Contributor's Guidelines
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Red Hat Enterprise Linux 6 Developer Guide
Red Hat Enterprise Linux 6 Developer Guide An introduction to application development tools in Red Hat Enterprise Linux 6 Dave Brolley William Cohen Roland Grunberg Aldy Hernandez Karsten Hopp Jakub Jelinek Developer Guide Jeff Johnston Benjamin Kosnik Aleksander Kurtakov Chris Moller Phil Muldoon Andrew Overholt Charley Wang Kent Sebastian Red Hat Enterprise Linux 6 Developer Guide An introduction to application development tools in Red Hat Enterprise Linux 6 Edition 0 Author Dave Brolley [email protected] Author William Cohen [email protected] Author Roland Grunberg [email protected] Author Aldy Hernandez [email protected] Author Karsten Hopp [email protected] Author Jakub Jelinek [email protected] Author Jeff Johnston [email protected] Author Benjamin Kosnik [email protected] Author Aleksander Kurtakov [email protected] Author Chris Moller [email protected] Author Phil Muldoon [email protected] Author Andrew Overholt [email protected] Author Charley Wang [email protected] Author Kent Sebastian [email protected] Editor Don Domingo [email protected] Editor Jacquelynn East [email protected] Copyright © 2010 Red Hat, Inc. and others. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/. In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. -

Atmospheric Modelling and HPC
Atmospheric Modelling and HPC Graziano Giuliani ICTP – ESP Trieste, 1 October 2015 NWP and Climate Codes ● Legacy code from the '60 : FORTRAN language ● Path and Dynamic Libraries ● Communication Libraries ● I/O format Libraries ● Data analysis tools and the data deluge http://clima-dods.ictp.it/Workshops/smr2761 Materials ● This presentation: – atmospheric_models_and_hpc.pdf ● Codes: – codes.tar.gz ● Download both, uncompress codes: – cp codes.tar.gz /scratch – cd /scratch – tar zxvf codes.tar.gz Legacy code ● Numerical Weather Prediction uses mathematical models of the atmosphere and oceans to predict the weather based on current weather conditions. ● MOST of the NWP and climate codes can push their roots back in the 1960-1970 ● The NWP problem was one of the target problem which led to the Computer Era: the ENIAC was used to create the first weather forecasts via computer in 1950. ● Code grows by ACCRETION FORTRAN and FortranXX ● Fortran Programming Language is a general-purpose, imperative programming language that is especially suited to numeric computation and scientific computing. ● Originally developed by IBM in the 1950s for scientific and engineering applications ● Its standard is controlled by an ISO comitee: the most recent standard, ISO/IEC 1539-1:2010, informally known as Fortran 2008, was approved in September 2010. ● Needs a compiler to translate code into executable Fortran Compilers ● http://fortranwiki.org ● Most of the High Performance Compilers are Commercial, and “SuperComputer” vendors usually provide their HIGH OPTIMIZED version of Fortran Compiler. ● Some part of the Standard are left “COMPILER SPECIFIC”, opening for incompatibility among the binary formats produced by different compilers. The Fortran .mod files ● Fortran 90 introduced into the language the modules: module my_mod contains subroutine mysub(a,b) real , intent(in) :: a real , intent(out) :: b end subroutine mysub end module my_mod ● The compiler creates the object file and a .mod file compiling the above code. -

FIPS 140-2 Non-Proprietary Security Policy Oracle Linux 7 Kernel Crypto
FIPS 140-2 Non-Proprietary Security Policy Oracle Linux 7 Kernel Crypto API Cryptographic Module FIPS 140-2 Level 1 Validation Software Version: R7-2.0.0 Date: December 7, 2018 Document Version 1.1 ©Oracle Corporation This document may be reproduced whole and intact including the Copyright notice. Title: Oracle Linux 7 Kernel Crypto API Cryptographic Module Security Policy December 07, 2018 Author: Atsec Information Security Contributing Authors: Oracle Linux Engineering Oracle Security Evaluations – Global Product Security Oracle Corporation World Headquarters 500 Oracle Parkway Redwood Shores, CA 94065 U.S.A. Worldwide Inquiries: Phone: +1.650.506.7000 Fax: +1.650.506.7200 oracle.com Copyright © 2018, Oracle and/or its affiliates. All rights reserved. This document is provided for information purposes only and the contents hereof are subject to change without notice. This document is not warranted to be error-free, nor subject to any other warranties or conditions, whether expressed orally or implied in law, including implied warranties and conditions of merchantability or fitness for a particular purpose. Oracle specifically disclaim any liability with respect to this document and no contractual obligations are formed either directly or indirectly by this document. This document may reproduced or distributed whole and intact including this copyright notice. Oracle and Java are registered trademarks of Oracle and/or its affiliates. Other names may be trademarks of their respective owners. Oracle Linux 7 Kernel Crypto API Cryptographic -

