OS/2 Server Transitionsition
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Illustrated Tutorial: Creating a Bootable USB Flash Drive for Windows XP
Illustrated tutorial: Creating a bootable Version 1.0 February 15, 2007 USB flash drive for Windows XP By Greg Shultz The ability to boot Windows XP from a USB Flash Drive (UFD) offers endless possibilities. For example, you might make an easy-to-use troubleshooting tool for booting and analyzing seemingly dead PCs. Or you could transport your favorite applications back and forth from home to work without having to install them on both PCs. However, before you can create a bootable UFD, you must clear a few hurdles. You saw that one coming didn’t you? The first hurdle is having a PC in which the BIOS will allow you to configure the USB port to act as a bootable device. The second hurdle is having a UFD that that will work as a bootable device and that’s large enough and fast enough to boot an operating system such as Windows XP. The third hurdle is finding a way to condense and install Windows XP on a UFD. If you have a PC that was manufactured in the last several years, chances are that its BIOS will allow you to configure the USB port to act as a bootable device. If you have a good qual- ity UFD that’s at least 512 KB and that was manufactured in the last couple of years, you’ve probably cleared the second hurdle. And once you’ve cleared those first two hur- dles, the third one is a piece of cake. All you have to do is download and run some free soft- ware to create the bootable UFD. -

11.7 the Windows 2000 File System
830 CASE STUDY 2: WINDOWS 2000 CHAP. 11 11.7 THE WINDOWS 2000 FILE SYSTEM Windows 2000 supports several file systems, the most important of which are FAT-16, FAT-32, and NTFS (NT File System). FAT-16 is the old MS-DOS file system. It uses 16-bit disk addresses, which limits it to disk partitions no larger than 2 GB. FAT-32 uses 32-bit disk addresses and supports disk partitions up to 2 TB. NTFS is a new file system developed specifically for Windows NT and car- ried over to Windows 2000. It uses 64-bit disk addresses and can (theoretically) support disk partitions up to 264 bytes, although other considerations limit it to smaller sizes. Windows 2000 also supports read-only file systems for CD-ROMs and DVDs. It is possible (even common) to have the same running system have access to multiple file system types available at the same time. In this chapter we will treat the NTFS file system because it is a modern file system unencumbered by the need to be fully compatible with the MS-DOS file system, which was based on the CP/M file system designed for 8-inch floppy disks more than 20 years ago. Times have changed and 8-inch floppy disks are not quite state of the art any more. Neither are their file systems. Also, NTFS differs both in user interface and implementation in a number of ways from the UNIX file system, which makes it a good second example to study. NTFS is a large and complex system and space limitations prevent us from covering all of its features, but the material presented below should give a reasonable impression of it. -

Page 1 of 3 How to Enable NTLM 2 Authentication 2/8/2012 Http
How to enable NTLM 2 authentication Page 1 of 3 Article ID: 239869 - Last Review: January 25, 2007 - Revision: 4.7 How to enable NTLM 2 authentication System Tip This article applies to a different version of Windows than the one you are using. Content in this article may not be relevant to you. Visit the Windows 7 Solution Center This article was previously published under Q239869 SUMMARY Historically, Windows NT supports two variants of challenge/response authentication for network logons: • LAN Manager (LM) challenge/response • Windows NT challenge/response (also known as NTLM version 1 challenge/response) The LM variant allows interoperability with the installed base of Windows 95, Windows 98, and Windows 98 Second Edition clients and servers. NTLM provides improved security for connections between Windows NT clients and servers. Windows NT also supports the NTLM session security mechanism that provides for message confidentiality (encryption) and integrity (signing). Recent improvements in computer hardware and software algorithms have made these protocols vulnerable to widely published attacks for obtaining user passwords. In its ongoing efforts to deliver more secure products to its customers, Microsoft has developed an enhancement, called NTLM version 2, that significantly improves both the authentication and session security mechanisms. NTLM 2 has been available for Windows NT 4.0 since Service Pack 4 (SP4) was released, and it is supported natively in Windows 2000. You can add NTLM 2 support to Windows 98 by installing the Active Directory Client Extensions. After you upgrade all computers that are based on Windows 95, Windows 98, Windows 98 Second Edition, and Windows NT 4.0, you can greatly improve your organization's security by configuring clients, servers, and domain controllers to use only NTLM 2 (not LM or NTLM). -

