IBM Spectrum Protect Plus: Installation and User's Guide What's New in Version 10.1.6
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Towards a Verified Range Analysis for Javascript Jits
Towards a Verified Range Analysis for JavaScript JITs Fraser Brown John Renner Andres Nötzli Stanford, USA UC San Diego, USA Stanford, USA Sorin Lerner Hovav Shacham Deian Stefan UC San Diego, USA UT Austin, USA UC San Diego, USA Abstract Earlier this year, Google’s Threat Analysis Group identi- We present VeRA, a system for verifying the range analysis fied websites, apparently aimed at people “born in a certain pass in browser just-in-time (JIT) compilers. Browser devel- geographic region” and “part of a certain ethnic group,” that opers write range analysis routines in a subset of C++, and would install a malicious spyware implant on any iPhone verification developers write infrastructure to verify custom used to visit them. Two bugs exploited in this campaign, analysis properties. Then, VeRA automatically verifies the according to analysis by Google’s Project Zero [41, 68], were range analysis routines, which browser developers can in- in the JIT component of Safari’s JavaScript engine [5, 34]. tegrate directly into the JIT. We use VeRA to translate and The JavaScript JITs shipped in modern browsers are ma- verify Firefox range analysis routines, and it detects a new, ture, sophisticated systems developed by compilers experts. confirmed bug that has existed in the browser for six years. Yet bugs in JIT compilers have emerged in recent months as the single largest threat to Web platform security, and the CCS Concepts: • Security and privacy ! Browser se- most dangerous attack surface of Web-connected devices. curity; • Software and its engineering ! Just-in-time Unlike other compilers, browser JITs are exposed to adver- compilers; Software verification and validation; Domain sarial program input. -

Understanding the Attack Surface and Attack Resilience of Project Spartan’S (Edge) New Edgehtml Rendering Engine
Understanding the Attack Surface and Attack Resilience of Project Spartan’s (Edge) New EdgeHTML Rendering Engine Mark Vincent Yason IBM X-Force Advanced Research yasonm[at]ph[dot]ibm[dot]com @MarkYason [v2] © 2015 IBM Corporation Agenda . Overview . Attack Surface . Exploit Mitigations . Conclusion © 2015 IBM Corporation 2 Notes . Detailed whitepaper is available . All information is based on Microsoft Edge running on 64-bit Windows 10 build 10240 (edgehtml.dll version 11.0.10240.16384) © 2015 IBM Corporation 3 Overview © 2015 IBM Corporation Overview > EdgeHTML Rendering Engine © 2015 IBM Corporation 5 Overview > EdgeHTML Attack Surface Map & Exploit Mitigations © 2015 IBM Corporation 6 Overview > Initial Recon: MSHTML and EdgeHTML . EdgeHTML is forked from Trident (MSHTML) . Problem: Quickly identify major code changes (features/functionalities) from MSHTML to EdgeHTML . One option: Diff class names and namespaces © 2015 IBM Corporation 7 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Method) © 2015 IBM Corporation 8 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Examples) . Suggests change in image support: . Suggests new DOM object types: © 2015 IBM Corporation 9 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Examples) . Suggests ported code from another rendering engine (Blink) for Web Audio support: © 2015 IBM Corporation 10 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Notes) . Further analysis needed –Renamed class/namespace results into a new namespace plus a deleted namespace . Requires availability -

Platform Support Matrix for SAP Business
Platform Support Matrix PUBLIC SAP Business One Document Version: 1.28 – 2021-05-07 SAP Business One Platform Support Matrix Release 9.0 and higher Typographic Conventions Type Style Description Example Words or characters quoted from the screen. These include field names, screen titles, pushbuttons labels, menu names, menu paths, and menu options. Textual cross-references to other documents. Example Emphasized words or expressions. EXAMPLE Technical names of system objects. These include report names, program names, transaction codes, table names, and key concepts of a programming language when they are surrounded by body text, for example, SELECT and INCLUDE. Example Output on the screen. This includes file and directory names and their paths, messages, names of variables and parameters, source text, and names of installation, upgrade and database tools. Example Exact user entry. These are words or characters that you enter in the system exactly as they appear in the documentation. <Example> Variable user entry. Angle brackets indicate that you replace these words and characters with appropriate entries to make entries in the system. EXAMPLE Keys on the keyboard, for example, F2 or ENTER. PUBLIC © 2021 SAP SE or an SAP affiliate company. All SAP Business One Platform Support Matrix 2 rights reserved. Typographic Conventions Document History Version Date Change 1.0 2014-02-12 Release Version 1.01 2014-05-08 SAP Note 1787431 link added on XL Reporter platform support restrictions 1.02 2014-07-08 SAP Business One 9.1 added to the overview -

