Understanding User-Generated Content on Social Media
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Challenges and Benefits of Web 2.0-Based Learning Among International Students of English During the Covid-19 Pandemic in Cyprus
Arab World English Journal (AWEJ) Special Issue on Covid 19 Challenges April 2021 Pp.295-306 DOI: https://dx.doi.org/10.24093/awej/covid.22 Challenges and Benefits of Web 2.0-based Learning among International Students of English during the Covid-19 Pandemic in Cyprus Isyaku Hassan Faculty of Languages and Communication Universiti Sultan Zainal Abidin, Kuala Terengganu, Malaysia Musa BaraU Gamji Department of Mass Communication Ahmadu Bello University, Zaria, Kaduna State, Nigeria Eastern Medtrenian University (EMU), Cyprus Corresponding Author: [email protected] Qaribu Yahaya Nasidi Department of Mass Communication Ahmadu Bello University, Zaria, Kaduna State, Nigeria Mohd Nazri Latiff Azmi Faculty of Languages and Communication Universiti Sultan Zainal Abidin, Kuala Terengganu, Malaysia Received: 2/15/2021 Accepted: 3/2/2021 Published: 4/26/2021 Abstract There has been an increased reliance on Web-based learning, particularly in higher learning institutions, due to the outbreak of Covid-19. However, learners require knowledge and skills on how to use Web 2.0- based learning tools. Thus, there is a need to focus on how Web-based tools can be used to enhance learning outcomes. Therefore, this study aims to explore the challenges and benefits of Web 2.0-based learning among international students of English as a Second Language (ESL) at the Eastern Mediterranean University (EMU), North Cyprus during the Covid-19 pandemic. The data were collected from a purposive sample of 15 ESL learners at EMU using focus group interviews. The interview data were analyzed using inductive thematic analysis. The findings showed that challenges faced by international students of English at EMU during the Covid-19 pandemic include inadequate knowledge of technology and technical issues such as poor internet connectivity, inability to upload large files, and loss of password. -

The Role of User Generated Content (UGC) in Social Media for Tourism Sector
The 2013 WEI International Academic Conference Proceedings Istanbul, Turkey The Role of User Generated Content (UGC) in Social Media for Tourism Sector KhairulHilmi A Manap Phd Candidate [email protected] Nor Azura Adzharudin (PhD) Faculty of Modern Languages & Communication Universiti Putra Malaysia, Serdang, Selangor Malaysia [email protected] Abstract The existence of social media has marked a substantial milestone in the way both business enterprises and government agencies communicate and engage with their demographic markets. Social media has essentially revolutionized our communication patterns and behavior through the Internet, thus creating a new medium in which we consume and disseminate information. This paper will disclose and describe how social media can help the tourism industry leverage on User-Generated Content (UGC) generated by social media services to strategically position tourism based products and services. This paper focuses on the role of social media and its relation to the hospitality and tourism industry. This paper examines the perspective of travelers who search for online information via social media channels and make well-informed decisions of their travel based on user-generated content (UGC). The authenticity and credibility of user-generated content is also explored and discussed in this paper. This paper highlights both the benefits and issues encountered during the process of UGC to make travel decisions. The recommendation suggest that although social media channels are popular, they are not yet considered to be as a credible or trustworthy as incumbent sources of travel information. UGC plays the role as an additional source of information that travelers consider as part of their search information process, rather than as the only source of information. -

