Mobile Devices Security Guideline
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Design & Implementation of Classification & Clustering
Summer Internship Report On Design & Implementation of Classification & Clustering Algorithm for Mobile Phones At IDRBT, Hyderabad 6th May 2014 to 5th July 2014 Submitted By: Ratnesh Chandak B. Tech- CSE (2nd Year) Roll Number: CS12B1030 Indian Institute of Technology, Hyderabad Guided By: Dr. V.N. Sastry Designation: Professor IDRBT, Hyderabad Date of Submission: 4th July 2014 1 Abstract This project is broadly divided in two parts, in the first part we would be finding intersection of common objects from different sets taking an example of finding common colored balls from different sets of containers. In second part we would describe K-Means Clustering Algorithm to find similar numerical sets and we will experimentally find optimal value of “K” in clustering algorithm by using Elbow Method. Both the these are explained with an example of mobiles phones and done implementation in java. 2 Certificate Certified that this is a bonafide record of summer internship project work entitled Design & Implementation of Classification & Clustering Algorithm for Mobile Phones Done By Ratnesh Chandak B. Tech - CSE (2nd Year) Indian Institute of Technology, Hyderabad at IDRBT, Hyderabad during 6th May to 5th July 2014 Prof. V N Sastry (Project Guide) IDRBT, Hyderabad 3 Acknowledgement We have completed this project as summer internship in IDRBT (Institute for Development and Research in Banking Technology), Hyderabad under the guidance of Dr. V.N. Sastry. We would like to thank all our friends and our mentor for great support in completing this project. -

Dgipad-4544-Portable Power Max-Ss-V3
www.dreamGEAR.net | www.iSound.net 20001 S. Western Avenue, Torrance, CA 90501 tel: 310.222.5522 :: fax: 310.222.5577 Portable Power Max 16,000 mAh Backup Battery ITEM No. - DGIPAD-4544 UPC - 8 45620 04544 0 1 Inch 5.75 Inches COLOR - Black & Silver PRODUCT FEATURES Flashlight Switch The Portable Power Max is the only back up power supply you will ever Built-in again need while on the road. With its compact design and powerful Flashlight battery, you can squeeze more talk time and photos into multiple devices. The 5 USB ports allow you to charge and power any USB powered device, and the included USB to mini and micro USB cable means you don't have to carry around cables for each device. LED indicators let you know how much power is remaining, and a flashlight is built in to help you LED Charge & Power Status Indicator in the dark. The iSound Portable Power and Portable Power Max batteries use Lithium-ion Polymer, a gel type electrolyte. Unlike 3.25 Inches Lithium-ion batteries, which use a liquid, Lithium-ion Polymer batteries Power have less tendency to leak if cracked or otherwise damaged. Apple only Switch uses Lithium-ion Polymer batteries in the iPhone and iPad. Weight 14.6 oz • Battery with 16000 mAh (60 Wh) • Up to 480 hours of power for 5 USB powered devices simultaneously • Includes 5 USB ports for charging iPods, iPhones, iPads and any other USB powered devices • LED indicator for charging & power status • Power switch and LED status indicator • 100 / 240V AC adapter included Includes 100 / 240V • Built-in flashlight AC Adapter 5 USB Ports 1 USB to Mini USB / Micro USB Includes BlackBerry Adapter Cable included PRODUCT SPECIFICATIONS Portable Power Max Capacity: 16000 mAh Portable Power iPhone 5 iPad Air iPad iPod Touch iPhone 4 TRANSLATIONS Max Number of 4x .75x 1x 9x 5x PACKAGING | COMPLETE FRENCH: Yes | SPANISH: Yes Charges* USER GUIDE | COMPLETE FRENCH: Yes | SPANISH: Yes *Number of times you can charge that single device from a fully charged Portable Power Max. -

