COMPUTER HARDWARE SERVICING and NETWORKING for VI Semester DECE
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
How to Know What Drivers to Download
how to know what drivers to download How do I find the hard drive type and specifications? If you'd like to view detailed information about your hard disk drives, solid-state drives, or external storage devices attached to your computer, we recommend the methods below. System Information in Windows 10. In Windows 10, you can view information about your hardware (including disks) using the System Information utility . To open the System Information utility in Windows 10: Press the Windows key, type System Information , and press Enter . Or, you can use the Run box to open the System Information utility. Press the Windows key + R keyboard shortcut. In the Run box, type msinfo32 . Press Enter or click OK . In the System Information window that opens, in the left window pane, you'll see a list of hardware categories. Expand Components , then Storage . Then, choose Drives , Disks , or any category you'd like to view. Earlier versions of Microsoft Windows. In earlier versions of Microsoft Windows, you can open the System Information utility by following the steps below. Click Start and then click the Programs folder. Click Accessories and then the System Information or System Tools folder. Open the System Information file. In the System Information window, click the + symbol next to Components . Click the + next to Storage and click Drives . In the right-side of the window, you see information about the hard drive including its capacity and serial number. IBM-compatible users. IBM-compatible users can usually enter the computer's BIOS setup to view additional information about their hard drive. -

Download Date 24/09/2021 14:31:55
To Upgrade or Not To Upgrade Application Item Type Thesis Authors Francisco, Neil Download date 24/09/2021 14:31:55 Link to Item http://hdl.handle.net/20.500.12648/1799 To Upgrade or Not To Upgrade Application __________________________ A Master's Thesis Project Presented to the Department of Communication and Information Design __________________________ In Partial Fulfillment of the Requirements for the Master of Science Degree State University of New York Polytechnic Institute By Neil Francisco May 2021 TO UPGRADE OR NOT TO UPGRADE SUNY POLYTECHNIC INSTITUTE DEPARTMENT OF INFORMATION DESIGN AND TECHNOLOGY CERTIFICATE OF APPROVAL Approved and recommended for acceptance as a thesis in partial fulfillment of the requirements for the degree of Master of Science in Information Design and Technology. ____________________June 11, 2021 DATE ________________________________ Dr. Kathryn Stam Thesis Advisor ____________________ DATE ________________________________ Dr. Ryan Lizardi Second Reader 2 TO UPGRADE OR NOT TO UPGRADE ABSTRACT New Technology consists of new hardware devices, computational workflows, digital advances, and information systems. As technology continues to evolve over the years, this never-ending cycle of new devices and experiences will always be present amongst consumers. Traditionally, new hardware devices are intriguing because they are designed to improve our access to information, media, and a connection to the digital world, but does this mean our previous-gen devices are no longer valuable? This project involves creating a prototype application designed for both computer and mobile interfaces to help improve the accessibility to information and the overall user experience with an older device. The “To Upgrade or Not To Upgrade” app will inform end-users of their older technological device specifications and suggest hardware/software methods to unlock their full potential. -
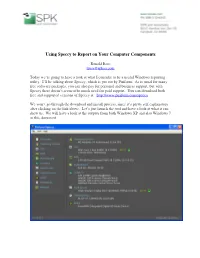
Using Speccy to Report on Your Computer Components