Ricki-Lee - Edge of Glory (LIVE Piano Version)
ai - edgeum - Ricki-Lee - Edge Of Glory (LIVE Piano Version) Select a Language - Microsoft Edge, now available on Android, creates one continuous browsing experience for Windows 10 users across their devices. Content and data sync seamlessly in the background, so users can browse across devices, without skipping a beat. Business Grants For Scottish Entrepreneurs | Scottish EDGE Inspired by the NAAEE mission, Microsoft Edge worked with the NAAEE to develop a web experience for innovators in environmental education and literacy to demonstrate the positive impact they have h... Microsoft Support My saves. My interests / All saves 0. Recipes Images Videos News My places. Collections + New. Help. All saves. 1/2. See all of your saved results, starting with the most recent. Next Close. All saves. Moderate. You haven't saved anything yet. From the Bing search results, select the to save a result here. Samsung Galaxy S7 and S7 edge - The Official Samsung ... The Microsoft Edge DevTools are built with TypeScript, powered by open source, optimized for modern front-end workflows, and now available as a standalone Windows 10 app in the Microsoft Store! For more on the latest features, check out DevTools in the latest update of Windows 10 (EdgeHTML 18). Test ... 2018 Ford Edge SUV | Sporty Utility for Unstoppable ... Noun. They peered over the edge of the roof. The fabric was frayed at the edge. He made us all nervous by standing so close to the edge of the cliff. She sat on the edge of the counter, swinging her legs. the edge of an ax His voice had a sarcastic edge. -

Ansys SCADE Lifecycle®
EMBEDDED SOFTWARE Ansys SCADE LifeCycle® SCADE LifeCycle is part of the Ansys Embedded Software family of products and solutions that includes modules providing unique support for application lifecycle management. This product line features requirements traceability via Application Lifecycle Management (ALM) tools, traceability from models, configuration and change management, and automatic documentation generation. SCADE LifeCycle enhances the functionalities of Ansys SCADE® tools with add-on modules that bridge SCADE solutions and Requirement Management tools or PLM/ALM (Product Lifecycle Management/ Application Lifecycle Management) tools. With SCADE LifeCycle, all systems and software teams involved in critical applications development can manage and control their design and verification activities across the full life cycle of their SCADE applications. / Requirements Traceability SCADE LifeCycle Application Lifecycle Management (ALM) Gateway provides an integrated traceability analysis solution for safety-critical design processes with SCADE Architect, SCADE Suite, SCADE Display, SCADE Solutions for ARINC 661 and SCADE Test: • Connection to ALM tools: linkage to DOORS NG, DOORS (9.6 and up) Jama Connect, Siemens Polarion, Dassault Systèmes Reqtify 2016. • Graphical creation of traceability links between requirements or other structured documents and SCADE models. • Traceability of test cases from SCADE Test Environment projects. • Bidirectional navigation across requirements and tests. • Customizable Export of SCADE artifacts to DOORS or Jama Connect. • Compliant with DO-178B, DO-178C, EN 50128, IEC 61508, ISO 26262, and IEC 60880 standards. EMBEDDED SOFTWARE / SCADE LifeCycle® // 1 / Project Documentation Generation SCADE LifeCycle Reporter automates the time-consuming creation of detailed and complete reports from SCADE Suite, SCADE Display, SCADE Architect and SCADE UA Page Creator for ARINC 661 designs through: • Generation of reports in RTF or HTML formats. -

Configuration Management for Distributed Development
Software Configuration Management Configuration Management for Distributed Development By Nina Rajkumar. © Think Business Networks Pvt. Ltd., July 2001 All rights reserved. You may make one attributed copy of this material for your own personal use. For additional information or assistance please contact Nina at (+91)422-320-606. www.thinkbn.com • 697A, Trichy Road, Coimbatore, TN 641045. Table of Contents Configuration Management for Distributed Development.............................. 4 Configuration Management ................................................................................ 5 Distributed Development.................................................................................... 5 Cases of Distributed Development ..................................................................... 6 Distance Working ........................................................................................... 6 Outsourcing..................................................................................................... 6 Co-located Groups .......................................................................................... 7 Distributed Groups.......................................................................................... 7 Architecture ........................................................................................................ 8 Remote Login.................................................................................................. 8 Several sites by Master-Slave connections .................................................... -

