delivery Address Line and Last Line. 5 212 Format . 5 213 Secondary Address Unit Designators . 6 214 Attention Line . 7 215 Dual Addresses . 7 22 Last Line of the Address. 8 221 City Names . 8 222 Punctuation . 8 223 Spelling of City Names . 8 224 Format . 9 225 Military Addresses. 9 226 Preprinted Delivery Point Barcodes . 9 23 Delivery Address Line . 10 231 Components . 10 232 Street Name . 10 233 Directionals . 11 234 Suffixes . 13 235 Numeric Street Names . 13 236 Corner Addresses . 14 237 Highways. 14 238 Military Addresses. 14 239 Department of State Addresses . 15 June 2020 i Postal Addressing Standards 24 Rural Route Addresses. 15 241 Format . 15 242 Leading Zero . 16 243 Hyphens . 16 244 Designations RFD and RD . 16 245 Additional Designations . 16 246 ZIP+4. 16 25 Highway Contract Route Addresses . 17 251 Format . 17 252 Leading Zero . 17 253 Hyphens . 17 254 Star Route Designations . 17 255 Additional Designations . 18 256 ZIP+4. 18 26 General Delivery Addresses . 18 261 Format . 18 262 ZIP Code or ZIP+4 . 18 27 United States Postal Service Addresses . 19 271 Format . 19 272 ZIP Code or ZIP+4 . 19 28 Post Office Box Addresses. 19 281 Format . 19 282 Leading Zero .