Using Speccy to Report on Your Computer Components Ronald Ross [email protected] Today we’re going to have a look at what I consider to be a useful Windows reporting utility. I’ll be talking about Speccy, which is put out by Piriform. As is usual for many free software packages, you can also pay for personal and business support, but with Speccy there doesn’t seem to be much need for paid support. You can download both free and supported versions of Speccy at: http://www.piriform.com/speccy We won’t go through the download and install process, since it’s pretty self explanatory after clicking on the link above. Let’s just launch the tool and have a look at what it can show us. We will have a look at the outputs from both Windows XP and also Windows 7 in this document. In the screen shot above, we see summary information for a Windows XP, 32-bit machine. Each of the items listed in the left hand panel can be drilled down into for expanded information. Before we have a more detailed look at some of the components we see summarized, it might be useful to look at some of the general features of Speccy. Above we see that it is possible to take a full snapshot of a machine’s information. This snapshot can be reloaded later by Speccy for analysis, or comparison with some other snapshot. It’s also possible to publish the snapshot to a webpage with the Publish Snapshot… menu choice. -

Release 343 Graphics Drivers for Windows, Version 344.48. RN
Release 343 Graphics Drivers for Windows - Version 344.48 RN-W34448-01v02 | September 22, 2014 Windows Vista / Windows 7 / Windows 8 / Windows 8.1 Release Notes TABLE OF CONTENTS 1 Introduction to Release Notes ................................................... 1 Structure of the Document ........................................................ 1 Changes in this Edition ............................................................. 1 2 Release 343 Driver Changes ..................................................... 2 Version 344.48 Highlights .......................................................... 2 What’s New in Version 344.48 ................................................. 3 What’s New in Release 343..................................................... 5 Limitations in This Release ..................................................... 8 Advanced Driver Information ................................................. 10 Changes and Fixed Issues in Version 344.48.................................... 14 Open Issues in Version 344.48.................................................... 15 Windows Vista/Windows 7 32-bit Issues..................................... 15 Windows Vista/Windows 7 64-bit Issues..................................... 15 Windows 8 32-bit Issues........................................................ 17 Windows 8 64-bit Issues........................................................ 17 Windows 8.1 Issues ............................................................. 18 Not NVIDIA Issues.................................................................. -

Architecture for Analyzing Potentially Unwanted Applications
Architecture for analyzing Potentially Unwanted Applications Alberto Geniola School of Science Thesis submitted for examination for the degree of Master of Science in Technology. Espoo 10.10.2016 Thesis supervisor: Prof. Tuomas Aura Thesis advisor: M.Sc. Markku Antikainen aalto university abstract of the school of science master’s thesis Author: Alberto Geniola Title: Architecture for analyzing Potentially Unwanted Applications Date: 10.10.2016 Language: English Number of pages: 8+149 Department of Computer Science Professorship: Information security Supervisor: Prof. Tuomas Aura Advisor: M.Sc. Markku Antikainen The spread of potentially unwanted programs (PUP) and its supporting pay par install (PPI) business model have become relevant issues in the IT security area. While PUPs may not be explicitly malicious, they still represent a security hazard. Boosted by PPI companies, PUP software evolves rapidly. Although manual analysis represents the best approach for distinguishing cleanware from PUPs, it is inapplicable to the large amount of PUP installers appearing each day. To challenge this fast evolving phenomenon, automatic analysis tools are required. However, current automated malware analisyis techniques suffer from a number of limitations, such as the inability to click through PUP installation processes. Moreover, many malware analysis automated sandboxes (MSASs) can be detected, by taking advantage of artifacts affecting their virtualization engine. In order to overcome those limitations, we present an architectural design for imple- menting a MSAS mainly targeting PUP analysis. We also provide a cross-platform implementation of the MSAS, capable of running PUP analysis in both virtual and bare metal environments. The developed prototype has proved to be working and was able to automatically analyze more that 480 freeware installers, collected by the three top most ranked freeware websites, such as cnet.com, filehippo.com and softonic.com. -
