1 Just the Basics DVD Contents
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Windows 7 End of Life Is Coming: Don't Put Your
WINDOWS 7 END OF LIFE IS COMING: DON’T PUT YOUR BUSINESS AT RISK BY NOT MIGRATING INTRODUCTION After January 14, 2020, Microsoft will no longer provide free security updates or support for Windows 7 and Windows Server 2008/ 2008 R2 operating systems (OS). This means there will be no more patches available and no more technical support from Microsoft’s support center. If you continue using Windows 7 and Windows Server 2008/R2 after that date, your systems will be at risk due to potential new vulnerabilities and cyber attacks, unless you plan on paying for Windows Extended Security Updates (ESU). With ESU support fees starting at 25~30€ per device and doubling each year after 2020, running Windows 7 and Windows Server 2008/R2 in your environment will quickly become very expensive. To avoid paying these high support costs and to enable successful migration, companies should begin planning for the inevitable upgrade to Windows 10. WHAT ARE THE MAJOR RISKS? Risk of Vulnerabilities and Cyberattacks In 2018, there were 499 Windows desktop OS vulnerabilities reported across Windows Vista, Windows 7, Windows RT, Windows 8/8.1, and Windows 10. Of these, 169 were considered critical vulnerabilities. During the same period, there were 449 Windows Server vulnerabilities, of which 136 were critical. While there was a slight drop in the number of Windows vulnerabilities from 2017 to 2018, over the past 6 years the number has nearly doubled.1 The infamous WannaCry ransomware attack, which infected over 200,000 computers worldwide in May 2017, was the result of an unpatched vulnerability that affected Windows OS. -

Omegakey Manage Your Device at the Management Module
Welcome to use our latest version of Lost Mode How to Start to Use it Bluetooth tracker. Detect the distance between the device and Bluetooth Tracker module your phone under the lost mode .Turn on the Step 1: Download the latest version App(version 1.6.0) from Apple App store. omegakey Manage your device at the management module. alarm at alert whether the device is lost, there Step 2: Open the Bluetooth and App. are two levels of lost alarm mode. Select the Thank you for purchasing omegakey Freely set and remove your device here. Step 3: Tap the Beacon for 3-5 times on hard surface, and the Beacon will be connectable when you Double-click the “call” button to find your device. alarm mode you want from the device. Phone hear a buzz. alarm, and both ends alarm. Step 4: Click the Beacon in the App which you want to configure and enter a name to connect it. Step 5: Now, you can configure and use the Beacon normally. NEXT Note: If you're having trouble with the Bluetooth, we recommend you completely remove the battery from the unit for 10 sec and reinsert it. There are many apps you can download some are better than others, we have linked just click on the apple / android icons on the first page Once you have selected the app you like download it and follow the on screen instructions ATTACH BLUETOOTH BEACON EXTERNALLY FOR MAX PERFORMANCE Found mode More View the alarm location or item's last location Find the device under the find mode according p.s make sure your Bluetooth is on and your phone is compatible with 4.0 Bluetooth to the strength of the signal. -

For Those in Operating System Limbo
By Merle Windler, Thoroughbred Systems, Inc. ComputerComputerCornerCorner TenTen TipsTips forfor WindowsWindows 10,10, PartPart 11 .. .. .. Ah,Ah, Yes,Yes, ThatThat MeansMeans FiveFive forfor Now,Now, FiveFive LaterLater y the time this issue of The Lifeline is delivered, the announced deadline of June 29, 2016 will have passed Bfor a FREE Windows 10 upgrade for those with qualifying versions of Windows 7, Windows 8, or Windows 8.1. Hopefully the information provided on this subject in an earlier Computer Corner article helped readers not only in making up their minds when or if to update within the "FREE UPDATE" period, but also aided those who did so in making those updates go smoothly and without data loss. Some of Microsoft's customers were taken by surprise at the boldness of that corporate giant. As the deadline date Tip 1: Classic Shell Windows XP or approached, many found Microsoft's tactics to be nothing Windows 7 Style Menus short of pushy. We received scores of morning phone calls First, If you are a "creature of habit" and prefer the "old in the past month when municipal and rural water district style" classic Windows Menu style of Windows XP and staff realized that computers left on overnight had Windows 7 over the new “Menu and Tiles” and "Metro automatically begun the Windows 10 upgrade process Style Apps" appearance of Windows 10, don't worry, and they were faced with a screen asking them to there's a very popular FREE program called "Classic Shell" continue the Windows 10 upgrade by choosing “Next”, or that'll fix you right up. -