PD# Brand Model 1 Ipad 4 2 Mini Ipad 3 New Ipad 4 Ipad2 A1395 5 Ipad
PD# Brand Model 1 iPad 4 2 Mini iPad 3 New iPad 4 iPad2 A1395 5 iPad A1219 6 iPad MC349LL/A 7 iPhone5 8 iPhone4s MD239ZP 9 iPhone4 MD128ZP 10 iPhone 4 A1332 11 AT&T iPhone 4 12 AT&T iPhone 3Gs 13 iPhone 3Gs A1241 14 iPhone 3Gs MB489J/A 15 iPod touch 2G 16GB MB531J/A 16 iPod touch 32GB MB376J/A 17 iPod touch 32GB MC544J/A 18 iPod touch 3G 64GB MC011J/A Apple 19 iPod Touch A1288 20 iPod Classic A1238 21 iPod classic 160GB MB150J/A 22 iPod classic 160GB MC297J/A 23 iPod Classic 6.5Gen 120GB (MB565TA/A) 24 iPod nano 16GB MC526J/A 25 iPod nano 4G 16GB MB918J/A 26 iPod nano 8GB MB261J/A 27 iPod nano 5G 16GB MC060J/A 28 iPod shuffle 2G 1GB MB225J/A 29 iPod shuffle 3G 4GB MC164J/A 30 iPod shuffle2GB MC584J/A 31 iPod Nano A1285 32 iPod Nano A1366 33 iPod Shuffle A1271 34 iPod 1204 35 iPod iShuffle A1373 36 Samsung Galaxy Tab 7" 37 Samsung Galaxy Tab 10.1" 38 Samsung Galaxy Tab2 7.0” 39 Samsung Galaxy SIII 40 Samsung Galaxy SII 41 Samsung Galaxy Ace 42 Samsung Evergreen (SGH-A667) 43 Samsung SGH-A777 44 Samsung Solstice II (SGH-A817) 45 Samsung Samsung Rugby II (SGH-A847) 46 Samsung Flight II (SGH-A927) 47 Samsung Jack (SGH-i637) 48 Samsung Captivate (SGH-i897) 49 Samsung Focus (SGH-i917) 50 Samsung Infuse (SGH-i997) 51 Samsung GT-I9000 (Galaxy S I9000 8GB) 52 Samsung YP-P3 53 Samsung OMNIA II i8000 54 Samsung GOOGLE NEXUS S (GT-I9023) 55 Google Nexus 7 56 Kindle Wireless Reading Device (6'') Amazon 57 Kindle Fire HD 58 HTC Freestyle (F5151) 59 HTC HD7S (PD29150) 60 HTC Inspire 4G (PD98120) 61 HTC Tilt (ST7377) 62 HTC Surround (T8788) 63 HTC Desires -

Comparing the Apple Ipad and Non-Apple Camp Tablet Pcs: a Multicriteria Decision Analysis
TECHNOLOGICAL AND ECONOMIC DEVELOPMENT OF ECONOMY ISSN 2029-4913 print/ISSN 2029-4921 online 2013 Volume 19(Supplement 1): S256–S284 doi:10.3846/20294913.2013.881929 COMPARING THE APPLE IPAD AND NON-APPLE CAMP TABLET PCS: A MULTICRITERIA DECISION ANALYSIS Pei-Hsuan TSAI, Shun-Chiao CHANG Department of Business Administration, National Taiwan University of Science and Technology, No. 43, Sec. 4, Keelung Road, 10607 Taipei, Taiwan Received 06 November 2012; accepted 27 Apr 2013 Abstract. This study mainly evaluates the performances of Tablet PCs such as the Apple iPad based on a benefits, opportunity, costs, and risks (BOCR) conceptual framework with qualitative and quantitative criteria. We apply four methods, namely, the multiple-criteria decision-making (MCDM) tools (grey relational analysis (GRA), the technique for order performance by similarity to ideal solution (TOPSIS), the VlseKriterijumska Optimizacija I Kompromisno (VIKOR) method, and fuzzy approach) to evaluate and select the tablet PCs’ rankings and then construct a tablet PCs evaluation performance model under an analytic hierarchy process (AHP). The empirical results reveal that a firm’s revenue growth, capacity for profitability, product design and product function are highly important evaluation indexes. This indicates that Tablet PC companies should channel more efforts into their product innovation for creating revenue growth and maintaining customer loyalty. Finally, fuzzy AHP also leads to the same findings. Keywords: tablet PCs, multiple-criteria decision-making, analytic hierarchy process (AHP), product innovation, fuzzy AHP. Reference to this paper should be made as follows: Tsai, P.-H.; Chang, S.-C. 2013. Comparing the Apple iPad and non-Apple camp tablet PCs: a multicriteria decision analysis, Technological and Economic Development of Economy 19(Supplement 1): S256–S284. -