Metric Ambiguity and Flow in Rap Music: a Corpus-Assisted Study of Outkast’S “Mainstream” (1996)
Metric Ambiguity and Flow in Rap Music: A Corpus-Assisted Study of Outkast’s “Mainstream” (1996) MITCHELL OHRINER[1] University of Denver ABSTRACT: Recent years have seen the rise of musical corpus studies, primarily detailing harmonic tendencies of tonal music. This article extends this scholarship by addressing a new genre (rap music) and a new parameter of focus (rhythm). More specifically, I use corpus methods to investigate the relation between metric ambivalence in the instrumental parts of a rap track (i.e., the beat) and an emcee’s rap delivery (i.e., the flow). Unlike virtually every other rap track, the instrumental tracks of Outkast’s “Mainstream” (1996) simultaneously afford hearing both a four-beat and a three-beat metric cycle. Because three-beat durations between rhymes, phrase endings, and reiterated rhythmic patterns are rare in rap music, an abundance of them within a verse of “Mainstream” suggests that an emcee highlights the three-beat cycle, especially if that emcee is not prone to such durations more generally. Through the construction of three corpora, one representative of the genre as a whole, and two that are artist specific, I show how the emcee T-Mo Goodie’s expressive practice highlights the rare three-beat affordances of the track. Submitted 2015 July 15; accepted 2015 December 15. KEYWORDS: corpus studies, rap music, flow, T-Mo Goodie, Outkast THIS article uses methods of corpus studies to address questions of creative practice in rap music, specifically how the material of the rapping voice—what emcees, hip-hop heads, and scholars call “the flow”—relates to the material of the previously recorded instrumental tracks collectively known as the beat. -

The Evolution of Commercial Rap Music Maurice L
Florida State University Libraries Electronic Theses, Treatises and Dissertations The Graduate School 2011 A Historical Analysis: The Evolution of Commercial Rap Music Maurice L. Johnson II Follow this and additional works at the FSU Digital Library. For more information, please contact [email protected] THE FLORIDA STATE UNIVERSITY COLLEGE OF COMMUNICATION A HISTORICAL ANALYSIS: THE EVOLUTION OF COMMERCIAL RAP MUSIC By MAURICE L. JOHNSON II A Thesis submitted to the Department of Communication in partial fulfillment of the requirements for the degree of Master of Science Degree Awarded: Summer Semester 2011 The members of the committee approve the thesis of Maurice L. Johnson II, defended on April 7, 2011. _____________________________ Jonathan Adams Thesis Committee Chair _____________________________ Gary Heald Committee Member _____________________________ Stephen McDowell Committee Member The Graduate School has verified and approved the above-named committee members. ii I dedicated this to the collective loving memory of Marlena Curry-Gatewood, Dr. Milton Howard Johnson and Rashad Kendrick Williams. iii ACKNOWLEDGEMENTS I would like to express my sincere gratitude to the individuals, both in the physical and the spiritual realms, whom have assisted and encouraged me in the completion of my thesis. During the process, I faced numerous challenges from the narrowing of content and focus on the subject at hand, to seemingly unjust legal and administrative circumstances. Dr. Jonathan Adams, whose gracious support, interest, and tutelage, and knowledge in the fields of both music and communications studies, are greatly appreciated. Dr. Gary Heald encouraged me to complete my thesis as the foundation for future doctoral studies, and dissertation research. -

Global Connectivity and Multilinguals in the Twitter Network
Global Connectivity and Multilinguals in the Twitter Network Scott A. Hale Oxford Internet Institute, University of Oxford 1 St Giles, Oxford OX1 3JS, UK [email protected] ABSTRACT the Twitter mentions and retweet network to assess the extent This article analyzes the global connectivity of the Twitter to which language structures the network and asks whether retweet and mentions network and the role of multilingual multilingual users form cross-language bridges for informa- users engaging with content in multiple languages. The net- tion exchange that provide unique connections without which work is heavily structured by language with most mentions the network would break apart. The study finds language is a and retweets directed to users writing in the same language. key force structuring ties in the network, but that multilingual Users writing in multiple languages are more active, author- users are an important case to design for: over 10% of users ing more tweets than monolingual users. These multilingual engage with content in multiple languages and these users users play an important bridging role in the global connectiv- are more active than their monolingual counterparts. There ity of the network. The mean level of insularity from speak- is thus value in a single multilingual system, and language ers in each language does not correlate straightforwardly with should not be used as an absolute (i.e. only ever returning the size of the user base as predicted by previous research. Fi- search results or recommending friends in the main language nally, the English language does play more of a bridging role of the user). -