Introduction to Tivoli Enterprise Data Warehouse
Front cover Introduction to Tivoli Enterprise Data Warehouse Insider’s guide to Tivoli Enterpise Data Warehouse Best practices for creating data marts Integration with all major OLAP tools Vasfi Gucer William Crane Chris Molloy Sven Schubert Roger Walker ibm.com/redbooks International Technical Support Organization Introduction to Tivoli Enterprise Data Warehouse May 2002 SG24-6607-00 Take Note! Before using this information and the product it supports, be sure to read the general information in “Notices” on page xvii. First Edition (May 2002) This edition applies to Tivoli Enterprise Data Warehouse Version 1.1. Comments may be addressed to: IBM Corporation, International Technical Support Organization Dept. JN9B Building 003 Internal Zip 2834 11400 Burnet Road Austin, Texas 78758-3493 When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. © Copyright International Business Machines Corporation 2002. All rights reserved. Note to U.S Government Users – Documentation related to restricted rights – Use, duplication or disclosure is subject to restrictions set forth in GSA ADP Schedule Contract with IBM Corp. Contents Figures . .ix Tables . xv Notices . xvii Trademarks . xviii Preface . xix The team that wrote this redbook. xx Notice . xxi Comments welcome. xxii Chapter 1. Introducing building blocks. 1 1.1 Business Intelligence. 2 1.2 Business driving forces . 2 1.3 Main Business Intelligence terms . 3 1.3.1 Operational databases . 4 1.3.2 Online transaction processing (OLTP) . 4 1.3.3 Data warehouse . 5 1.3.4 Data mart . -

IBM Tivoli Endpoint Manager for Patch Management Continuous Patch Compliance Visibility and Enforcement
IBM Software Data Sheet Tivoli IBM Tivoli Endpoint Manager for Patch Management Continuous patch compliance visibility and enforcement With software and the threats against that software constantly evolving, Highlights organizations need an effective way to assess, deploy and manage a con- stant flow of patches for the myriad operating systems and applications in ● Automatically manage patches for multi- their heterogeneous environments. For system administrators responsible ple operating systems and applications across hundreds of thousands of end- for potentially tens or hundreds of thousands of endpoints running vari- points regardless of location, connection ous operating systems and software applications, patch management type or status can easily overwhelm already strained budgets and staff. IBM Tivoli® ● Reduce security and compliance risk by Endpoint Manager for Patch Management balances the need for fast slashing remediation cycles from weeks deployment and high availability with an automated, simplified patching to days or hours process that is administered from a single console. ● Gain greater visibility into patch compli- ance with flexible, real-time monitoring Tivoli Endpoint Manager for Patch Management, built on BigFix® and reporting technology, gives organizations access to comprehensive capabilities ● Provide up-to-date visibility and control for delivering patches for Microsoft® Windows®, UNIX®, Linux® and from a single management console Mac operating systems, third-party applications from vendors including Adobe®, Mozilla, Apple and Java™, and customer-supplied patches to endpoints—regardless of their location, connection type or status. Endpoints can include servers, laptops, desktops, and specialized equip- ment such as point-of-sale (POS) devices, ATMs, and self-service kiosks. Apply only the correct patches to the correct endpoint One approach to patch management is to create large patch files with a large update “payload” and distribute them to all of the endpoints, regardless of whether they already have all of the patches or not. -

Exploring the Windows Server 2008 Interface
LAB 1 EXPLORING THE WINDOWS SERVER 2008 INTERFACE This lab contains the following projects and activities: Project 1.1 Modifying Basic Server Settings Project 1.2 Configuring TCP/IP Settings Project 1.3 Configuring a Second Windows Server 2008 Computer (Optional) Project 1.4 Configuring a Windows Server 2008 Server Core Computer (Optional) Lab Review Questions Lab Challenge Verifying Active Directory SRV Records 1.1 COPYRIGHTED MATERIAL BEFORE YOU BEGIN Lab 1 assumes that setup has been completed as specified in the setup document and that your computer has connectivity to other lab computers and the Internet. To perform all projects in Lab 1, you will need: • Two (2) full installations of Windows Server 2008 • One (1) Server Core installation of Windows Server 2008 2 Microsoft Windows Server 2008 Active Directory Configuration For subsequent labs, optional projects are provided that involve a second server running the full GUI version of Windows Server 2008 to be configured as a Read- Only Domain Controller and a third server running Windows Server 2008 Server Core. You can use multiple physical computers, or you can use Microsoft Virtual PC or Virtual Server to install and run multiple servers on a single machine. This manual assumes that you are using multiple virtual machines under Microsoft Virtual PC. In the optional projects for this lab, Projects 1.3 and 1.4, you will configure the second and third servers necessary to perform the optional projects in future lessons. The instructor PC is preconfigured as a domain controller in the lucernepublishing.com domain for demonstration purposes; it is named INSTRUCTOR01. -

