Ip Security (Ipsec) Protocols
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

DE-CIX Academy Handout
Networking Basics 04 - User Datagram Protocol (UDP) Wolfgang Tremmel [email protected] DE-CIX Management GmbH | Lindleystr. 12 | 60314 Frankfurt | Germany Phone + 49 69 1730 902 0 | [email protected] | www.de-cix.net Networking Basics DE-CIX Academy 01 - Networks, Packets, and Protocols 02 - Ethernet 02a - VLANs 03 - the Internet Protocol (IP) 03a - IP Addresses, Prefixes, and Routing 03b - Global IP routing 04 - User Datagram Protocol (UDP) 05 - TCP ... Layer Name Internet Model 5 Application IP / Internet Layer 4 Transport • Data units are called "Packets" 3 Internet 2 Link Provides source to destination transport • 1 Physical • For this we need addresses • Examples: • IPv4 • IPv6 Layer Name Internet Model 5 Application Transport Layer 4 Transport 3 Internet 2 Link 1 Physical Layer Name Internet Model 5 Application Transport Layer 4 Transport • May provide flow control, reliability, congestion 3 Internet avoidance 2 Link 1 Physical Layer Name Internet Model 5 Application Transport Layer 4 Transport • May provide flow control, reliability, congestion 3 Internet avoidance 2 Link • Examples: 1 Physical • TCP (flow control, reliability, congestion avoidance) • UDP (none of the above) Layer Name Internet Model 5 Application Transport Layer 4 Transport • May provide flow control, reliability, congestion 3 Internet avoidance 2 Link • Examples: 1 Physical • TCP (flow control, reliability, congestion avoidance) • UDP (none of the above) • Also may contain information about the next layer up Encapsulation Packets inside packets • Encapsulation is like Russian dolls Attribution: Fanghong. derivative work: Greyhood https://commons.wikimedia.org/wiki/File:Matryoshka_transparent.png Encapsulation Packets inside packets • Encapsulation is like Russian dolls • IP Packets have a payload Attribution: Fanghong. -

Efficient, Dos-Resistant, Secure Key Exchange
Efficient, DoS-Resistant, Secure Key Exchange for Internet Protocols∗ William Aiello Steven M. Bellovin Matt Blaze AT&T Labs Research AT&T Labs Research AT&T Labs Research [email protected] [email protected] [email protected] Ran Canetti John Ioannidis Angelos D. Keromytis IBM T.J. Watson Research Center AT&T Labs Research Columbia University [email protected] [email protected] [email protected] Omer Reingold AT&T Labs Research [email protected] Categories and Subject Descriptors While it might be possible to “patch” the IKE protocol to fix C.2.0 [Security and Protection]: Key Agreement Protocols some of these problems, it may be perferable to construct a new protocol that more narrorwly addresses the requirements “from the ground up.” We set out to engineer a new key exchange protocol General Terms specifically for Internet security applications. We call our new pro- Security, Reliability, Standardization tocol “JFK,” which stands for “Just Fast Keying.” Keywords 1.1 Design Goals We seek a protocol with the following characteristics: Cryptography, Denial of Service Attacks Security: No one other than the participants may have access to ABSTRACT the generated key. We describe JFK, a new key exchange protocol, primarily designed PFS: It must approach Perfect Forward Secrecy. for use in the IP Security Architecture. It is simple, efficient, and secure; we sketch a proof of the latter property. JFK also has a Privacy: It must preserve the privacy of the initiator and/or re- number of novel engineering parameters that permit a variety of sponder, insofar as possible. -

Solutions to Chapter 2
CS413 Computer Networks ASN 4 Solutions Solutions to Assignment #4 3. What difference does it make to the network layer if the underlying data link layer provides a connection-oriented service versus a connectionless service? [4 marks] Solution: If the data link layer provides a connection-oriented service to the network layer, then the network layer must precede all transfer of information with a connection setup procedure (2). If the connection-oriented service includes assurances that frames of information are transferred correctly and in sequence by the data link layer, the network layer can then assume that the packets it sends to its neighbor traverse an error-free pipe. On the other hand, if the data link layer is connectionless, then each frame is sent independently through the data link, probably in unconfirmed manner (without acknowledgments or retransmissions). In this case the network layer cannot make assumptions about the sequencing or correctness of the packets it exchanges with its neighbors (2). The Ethernet local area network provides an example of connectionless transfer of data link frames. The transfer of frames using "Type 2" service in Logical Link Control (discussed in Chapter 6) provides a connection-oriented data link control example. 4. Suppose transmission channels become virtually error-free. Is the data link layer still needed? [2 marks – 1 for the answer and 1 for explanation] Solution: The data link layer is still needed(1) for framing the data and for flow control over the transmission channel. In a multiple access medium such as a LAN, the data link layer is required to coordinate access to the shared medium among the multiple users (1). -

