Devices That Tell on You: the Nike+Ipod Sport Kit
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ipod Nano Features Guide
iPod nano Features Guide 2 Contents Chapter 1 4 iPod nano Basics 5 iPod nano at a Glance 5 Using iPod nano Controls 7 Disabling iPod nano Buttons 8 Using iPod nano Menus 9 Connecting and Disconnecting iPod nano Chapter 2 14 Music Features 14 About iTunes 15 Importing Music Into Your Computer 19 Organizing Your Music 20 Downloading Music and Podcasts From Your Computer to iPod nano 24 Playing Music 25 Listening to Podcasts 25 Listening to Spoken Word Audio 26 Adjusting iPod nano Settings Chapter 3 30 Photo Features 30 Downloading Photos 33 Viewing Photos and Other Images Chapter 4 35 Extra Features and Accessories 35 Using iPod nano as an External Disk 36 Using Extra Settings 39 Importing Contacts, Calendars, and To-Do Lists 41 Storing and Reading Notes 42 Learning About iPod nano Accessories 2 Chapter 5 43 Tips and Troubleshooting 43 General Suggestions 47 Updating and Restoring iPod Software Chapter 6 49 Safety and Cleaning 49 Setup Safety Instructions 49 General Safety, Cleaning, and Handling Guidelines Chapter 7 51 Learning More, Service, and Support Index 54 Contents 3 1 iPod nano Basics 1 Congratulations on purchasing your iPod nano. Read this section to learn about the features of your iPod nano, how to use its controls, and more. To use iPod nano, you put music, photos, and other files on your computer and then download them to iPod nano. iPod nano is a music player and much more. With iPod nano, you can:  Store hundreds of songs and digital photos for listening and viewing on the go  Listen to podcasts, downloadable radio-style -

8.11.15 Hied K12 3PP Price List
Apple Inc. K-12 and Higher Education Institution US Only Third-Party Products: Software Licensing and Hardware Price List August 11, 2015 Table Of Contents Page • How to Order 1 • Revisions to the Price List 1-3 SECTION A: THIRD-PARTY HARDWARE 3-20 • Bags & Cases 3-6 • Cables 6-7 • Carts, Mounts & Stands 7-9 • Digital Cameras 9 • Headphones 9-10 15-16 • Input Devices 10-11 • iPad Accessories 11-12 • iPad Cases 12-13 • iPhone/iPod Accessories 13-14 • iPhone Cases 14-16 • iPod Cases 16 • Music Creation 16 -17 • Networking 17 • Printers 17 • Printer Supplies Note: Printer supplies are no longer offered through Apple 17 • Projectors & Presentation 17 • Scanners 17 • Security & More 17-18 • Server Accessories 18-19 • Speakers & Audio 19 • Storage 19-20 SECTION B: THIRD-PARTY SOFTWARE LICENSING 20-29 • Creativity & Productivity Tools 20-21 • IT Infrastructure & Learning Services 21-26 • IT Infrastructure & Wireless Networking Products 26-31 SECTION C: FOR MORE INFORMATION 28-29 • Apple Store for Education 29 • Third-Party Websites 29 • Third-Party Sales Policies 29 • Third-Party Products and Ship-Complete Orders 29 HOW TO ORDER Many of the products on this price list are available to order online from the Apple Store for Education: www.apple.com/education/store or 800-800-2775 Purchase orders for all products may be submitted to: Apple Inc. Attn: Apple Education Sales Support 12545 Riata Vista Circle Mail Stop: 198-3ED Austin, TX 78727-6524 Phone: 1-800-800-2775 Fax: (800) 590-0063 IMPORTANT INFORMATION REGARDING ORDERING THIRD PARTY SOFTWARE LICENSING Contact Information: End-user (or, tech coordinator) contact information is required in order to fulfill orders for third party software licensing. -