CCPP Technical Documentation Release V3.0.0
CCPP Technical Documentation Release v3.0.0 J. Schramm, L. Bernardet, L. Carson, G. Firl, D. Heinzeller, L. Pan, and M. Zhang Jun 17, 2019 For referencing this document please use: Schramm, J., L. Bernardet, L. Carson, G. Firl, D. Heinzeller, L. Pan, and M. Zhang, 2019. CCPP Technical Documentation Release v3.0.0. 91pp. Available at https://dtcenter.org/GMTB/v3.0/ccpp_tech_guide.pdf. CONTENTS 1 CCPP Overview 1 1.1 How to Use this Document........................................4 2 CCPP-Compliant Physics Parameterizations7 2.1 General Rules..............................................8 2.2 Input/output Variable (argument) Rules.................................9 2.3 Coding Rules............................................... 10 2.4 Parallel Programming Rules....................................... 11 2.5 Scientific Documentation Rules..................................... 12 2.5.1 Doxygen Comments and Commands.............................. 12 2.5.2 Doxygen Documentation Style................................. 13 2.5.3 Doxygen Configuration..................................... 18 2.5.4 Using Doxygen......................................... 20 3 CCPP Configuration and Build Options 23 4 Constructing Suites 27 4.1 Suite Definition File........................................... 27 4.1.1 Groups............................................. 27 4.1.2 Subcycling........................................... 27 4.1.3 Order of Schemes........................................ 28 4.2 Interstitial Schemes........................................... 28 4.3 SDF Examples............................................. -

Namespacing in Selinux
Namespacing in SELinux Linux.conf.au 2018 Sydney, Australia James Morris [email protected] Introduction ● Who am I? – Linux security subsystem maintainer ● Previously: Crypto API, Netfilter, SELinux, LSM, IPSec, MCS, sVirt ● Recovering manager ● blog.namei.org ● @xjamesmorris ● Overview – Briefly review technologies – Discuss requirements – SELinux namespace prototype – Current work: inode labeling – Future work SELinux ● Label-based mandatory access control (MAC) – Set security labels on: ● Subjects ● Objects – Define permissions – Centrally managed policy – Enforced by kernel ● Generalized ● Separation of policy and mechanism Linux Security Modules (LSM) ● Kernel API for access control ● Hooks – Located at security decision points – All security relevant information available – Race-free ● Kind of like Netfilter but for the whole kernel ● Pluggable: Smack, SELinux, AppArmor etc. Linux Namespaces ● Private views of global resources – mount, network, ipc, pid, user, uts, cgroup ● APIs: clone(2), setns(2), unshare(2) ● See also: pam_namespace(8) ● Uses: – Sandboxes – Containers – Multi-level security (!) ● No namespacing of LSM or other security APIs Containers ● Not a Thing ™ ● Actually namespaces + cgroups + magic – Docker, lxc, lxd etc. ● Very popular ● Kernel security APIs not containerized, e.g. – Limits functionality for OS-like containers – SELinux on Fedora-based distros pretends to be disabled inside container, and yet … ! Use Cases ● Enable SELinux confinement within a container – Currently runs as one global label and appears -

The Glib/GTK+ Development Platform
The GLib/GTK+ Development Platform A Getting Started Guide Version 0.8 Sébastien Wilmet March 29, 2019 Contents 1 Introduction 3 1.1 License . 3 1.2 Financial Support . 3 1.3 Todo List for this Book and a Quick 2019 Update . 4 1.4 What is GLib and GTK+? . 4 1.5 The GNOME Desktop . 5 1.6 Prerequisites . 6 1.7 Why and When Using the C Language? . 7 1.7.1 Separate the Backend from the Frontend . 7 1.7.2 Other Aspects to Keep in Mind . 8 1.8 Learning Path . 9 1.9 The Development Environment . 10 1.10 Acknowledgments . 10 I GLib, the Core Library 11 2 GLib, the Core Library 12 2.1 Basics . 13 2.1.1 Type Definitions . 13 2.1.2 Frequently Used Macros . 13 2.1.3 Debugging Macros . 14 2.1.4 Memory . 16 2.1.5 String Handling . 18 2.2 Data Structures . 20 2.2.1 Lists . 20 2.2.2 Trees . 24 2.2.3 Hash Tables . 29 2.3 The Main Event Loop . 31 2.4 Other Features . 33 II Object-Oriented Programming in C 35 3 Semi-Object-Oriented Programming in C 37 3.1 Header Example . 37 3.1.1 Project Namespace . 37 3.1.2 Class Namespace . 39 3.1.3 Lowercase, Uppercase or CamelCase? . 39 3.1.4 Include Guard . 39 3.1.5 C++ Support . 39 1 3.1.6 #include . 39 3.1.7 Type Definition . 40 3.1.8 Object Constructor . 40 3.1.9 Object Destructor . -