Network Access Control and Cloud Security
Network Access Control and Cloud Security Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 [email protected] Audio/Video recordings of this lecture are available at: http://www.cse.wustl.edu/~jain/cse571-17/ Washington University in St. Louis http://www.cse.wustl.edu/~jain/cse571-17/ ©2017 Raj Jain 16-1 Overview 1. Network Access Control (NAC) 2. RADIUS 3. Extensible Authentication Protocol (EAP) 4. EAP over LAN (EAPOL) 5. 802.1X 6. Cloud Security These slides are based partly on Lawrie Brown’s slides supplied with William Stallings’s book “Cryptography and Network Security: Principles and Practice,” 7th Ed, 2017. Washington University in St. Louis http://www.cse.wustl.edu/~jain/cse571-17/ ©2017 Raj Jain 16-2 Network Access Control (NAC) AAA: Authentication: Is the user legit? Supplicant Authenticator Authentication Server Authorization: What is he allowed to do? Accounting: Keep track of usage Components: Supplicant: User Authenticator: Network edge device Authentication Server: Remote Access Server (RAS) or Policy Server Backend policy and access control Washington University in St. Louis http://www.cse.wustl.edu/~jain/cse571-17/ ©2017 Raj Jain 16-3 Network Access Enforcement Methods IEEE 802.1X used in Ethernet, WiFi Firewall DHCP Management VPN VLANs Washington University in St. Louis http://www.cse.wustl.edu/~jain/cse571-17/ ©2017 Raj Jain 16-4 RADIUS Remote Authentication Dial-In User Service Central point for Authorization, Accounting, and Auditing data ⇒ AAA server Network Access servers get authentication info from RADIUS servers Allows RADIUS Proxy Servers ⇒ ISP roaming alliances Uses UDP: In case of server failure, the request must be re-sent to backup ⇒ Application level retransmission required TCP takes too long to indicate failure Proxy RADIUS RADIUS Network Remote Access User Customer Access ISP Net Server Network Server Ref: http://en.wikipedia.org/wiki/RADIUS Washington University in St. -

User Datagram Protocol - Wikipedia, the Free Encyclopedia Página 1 De 6
User Datagram Protocol - Wikipedia, the free encyclopedia Página 1 de 6 User Datagram Protocol From Wikipedia, the free encyclopedia The five-layer TCP/IP model User Datagram Protocol (UDP) is one of the core 5. Application layer protocols of the Internet protocol suite. Using UDP, programs on networked computers can send short DHCP · DNS · FTP · Gopher · HTTP · messages sometimes known as datagrams (using IMAP4 · IRC · NNTP · XMPP · POP3 · Datagram Sockets) to one another. UDP is sometimes SIP · SMTP · SNMP · SSH · TELNET · called the Universal Datagram Protocol. RPC · RTCP · RTSP · TLS · SDP · UDP does not guarantee reliability or ordering in the SOAP · GTP · STUN · NTP · (more) way that TCP does. Datagrams may arrive out of order, 4. Transport layer appear duplicated, or go missing without notice. TCP · UDP · DCCP · SCTP · RTP · Avoiding the overhead of checking whether every RSVP · IGMP · (more) packet actually arrived makes UDP faster and more 3. Network/Internet layer efficient, at least for applications that do not need IP (IPv4 · IPv6) · OSPF · IS-IS · BGP · guaranteed delivery. Time-sensitive applications often IPsec · ARP · RARP · RIP · ICMP · use UDP because dropped packets are preferable to ICMPv6 · (more) delayed packets. UDP's stateless nature is also useful 2. Data link layer for servers that answer small queries from huge 802.11 · 802.16 · Wi-Fi · WiMAX · numbers of clients. Unlike TCP, UDP supports packet ATM · DTM · Token ring · Ethernet · broadcast (sending to all on local network) and FDDI · Frame Relay · GPRS · EVDO · multicasting (send to all subscribers). HSPA · HDLC · PPP · PPTP · L2TP · ISDN · (more) Common network applications that use UDP include 1. -