Rischar, Richard
A Vision of Love: An Etiquette of Vocal Ornamentation in African-American Popular Ballads of the Early 1990s Author(s): Richard Rischar Source: American Music, Vol. 22, No. 3 (Autumn, 2004), pp. 407-443 Published by: University of Illinois Press Stable URL: http://www.jstor.org/stable/3592985 Accessed: 01-01-2018 16:47 UTC REFERENCES Linked references are available on JSTOR for this article: http://www.jstor.org/stable/3592985?seq=1&cid=pdf-reference#references_tab_contents You may need to log in to JSTOR to access the linked references. JSTOR is a not-for-profit service that helps scholars, researchers, and students discover, use, and build upon a wide range of content in a trusted digital archive. We use information technology and tools to increase productivity and facilitate new forms of scholarship. For more information about JSTOR, please contact [email protected]. Your use of the JSTOR archive indicates your acceptance of the Terms & Conditions of Use, available at http://about.jstor.org/terms University of Illinois Press is collaborating with JSTOR to digitize, preserve and extend access to American Music This content downloaded from 199.79.170.81 on Mon, 01 Jan 2018 16:47:15 UTC All use subject to http://about.jstor.org/terms RICHARD RISCHAR A Vision of Love: An Etiquette of Vocal Ornamentation in African-American Popular Ballads of the Early 1990s Around 1990, buoyed by the success of Bill Cosby's situation come- dy and Oprah Winfrey's daytime talk show, there was a renewed vis- ibility of African-American pop culture in the mainstream. -

The Assassination of Dr. Martin Luther King Jr. and the Birth of Funk Culture
Loyola University Chicago Loyola eCommons Dissertations Theses and Dissertations 2013 Funk My Soul: The Assassination of Dr. Martin Luther King Jr. And the Birth of Funk Culture Domenico Rocco Ferri Loyola University Chicago Follow this and additional works at: https://ecommons.luc.edu/luc_diss Part of the United States History Commons Recommended Citation Ferri, Domenico Rocco, "Funk My Soul: The Assassination of Dr. Martin Luther King Jr. And the Birth of Funk Culture" (2013). Dissertations. 664. https://ecommons.luc.edu/luc_diss/664 This Dissertation is brought to you for free and open access by the Theses and Dissertations at Loyola eCommons. It has been accepted for inclusion in Dissertations by an authorized administrator of Loyola eCommons. For more information, please contact [email protected]. This work is licensed under a Creative Commons Attribution-Noncommercial-No Derivative Works 3.0 License. Copyright © 2013 Domenico Rocco Ferri LOYOLA UNIVERSITY CHICAGO FUNK MY SOUL: THE ASSASSINATION OF DR. MARTIN LUTHER KING JR. AND THE BIRTH OF FUNK CULTURE A DISSERTATION SUBMITTED TO THE FACULTY OF THE GRADUATE SCHOOL IN CANDIDACY FOR THE DEGREE OF DOCTOR OF PHILOSOPHY PROGRAM IN HISTORY BY DOMENICO R. FERRI CHICAGO, IL AUGUST 2013 Copyright by Domenico R. Ferri, 2013 All rights reserved. ACKNOWLEDGEMENTS Painstakingly created over the course of several difficult and extraordinarily hectic years, this dissertation is the result of a sustained commitment to better grasping the cultural impact of Dr. Martin Luther King Jr.’s life and death. That said, my ongoing appreciation for contemporary American music, film, and television served as an ideal starting point for evaluating Dr. -

Pdf, 312.59 KB
00:00:00 Music Transition “Crown Ones” off the album Stepfather by People Under The Stairs. 00:00:05 Oliver Wang Host Hello, I’m Oliver Wang. 00:00:07 Morgan Host And I’m Morgan Rhodes. You’re listening to Heat Rocks. Rhodes 00:00:09 Oliver Host Every episode we invite a guest to join us to talk about a heat rock, hot lava. And today we are going to be joining hands to take it back to 1994 and Two—or maybe it’s just II, I don’t know—the second album by the R&B mega smash group, Boyz II Men. 00:00:30 Music Music “Thank You” off the album II by Boyz II Men. Smooth, funky R&B. (I like this, I like this, I like...) I was young And didn't have nowhere to run I needed to wake up and see (and see) What's in front of me (na-na-na) There has to be a better way Sing it again a better way To show... 00:00:50 Morgan Host Boyz II Men going off, not too hard, not too soft— [Oliver says “ooo” appreciatively.] —could easily be considered a bit of a mantra for Shawn, Wanya, Nathan, and Michael, two tenors, a baritone, and a bass singer from Philly, after their debut album. The one that introduced us to their steez, and their melodies. This one went hella platinum. The follow-up, II. This album had hits that can be divided into three sections. Section one, couple’s therapy. -