GUD01 Datasheet
GUD01 Charge & Sync Cable, 3.3ft (1m) - USB to 30-Pin Cable Designed as a replacement for factory Apple® Dock Cables or as an additional cable to keep in the office, car, backpack or briefcase, IOGEAR's super flexible Charge n' Sync USB to 30-Pin cables meet or exceed OEM cable standards for performance without being stiff or difficult to coil. High-grade materials enable thinner construction, and make for a non-bulky, tangle-free cable. IOGEAR Charge n' Sync USB to 30-Pin cables are compatible with all Apple USB chargers, computer USB ports, and aftermarket USB chargers with built-in compatibility for iPod®/iPhone®/iPad®. All of IOGEAR's Lightning and 30-Pin cables are Apple MFi certified to work with every device compatible with the original Apple supplied cable. Non-certified cables can have out of spec connectors and imitation processors which can damage your device, so always makes sure you a purchasing an actual Apple Authorized cable like the those available from IOGEAR! Compatible with USB compatible Apple 30-pin devices Strain relieved connectors for maximum durability Super flexible cable 3.3ft (1 meter) length Stain resistant, easy grip cable jacket Requirements Package Contents USB compatible iOS device with 30-pin Dock Connector 1 x 3.3ft (1 Meter) 30-pin cable Compatible Devices: iPhone models: iPhone 3G iPhone 3GS iPhone 4 iPhone 4S iPad models: iPad (1st generation) iPad 2 (2nd generation) iPad (3rd generation) iPod models: iPod 3rd Generation* iPod 4th Generation iPod photo 4th Generation iPod color 4th Generation iPod -
API Diagrams
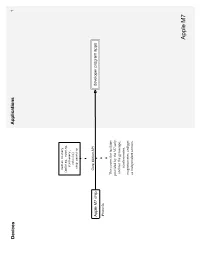
Devices Applications 1 motion history (walking, running, stationary, vehicle) step counting Core Motion API Apple M7 chip developer program apps iPhone 5s This covers the facilities provided by the M7 only, and not the gyroscope, accelerometer, magnetometer, and gps as independent sensors. Apple M7 Devices Applications Services 2 Runkeeper Argus Fitbit bluetooth 4.0 Withings LifeTrak Move C300 iOS Argus uses each New Balance LifeTRNr Watches services’ Pebble SmartWatch Sleep Time respective API. Mio Alpha Data is only viewable in the Wahoo Blue HR Heart Rate Strap iOS/Android Argus app, not in the website Stress Check iOS/Android Instant Heart Rate CSV Azumio cloud CSV premium feature or text iOS/Android/Windows table Phone/Windows 8 Cardio Buddy Data is not available for for Argus (steps only), iOS viewing from website, but Instant Heart Rate, Stress can sync to multiple Check and Sleep Time devices. Instant Fitness iOS CSV or text Fitness Buddy table iOS/Android text Glucose Buddy CSV table Glucose Buddy iOS/Android Azumio Devices Applications Services 3 Viera is Panasonic’s Smart TV platform that runs 3rd- party apps App requires Link Armband armband and API is active to subscription current developers but closed off to activity Bluetooth 2.0 new development heart rate food sleep BodyMedia FIT nutrients steps iOS/Android/Viera BodyMedia FIT API partner Armband Advantage Activity Manager program USB web dashboard BodyMedia SYNC Jawbone UP API apps Windows/Mac The desktop software only location CORE Armband transfers data to the registered image “Activity Manager” developers cardiac service. It does not allow oauth 2.0 food users to view data json goals mood activity sleep RF workout Since the armbands do not have displays, the Display Device is a Display way to show the data. -