HP Veer 4G P160UNA
User Guide Intellectual property notices Recycling and disposal © 2009–2011 Hewlett-Packard Development Company, L.P. The information contained herein This symbol indicates that HP products should be recycled and not be disposed of in is subject to change without notice. Microsoft, Exchange ActiveSync, and Outlook are unsorted municipal waste. HP products should be sent to a facility that properly trademarks of the Microsoft group of companies. Facebook is a registered trademark of recycles electrical and electronic equipment. For information on environmental Facebook, Inc. Google, Gmail, Google Maps, and YouTube are trademarks of Google, Inc. programs visit hp.com/environment or recyclewirelessphones.com/. LinkedIn and the LinkedIn logo are registered trademarks of LinkedIn Corporation in the United States and/or other countries. Yahoo! and Yahoo! Mail are registered trademarks of Yahoo! Inc. As part of HP’s corporate commitment to be a good steward of the environment, we strive to Amazon, Amazon MP3, and the Amazon MP3 logo are trademarks of Amazon.com, Inc. or its use environmentally friendly materials, reduce waste, and develop the highest standards in affiliates. Quickoffice is a registered trademark of Quickoffice, Inc. PDF View is provided by electronics recycling. Documents To Go®, a product of DataViz, Inc. (dataviz.com). All other brand and product names are or may be trademarks of their respective owners. All screen images simulated. v. 1.0 Disclaimer and limitation of liability Hewlett-Packard, Inc. and its suppliers assume no responsibility for any damage or loss resulting from the use of this guide. Hewlett-Packard, Inc. and its suppliers assume no responsibility for any loss or claims by third parties that may arise through the use of this software. -

HP Cloud for Webos Devices Will It Be Halfhearted
HP Cloud For WebOS Devices, Will It Be Half-hearted 1 / 5 HP Cloud For WebOS Devices, Will It Be Half-hearted 2 / 5 3 / 5 In addition, HP will launch a public cloud platform that will serve multiple ... Indeed, HP has Veritca-powered appliances set in half-rack and full racks once the deal closes. ... "At the heart of all of this is cloud computing and connectivity," said Apotheker. HP ... HP will push the WebOS and in multiple devices. ... 2014 · Over half of LG's TVs next year will run webOS TV, so it's a significant ... WebOS homebrewing Homebrewing, which is for HP's WebOS devices, ... OS is considered to be the heart of the devices whether it is a desktop or a mobile device. ... While Gauddi's cloud-based application acts as your command centre, LG .... Hewlett-Packard has confirmed that it will be ceasing support of its ... HP confirmed in 2011 that production of webOS-enabled phones and .... HP has announced that they plan to discountinue operations for webOS devices, which include the TouchPad and webOS phones like the Veer and HP Pre 3 handset which has just half-heartedly launched in Europe. ... IT infrastructure at the convergence of the cloud and connectivity, creating seamless, .... HP Cloud for webOS devices, will it be half-hearted? by Peter Chubb 9 years ago. Read More. in Cell Phone Information, Cell Phones ... Official Gapps For Android 5.1.1 Lollipop Arm64 64bit Flashable.zip Amazon.com : HP TouchPad Wi-Fi 32 GB 9.7-Inch Tablet Computer : Computers ... together with other HP webOS devices: Touch to share websites with your HP Pre3 or .. -
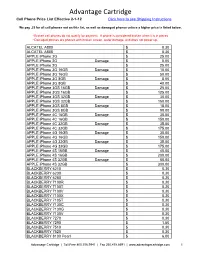