Speeding up Linux Disk Encryption Ignat Korchagin @Ignatkn $ Whoami
Speeding Up Linux Disk Encryption Ignat Korchagin @ignatkn $ whoami ● Performance and security at Cloudflare ● Passionate about security and crypto ● Enjoy low level programming @ignatkn Encrypting data at rest The storage stack applications @ignatkn The storage stack applications filesystems @ignatkn The storage stack applications filesystems block subsystem @ignatkn The storage stack applications filesystems block subsystem storage hardware @ignatkn Encryption at rest layers applications filesystems block subsystem SED, OPAL storage hardware @ignatkn Encryption at rest layers applications filesystems LUKS/dm-crypt, BitLocker, FileVault block subsystem SED, OPAL storage hardware @ignatkn Encryption at rest layers applications ecryptfs, ext4 encryption or fscrypt filesystems LUKS/dm-crypt, BitLocker, FileVault block subsystem SED, OPAL storage hardware @ignatkn Encryption at rest layers DBMS, PGP, OpenSSL, Themis applications ecryptfs, ext4 encryption or fscrypt filesystems LUKS/dm-crypt, BitLocker, FileVault block subsystem SED, OPAL storage hardware @ignatkn Storage hardware encryption Pros: ● it’s there ● little configuration needed ● fully transparent to applications ● usually faster than other layers @ignatkn Storage hardware encryption Pros: ● it’s there ● little configuration needed ● fully transparent to applications ● usually faster than other layers Cons: ● no visibility into the implementation ● no auditability ● sometimes poor security https://support.microsoft.com/en-us/help/4516071/windows-10-update-kb4516071 @ignatkn Block -

Red Hat Enterprise Linux Kernel Crypto API Cryptographic Module V4.0
Red Hat Enterprise Linux Kernel Crypto API Cryptographic Module v4.0 FIPS 140-2 Non-Proprietary Security Policy Version 1.2 Last update: 2016-08-29 Prepared by: atsec information security corporation 9130 Jollyville Road, Suite 260 Austin, TX 78759 www.atsec.co m ©2016 Red Hat Enterprise Linux / atsec information security corporation Page 1 of 24 This document can be reproduced and distributed only whole and intact, including this copyright notice. Red Hat Enterprise Linux Kernel Crypto API Cryptographic Module v4.0 FIPS 140-2 Non-Proprietary Security Policy Table of Contents 1Cryptographic Module Specification........................................................................................4 1.1Module Overview...........................................................................................................4 1.2FIPS 140-2 validation.....................................................................................................6 1.3Modes of Operations......................................................................................................7 2Cryptographic Module Ports and Interfaces.............................................................................8 3Roles, Services and Authentication.........................................................................................9 3.1Roles.............................................................................................................................. 9 3.2Services........................................................................................................................ -

Demystifying Internet of Things Security Successful Iot Device/Edge and Platform Security Deployment — Sunil Cheruvu Anil Kumar Ned Smith David M
Demystifying Internet of Things Security Successful IoT Device/Edge and Platform Security Deployment — Sunil Cheruvu Anil Kumar Ned Smith David M. Wheeler Demystifying Internet of Things Security Successful IoT Device/Edge and Platform Security Deployment Sunil Cheruvu Anil Kumar Ned Smith David M. Wheeler Demystifying Internet of Things Security: Successful IoT Device/Edge and Platform Security Deployment Sunil Cheruvu Anil Kumar Chandler, AZ, USA Chandler, AZ, USA Ned Smith David M. Wheeler Beaverton, OR, USA Gilbert, AZ, USA ISBN-13 (pbk): 978-1-4842-2895-1 ISBN-13 (electronic): 978-1-4842-2896-8 https://doi.org/10.1007/978-1-4842-2896-8 Copyright © 2020 by The Editor(s) (if applicable) and The Author(s) This work is subject to copyright. All rights are reserved by the Publisher, whether the whole or part of the material is concerned, specifically the rights of translation, reprinting, reuse of illustrations, recitation, broadcasting, reproduction on microfilms or in any other physical way, and transmission or information storage and retrieval, electronic adaptation, computer software, or by similar or dissimilar methodology now known or hereafter developed. Open Access This book is licensed under the terms of the Creative Commons Attribution 4.0 International License (http://creativecommons.org/licenses/by/4.0/), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license and indicate if changes were made. The images or other third party material in this book are included in the book’s Creative Commons license, unless indicated otherwise in a credit line to the material. -

