Statistics in High Dimensions Without IID Samples: Truncated Statistics and Minimax Optimization Emmanouil Zampetakis
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

1.2 Examples of Descriptive Statistics in Statistics, a Summary Statistic Is a Single Numerical Measure of an At- Tribute of a Sample
Arkansas Tech University MATH 3513: Applied Statistics I Dr. Marcel B. Finan 1.2 Examples of Descriptive Statistics In Statistics, a summary statistic is a single numerical measure of an at- tribute of a sample. In this section we discuss commonly used summary statistics. Sample Mean The sample mean (also known as average or arithmetic mean) is a mea- sure of the \center" of the data. Suppose that a sample consists of the data values x1; x2; ··· ; xn: Then the sample mean is given by the formula n x1 + x2 + ··· + xn 1 X x = = x : n n i i=1 Example 1.2.1 A random sample of 10 ATU students reported missing school 7, 6, 8, 4, 2, 7, 6, 7, 6, 5 days. Find the sample mean. Solution. The sample mean is 7+6+8+4+2+7+6+7+6+5 x = = 5:8 days 10 The Sample Variance and Standard Deviation The Standard deviation is a measure of the spread of the data around the sample mean. When the spread of data is large we expect most of the sample values to be far from the mean and when the spread is small we expect most of the sample values to be close to the mean. Suppose that a sample consists of the data values x1; x2; ··· ; xn: One way of measuring how these values are spread around the mean is to compute the deviations of these values from the mean, i.e., x1 − x; x2 − x; ··· ; xn − x and then take their average, i.e., find how far, on average, is each data value from the mean. -

Chapter 4 Truncated Distributions
Chapter 4 Truncated Distributions This chapter presents a simulation study of several of the confidence intervals first presented in Chapter 2. Theorem 2.2 on p. 50 shows that the (α, β) trimmed mean Tn is estimating a parameter μT with an asymptotic variance 2 2 equal to σW /(β−α) . The first five sections of this chapter provide the theory needed to compare the different confidence intervals. Many of these results will also be useful for comparing multiple linear regression estimators. Mixture distributions are often used as outlier models. The following two definitions and proposition are useful for finding the mean and variance of a mixture distribution. Parts a) and b) of Proposition 4.1 below show that the definition of expectation given in Definition 4.2 is the same as the usual definition for expectation if Y is a discrete or continuous random variable. Definition 4.1. The distribution of a random variable Y is a mixture distribution if the cdf of Y has the form k FY (y)= αiFWi (y) (4.1) i=1 <α < , k α ,k≥ , F y where 0 i 1 i=1 i =1 2 and Wi ( ) is the cdf of a continuous or discrete random variable Wi, i =1, ..., k. Definition 4.2. Let Y be a random variable with cdf F (y). Let h be a function such that the expected value Eh(Y )=E[h(Y )] exists. Then ∞ E[h(Y )] = h(y)dF (y). (4.2) −∞ 104 Proposition 4.1. a) If Y is a discrete random variable that has a pmf f(y) with support Y,then ∞ Eh(Y )= h(y)dF (y)= h(y)f(y). -