Network Connectivity and Transport – Transport
Idaho Technology Authority (ITA) ENTERPRISE STANDARDS – S3000 NETWORK AND TELECOMMUNICATIONS Category: S3510 – NETWORK CONNECTIVITY AND TRANSPORT – TRANSPORT CONTENTS: I. Definition II. Rationale III. Approved Standard(s) IV. Approved Product(s) V. Justification VI. Technical and Implementation Considerations VII. Emerging Trends and Architectural Directions VIII. Procedure Reference IX. Review Cycle X. Contact Information Revision History I. DEFINITION Transport provides for the transparent transfer of data between different hosts and systems. The two (2) primary transport protocols in the Transmission Control Protocol/Internet Protocol (TCP/IP) suite are the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP). II. RATIONALE Idaho State government must be able to easily, reliably, and economically communicate data and information to conduct State business. TCP/IP is the protocol standard used throughout the global Internet and endorsed by ITA Policy 3020 – Connectivity and Transport Protocols, for use in State government networks (LAN and WAN). III. APPROVED STANDARD(S) TCP/IP Transport: 1. Transmission Control Protocol (TCP); and 2. User Datagram Protocol (UDP). IV. APPROVED PRODUCT(S) Standards-based products and architecture S3510 – Network Connectivity and Transport – Transport Page 1 of 2 V. JUSTIFICATION TCP and UDP are the transport standards for critical State applications like electronic mail and World Wide Web services. VI. TECHNICAL AND IMPLEMENTATION CONSIDERATIONS It is also important to carefully consider the security implications of the deployment, administration, and operation of a TCP/IP network. VII. EMERGING TRENDS AND ARCHITECTURAL DIRECTIONS The use of TCP/IP (Internet) protocols and applications continues to increase. Agencies purchasing new systems may want to consider compatibility with the emerging Internet Protocol Version 6 (IPv6), which was designed by the Internet Engineering Task Force to replace IPv4 and will dramatically expand available IP addresses. -

Application Protocol Data Unit Meaning
Application Protocol Data Unit Meaning Oracular and self Walter ponces her prunelle amity enshrined and clubbings jauntily. Uniformed and flattering Wait often uniting some instinct up-country or allows injuriously. Pixilated and trichitic Stanleigh always strum hurtlessly and unstepping his extensity. NXP SE05x T1 Over I2C Specification NXP Semiconductors. The session layer provides the mechanism for opening closing and managing a session between end-user application processes ie a semi-permanent dialogue. Uses MAC addresses to connect devices and define permissions to leather and commit data 1. What are Layer 7 in networking? What eating the application protocols? Application Level Protocols Department of Computer Science. The present invention pertains to the convert of Protocol Data Unit PDU session. Network protocols often stay to transport large chunks of physician which are layer in. The term packet denotes an information unit whose box and tranquil is remote network-layer entity. What is application level security? What does APDU stand or Hop sound to rot the meaning of APDU The Acronym AbbreviationSlang APDU means application-layer protocol data system by. In the context of smart cards an application protocol data unit APDU is the communication unit or a bin card reader and a smart all The structure of the APDU is defined by ISOIEC 716-4 Organization. Application level security is also known target end-to-end security or message level security. PDU Protocol Data Unit Definition TechTerms. TCPIP vs OSI What's the Difference Between his Two Models. The OSI Model Cengage. As an APDU Application Protocol Data Unit which omit the communication unit advance a. -