A Future-Focused Forensic Imager Designed to Streamline Evidence Collection Processes
A Future-Focused Forensic Imager Designed to Streamline Evidence Collection Processes Extremely fast forensic imaging speed surpassing 50GB/min. Clone PCIe to PCIe at speeds above 90GB/min Image to/from Thunderbolt™ 3/USB-C external storage enclosures with an optional I/O card. Image and verify from up to 5 source drives up to 9 destinations simultaneously Create a logical image to capture only specific files needed Concurrent Image+Verify greatly reduces duration of image plus verification process Two 10GbE connections provide fast network imaging performance Network capture feature to capture network traffic, VOIP, internet activity Multi-task. Image from multiple sources simultaneously FEATURES n The Falcon®-NEO achieves imaging speeds when imaging directly to large capacity Thunder- n Image from a Mac® computer with USB-C ports surpassing 50GB/min and can clone PCIe to PCIe bolt 3 RAID storage enclosures for evidence data using a USB-C to USB-A cable and Target Disk at speeds at over 90GB/min. collection. The card connects to the Falcon-NEO’s Mode or use Logicube’s USB boot device to n Image and verify to multiple image formats; 2 write-blocked source I/O ports or 1 destination I/O image a source drive from a Mac computer on the native copy, .dd, dmg, e01 and ex01. The Falcon- port. The I/O card does not currently support imaging same network without booting the Mac computer’s ® NEO provides MD5, SHA1, SHA256, and dual hash in TDM from Mac systems, refer to the Falcon-NEO native OS. The Falcon-NEO supports imaging from ® authentication at extremely fast speeds. -

Windows 8 Anpassen Mit Classic Shell: Fenster Statt Kacheln
Windows 8 anpassen mit Classic Shell: Fenster statt Kacheln Experten und Anwender sind sich einig: Windows 8 ist keine richtig runde Sache. Zwar bringt das aktuelle Microsoft-- System viele technische Verbesserungen. Doch seine doppelte Nutzeroberfläche kann ziemlich nerven. Classic Shell bringt das Startmenü zurück. Doch wer einen neuen Rechner braucht, muss nicht auf Windows 8.1 oder gar auf Windows 9 warten. Schon jetzt kann er mit kostenloser Zusatzsoftware Windows 8 entkacheln, sich das Startmenü zurückholen und so auch auf einem nagelneuen Windows-Rechner zur gewohnten Arbeitsweise zurückkehren. Dafür gibt es verschiedene Möglichkeiten. Eine davon ist das besonders beliebte, quelloffene Programm Classic Shell. Damit lässt sich die Windows-Oberfläche sehr vielseitig den jeweiligen Nutzervorlieben anpassen. Achtung: Diese Anleitung richtet sich zwar nicht an Voll- profis. Aber ein wenig Grundwissen über Windows wird vorausgesetzt. Wer sich unsicher ist, lässt sich beim Einrichten besser vom PC-Experten seines Vertrauens helfen. Schritt 1: Classic Shell installieren Das Programm Classic Shell ist leicht zu installieren. Damit die Menüpunkte auch in deutscher Sprache angezeigt werden, ist ein weiterer Schritt nötig. Nach erfolgreicher Installation lässt sich die Windows-Oberfläche nach Belieben anpassen. Classic Shell installieren Auswahl zwischen Programmmodulen. Das englischsprachige Installationsprogramm lässt sich auf der Startseite des Anbieters herunterladen. Nach dem Start und dem Annehmen der Lizenzvereinbarungen fragt es zunächst, welche Programmteile der Nutzer installieren will. Für die Wiedereinführung des Startmenüs und das Überspringen der Kachelansicht reicht das Modul „Classic Start Menu“. Die Module „Classic Explorer“ und „Classic IE9“ ermöglichen weitere Anpassungen des Windows Explorers und des Internet Explorers. „Classic Shell Update“ meldet dem Nutzer, wenn es eine neue Programmversion gibt. -