Statistical Inference of Truncated Normal Distribution Based on the Generalized Progressive Hybrid Censoring
entropy Article Statistical Inference of Truncated Normal Distribution Based on the Generalized Progressive Hybrid Censoring Xinyi Zeng and Wenhao Gui * Department of Mathematics, Beijing Jiaotong University, Beijing 100044, China; [email protected] * Correspondence: [email protected] Abstract: In this paper, the parameter estimation problem of a truncated normal distribution is dis- cussed based on the generalized progressive hybrid censored data. The desired maximum likelihood estimates of unknown quantities are firstly derived through the Newton–Raphson algorithm and the expectation maximization algorithm. Based on the asymptotic normality of the maximum likelihood estimators, we develop the asymptotic confidence intervals. The percentile bootstrap method is also employed in the case of the small sample size. Further, the Bayes estimates are evaluated under various loss functions like squared error, general entropy, and linex loss functions. Tierney and Kadane approximation, as well as the importance sampling approach, is applied to obtain the Bayesian estimates under proper prior distributions. The associated Bayesian credible intervals are constructed in the meantime. Extensive numerical simulations are implemented to compare the performance of different estimation methods. Finally, an authentic example is analyzed to illustrate the inference approaches. Keywords: truncated normal distribution; generalized progressive hybrid censoring scheme; ex- pectation maximization algorithm; Bayesian estimate; Tierney and Kadane approximation; impor- tance sampling Citation: Zeng, X.; Gui, W. Statistical Inference of Truncated Normal 1. Introduction Distribution Based on the 1.1. Truncated Normal Distribution Generalized Progressive Hybrid Normal distribution has played a crucial role in a diversity of research fields like Entropy 2021 23 Censoring. , , 186. reliability analysis and economics, as well as many other scientific developments. -
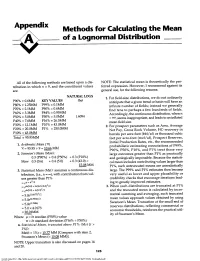
Appendix Methods for Calculating the Mean of a Lognormal Distribution
Appendix Methods for Calculating the Mean of a Lognormal Distribution All of the following methods are based upon a dis- NOTE: The statistical mean is theoretically the pre- tribution in which n = 9, and the constituent values ferred expression. However, I recommend against its are: general use, for the following reasons: NATURAL LOGS 1. For field-size distributions, we do not ordinarily P900/0 = 0.6MM KEY VALUES (In) anticipate that a given trend or basin will have an P800/0 = 1.25MM P99% = O.lMM infinite number of fields; instead we generally P700/0 = 2.1MM P900/0 = 0.6MM find tens to perhaps a few hundreds of fields. P600/0 = 3.3MM P84% = 0.95MM Accordingly, the continuous distribution, when n P500/0 = 5.0MM P500/0 = 5.0MM 1.6094 = 00, seems inappropriate, and leads to an inflated P400/0 = 7.6MM PI6% = 26.5MM mean field size. P300/0 = 12.1MM P100/0 = 43.0MM 2. For prospect parameters such as Area, Average P200/0 = 20.0MM PI% = 250.0MM Net Pay, Gross Rock Volume, HC-recovery in P100/0 = 43.0MM barrels per acre-foot (bbl/af) or thousand cubic Total = 95.95MM feet per acre-foot (mcf/ af), Prospect Reserves, Initial Production Rates, etc., the recommended 1. Arithmetic Mean (x) probabilistic estimating connotations of P99%, x = 95.95 + 9 = 10.66 MM P900/0, P500/0, P100/0, and PI% treat those very 2. Swanson's Mean (Msw): 0 0 0 large outcomes greater than PI% as practically 0.3 (P90 /0) + 0.4 (P50 /0) + 0.3 (P10 /0) and geologically impossible. -

Measures of Average and Spread
Statistical literacy guide Measures of average and spread Last updated: February 2007 Author: Richard Cracknell Am I typical? A common way of summarising figures is to present an average. Suppose, for example, we wanted to look at incomes in the UK the most obvious summary measurement to use would be average income. Another indicator which might be of use is one which showed the spread or variation in individual incomes. Two countries might have similar average incomes, but the distribution around their average might be very different and it could be useful to have a measure which quantifies this difference. There are three often-used measures of average: • Mean – what in everyday language would think of as the average of a set of figures. • Median – the ‘middle’ value of a dataset. • Mode – the most common value Mean This is calculated by adding up all the figures and dividing by the number of pieces of data. So if the hourly rate of pay for 5 employees was as follows: £5.50, £6.00, £6.45, £7.00, £8.65 The average hourly rate of pay per employee is 5.5+6.0+6.45+7.0+8.65 = 33.6 = £6.72 5 5 It is important to note that this measure can be affected by unusually high or low values in the dataset and the mean may result in a figure that is not necessarily typical. For example, in the above data, if the individual earning £8.65 per hour had instead earned £30 the mean earnings would have been £10.99 per hour – which would not have been typical of those of the group. -