Advantage Cartridge Cell Phone Price List Effective 2-1-12 Click Here to See Shipping Instructions
Advantage Cartridge Cell Phone Price List Effective 2-1-12 Click here to see Shipping Instructions We pay .25 for all cell phones not on this list, as well as damaged phones unless a higher price is listed below. • Broken cell phones do not qualify for payment. A phone is considered broken when it is in pieces • Damaged phones are phones with broken screen, water damage, and does not power up. ALCATEL A800 $ 0.30 ALCATEL A808 $ 0.30 APPLE iPhone 2G $ 25.00 APPLE iPhone 2G Damage $ 5.00 APPLE iPhone 2G $ 25.00 APPLE iPhone 3G 16GB Damage $ 10.00 APPLE iPhone 3G 16GB $ 50.00 APPLE iPhone 3G 8GB Damage $ 8.00 APPLE iPhone 3G 8GB $ 40.00 APPLE iPhone 3GS 16GB Damage $ 25.00 APPLE iPhone 3GS 16GB $ 125.00 APPLE iPhone 3GS 32GB Damage $ 30.00 APPLE iPhone 3GS 32GB $ 150.00 APPLE iPhone 3GS 8GB Damage $ 18.00 APPLE iPhone 3GS 8GB $ 90.00 APPLE iPhone 4C 16GB Damage $ 30.00 APPLE iPhone 4C 16GB $ 150.00 APPLE iPhone 4C 32GB Damage $ 35.00 APPLE iPhone 4C 32GB $ 175.00 APPLE iPhone 4G 16GB Damage $ 30.00 APPLE iPhone 4G 16GB $ 150.00 APPLE iPhone 4G 32GB Damage $ 35.00 APPLE iPhone 4G 32GB $ 175.00 APPLE iPhone 4S 16GB Damage $ 40.00 APPLE iPhone 4S 16GB $ 200.00 APPLE iPhone 4S 32GB Damage $ 60.00 APPLE iPhone 4S 32GB $ 300.00 BLACKBERRY 6210 $ 0.30 BLACKBERRY 6230 $ 0.30 BLACKBERRY 6280 $ 0.30 BLACKBERRY 7100R $ 0.30 BLACKBERRY 7100T $ 0.30 BLACKBERRY 7100V $ 0.30 BLACKBERRY 7100X $ 0.30 BLACKBERRY 7105T $ 0.30 BLACKBERRY 7130C $ 0.30 BLACKBERRY 7130G $ 0.30 BLACKBERRY 7130V $ 0.30 BLACKBERRY 7270 $ 0.30 BLACKBERRY 7290 $ 1.50 BLACKBERRY 7510 -

Bedienungsanleitung HP Veer
Benutzerhandbuch Hinweise zum geistigen Eigentum • Mac: Öffnen Sie den Finder. • Linux (Ubuntu): Das Laufwerk wird auf dem Desktop angezeigt. © 2009–2011 Hewlett-Packard Development Company, L.P. Die hierin enthaltenen Informationen können ohne Vorankündigung geändert werden. Microsoft, Exchange • Andere Linux-Distributionen: Der Ort des Laufwerks kann von System zu System ActiveSync und Outlook sind Marken der Microsoft-Unternehmensgruppe. Facebook ist eine verschieden sein. eingetragene Marke von Facebook, Inc. Google, Google Mail, Google Maps und YouTube sind Marken von Google, Inc. LinkedIn und das LinkedIn-Logo sind eingetragene Marken Nachdem Sie das Laufwerk geöffnet haben, doppelklicken Sie auf die Datei Open Source der LinkedIn Corporation in den USA und/ oder anderen Ländern. Yahoo! und Yahoo! Mail Information.pdf. sind eingetragene Marken von Yahoo! Inc. Amazon, Amazon MP3 und das Amazon MP3-Logo sind Marken von Amazon.com, Inc. oder seinen Konzerngesellschaften. Wiederverwertung und Entsorgung Quickoffice ist eine eingetragene Marke von Quickoffice, Inc. PDF-Viewer ist eine ® Komponente von Documents To Go , einem Produkt von DataViz, Inc. (dataviz.com). Alle Dieses Symbol weist darauf hin, dass HP-Produkte recycelt und nicht im unsortierten anderen Marken- und Produktnamen sind möglicherweise Marken der jeweiligen Inhaber. Hausmüll entsorgt werden sollten. Übergeben Sie Produkte von HP an eine Alle Bildschirmdarstellungen sind simuliert. Einrichtung, in der Elektro- und Elektronikgeräte ordnungsgemäß recycelt werden. Weitere Informationen zu unseren Umweltprogrammen finden Sie unter hp.com/ Haftungsausschluss und Haftungsbeschränkung environment oder recyclewirelessphones.com/. Hewlett-Packard und seine Lieferanten übernehmen keine Haftung für Schäden oder Verluste, Als Unternehmen engagiert sich HP für die Stärkung des Umweltbewusstseins. Unser Ziel ist die aus der Verwendung dieses Handbuchs resultieren. -