Recuva Software Free Download Full Version for Windows 8 ->>->>->>
Recuva Software Free Download Full Version For Windows 8 ->>->>->> http://shurll.com/78fy0 1 / 5 2 / 5 You..may..want..to..scan..your..system..for..spyware..and..viruses,..as..they..may..interfere..with..yo ur..ability..to..connect..to..Yahoo!Close..Update..Your..Review..Since..you've..already..submitted..a..r eview..for..this..product,..this..submission..will..be..added..as..an..update..to..your..original..reviewEd itors'....Review+....by:....Download.com....staff....on....September....10,....2014....Recuva....undeletes. ...files;....recovers....data....from....corrupted,....damaged,....and....reformatted....discs;....restores....u nsaved....Word....documents;....and....securely....deletes....files....so....they're....unrecoverable,....eve n....by....RecuvaAnother....Picture....recovery....software....(that's....free)....is....TestDisk....and....it's... .sister....program....PhotoRecThank...you,...manIncluding..both..32-bit..and..64-bit..versions,..but..not ..RT..tablet..editions.Builds..We..also..offer..a..portable..version..for..installing..on..USB..thumb..drive sreviewed....on....October....19,....2015....Read....all....reviews....Review........You....may....also....like... .....Recuva....PortableA....portable....tool....to....restore....accidentally....deleted....filesFreeEnglish....S peccyA....simple....way....to....get....your....system....specificationsFreeEnglish....DefragglerFree....def ragmenter....from....the....creators....of....CCleanerFreeEnglish....Speccy....Portable....Easy....portable. ...system....information....tool....for....your....PCFreeEnglish........Features........about....Recuva....list... -
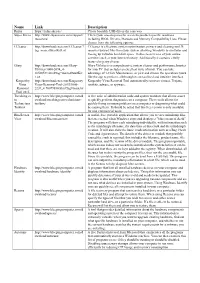
Name Link Description
Name Link Description Rufus https://rufus.akeo.ie/ Create bootable USB drives the easy way Super Micro http://www.supermicro.com/support/ This is your one-stop area for access to product-specific resources resources/ including BIOS, Drivers, Manuals and Memory Compatibility Lists. Please choose from the following options: CCleaner http://download.cnet.com/CCleaner/? CCleaner is a freeware system optimization, privacy and cleaning tool. It tag=main;dlStartKitList removes unused files from your system allowing Windows to run faster and freeing up valuable hard disk space. It also cleans traces of your online activities such as your Internet history. Additionally it contains a fully featured registry cleaner. Glary http://download.cnet.com/Glary- Glary Utilities is a comprehensive system cleaner and performance booster Utilities/3000-2094_4- for your PC that includes an excellent suite of tools. You can take 10508531.html?tag=main;dlStartKit advantage of 1-Click Maintenance, or pick and choose the operations you'd List like the app to perform, all through its streamlined and intuitive interface. Kaspersky http://download.cnet.com/Kaspersky- Kaspersky Virus Removal Tool automatically removes viruses, Trojans, Virus Virus-Removal-Tool-2015/3000- rootkits, adware, or spyware. Removal 2239_4-76079830.html?tag=main;lsr Tool 2015 Tweaking.co http://www.bleepingcomputer.com/d A free suite of administration tools and system monitors that allows a user m ownload/tweakingcom-technicians- to quickly perform diagnostics on a computer. These tools allows for Technicians toolbox/ quickly fixing common problems on a computer or diagnosing what could Toolbox be causing them. It should be noted that this free version is only available for non-commercial users. -

Bearly Bytes January, 2011