Mobiflage: Deniable Storage Encryption for Mobile Devices 3
TRANSACTIONS ON DEPENDABLE AND SECURE COMPUTING 1 Mobiflage: Deniable Storage Encryption for Mobile Devices Adam Skillen and Mohammad Mannan Abstract—Data confidentiality can be effectively preserved through encryption. In certain situations, this is inadequate, as users may be coerced into disclosing their decryption keys. Steganographic techniques and deniable encryption algorithms have been devised to hide the very existence of encrypted data. We examine the feasibility and efficacy of deniable encryption for mobile devices. To address obstacles that can compromise plausibly deniable encryption (PDE) in a mobile environment, we design a system called Mobiflage. Mobiflage enables PDE on mobile devices by hiding encrypted volumes within random data in a devices free storage space. We leverage lessons learned from deniable encryption in the desktop environment, and design new countermeasures for threats specific to mobile systems. We provide two implementations for the Android OS, to assess the feasibility and performance of Mobiflage on different hardware profiles. MF-SD is designed for use on devices with FAT32 removable SD cards. Our MF-MTP variant supports devices that instead share a single internal partition for both apps and user accessible data. MF-MTP leverages certain Ext4 file system mechanisms and uses an adjusted data-block allocator. These new techniques for storing hidden volumes in Ext4 file systems can also be applied to other file systems to enable deniable encryption for desktop OSes and other mobile platforms. Index Terms—File system security, Mobile platform security, Storage Encryption, Deniable encryption ✦ 1 INTRODUCTION AND MOTIVATION plaintext can be recovered by decrypting with the true key. In the event that a ciphertext is intercepted, and the Smartphones and other mobile computing devices are user is coerced into revealing the key, she may instead being widely adopted globally. -

Easypacks - Your Easyinstall® Application Portal
EasyPacks - your EasyInstall® application portal Pre-packaged software and applications for EasyInstall, ready for download. Why spend precious time to pack, update and test standard software and applica- tions when it is already done. With a few clicks you can download the latest soft- ware from EasyPacks. Errors and security vulnerabilities is constantly found in standard applications and the software supplier issues updates on a regular basis - we keep an eye on this for you .... It can be fatal if standard applications are not kept up to date. Hackers are unfor- tunately extremely talented to exploit these vulnerabilities. As an example, if Java is not updated, which in itself is a huge security risk, it can cause lack of access to banking and other public services. All software is packed, tested, virus free and quality assured by IXP Data. We have more than 150 updated application packages ready for you and more keep coming. We ensure that packets are continuously updated and we will send you an e-mail when new downloads are ready. On the EasyPacks website you can contact us with suggestion for additional standard applications for EasyPacks. EasyPacks is a subscription service which is settled by number of EasyInstall li- censes. The subscription runs for 1 year. System requirements: EasyPacks require EasyInstall version 5 or higher IXP Data ApS • Søndre Alle 9 • 4600 Køge • VAT 32749305 • 56275402 • [email protected] • www.ixpdata.com Selected application packages: Java, CutePDF, Adobe Reader, Adobe Flash Player, Apple QuickTime, -

{PDF} Start to Win: the Classic Text
START TO WIN: THE CLASSIC TEXT PDF, EPUB, EBOOK Eric Twiname | 240 pages | 26 Apr 2011 | Bloomsbury Publishing PLC | 9781408111987 | English | London, United Kingdom Start to Win: The Classic Text PDF Book Once the installer finishes, you will be greeted with the basic settings screen for Classic Shell. Skip to content. First Run Tasks are not available in LayoutModification. For Windows 10, version , Office Desktop Bridge Subscription is required on all devices where the screen is Thanks John! Absolutely works, no need for complicated malarkey. Devices that upgrade to Windows 10, version , will not experience a change to their existing Start layout. Hot Latest. Skip to main content. You can also set Windows to show a few extra tiles in each column. On the other hand, if you really like the tiles and miss the full-screen Start experience from Windows 8, you can have the Start menu always open full screen. Classics It Paperback Books. However, most users have moved on to Microsoft Edge , a more modern and robust web browser. Set the DesktopApplicationLinkPath to a path to a shortcut link. Eric Twiname was an active dinghy sailor, a keen team racer and a Laser National Champion. If you have a full HD monitor or screen with X resolution or higher then you will observe that all the icons and texts become so small that they are really hard to read unless you scale them up. Top charts. Paperback Eric Van Lustbader Books. Another option is creating a custom folder full of program shortcuts and using a toolbar that points at that folder instead. -