Release 0.11 Todd Gamblin
Spack Documentation Release 0.11 Todd Gamblin Feb 07, 2018 Basics 1 Feature Overview 3 1.1 Simple package installation.......................................3 1.2 Custom versions & configurations....................................3 1.3 Customize dependencies.........................................4 1.4 Non-destructive installs.........................................4 1.5 Packages can peacefully coexist.....................................4 1.6 Creating packages is easy........................................4 2 Getting Started 7 2.1 Prerequisites...............................................7 2.2 Installation................................................7 2.3 Compiler configuration..........................................9 2.4 Vendor-Specific Compiler Configuration................................ 13 2.5 System Packages............................................. 16 2.6 Utilities Configuration.......................................... 18 2.7 GPG Signing............................................... 20 2.8 Spack on Cray.............................................. 21 3 Basic Usage 25 3.1 Listing available packages........................................ 25 3.2 Installing and uninstalling........................................ 42 3.3 Seeing installed packages........................................ 44 3.4 Specs & dependencies.......................................... 46 3.5 Virtual dependencies........................................... 50 3.6 Extensions & Python support...................................... 53 3.7 Filesystem requirements........................................ -

The Central Control Room Man-Machine Interface at the Clinton P
© 1973 IEEE. Personal use of this material is permitted. However, permission to reprint/republish this material for advertising or promotional purposes or for creating new collective works for resale or redistribution to servers or lists, or to reuse any copyrighted component of this work in other works must be obtained from the IEEE. THE CENTRAL CONTROL ROOM MAN-MACHINE INTERFACE AT THE CLINTON P. ANDERSON MESON PHYSICS FACILITY (LAMPF)* B. L. Hartway, J. Bergstein, C. M. Plopper University of California Los Alamos Scientific Laboratory Los Alamos, New Mexico Summary tial that the data be organized and displayed for the operator in a format which quickly conveyed the status The control system for the Clinton P. Anderson of the whole accelerator or any subsystems under study. Meson Physics Facility (LAMPF) is organized around an Similarly, there had to be a simple but flexible scheme on-line digital computer. Accelerator operations are for the operator to manipulate the various controls. conducted from the Central Control Room (CCR) where two The experience gained from the prototype console identical but independent operator consoles provide the was incorporated in the design for the LAMPF operator's This paper traces the evolution man-machine interface. console. A mockup of the console was built and evalu- of the man-machine interface from the initial concepts ated from many points of view. Several human-factor Special emphasis is given of a computer control system. studies were performed to determine the optimum shape of to the human factors which influenced the development. the console and the location for various controls. -
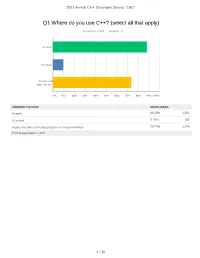
Q1 Where Do You Use C++? (Select All That Apply)
2021 Annual C++ Developer Survey "Lite" Q1 Where do you use C++? (select all that apply) Answered: 1,870 Skipped: 3 At work At school In personal time, for ho... 0% 10% 20% 30% 40% 50% 60% 70% 80% 90% 100% ANSWER CHOICES RESPONSES At work 88.29% 1,651 At school 9.79% 183 In personal time, for hobby projects or to try new things 73.74% 1,379 Total Respondents: 1,870 1 / 35 2021 Annual C++ Developer Survey "Lite" Q2 How many years of programming experience do you have in C++ specifically? Answered: 1,869 Skipped: 4 1-2 years 3-5 years 6-10 years 10-20 years >20 years 0% 10% 20% 30% 40% 50% 60% 70% 80% 90% 100% ANSWER CHOICES RESPONSES 1-2 years 7.60% 142 3-5 years 20.60% 385 6-10 years 20.71% 387 10-20 years 30.02% 561 >20 years 21.08% 394 TOTAL 1,869 2 / 35 2021 Annual C++ Developer Survey "Lite" Q3 How many years of programming experience do you have overall (all languages)? Answered: 1,865 Skipped: 8 1-2 years 3-5 years 6-10 years 10-20 years >20 years 0% 10% 20% 30% 40% 50% 60% 70% 80% 90% 100% ANSWER CHOICES RESPONSES 1-2 years 1.02% 19 3-5 years 12.17% 227 6-10 years 22.68% 423 10-20 years 29.71% 554 >20 years 34.42% 642 TOTAL 1,865 3 / 35 2021 Annual C++ Developer Survey "Lite" Q4 What types of projects do you work on? (select all that apply) Answered: 1,861 Skipped: 12 Gaming (e.g., console and..