When Windows 2000 Or Windows Server 2003 Is Introduced
IMPORTANT INFORMATION FOR PRIMERGY CUSTOMERS July 11th, 2007 FUJITSU, LTD. NOTICE: Any server using an Intel Xeon 7100 or higher model CPU and has either Windows 2000, Windows 2000 Server, or Windows 2003 Server installed may encounter a “blue screen.” The problem occurs when the operating system running on a computer with a fast processor and a large L3 cache encounters a timing problem with asynchronous hardware. Although Fujitsu has not received any reports of this problem to date, there is a possibility that PRIMERGY server products may be affected. Problem: Any computer running any edition of Windows 2000, Windows 2000 Server, or Windows 2003 with an Intel Xeon processor (model 7100 or higher) that utilizes a large L3 cache may generate a “blue screen.” An error similar to: STOP 0x0000008E(parameter1, parameter2, parameter3, parameter4) KERNEL_MODE_EXCEPTION_NOT_HANDLED or STOP 0x0000001E(parameter1, parameter2, parameter3, parameter4) KERNEL_MODE_EXCEPTION_NOT_HANDLED may be displayed with Windows 2003-based and Windows 2000-based computers, respectively. Affected Operating Systems: Microsoft® Windows® 2000 Server Microsoft® Windows® 2000 Advanced Server Microsoft® Windows Server® 2003, Standard Edition (*) Microsoft® Windows Server® 2003, Enterprise Edition (*) (*)This problem has been corrected in Service Pack 1 for Windows Server 2003. Therefore Windows 2003 Server SP1 is not affected by this problem. Affected Fujitsu PRIMERGY models: The following models use Intel Xeon 7100 or higher processors. PRIMERGY Models, Product Codes, and CPU z PRIMERGY RX600 S3 (SAS), Product codes PGR603D* and PGR603B* ¾ Dual Core Intel® Xeon® Processor 7140M (3.40GHz)/7120M (3GHz) z PRIMERGY RX600 S3, Product codes PGR6038* and PGR6036* ¾ Dual Core Intel® Xeon® Processor 7140M (3.40GHz)/7120M (3GHz) * Changes by type. -
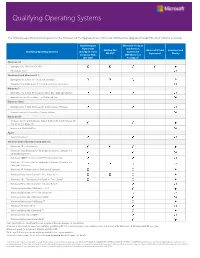
Qualifying Operating Systems
Qualifying Operating Systems The following operating systems qualify for the Windows 10 Pro Upgrade and/or Windows 10 Enterprise Upgrade through Microsoft Volume Licensing. New Enterprise Microsoft Products Agreement and Services Existing EA/ Microsoft Cloud Academic and Qualifying Operating Systems (EA)/Open Value Agreement OV-CW2 Agreement Charity Company-Wide (MPSA)/Select (OV-CW)1 Plus/Open3 Windows 10 4 Enterprise (N, KN) , Pro (N, KN) Education, Home Windows 8 and Windows 8.1 Enterprise (N, K, KN), Pro (N, K, KN, diskless) Windows 8 and Windows 8.1 (including Single Language) Windows 7 Enterprise (N, K, KN), Professional (N, K, KN, diskless), Ultimate Home Premium, Home Basic, or Starter Edition Windows Vista Enterprise (N, K, KN), Business (N, K, KN, Blade), Ultimate Home Premium, Home Basic, Starter Edition Windows XP Professional (N, K, KN, Blade), Tablet Edition (N, K, KN, Blade), XP Pro N, XP Pro Blade PC Home and Starter Edition Apple Apple Macintosh Windows Embedded Operating Systems Windows 10 IoT Enterprise Windows Vista Business for Embedded Systems, Ultimate for Embedded Systems Windows 2000 Professional for Embedded Systems Windows 7 Professional for Embedded Systems, Ultimate for Embedded Systems Windows XP Professional for Embedded Systems Windows Embedded 8 and 8.1 Pro, Industry Pro Windows 10 IoT Enterprise for Retail or Thin Clients5 5 Windows Embedded 8 and 8.1 Industry Retail Windows Embedded POSReady 7 Pro5 5 Windows Embedded for Point of Service Windows Embedded POSReady 20095 5 Windows Embedded POSReady 7 5 Windows XP Embedded Windows Embedded Standard 75 5 Windows Embedded 2009 5 Windows Embedded 8 Standard 1Also applicable to Qualified Devices acquired through merger or acquisition. -