The Connectivity Doctrine: a Critique of Techo-Utopian Discourse, Liberal Governmentality, and the Colonization of Cyberspace
DePaul University Via Sapientiae College of Liberal Arts & Social Sciences Theses and Dissertations College of Liberal Arts and Social Sciences 8-2012 The connectivity doctrine: A critique of techo-utopian discourse, liberal governmentality, and the colonization of cyberspace Geoffrey S. Pettys DePaul University, [email protected] Follow this and additional works at: https://via.library.depaul.edu/etd Recommended Citation Pettys, Geoffrey S., "The connectivity doctrine: A critique of techo-utopian discourse, liberal governmentality, and the colonization of cyberspace" (2012). College of Liberal Arts & Social Sciences Theses and Dissertations. 131. https://via.library.depaul.edu/etd/131 This Thesis is brought to you for free and open access by the College of Liberal Arts and Social Sciences at Via Sapientiae. It has been accepted for inclusion in College of Liberal Arts & Social Sciences Theses and Dissertations by an authorized administrator of Via Sapientiae. For more information, please contact [email protected]. The Connectivity Doctrine: A Critique of Techno-Utopian Discourse, Liberal-Governmentality, and the Colonization of Cyberspace A Thesis Presented in Partial Fulfillment of the Requirements for the Degree of Master of Arts August 2012 By Geoffrey S. Pettys Department of International Studies College of Liberal Arts and Sciences DePaul University Chicago, Illinois Table of Contents Acknowledgements 3 Introduction 4 Chapter Overview 6 Chapter I: The Connectivity Doctrine 9 1.1: The Connectivity Doctrine as Articulated -

An Examination of Essential Popular Music Compact Disc Holdings at the Cleveland Public Library
DOCUMENT RESUME ED 435 403 IR 057 553 AUTHOR Halliday, Blane TITLE An Examination of Essential Popular Music Compact Disc Holdings at the Cleveland Public Library. PUB DATE 1999-05-00 NOTE 94p.; Master's Research Paper, Kent State University. Information Science. Appendices may not reproduce adequately. PUB TYPE Dissertations/Theses (040) EDRS PRICE MF01/PC04 Plus Postage. DESCRIPTORS *Audiodisks; Discographies; *Library Collection Development; *Library Collections; *Optical Disks; *Popular Music; *Public Libraries; Research Libraries; Tables (Data) IDENTIFIERS *Cleveland Public Library OH ABSTRACT In the 1970s and early 1980s, a few library researchers and scholars made a case for the importance of public libraries' acquisition of popular music, particularly rock music sound recordings. Their arguments were based on the anticipated historical and cultural importance of obtaining and maintaining a collection of these materials. Little new research in this direction has been performed since then. The question arose as to what, if anything, has changed since this time. This question was answered by examining the compact disc holdings of the Cleveland Public Library, a major research-oriented facility. This examination was accomplished using three discographies of essential rock music titles, as well as recent "Billboard" Top 200 Album charts. The results indicated a strong orientation toward the acquisition of recent releases, with the "Billboard" charts showing the largest percentages of holdings for the system. Meanwhile, the holdings vis-a-vis the essential discographies ran directly opposite the "Billboard" holdings. This implies a program of short-term patron satisfaction by providing current "hits," while disregarding the long-term benefits of a collection based on demonstrated artistic relevance. -