Christopher Anderson [email protected] Mountain View, CA
Christopher Anderson [email protected] Mountain View, CA Experience Jawbone System Software Engineer – Device/System Software Sept 2010 to Mar 2012 • Implemented product features in C/ASM on the CSR Kalimba platform. • Implemented various device drivers and system services for peripheral buses for jOS. • Worked on various stages of board bring-up and development for different ARM development boards. • Served as primary engineer for working with DSP vendors and designing/implementing DSP services for jOS host side requirements. • Designed jawbone filesystem and implemented the driver and base userspace tools for use with jOS systems and services. Palm, Inc Software Engineer – WebOS Kernel and Bootloader Oct 2008 to Sept 2010 • Worked on Linux kernel, driver, and bootloader support for various embedded products. • Implemented software support for hardware components consisting of, but not limited to, touchscreen controllers, charging chips, chipset buses, keypads, and led engines. • Participated in board bring-up for multiple Qualcomm chipsets. • Developed and maintained application support for userspace components (e.g. touchpanel firmware flashing). • Worked on-site in Asia on multiple occasions to support hardware bring-up, touchpanel hardware validation/calibration, and to provide kernel and bootloader support for prototype builds of the Pixi and Veer. • Investigated and resolved release critical bugs in various core components of webOS in a timely manner. Twenty First Century Communications Infrastructure Intern Jun 2007 to Mar 2008 • Responsible for Linux and Solaris systems, as well as the deployment and maintenance of thin client solutions. • Maintained existing C and Perl code bases and developed new software to better manage infrastructure systems. ATS: Intelligent Discovery Engineering Intern Jun 2006 to Dec 2006 • Developed application features in C++ and Java for multiple platforms. -

GO!Notifylink Palm Webos Solution
GO!NotifyLink Palm webOS Solution User Guide What’s in this document This document: Lists software requirements Provides instructions for creating the required Microsoft Exchange® mail account on the device Provides information for getting started using the GO!NotifyLink ActiveSync solution for Palm® webOSTM devices Requirements 1 Table of Contents Requirements 3 Account Setup Instructions 4 Account Maintenance 7 Settings 8 Synchronization Settings .............................................................................................. 8 Accessing the GO!NotifyLink Client Web ..................................................................... 9 Email and PIM Settings ............................................................................................... 10 Security Settings ......................................................................................................... 11 Using Your Device 13 Mail .............................................................................................................................. 13 Sending Email ................................................................................................ 13 Reading Email ................................................................................................ 15 Calendar ...................................................................................................................... 18 Contacts ...................................................................................................................... 21 -