Windows 2000 Accessibility Options
© 2004 Microsoft Corporation Step By Step Tutorials for Microsoft® Windows 2000 Accessibility Options Step by Step Tutorials for Microsoft Windows 2000 Accessibility Options Table of Contents Overview .................................................................................................................................. 4 Using the Accessibility Wizard ............................................................................................... 6 Opening Accessibility Wizard ............................................................................................... 7 Changing the Font Size of Text on the Screen ...................................................................... 9 Switching to a Lower Screen Resolution to Increase the Size of Items on the Screen ....... 10 Changing the Size of Items on the Screen ........................................................................... 11 Disabling Personalized Menus ............................................................................................ 13 Setting Options for People Who Are Blind or Have Difficulty Seeing Things on the Screen ............................................................................................................................................. 14 Setting Options for People Who Are Deaf or Have Difficulty Hearing Sounds from the Computer ............................................................................................................................. 16 Setting Options for People Who Have Difficulty Using the Keyboard -

Introduction to Microsoft Core Licensing Models
Licensing brief October 2020 Introduction to Microsoft Core licensing models This brief applies to all Microsoft Licensing programs. Contents Summary ...................................................................................................................................................................................................................... 1 Definitions ................................................................................................................................................................................................................... 2 Introduction to Per Core Licensing ................................................................................................................................................................... 4 Per Core licensing model ............................................................................................................................................................................. 5 Per Core/CAL licensing model ................................................................................................................................................................... 5 Management Servers licensing model ................................................................................................................................................... 6 SQL Server ............................................................................................................................................................................................................. -

Monitoring Windows with Powershell
Monitoring Windows Systems with PowerShell SL1 version 8.14.0 Table of Contents Introduction 4 Monitoring Windows Devices in the ScienceLogic Platform 5 What is SNMP? 5 What is PowerShell? 5 PowerPacks 6 Configuring Windows Systems for Monitoring with SNMP 7 Configuring SNMP for Windows Server 2016 and Windows Server 2012 8 Configuring Ping Responses 8 Installing the SNMP Service 9 Configuring the SNMP Service 14 Configuring the Firewall to Allow SNMP Requests 19 Configuring Device Classes for Windows Server 2016 and Windows 10 19 Manually Align the Device Class 20 Edit the Registry Key 20 Configuring SNMP for Windows Server 2008 21 Configuring Ping Responses 21 Installing the SNMP Service 22 Configuring the SNMP Service 25 Configuring the Firewall to Allow SNMP Requests 30 Configuring Windows Servers for Monitoring with PowerShell 31 Prerequisites 32 Configuring PowerShell 32 Step 1: Configuring the User Account for the ScienceLogic Platform 33 Option 1: Creating an Active Directory Account with Administrator Access 33 Option 2: Creating a Local User Account with Administrator Access 34 Option 3: Creating a Non-Administrator User Account 34 Optional: Configuring the User Account for Remote PowerShell Access to Microsoft Exchange Server 36 Optional: Configuring the User Account for Remote PowerShell Access to Hyper-V Servers 36 Creating a User Group and Adding a User in Active Directory 36 Setting the Session Configuration Parameters and Group Permissions 37 Creating a PowerShell Credential 38 Optional: Configuring the User Account for -

Win Xp Pe Iso Download
Win Xp Pe Iso Download 1 / 4 Win Xp Pe Iso Download 2 / 4 3 / 4 Download Files. Download PEbuilder 3.1.10 File: Download PEbuilder 3.1.10 File. BartPE Iso WINXP Emulated Version 155MB: .... To start working with WinPE, download and install both the Windows ... To learn how to create a bootable WinPE CD, DVD, ISO, or VHD, see .... A tutorial on installing BartPE onto a bootable USB drive. ... but instead of going straight into the BartPE OS, it loaded the BartPE ISO file into the ... Secondly, download Microsoft's Windows Server 2003 SP1 installation file (this can ... This utility has the ability to properly format a USB disk & install a Windows XP boot sector.. Jump to Boot WinPE/BartPE from an ISO file - Download firadisk.gz from the Beta ... For example, for the Avast BartPE ISO you can use a .... Download BartPE builder from http://www.nu2.nu/pebuilder/ ... When it's done building, image file "c:\pebuilder\pebuilder.iso" should be created properly.. Use Windows 7/XP ISO File or DVD to Create Bootable Install USB Drive ... it also allows you transfer Windows PE( Windows XP / Windows 7 / Vista / 2003 / 2008 ) to usb pen drive in a few clicks. ... Download it from softpedia.. Here we show you 5 Windows PE based boot discs to help technicians and ... disc is fully automated including the downloading of the Windows ISO image file.. 1.1 USB Drive; 1.2 BIOS/UEFI configuration; 1.3 ISO image ... If not, download BartPE; The original CD of Windows XP Professional, not a Windows XP Home ...