Re-Establishing the Theoretical Foundations of a Truncated Normal Distribution: Standardization Statistical Inference, and Convolution Jinho Cha Clemson University
Clemson University TigerPrints All Dissertations Dissertations 8-2015 Re-Establishing the Theoretical Foundations of a Truncated Normal Distribution: Standardization Statistical Inference, and Convolution Jinho Cha Clemson University Follow this and additional works at: https://tigerprints.clemson.edu/all_dissertations Recommended Citation Cha, Jinho, "Re-Establishing the Theoretical Foundations of a Truncated Normal Distribution: Standardization Statistical Inference, and Convolution" (2015). All Dissertations. 1793. https://tigerprints.clemson.edu/all_dissertations/1793 This Dissertation is brought to you for free and open access by the Dissertations at TigerPrints. It has been accepted for inclusion in All Dissertations by an authorized administrator of TigerPrints. For more information, please contact [email protected]. RE-ESTABLISHING THE THEORETICAL FOUNDATIONS OF A TRUNCATED NORMAL DISTRIBUTION: STANDARDIZATION, STATISTICAL INFERENCE, AND CONVOLUTION A Dissertation Presented to the Graduate School of Clemson University In Partial Fulfillment of the Requirements for the Degree Doctor of Philosophy Industrial Engineering by Jinho Cha August 2015 Accepted by: Dr. Byung Rae Cho, Committee Chair Dr. Julia L. Sharp, Committee Co-chair Dr. Joel Greenstein Dr. David Neyens ABSTRACT There are special situations where specification limits on a process are implemented externally, and the product is typically reworked or scrapped if its performance does not fall in the range. As such, the actual distribution after inspection is truncated. Despite the practical importance of the role of a truncated distribution, there has been little work on the theoretical foundation of standardization, inference theory, and convolution. The objective of this research is three-fold. First, we derive a standard truncated normal distribution and develop its cumulative probability table by standardizing a truncated normal distribution as a set of guidelines for engineers and scientists. -

Mean Estimation and Regression Under Heavy-Tailed Distributions—A
Mean estimation and regression under heavy-tailed distributions—a survey * Gabor´ Lugosi†‡§ Shahar Mendelson ¶ June 12, 2019 Abstract We survey some of the recent advances in mean estimation and regression function estimation. In particular, we describe sub-Gaussian mean estimators for possibly heavy-tailed data both in the univariate and multivariate settings. We focus on estimators based on median-of-means techniques but other meth- ods such as the trimmed mean and Catoni’s estimator are also reviewed. We give detailed proofs for the cornerstone results. We dedicate a section on sta- tistical learning problems–in particular, regression function estimation–in the presence of possibly heavy-tailed data. AMS Mathematics Subject Classification: 62G05, 62G15, 62G35 Key words: mean estimation, heavy-tailed distributions, robustness, regression function estimation, statistical learning. arXiv:1906.04280v1 [math.ST] 10 Jun 2019 * Gabor´ Lugosi was supported by the Spanish Ministry of Economy and Competitiveness, Grant MTM2015-67304-P and FEDER, EU, by “High-dimensional problems in structured probabilistic models - Ayudas Fundacion´ BBVA a Equipos de Investigacion´ Cientifica 2017” and by “Google Focused Award Algorithms and Learning for AI”. Shahar Mendelson was supported in part by the Israel Science Foundation. †Department of Economics and Business, Pompeu Fabra University, Barcelona, Spain, ga- [email protected] ‡ICREA, Pg. Llus Companys 23, 08010 Barcelona, Spain §Barcelona Graduate School of Economics ¶Mathematical Sciences Institute, The Australian National University and LPSM, Sorbonne Uni- versity, [email protected] 1 Contents 1 Introduction 2 2 Estimating the mean of a real random variable 3 2.1 The median-of-means estimator . -