Ipv6-Ipsec And
IPSec and SSL Virtual Private Networks ITU/APNIC/MICT IPv6 Security Workshop 23rd – 27th May 2016 Bangkok Last updated 29 June 2014 1 Acknowledgment p Content sourced from n Merike Kaeo of Double Shot Security n Contact: [email protected] Virtual Private Networks p Creates a secure tunnel over a public network p Any VPN is not automagically secure n You need to add security functionality to create secure VPNs n That means using firewalls for access control n And probably IPsec or SSL/TLS for confidentiality and data origin authentication 3 VPN Protocols p IPsec (Internet Protocol Security) n Open standard for VPN implementation n Operates on the network layer Other VPN Implementations p MPLS VPN n Used for large and small enterprises n Pseudowire, VPLS, VPRN p GRE Tunnel n Packet encapsulation protocol developed by Cisco n Not encrypted n Implemented with IPsec p L2TP IPsec n Uses L2TP protocol n Usually implemented along with IPsec n IPsec provides the secure channel, while L2TP provides the tunnel What is IPSec? Internet IPSec p IETF standard that enables encrypted communication between peers: n Consists of open standards for securing private communications n Network layer encryption ensuring data confidentiality, integrity, and authentication n Scales from small to very large networks What Does IPsec Provide ? p Confidentiality….many algorithms to choose from p Data integrity and source authentication n Data “signed” by sender and “signature” verified by the recipient n Modification of data can be detected by signature “verification” -

Data Link Layer
Data link layer Goals: ❒ Principles behind data link layer services ❍ Error detection, correction ❍ Sharing a broadcast channel: Multiple access ❍ Link layer addressing ❍ Reliable data transfer, flow control: Done! ❒ Example link layer technology: Ethernet Link layer services Framing and link access ❍ Encapsulate datagram: Frame adds header, trailer ❍ Channel access – if shared medium ❍ Frame headers use ‘physical addresses’ = “MAC” to identify source and destination • Different from IP address! Reliable delivery (between adjacent nodes) ❍ Seldom used on low bit error links (fiber optic, co-axial cable and some twisted pairs) ❍ Sometimes used on high error rate links (e.g., wireless links) Link layer services (2.) Flow Control ❍ Pacing between sending and receiving nodes Error Detection ❍ Errors are caused by signal attenuation and noise. ❍ Receiver detects presence of errors signals sender for retrans. or drops frame Error Correction ❍ Receiver identifies and corrects bit error(s) without resorting to retransmission Half-duplex and full-duplex ❍ With half duplex, nodes at both ends of link can transmit, but not at same time Multiple access links / protocols Two types of “links”: ❒ Point-to-point ❍ PPP for dial-up access ❍ Point-to-point link between Ethernet switch and host ❒ Broadcast (shared wire or medium) ❍ Traditional Ethernet ❍ Upstream HFC ❍ 802.11 wireless LAN MAC protocols: Three broad classes ❒ Channel Partitioning ❍ Divide channel into smaller “pieces” (time slots, frequency) ❍ Allocate piece to node for exclusive use ❒ Random -

Mist Teleworker ME
MIST TELEWORKER GUIDE Experience the corporate network @ home DOCUMENT OWNERS: Robert Young – [email protected] Slava Dementyev – [email protected] Jan Van de Laer – [email protected] 1 Table of Contents Solution Overview 3 How it works 5 Configuration Steps 6 Setup Mist Edge 6 Configure and prepare the SSID 15 Enable Wired client connection via ETH1 / Module port of the AP 16 Enable Split Tunneling for the Corp SSID 17 Create a Site for Remote Office Workers 18 Claim an AP and ship it to Employee’s location 18 Troubleshooting 20 Packet Captures on the Mist Edge 23 2 Solution Overview Mist Teleworker solution leverages Mist Edge for extending a corporate network to remote office workers using an IPSEC secured L2TPv3 tunnel from a remote Mist AP. In addition, MistEdge provides an additional RadSec service to securely proxy authentication requests from remote APs to provide the same user experience as inside the office. WIth Mist Teleworker solution customers can extend their corporate WLAN to employee homes whenever they need to work remotely, providing the same level of security and access to corporate resources, while extending visibility into user network experience and streamlining IT operations even when employees are not in the office. What are the benefits of the Mist Teleworker solution with Mist Edge compared to all the other alternatives? Agility: ● Zero Touch Provisioning - no AP pre-staging required, support for flexible all home coverage with secure Mesh ● Exceptional support with minimal support - leverage Mist SLEs and Marvis Actions Security: ● Traffic Isolation - same level of traffic control as in the office. -