Apple 30-Pin Dock Connector to Left Angle USB Cable for Iphone / Ipod / Ipad with Stepped Connector
1m (3 ft) Apple 30-pin Dock Connector to Left Angle USB Cable for iPhone / iPod / iPad with Stepped Connector Product ID: USB2ADC1MUL The USB2ADC1MUL Apple® (30-pin) Dock Connector to Left Angle USB Cable for iPhone®, iPod® and iPad® (1m) offers a simple and reliable solution for connecting iOS-enabled mobile digital devices to your computer, for syncing or charging. The left-angled USB connector allows for connection in tight spaces while the stepped Apple Dock Connector, designed by StarTech.com, plugs into your iPhone, iPod or iPad even when inside a protective case, avoiding the inconvenience of having to constantly remove the cover for every charge. This durable cable is Apple MFi certified and backed by our lifetime warranty to ensure dependable performance. As an alternative, StarTech.com also offers a 1m Apple® 30-pin Dock Connector to Right Angle USB Cable (USB2ADC1MUR), which provides the same convenience as this left-angled cable, but allows you to connect to your PC or Mac® computer or your USB wall/vehicle charger from the opposite direction. www.startech.com 1 800 265 1844 Note: If your computer USB port does not deliver sufficient power and you see a “Not Charging” message on your iPad or other Apple device, you can use this 1m 30-pin Dock to USB Cable with the USB 2.0 Fast Charging Adapter (USB2CHADP) in order to fast charge your devices. www.startech.com 1 800 265 1844 Certifications, Reports Applications and Compatibility • Charge your Apple® devices from a computer, USB wall charger, or vehicle USB charger • Replace -

Portable Speaker S135i
Logitech® Portable Speaker S135i Ready to move, ready to groove Ready to play. Ready to charge. With this go-anywhere speaker for your iPod, you’re set to rock around the house or wherever you want to listen to your music in clear stereo sound with a boost of booming bass. FEATURES AT A GLANCE Plays and charges Longer unplugged power • Works with virtually any Play up to 10 continuous hours of iPod with a built-in dock battery-powered music on the go**. connector.* AC adapter also included. • Clear stereo sound Multi-device input Boost your bass level Connect the speaker to any porta- ble MP3 player, CD player or laptop • Increase it from deep to with a standard 3.5 mm jack. booming with one touch of Ultra-compact and portable so you the Bass Boost button * Supports all iPod models with Universal Dock connector except 3rd gen iPod can take your music with you any- • Adjust volume on the fly with model. Supports older 1G - 3G iPod models and other portable music players via where you go front-of-speaker controls 3.5 mm auxiliary input. ** 4 AA batteries not included WORKS WITH • Supports all iPod models with Which Portable iPod/MP3 Universal Dock connector Speaker Is Right For You? except 3rd gen iPod model. • Supports older 1G-3G iPod mod- Find even more at logitech.com els and other portable music players via 3.5 mm auxiliary Better Best input. Good • 4 AA batteries (not included) Portable Speaker Rechargeable Rechargeable required for portable listening S135i Speaker S315i Speaker S715i Clear stereo sound Custom-tuned sound Custom tuned sound What Do You Get? for iPod for iPod and iPhone and wireless remote WHAT’S IN THE BOX? for iPod and iPhone Music controls • Speaker Wireless remote (30 ft. -

USB Sync/Charge Cable with Apple 30-Pin Dock Connector, Black, 10
USB Sync/Charge Cable with Apple 30-Pin Dock Highlights Connector, Black, 10 in. (.24 m) Features an Apple-compatible 30-pin plug and a USB-A plug MODEL NUMBER: M110-10N-BK Works with any computer MFi-certified for use with iPhone, iPad and iPod devices Compatible with all Apple devices with 30-pin connectors Perfectly sized for Tripp Lite’s Tablet Charging Stations Applications Charge and sync your Apple 30-pin iPhone, iPad or iPod using the USB port on your computer System Requirements USB-equipped computer or charger Description iPhone (4s, 4, 3Gs, 3G and The M110-10N-BK USB Sync/Charge Cable connects your iPhone, iPad or iPod with the USB port on a iPhone), iPad (3rd generation), computer, so you can charge your Apple device and transfer data. Compatible with all computers, this 10-inch iPad 2, iPad, iPod Touch (1st cable is MFi-certified for use with iPhone, iPad and iPod devices. It’s compatible with iPhone(4s, 4, 3Gs, 3G and through 4th generation), iPod iPhone), iPad(3rd generation), iPad 2, iPad, iPod Touch(1st through 4th generation), iPod classic and iPod classic and iPod nano (1st nano(1st through 6th generation). The M110-10N-BK is ideally sized to charge devices in Tripp Lite’s through 6th generation) CS16USB, CS32USB and CS48USB Tablet Charging Stations. Package Includes Features M110-10N-BK USB Sync/Charge Syncs and Charges Your Apple 30-Pin Electronic Devices Cable with Apple 30-Pin Dock MFi-certified for use with iPhone, iPad and iPod devices Connector Compatible with iPhone(4s, 4, 3Gs, 3G and iPhone), iPad(3rd generation), -