Big Bear Computer Club Bearly Bytes January, 2011 Volume 20 Big Bear Computer Club Bearly Bytes Big Bear, California Award Winning Bearly Bytes Newsletter Next Meeting JAN 11, 2011 - 5:30 @ The BIG BEAR CHAMBER of COMMERCE MEETING PLACE FOR JANUARY 11TH SNOW SUMMIT SKI SLOPES AT NIGHT MOVED TO THE BIG BEAR CHAMBER BIG BEAR LAKE, CA OF COMMERCE BUILDING 5:30-8:00 AS THE DISCOVERY CENTER HAS BUILDING PROBLEMS. WHO VIEWS OUR BEARLY BYTES NEWSLETTER? The Big Bear Computer Club’s newsletter gets widespread visibility. Not only does it get posted on our website www.bigbearcc.org, it is emailed to our 100+ membership - both active and inac- tive. It is estimated that our newsletter is seen by approximately 600 viewers. Table of Contents Table of Contents Bearly Bytes goes out to various other Com- Viewership of Bearly Bytes Newsletter . .1 puter User Group Clubs in the Southern Califor- HelpMeeting Line change& Key Leaders. of venue . for. .January . .. .. .. .2 . .1 nia area. The newsletter is also sent out to our President’sHelpline & MessageKey Leaders . .. .. .. .. .. .. .. .. .. .. 3. 2 advertisers - both local internet advertisers and President’s Message . 3 Club Calendar & Cash Flow. 6 out of State advertisers. Election of Officers & Key Leaders. 3 Word/Excel/WindowMore Portable Utilities Tips. for . Your. Flash. Drive. .. .11 . 4 & 5 Copies of our newsletter also go out to Peach- Calendar, Cash Flow, Computer Links. 6 pit, Pearson, and O’Reilly book vendors who are Door Prize Winners. .12 great supporters of our Computer Club by do- Facebook me! A Book Review . 7 nating monthly free books for review. -

Divide Plus User Manual
DivIDE Plus Hard Disk Expansion Interface For the Sinclair ZX Spectrum © Jarek Adamski & Jurek Dudek for RWAP Software USER MANUAL Manual Update 7.1 (January 2011) © RWAP Software www.rwapsoftware.co.uk DivIDE Plus User Manual Table of CONTENTS NOTICE ................................................................................................................................ 6 IMPORTANT NOTE FOR SPECTRUM +2A, +2B AND +3 USERS .......................... 6 COMPATIBLE ADD-ONS ................................................................................................. 7 AVAILABLE FIRMWARE ................................................................................................ 7 INSTALLATION OF DIVIDE PLUS .......................................................................................... 9 Setting Up ...................................................................................................................... 10 USING A DISK DRIVE ................................................................................................... 10 Compatible Disk Drives ................................................................................................ 10 Jumper Settings ............................................................................................................. 10 Use in 128K Mode ......................................................................................................... 11 Installing Firmware ..................................................................................................... -
Software We Recommend
Software we recommend Software we recommend to use in providing support and general day to day computer usage. Whitelist Blacklist Anti-Virus and Malware tools Windows Maintenance Disks Disk & Partition Management Verifying Disk Health Reading Machine Temperatures & Voltages Whitelist This serves as a master list of recommended and permitted software that we permit in the community. Please see the 'how tos' that may be present for these pieces of software. TypeNameNotesDownloadHowTo File https://www.7- 7zip Archival zip.org/download.html Gparted is a Linux/GNU front- end to the parted tool.The It gparted Disk is package Gparted HowTo manipulationthein recommendedany methoddistro for manipulating disks when using a Linux live session. TypeNameNotesDownloadHowTo Chrome , FireFox AduBlock , BlockerOrigin Edge , Opera TypeNameNotesDownloadHowTo Ventoy Linux documentation . Yumi documenation , make sure you Rufus select , the correctVentoy Rufus, tool, Ventoy, forbalenaEtcher balenaEthcher, your Image , YUMI, mountingmotherboard WindowsYUMI tools (BIOS Media, or Creation