Limited Dependent Variables—Truncation, Censoring, and Sample Selection
19 LIMITED DEPENDENT VARIABLes—TRUNCATION, CENSORING, AND SAMP§LE SELECTION 19.1 INTRODUCTION This chapter is concerned with truncation and censoring. As we saw in Section 18.4.6, these features complicate the analysis of data that might otherwise be amenable to conventional estimation methods such as regression. Truncation effects arise when one attempts to make inferences about a larger population from a sample that is drawn from a distinct subpopulation. For example, studies of income based on incomes above or below some poverty line may be of limited usefulness for inference about the whole population. Truncation is essentially a characteristic of the distribution from which the sample data are drawn. Censoring is a more common feature of recent studies. To continue the example, suppose that instead of being unobserved, all incomes below the poverty line are reported as if they were at the poverty line. The censoring of a range of values of the variable of interest introduces a distortion into conventional statistical results that is similar to that of truncation. Unlike truncation, however, censoring is a feature of the sample data. Presumably, if the data were not censored, they would be a representative sample from the population of interest. We will also examine a form of truncation called the sample selection problem. Although most empirical work in this area involves censoring rather than truncation, we will study the simpler model of truncation first. It provides most of the theoretical tools we need to analyze models of censoring and sample selection. The discussion will examine the general characteristics of truncation, censoring, and sample selection, and then, in each case, develop a major area of application of the principles. -

Mean-Variance Policy for Discrete-Time Cone Constrained
MEAN-VARIANCE POLICY FOR DISCRETE-TIME CONE CONSTRAINED MARKETS: TIME CONSISTENCY IN EFFICIENCY AND MINIMUM-VARIANCE SIGNED SUPERMARTINGALE MEASURE∗ Xiangyu Cui,† Duan Li‡ and Xun Li§ October 30, 2018 The discrete-time mean-variance portfolio selection formulation, a representative of gen- eral dynamic mean-risk portfolio selection problems, does not satisfy time consistency in efficiency (TCIE) in general, i.e., a truncated pre-committed efficient policy may become in- efficient when considering the corresponding truncated problem, thus stimulating investors’ irrational investment behavior. We investigate analytically effects of portfolio constraints on time consistency of efficiency for convex cone constrained markets. More specifically, we de- rive the semi-analytical expressions for the pre-committed efficient mean-variance policy and the minimum-variance signed supermartingale measure (VSSM) and reveal their close rela- tionship. Our analysis shows that the pre-committed discrete-time efficient mean-variance policy satisfies TCIE if and only if the conditional expectation of VSSM’s density (with re- spect to the original probability measure) is nonnegative, or once the conditional expectation becomes negative, it remains at the same negative value until the terminal time. Our findings indicate that the property of time consistency in efficiency only depends on the basic mar- ket setting, including portfolio constraints, and this fact motivates us to establish a general solution framework in constructing TCIE dynamic portfolio selection problem formulations by introducing suitable portfolio constraints. arXiv:1403.0718v1 [q-fin.PM] 4 Mar 2014 Key Words: cone constrained market, discrete-time mean-variance policy, time consistency in efficiency, minimum-variance signed supermartingale measure ∗This research work was partially supported by Research Grants Council of Hong Kong under grants 414808, 414610 and 520412, National Natural Science Foundation of China under grant 71201094, and Shanghai Pujiang Program of China under grant 12PJC051. -