How to Connect an Ipad to a MIDI Keyboard
MIDI Connections for iOS Devices iPad, iPhone, iPod touch www.timewarptech.com A Simple Process with Lots of Choices 1. Choose an appropriate connecting technique such as one of the following: A. MIDI interface that is made for iOS devices B. USB Device Cable (if your keyboard has a USB To Host port) C. The Bluetooth MIDI feature built into your keyboard D. Bluetooth LE MIDI adapter for your keyboard (if Option C is not available) 2. Connect the appropriate end to your iOS device NOTE: In some scenarios, an adapter may be required which provides your iOS device with a USB port. NOTE: In the case of Bluetooth LE MIDI, the connection will be wireless—no need to attach anything to your iOS device. 3. If using a cable, connect the other end of your cable to one of the following ports of your MIDI keyboard: A. USB To Host Port B. MIDI In and MIDI Out Ports MIDI Keyboard Connection Option 1 Connect the keyboard and iOS device using a USB device cable and an iOS “camera kit” adapter with the appropriate connector for MIDI Keyboard the iPad: 30-pin dock, Lightning, or USB-C. Dock connector USB device cable Lightning connector USB-C Connector MIDI Keyboard Connection Option 2 Connect the keyboard’s USB To Host port to the iOS device using an iOS MIDI interface made for this purpose, such as the Yamaha i- MIDI Keyboard UX1. Lightning to 30-Pin adapter may be necessary. Yamaha i-UX1 MIDI interface MIDI Keyboard Connection Option 3 Connect the piano’s MIDI ports to the iOS device using an iOS MIDI interface, such as the iConnectMIDI1 from iConnectivity . -

Portable Media
L Portable media 2. 3.5 mm AUX socket. Note: iPod shuffle may be connected via the 3. Rear media AV sockets. AUX socket. 4. Rear media USB/iPod socket. Note: On vehicles fitted with rear seat entertainment, additional Audio/Visual sockets Do not plug non-audio devices into the are provided. This allows auxiliary equipment USB port. (such as a video game console) to be linked to Note: Use the cable supplied with your media the rear DVD screens. For installation device to connect to the USB socket. information, please refer to the manufacturer's Note: A USB hub cannot be used to connect instructions. more than one USB device to the audio unit. Note: Devices connected to the USB ports will PLAYING A PORTABLE DEVICE be charged, but devices that are fully discharged If you are using a USB mass storage device or will not play. approved iPod, you can control playback using Note: In some cases if an iPhone is connected the Touch screen controls. via a USB cable for music and also to a If you are using a Bluetooth® device, you can Bluetooth wireless technology device for other control playback using the Touch screen, but phone functions, the audio will stream through some controls are unavailable. only the last connected port. For example if a If you are using any portable media device via Bluetooth wireless technology device is the last the AUX socket, then you must control playback connection made to the iPhone and the iPod from the device itself. lead is connected, no audio will be heard through the speakers via the iPod lead. -

IPA1070T Multimedia Video & Sound System for Ipod User Guide
IPA1070T Multimedia Video & Sound System for iPod User Guide • Before attempting to connect, operate or adjust this product, please save and read the Getting Started completely. • The style of the product shown in the Getting Started may be different from the actual unit due to various models. 82-282-00090 Thank you for purchasing the multimedia video & sound system. With a conven- ient quick-launch ports, you can play compatible files from memory card or a USB thumb drive without a computer. Before attempting to connect, operate or adjust this product, please save and read the User Guide completely. Important Safety Precautions • Keep away from water or moisture and dusty areas. • Ambient Temperature 0~40°C. Never store in hot and very cold areas. • Care must be taken not to drop the unit. • Do not try to open the case alone without technical support. • Connect the AC adapter to the DC IN jack and to power outlet. • Only use attachments/accessories specified by the manufacturer. • When left unused for a long period of time, the unit should be unplugged from the household AC outlet. Warning: To reduce the risk of fire or electric shock, do not expose to rain, mois- ture, dripping or splashing. Compatibility • This device supports iPod touch 1st/2nd, iPod classic, iPod 4th/5th generation iPods including the special edition U2 and HP iPods, the iPod mini 1st/2nd and iPod nano 1st/2nd/3rd/4th. • This device supports the following file formats: JPEG, MP3 and MPEG4 (*.avi). Please note that not all images, audio and MPEG4 formats are compatible with this device. -