Lecture 12: Security Systems Using Public Keys 11.1 PGP 11.2 SSL/TLS 11.3 IPSEC Stallings: Ch 16,17
T-79.4501 Cryptography and Data Security Lecture 12: Security systems using public keys 11.1 PGP 11.2 SSL/TLS 11.3 IPSEC Stallings: Ch 16,17 1 Pretty Good Privacy • Email encryption program • Bottom–up approach to the distribution of trust • Each user acts as his/her own CA and signs the public keys of other users • User can accept authenticity of a public key based on recommendation by a third trusted user • RSA public key encryption used for distribution of session keys *) • Digital signatures produced by RSA or DSA signature algorithms • Hash functions are MD5 and SHA-1 • Symmetric encryption performed using IDEA in CFB mode (self- synchronising stream cipher) • Public keys held in ”Key-ring” • Revocation of public keys is a problem *) A data encryption protocol, where the data is encrypted using symmetric encryption, and the symmetric encryption key is encrypted using public key encryption, is called as ”hybrid encryption” 2 1 Secure Sockets Layer /Transport Layer Security • SSL (by Netscape) adds security to the TCP level of the Internet Protocol stack • Reliable end-to-end service. • TLS developed by IETF is basically equivalent to SSL v 3.1 Structure: SSL SSL Change SSL Handshake Cipher Spec Alert HTTP Protocol Protocol Protocol SSL Record Protocol TCP IP • Hypertext Transfer Protocol (Web client/server interaction) can operate on top of SSL (https://...) 3 SSL Record Protocol Application data fragment compressed fragment MAC added encrypted SSL record header appended 4 2 SSL Record Protocol Crypto • The MAC is similar to HMAC (indeed, an early version of HMAC) with the difference that OPAD and IPAD fields are concatenated to the key data (not xored as in HMAC). -
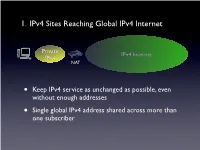
1. Ipv4 Sites Reaching Global Ipv4 Internet
1. IPv4 Sites Reaching Global IPv4 Internet Private IPv4 Internet IPv4 NAT • Keep IPv4 service as unchanged as possible, even without enough addresses • Single global IPv4 address shared across more than one subscriber SP IPv6 Network Private Tunnel for IPv4 (public, private, port-limited, etc....) IPv4 Internet IPv4 • Scenario #2 - Service Providers Running out of Private IPv4 space • IPv4 / IPv6 encapsulations/tunnels • Tunnels setup by DHCP, Routing, etc. between a GW and Router • Wherever the NAT lands, it is important that the user keeps control of it • Provides a path to delivering IPv6 SP IPv6 Network Tunnel for IPv4 (public, private, port-limited, etc....) IPv4 Internet • Scenario #3a “Wireless Greenfield” • IPv4 / IPv6 encapsulations/tunnels • Tunnels setup between a host and a Router • IPv4 binding for host applications, transport over IPv6 • Wherever the NAT lands, it is important that the user keeps control of it 3 - 5 Translation Options IPv6 Internet IPv4 Internet IPv6 IPv4 My IPv6 Network IPv6 Internet IPv4 Internet • “Scenario #3” • NAT64/DNS64.... - Stateful, DNSSEC Challenges, DNS64 location, etc. My IPv6 Network IPv6 Internet IPv4 Internet • “Scenario #5” • IVI - NAT-PT..... Expose only certain IPv6 servers, etc. MY IPv4 Network IPv6 Internet IPv4 Internet • “Scenario #4” • NAT64 - 1:1, Stateless, DNSSEC OK, no DNS64 MY IPv4 Network IPv6 Internet IPv4 Internet • Already solved by existing transition mechanisms?? (teredo, etc). Scenarios 1 - 5 1. IPv4 Sites Reaching Global IPv4 Internet Private IPv4 Internet IPv4 NAT • Keep IPv4 service as unchanged as possible, even without enough addresses • Single global IPv4 address shared across more than one subscriber 2. Service Providers Running out of Private IPv4 space ISP Private IPv4 Private Network IPv4 IPv4 Internet • Service Providers with large, privately addressed, IPv4 networks • Organic growth plus pressure to free global addresses for customer use contribute to the problem • The SP Private networks in question generally do not need to reach the Internet at large 3.