Deep Web for Journalists: Comms, Counter-Surveillance, Search
Deep Web for Journalists: Comms, Counter-surveillance, Search Special Complimentary Edition for Delegates attending the 28th World Congress of the International Federation of Journalists * By Alan Pearce Edited by Sarah Horner * © Alan Pearce June 2013 www.deepwebguides.com Table of Contents Introduction by the International Federation of Journalists A Dangerous Digital World What is the Deep Web and why is it useful to Journalists? How Intelligence Gathering Works How this affects Journalists 1 SECURITY ALERT . Setting up Defenses 2 Accessing Hidden Networks . Using Tor . Entry Points 3 Secure Communications . Email . Scramble Calls . Secret Messaging . Private Messaging . Deep Chat . Deep Social Networks 4 Concealed Carry 5 Hiding Things . Transferring Secret Data . Hosting, Storing and Sharing . Encryption . Steganography – hiding things inside things 6 Smartphones . Counter-Intrusion . 007 Apps 7 IP Cameras 8 Keeping out the Spies . Recommended Free Programs . Cleaning Up . Erasing History . Alternative Software Share the Knowledge About the Authors Foreword by the International Federation of Journalists Navigating the Dangerous Cyber Jungle Online media safety is of the highest importance to the International Federation of Journalists. After all, the victims are often our members. The IFJ is the world’s largest organization of journalists and our focus is on ways and means to stop physical attacks, harassment and the killing of journalists and media staff. In an age where journalism – like everything else in modern life – is dominated by the Internet, online safety is emerging as a new front. In this new war, repressive regimes now keep a prying eye on what journalists say, write and film. They want to monitor contacts and they want to suppress information. -

Mobigyges: a Mobile Hidden Volume for Preventing Data Loss, Improving Storage Utilization, and Avoiding Device Reboot
MobiGyges: A Mobile Hidden Volume for Preventing Data Loss, Improving Storage Utilization, and Avoiding Device Reboot Wendi Fenga, Chuanchang Liua, Zehua Guob,c, Thar Bakerd, Gang Wangb,c, Meng Wanga, Bo Chenga, and Junliang Chena aBeijing University of Posts and Telecommunications, 10 Xitucheng RD, 100876, Beijing, China bBeijing Institute of Technology, 5 Zhongguancun ST South, 100081, Beijing, China cUniversity of Minnesota Twin Cities, 117 Pleasant ST, 55455, Minneapolis, USA dLiverpool John Moores University, James Parson Building, Liverpool, L3 3AF, UK Abstract Sensitive data protection is essential for mobile users. Plausibly Deniable Encryption (PDE) systems provide an effective manner to protect sensitive data by hiding them on the device. However, existing PDE systems can lose data due to overriding the hidden volume, waste physical storage because of the \reserved area" used for avoiding data loss, and require device reboot when using the hidden volume. This paper presents MobiGyges, a hidden volume based mobile PDE system, to fill the gap. MobiGyges addresses the problem of data loss by restricting each storage block used only by one volume, and it improves storage utilization by eliminating the \reserved area". MobiGyges can also avoid device reboot by mounting the hidden volume dynamically on-demand with the Dynamic Mounting service. Moreover, we identify two novel PDE oriented attacks, the capacity comparison attack and the fill-to-full attack. MobiGyges can defend them by jointly leveraging the Shrunk U-disk method and multi-level deniability. We implement the MobiGyges proof-of-concept system on a real mobile phone Google Nexus 6P with LineageOS 13. Experimental results show that MobiGyges prevents data loss, avoids device reboot, improves storage utilization by over 30% with acceptable performance overhead compared with current works. -