Download Har File Viewer
download har file viewer Download har file viewer. Если вы не знаете, как получить HAR-файл, ознакомьтесь с инструкцией на странице загрузки для трех самых распространенных браузеров: Chrome, Firefox и Internet Explorer. Нажмите кнопку выбора файла. Выберите HAR-файл для анализа. Воспользуйтесь ей, чтобы выбрать файл для анализа. Записи могут быть показаны вместе или с разбивкой по страницам. Временные метки записей в таблице могут быть относительными или абсолютными. В первом режиме метки, которые соответствуют каждой записи, располагаются на временной шкале обработки страницы, а во втором метка каждой записи занимает всю ширину столбца. Относительный режим используется только при группировке записей по страницам. – полезный инструмент, позволяющий выполнять сложный поиск в HAR-записях. Самый простой способ поиска – ввести несколько поисковых слов, например [получить диск]. В результате будут найдены записи, содержащие все эти слова в ответе и запросе. Обратите внимание, что словосочетания в кавычках обрабатываются как единый поисковый запрос, поэтому для запроса [неделя "количество событий"] будут показаны результаты, где есть фраза "количество событий". Кроме того, поисковые запросы могут быть представлены парами "поле – поисковая фраза", например [requst.url:поисковая_фраза request.method:поисковая_фраза response.status:поисковая_фраза]. Для более сложного поиска можно использовать операторы, создавать группы и указывать поля. Оператор влияет на непосредственно следующую за ним поисковую фразу, изменяя способ ее поиска в целой группе или запросе. Поддерживаемые операторы: & : оператор по умолчанию, выполняющий операцию AND для результатов следующего поискового запроса и результатов всех предыдущих операций. | : выполняет операцию OR для результатов следующего поискового запроса и результатов всех предыдущих операций. ^ : выполняет операцию XOR для результатов следующего поискового запроса и результатов всех предыдущих операций. - : исключает результаты следующего поискового запроса. Выберите HAR-файл. -
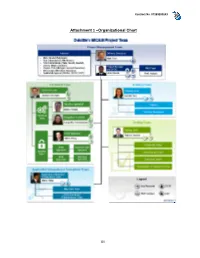
85 Attachment 1 –Organizational Chart
Contract No. 071B3200143 Attachment 1 –Organizational Chart 85 Contract No. 071B3200143 Appendix A - Breakdown of Hardware and Related Software Table 1: Hardware Cost ($): State Brand, Model # Item Specifications will provide from Comments and Description existing Contracts Total # of Virtual The hardware is Machines: 48 sized for Production, QA/Staging, Secure-24 VMware Total # of Virtual Development, and Cluster Access for CPUs: 96 Sandbox Server deploying ISIM, environments in the ISAM and ISFIM Total Virtual RAM: primary data center components 416 GB and for Production, and QA environments in the OS: RedHat Linux secondary data 6.x center The total storage is estimated for Total Storage: 35.7 Production, , TB QA/Staging, Development and Enterprise Class Sandbox Storage (3.8TB of Bronze SAN Storage Tier, 15.8TB of environments in the Silver Tier, 5.1TB of primary data center Logs Tier, 11TB of and for Production, Gold Tier) QA environments in the secondary data center CD/DVD Backup Device None None Rack w/ Power Supply Rack mountable Redundant Power Screen None None A total of 10 Web Gateway appliances are estimated for Production, QA/Staging, Web Gateway Development and Any other Hardware (list) v7.0 Hardware Appliance Sandbox environments in the primary data center and for Production, QA environments in the secondary data center. TOTAL $ 86 Contract No. 071B3200143 Table 2: Related Software Software Component Product Name Cost ($): State # of Licenses Comments License and Version will provide from existing Contracts Contractor user laptops already include this software. We will reuse the Report writers MS Office 2010 State owned software State of Michigan user licenses laptops will need this software for up to 4 users. -

Using Visual COBOL in Modern Application Development Micro Focus the Lawn 22-30 Old Bath Road Newbury, Berkshire RG14 1QN UK
Using Visual COBOL in Modern Application Development Micro Focus The Lawn 22-30 Old Bath Road Newbury, Berkshire RG14 1QN UK http://www.microfocus.com © Copyright 2018-2020 Micro Focus or one of its affiliates. MICRO FOCUS, the Micro Focus logo and Visual COBOL are trademarks or registered trademarks of Micro Focus or one of its affiliates. All other marks are the property of their respective owners. 2020-08-25 ii Contents Using Visual COBOL in Modern Application Development ........................... 4 Introduction to Modern Application Development ................................................................4 What is Modern Application Development? ..............................................................4 Key Concepts in Modern Application Development ..................................................5 Steps Involved in Modern Application Development ................................................ 6 Agile Methods ..................................................................................................................... 7 Introduction to Agile Methods ...................................................................................7 Agile Development Workflow ....................................................................................7 Agile Development and Micro Focus Development Tools .........................................9 Continuous Integration ...................................................................................................... 11 Introduction to Continuous Integration .................................................................. -