Dock for Iphone®/Ipad® with Airplay® DS-A5
Dock for iPhone®/iPad® with AirPlay® DS-A5 Instruction Manual En Thank you for purchasing an Onkyo product. Please Important Safety Instructions read this manual carefully before making any connections or using this product. By following these 1. Read these instructions. instructions, you’ll get the best audio performance 2. Keep these instructions. and the most listening pleasure from your Onkyo 3. Heed all warnings. product. Keep this manual for future reference. 4. Follow all instructions. WARNING: 5. Do not use this apparatus near water. TO REDUCE THE RISK OF FIRE OR ELECTRIC SHOCK, DO NOT 6. Clean only with dry cloth. EXPOSE THIS APPARATUS TO RAIN OR MOISTURE. 7. Do not block any ventilation openings. Install in accordance with the manufacturer’s instructions. CAUTION: 8. Do not install near any heat sources such as radiators, TO REDUCE THE RISK OF ELECTRIC SHOCK, DO NOT REMOVE heat registers, stoves, or other apparatus (including COVER (OR BACK). NO USER-SERVICEABLE PARTS INSIDE. amplifiers) that produce heat. REFER SERVICING TO QUALIFIED SERVICE PERSONNEL. 9. Do not defeat the safety purpose of the polarized or grounding-type plug. A polarized plug has two blades WARNING AVIS with one wider than the other. A grounding type plug RISK OF ELECTRIC SHOCK RISQUE DE CHOC ELECTRIQUE DO NOT OPEN NE PAS OUVRIR has two blades and a third grounding prong. The wide blade or the third prong are provided for your safety. If The lightning flash with arrowhead symbol, within an equilateral the provided plug does not fit into your outlet, consult triangle, is intended to alert the user to the presence of uninsulated “dangerous voltage” within the product’s enclosure an electrician for replacement of the obsolete outlet. -

PORTABLE ENTERTAINMENT 10 Ebooks
PORTABLE ENTERTAINMENT 10 eBooks www.BandH.com eDGe Dualbook TheBook eReader eReader & Android Tablet in one Device 7” Novel Multimedia Reader • Read books in multiple formats • 9.7” reader for • 7” color LCD touch screen • 7” color display screen eBooks and notes • Android OS • Audio player, picture and video viewing • 10.1” color touch • 2GB Memory screen tablet • 2GB memory with SD card slot • SD card slot • 3GB memory • Wi-Fi with full web browsing capability • Wi-Fi and USB 2.0 • Virtual keyboard • Full Qwerty keyboard • Text, Photo, Video & Audio • Wi-Fi 802.11b/g + Bluetooth • Read-out-Loud text to speech function • Full virtual keyboard • Webcam and audio recorder via built-in speaker • Android AppsLib function • SD card slot, two USB ports • 150 preloaded eBooks • Access Barnes & Noble • Landscape or portrait viewing with zooming capabilities • Portrait or landscape viewing (tablet) Online Bookstore TheBook with leather carrying case (AUEBA701)...............129.95 In Black (ENEDBRB), Blue (ENEDBRBL) or Red (ENEDBR) ............499 #PAR70E200....................................................................149.95 Pocket eDGe Dualbook LIBRE eBook Reader PRO eReader & Android Tablet in one Device PRS-350PC Reader Pocket Edition • 6” reader for • 5” ePaper Display • 5” paper-like touch screen display eBooks and notes • Easy navigation between books and • Intuitive navigation • 7” color touch pages, bookmark or auto page turn screen tablet • Built-In dictionaries and translators • Adjustable font and type size • 3GB memory and