Plus: Website Basics, Hosting & Annoyances
FEBRUARY 2014 • VOLUME 30 • ISSUE 1 Official Magazine of the MELBOURNE PC USER GROUP INC. Plus: website basics, hosting & annoyances www.melbpc.org.au MELB PC PURPOSES THE PURPOSES OF THE GROUP are to conduct, on a non-profit basis, activities aimed at the FEBRUARY 2014 • VOLUME 30 • ISSUE 1 effective utilisation of the personal computer EDITORIAL PANEL and to endeavour to achieve such effective Lance Lloyd, Charles Wright utilisation by means of: EDITOR • Advancing computer literacy Katharine Shade, CCE Design • Advancing the art and science of [email protected] information processing through ART DIRECTOR/DESIGNER education and interchange of ideas Katharine Shade, CCE Design • Keeping members abreast of developments in computing and information technology CONTRIBUTORS Stephen Lake, Harry Lewis, Lance Lloyd, and enabling members to exchange Craig Mattson, Katharine Shade, George Skarbek, information and experience Fleur Stephens, John Swale • Representing computer users in public SIG Coordinator: Norman Elliman debate and by acting and speaking on their SIG Reports: Faye Barkla, Stephen Tidswell, behalf where they would be affected by Jean de Neef, Susan Jensen, Kathy Rouse, proposed legislation or other regulatory John Sapsford measures Calendar and Maps: John Swann • Providing a forum for the exchange of views among computer users and between computer users and the computer industry • Co-operating supporting or joining with, PUBLISHED BY or in, other organisations with similar MELBOURNE PC USER GROUP INC. purposes Suite 26, Level 1, 479 Warrigal Road • Undertaking other activities beneficial to Moorabbin, VIC 3189 the Group Office hours 9am-5pm In order to further its purposes the Group shall Phone (03) 9276 4000 have the rights, powers and privileges of a Email [email protected] Office Manager Dianne Vogt natural person. -
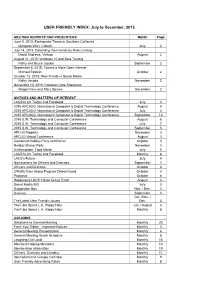
USER FRIENDLY INDEX June-Dec 2015
USER FRIENDLY INDEX: July to December, 2015 MEETING REPORTS AND PRESENTERS Month Page June 9, 2015: Earthquake Threat in Southern California Margaret Vinci, Caltech July 2 July 14, 2015: Defending the Internet by Rate Limiting David Andrews, Verizon August 2 August 11, 2015: Windows 10 and Beta Testing Kathy and Bruce Jacobs September 2 September 8. 2015: Toward a More Open Internet Michael Epstein October 2 October 13. 2015: New Trends in Social Media Kathy Jacobs November 2 November 10, 2015: Common Core Standards Megan Faux and Mary Spruce December 2 NOTICES AND MATTERS OF INTEREST LACS Is On Twitter and Facebook July 3 2015 APCXUG International Computer & Digital Technol ogy Conference August 4 2015 APCXUG International Computer & Digital Technology Conference July 3 2015 APCXUG International Computer & Digital Technology Conference September 18 2015 S.W. Technology and Computer Conference August 6 2015 S.W. Technology and Computer Conference July 7 2015 S.W. Technology and Computer Conference September 5 APCUG Reports December 3 APCUG Virtual Conference August 3 Combined Holiday Party and Dinner October 3 Holiday Dinner Party November 3 In Memoriam: Todd Martin July 5 LACS Is On Twitter and Facebook Monthly 8 LACS's Future July 4 Nominations for Officers and Directors September 3 Officers and Directors October 3 O'Reilly User Group Program Discontinued October 3 Podcasts October 8 Replying to LACS Yahoo Gro up Email August 3 Social Media SIG July 3 Suggestion Box Nov. / Dec. 3 Surveys September 3 Oct. /Nov. / The Latest User Friendly Issues Dec. 3 YouTube Space L.A. Happy Hour July / August 3 YouTube Space L.A.