Revision Control Solutions to Protect Your Documents and Track Workflow
Revision Control Solutions to Protect Your Documents and Track Workflow WHITE PAPER Contents Overview 3 Common Revision Control Systems 4 Revision Control Systems 4 Using BarTender with Revision Control Systems 4 Limitations of Windows Security 5 Librarian 6 Librarian Features 6 Benefits of Using Librarian with BarTender 7 File States, Publishing and Workflow in Librarian 8 Don’t Forget About Security! 9 Related Documentation 10 Overview A revision control system is based around the concept of tracking changes that happen within directories or files, and preventing one user from overwriting the work of another. Some revision control systems are also used to establish and track workflow for the progression of a file through a series of states. The collection of files or directories in a revision control system are usually called a repository. These systems allow you to specify a directory, file or group of files that will have their changes tracked. This frequently entails users "checking out" and "checking in" files from a repository. Changes are tracked as the user edits the folder or file; these changes will be visible to all users once the item is checked back in. Each revision is annotated with a timestamp and the person making the change. Some of the benefits of revision control include: l Automatic revision numbering for easy tracking. l Enhanced security. Not only does a "check in" and "check out" system keep one user's work from overwriting another, it can prevent unauthorized or even malicious users from accessing a document. l Some revision control systems include publishing "states," which allow you to track the publishing progress of a document and establish a logical, traceable workflow. -

Nextflow Documentation
Nextflow Documentation Release 0.30.2 Paolo Di Tommaso Jul 12, 2018 Contents 1 Get started 3 1.1 Requirements...............................................3 1.2 Installation................................................3 1.3 Your first script..............................................3 2 Basic concepts 7 2.1 Processes and channels..........................................7 2.2 Execution abstraction..........................................8 2.3 Scripting language............................................9 2.4 Configuration options..........................................9 3 Pipeline script 11 3.1 Language basics............................................. 11 3.2 Closures................................................. 14 3.3 Regular expressions........................................... 15 3.4 Files and I/O............................................... 17 4 Processes 27 4.1 Script................................................... 28 4.2 Inputs................................................... 32 4.3 Outputs.................................................. 39 4.4 When................................................... 44 4.5 Directives................................................. 44 5 Channels 63 5.1 Channel factory............................................. 63 5.2 Binding values.............................................. 67 5.3 Observing events............................................. 68 6 Operators 71 6.1 Filtering operators............................................ 71 6.2 Transforming operators........................................ -

Git for the ASP.NET Programmer
git for the ASP.NET Programmer Paul Litwin Fred Hutchinson Cancer Research Center [email protected] @plitwin Slides & samples can be found here… • http://tinyurl.com/DevInt2015Oct Litwin Git for the ASP.NET Programmer 2 Session Itinerary • Why distributed version control? • git basics • Command line git • Using git from VS Code • Using git from Visual Studio • Branching and merging • Wrap up Litwin Git for the ASP.NET Programmer 3 Why distributed version control? Git is a free and open source distributed version control system designed to handle everything from small to very large projects with speed and efficiency Created by Linux creator, Linus Torvalds Litwin Git for the ASP.NET Programmer 5 The name git? “I'm an egotistical bastard, and I name all my projects after myself. First Linux, now git.” Linus Torvalds quote from 2007 Litwin Git for the ASP.NET Programmer 6 Centralized Version Control One repository using a client-server model Litwin Git for the ASP.NET Programmer 7 Distributed Version Control Many repositories using peer to peer model Litwin Git for the ASP.NET Programmer 8 Comparing centralized (tfs) vs distributed (git) Attribute Centralized Distributed TFS, SVN, PVCS git, Mercurial Repositories 1 Many Model Client-server Peer-to-peer Speed of common Slower Fast against local repo operations Redundancy of system None; single point of Redundancy built in failure Offline work More difficult Easy Merging of changes When you check When you sync changes changes in (push/pull) Litwin Git for the ASP.NET Programmer 9 git Basics