Portable Power Max 16,000 Mah Backup Battery ITEM No
www.dreamGEAR.net | www.iSound.net 20001 S. Western Avenue, Torrance, CA 90501 tel: 310.222.5522 :: fax: 310.222.5577 Portable Power Max 16,000 mAh Backup Battery ITEM No. - DGIPAD-4544 UPC - 8 45620 04544 0 1 Inch 5.75 Inches COLOR - Black & Silver PRODUCT FEATURES Flashlight Switch The Portable Power Max is the only back up power supply you will ever Built-in again need while on the road. With its compact design and powerful Flashlight battery, you can squeeze more talk time and photos into multiple devices. The 5 USB ports allow you to charge and power any USB powered device, and the included USB to mini and micro USB cable means you don't have to carry around cables for each device. LED indicators let you know how much power is remaining, and a flashlight is built in to help you LED Charge & Power Status Indicator in the dark. 3.25 Inches • Battery with 16000 mAh (60 Wh) Power • Up to 480 hours of power for 5 USB powered devices simultaneously Switch • Includes 5 USB ports for charging iPods, iPhones, iPads and any other Weight USB powered devices 14.6 oz • LED indicator for charging & power status • Power switch and LED status indicator • 100 / 240V AC adapter included • Built-in flashlight Includes 100 / 240V AC Adapter 5 USB Ports 1 USB to Mini USB / Micro USB Includes BlackBerry Adapter Cable included PRODUCT SPECIFICATIONS Portable Power Max Capacity: 16000 mAh Portable Power iPhone 4 iPad iPod Touch iPhone 3G iPhone 3GS TRANSLATIONS Max Number of 5x 1x 9x 7x 6x PACKAGING | COMPLETE FRENCH: Yes | SPANISH: Yes Charges* USER GUIDE | COMPLETE FRENCH: Yes | SPANISH: Yes *Number of times you can charge that single device from a fully charged Portable Power Max. -

EASY USE Lagerprodukte Aktualisiert Donnerstag, Den 19
EASY USE Lagerprodukte Aktualisiert Donnerstag, den 19. März 2020 um 16:07 Uhr EASY USE - Produkt-/ Lagerliste Stand: 15.03.2020 ( Preisanpassungen vorbehalten ) Alle Preise inkl. MwSt., zzgl. Versand Aktuelle Lager-Artikel - bestellbar per Mail an [email protected] oder Tel.: 08551 9139319 Artikelnr. Kurztext Matchcode HPDOCKU565 HP USB Docking Cradle f. Jornada 560 Serie (565,568) mit USB-Kabel F2903A FXC371BATCE Batteriefachabdeckung f. iPAQ rx3715 verwendet mit extended AkkuFXC371BATCE FXC65COVT HP Screen Protector f. iPAQ hw6000 Serie (hw6510, hw6515, hw6910, 398326-001 hw6915) HP39XACR HP Netzteil f. iPAQ h3800, h3900, h1900, h2200, h6300, hx4700, 389145-021 hx2000, rz1700, 253628-021 rx3700, hw6000, h5000 FXC221IRC Ersatzteil : Abdeckung schwarz über Infrarot Port f. iPAQ h2200 FXC221IRCSerie (h2210, h2215) HP651DOCK HP Docking Cradle USB f. hw6000 Serie (hw6510, hw6515, hw6910, 383749-001 hw6915) 366854-005 370526-007 1 / 94 EASY USE Lagerprodukte Aktualisiert Donnerstag, den 19. März 2020 um 16:07 Uhr RPL19XBAT HP Standard Akku f. iPAQ h1900 Serie (h1910,h1930,h1940) 900mAh FA114A Li-Ion 311315-B21 311340-001 311349 HP170PENS HP 3er Pack Stifte f. iPAQ hx2000, rz1710, rx3715, hx4700, hw6000 FA261A Serien 367202-001 FXCHX241BATCE Batteriefachabdeckung f. iPAQ hx2000 Serie verwendet mit extended FXCHX241BATCE Akku HPGLANUSB3A HP USB 3.0 kompatibel 2.0 an Gigabit LAN RJ45 Adapter N7P47AA 829834-001 829941-001 HPSP65BLTC HP Gürtelhalterung mit Clip schwarz f. iPAQ hw6000 Serie (hw6510, 383744-001 hw6515, hw6910, hw6915) HPNB4720KITL HP Tastatur international / US Englisch f. ProBook4720s 598692-B31 HPSP65HEADP HP Headphone mit Mikrophonef. hw6000 Serie + Voice Messenger 383748-001 514 445667-001 2 / 94 EASY USE Lagerprodukte Aktualisiert Donnerstag, den 19.