UEFI).Windows Tool TheMedia Windows Creation Media CreationTool Tool only works on Windows and for creating the Windows installer Blacklist This serves as a master list of banned software that we do not permit in the community. EOL OS Any EOL OS is unsupported, it does not need to be listed here. Name Notes Windows XP Windows Vista Windows 7 Ubuntu 12.04 Name Notes See here to check if you are running a compatable verion. Windows You 10 can type "Winver" on the start menu to see your current version. ETC Unsupported OS Name Notes Due to ReviOS TOS this is considered to have malware ReviOSincluded such as keyloggers. The vendor also provides support to users. -

D:\My Documents\My Godaddy Website\Pdfs\Word
UTILITY PROGRAMS Jim McKnight www.jimopi.net Utilities1.lwp revised 10-30-2016 My Favorite download site for common utilities is www.ninite.com. Always go there first to see if what you want is available there. WARNING: These days, pretty much every available free utility tries to automatically install Potenially Unsafe Programs (PUP’s) during the install process of the desired utility. To prevent this, you must be very careful during the install to uncheck any boxes for unwanted programs (like Chrome, Ask Toolbar, Conduit Toolbar, Yahoo Toolbar, etc.). Also when asked to choose a “Custom” or “Express” Install, ALWAYS choose “Custom”, because “Express” will install unwanted programs without even asking you. Lastly, there are also sneaky windows that require you to “Decline” an offer to prevent an unwanted program from installing. After clicking “I Decline”, the program install will continue. This is particularly sneaky. Always read carefully before clicking Next. Both download.com (aka download.cnet.com) and sourcforge.net have turned to the dark side. In other words, don’t trust ANY download website to be PUP or crapware free. CONTENTS: GENERAL TOOLS & UTILITIES HARD-DRIVE & DATA RECOVERY UTILITIES MISC PROGRAM TIPS & NOTES - listed by Category ADDITIONAL PROGRAM TIPS & NOTES - listed by Program Name : ADOBE READER BELARC ADVISOR CCLEANER Setup & Use CODESTUFF STARTER FAB’s AUTOBACKUP MOZBACKUP REVO Uninstaller SANDBOXIE SECUNIA Personal Software Inspector SPEEDFAN SPINRITE SYNCBACK UBCD 4 WINDOWS Tips GENERAL TOOLS & UTILITIES (Mostly Free) (BOLD = Favorites) ANTI-MALWARE UTILITIES: (See my ANTI~MALWARE TOOLS & TIPS) ABR (Activation Backup & Restore) http://directedge.us/content/abr-activation-backup-and-restore BART PE (Bootable Windows Environment ) http://www.snapfiles.com/get/bartpe.html BOOTABLE REPAIR CD's. -

Metadefender Core V4.14.2
MetaDefender Core v4.14.2 © 2018 OPSWAT, Inc. All rights reserved. OPSWAT®, MetadefenderTM and the OPSWAT logo are trademarks of OPSWAT, Inc. All other trademarks, trade names, service marks, service names, and images mentioned and/or used herein belong to their respective owners. Table of Contents About This Guide 11 Key Features of Metadefender Core 12 1. Quick Start with MetaDefender Core 13 1.1. Installation 13 Operating system invariant initial steps 13 Basic setup 14 1.1.1. Configuration wizard 14 1.2. License Activation 19 1.3. Process Files with MetaDefender Core 19 2. Installing or Upgrading Metadefender Core 20 2.1. Recommended System Requirements 20 System Requirements For Server 20 Browser Requirements for the Metadefender Core Management Console 22 2.2. Installing Metadefender 22 Installation 22 Installation notes 23 2.2.1. Installing Metadefender Core using command line 23 2.2.2. Installing Metadefender Core using the Install Wizard 25 2.3. Upgrading MetaDefender Core 25 Upgrading from MetaDefender Core 3.x 25 Upgrading from MetaDefender Core 4.x 26 2.4. Metadefender Core Licensing 26 2.4.1. Activating Metadefender Licenses 26 2.4.2. Checking Your Metadefender Core License 33 2.5. Performance and Load Estimation 34 What to know before reading the results: Some factors that affect performance 34 How test results are calculated 35 Test Reports 35 Performance Report - Multi-Scanning On Linux 35 Performance Report - Multi-Scanning On Windows 39 2.6. Special installation options 42 Use RAMDISK for the tempdirectory 42 3. Configuring MetaDefender Core 46 3.1. Management Console 46 3.2.