Various Soul Food Soundtrack Mp3, Flac, Wma
Various Soul Food Soundtrack mp3, flac, wma DOWNLOAD LINKS (Clickable) Genre: Hip hop / Funk / Soul / Pop / Stage & Screen Album: Soul Food Soundtrack Country: Europe Released: 1997 Style: RnB/Swing, Soundtrack, Pop Rap, Soul MP3 version RAR size: 1847 mb FLAC version RAR size: 1764 mb WMA version RAR size: 1165 mb Rating: 4.9 Votes: 650 Other Formats: AA MP4 AU DMF AIFF ASF MPC Tracklist Hide Credits 1 –Boyz II Men A Song For Mama 5:01 Call Me (Hip Hop Mix) 2 –Blackstreet Co-producer – Chauncey HannibalFeaturing – Jay-ZProducer – 4:28 Teddy Riley 3 –Milestone I Care 'Bout You 4:35 What About Us 4 –Total 4:22 Producer – Timbaland Don't Stop What You're Doing 5 –Puff Daddy & The Family Featuring – Lil' KimProducer – Ron "Amen-Ra" Lawrence, Sean 5:11 "Puffy" Combs* We're Not Making Love No More 6 –Dru Hill 4:50 Producer – Daryl Simmons 7 –Tenderoni Baby I 4:12 Let's Do It Again 8 –Xscape 3:15 Co-producer – Manuel SealProducer – Jermaine Dupri In Due Time 9 –OutKast 3:53 Featuring – Cee-LoProducer – OutKast Slow Jam 10 –Usher 4:43 Featuring – Monica Boys And Girls 11 –Tony! Toni! Toné! 4:16 Co-producer – Raphael Saadiq 12 –En Vogue You Are The Man 4:13 13 –Earth, Wind & Fire September 3:36 Credits Producer – Babyface (tracks: 1, 3, 6, 7, 10 to 12) Notes BIEM/GEMA Barcode and Other Identifiers Barcode: 743215230724 Other versions Category Artist Title (Format) Label Category Country Year Soul Food Soundtrack (CD, 73008-26041-2 Various LaFace Records 73008-26041-2 US 1997 Comp) BVCA-734 Various Soul Food Soundtrack (CD) LaFace Records BVCA-734 Japan 1997 Soul Food Soundtrack 73008-26041-4 Various LaFace Records 73008-26041-4 US 1997 (Cass, Album) Soul Food Soundtrack LFL-6041-1 Various LaFace Records LFL-6041-1 US 1997 (2xLP, Comp, Promo) ARCD-6041 Various Soul Food Soundtrack (CD) LaFace Records ARCD-6041 US 1997 Related Music albums to Soul Food Soundtrack by Various Puff Daddy & Faith Evans Feat. -
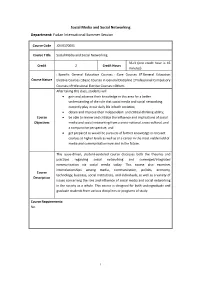
Social Media and Social Networking Department: Fudan International Summer Session
Social Media and Social Networking Department: Fudan International Summer Session Course Code JOUR170005 Course Title Social Media and Social Networking 36+3 (one credit hour is 45 Credit 2 Credit Hours minutes) □Specific General Education Courses □Core Courses ☑General Education Course Nature Elective Courses □Basic Courses in General Discipline □Professional Compulsory Courses □Professional Elective Courses □Others After taking this class, students will gain and advance their knowledge in this area for a better understanding of the role that social media and social networking currently play in our daily life in both societies; obtain and improve their independent- and critical-thinking ability; Course be able to review and criticize the influence and implications of social Objectives media and social networking from a cross-national, cross-cultural, and a comparative perspective; and get prepared as would-be pursuers of further knowledge in relevant courses at higher levels as well as of a career in the most viable field of media and communication now and in the future. This issue-driven, student-centered course discusses both the theories and practices regarding social networking and converged/integrated communication via social media today. This course also examines interrelationships among media, communication, politics, economy, Course technology, business, social institutions, and individuals, as well as a variety of Description issues concerning the role and influence of social media and social networking in the society as a whole. This course is designed for both undergraduate and graduate students from various disciplines or programs of study. Course Requirements: No. 1 Teaching Methods: This course is devoted to creating a student-centered learning environment, by adopting a balanced approach to covering both the breadth and depth of the subjects.