1986: Estimation of the Mean from Censored Income Data
ESTIMATION OF ~E ~N FROM C~SOHED IN~ DATA Sandra A. West, Bureau of Labor Statistics from censored data. One way to approach this I. ~CTION problem is to fit a theoretical distribution to In recent years economists and sociologists the upper portion of the observed income have increasingly become interested in the distribution and then determine the conditional study of income attainment and income mean of the upper tail. An estimator of this inequality as is reflected by the growing conditional mean will be referred to as a tail numbers of articles which treat an individual's estimator. In this paper a truncated Pareto income as the phenomenum to be explained. Some distribution is used and a modified maximum research on income have Included the likelihood estimator is developed for the investigation of the effects of status group Pareto parameter. Other estimators of the membership on income attainment and inequality: Pareto parameter are also considered. In the determinants of racial or ethnic particular it is shown that the estimator most inequality; the determinants of gender used in applications can lead to very inequality; and the determinants of income and misleading results. In order to see the effect wealth attainment in old age. of the tail estimator, six actual populations, Although many of the studies used census consisting of income data that were not data, research on income has come increasingly censored, were considered. Different estimates to rely on data from social surveys. The use of the tail and overall mean were compared to of survey data in the study of income can the true values for twenty subpopulations. -

Robust Multivariate Mean Estimation: the Optimality of Trimmed Mean
Submitted to the Annals of Statistics ROBUST MULTIVARIATE MEAN ESTIMATION: THE OPTIMALITY OF TRIMMED MEAN By Gabor´ Lugosi∗,y,z,x, and Shahar Mendelson{ ICREAy, Pompeu Fabra Universityz, Barcelona GSEx, The Australian National University{ We consider the problem of estimating the mean of a random vector based on i.i.d. observations and adversarial contamination. We introduce a multivariate extension of the trimmed-mean estimator and show its optimal performance under minimal conditions. 1. Introduction. Estimating the mean of a random vector based on independent and identically distributed samples is one of the most basic statistical problems. In the last few years the problem has attracted a lot of attention and important advances have been made both in terms of statis- tical performance and computational methodology. In the simplest form of the mean estimation problem, one wishes to es- d timate the expectation µ = EX of a random vector X taking values in R , based on a sample X1;:::;XN consisting of independent copies of X. An estimator is a (measurable) function of the data d µb = µb(X1;:::;XN ) 2 R : We measure the quality of an estimator by the distribution of its Euclidean distance to the mean vector µ. More precisely, for a given δ > 0|the confi- dence parameter|, one would like to ensure that kµb − µk ≤ "(N; δ) with probability at least 1 − δ with "(N; δ) as small as possible. Here and in the entire article, k · k denotes d the Euclidean norm in R . −1 PN The obvious choice of µb is the empirical mean N i=1 Xi, which, apart from its computational simplicity, has good statistical properties when the distribution is sufficiently well-behaved. -

Typical Values and Measures of Variability
Typical values and Measures of variability Helgi Thorsson Reykjavik University Notes to Methodology, T-701-Rem4 September 9, 2007 1 Introduction Some of the most elementary topics of Statistics deal with de¯ning and com- puting typical values for a data set, as well as measures of variability among the data. These are used in descriptive statistics to summarize a data set as well as to describe parameters of statistical models. 2 Typical values The mean (or average, depending on context) is what everybody gets if every- thing is put together and distributed evenly. Sometimes this has a concrete meaning, but often the mean should be looked upon as a normalised sum. The average class of (say) 25.2 pupils is nowhere to be found. The close relationship to the sum of all the values is evident from the de¯nition of the average of the mumbers x1; x2; ¢ ¢; x ¢i; ¢ ¢; x ¢n: x + x + ¢ ¢+ ¢x + ¢ ¢+ ¢x 1 Xn x¹ = 1 2 i n = x n n i i=1 The median is the value in the middle when the dataset is ordered by size. The most common notation for the median is x. For an even number of values, the median is not well de¯ned, any value in the middle interval is a median. A classic solution is to use the mean of the two adjacent values. If the arithmetic mean is in the middle interval, it may also be used as a median. The mean and the median are related through the concept of truncated mean. A certain number or a certain proportion of the largest and smallest values are dropped from the data before the mean is computed.