An Introduction to the X Window System
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Part II, Window Managers and Desktop Environments
Part II Window Managers and Desktop Environments The window manager is responsible for managing application windows and application- independent behavior, such as pop-up menus appearing in the background. The window manager manages the placement, borders, and decorations of all windows, and is responsible for the look and feel of your particular X session. Desktop environments typically include an integrated window manager, some sort of control panel, applications, and a consistent look and feel across applications. The chapters in Part II, Window Managers and Desktop Environments, are: Overview This chapter provides a conceptual introduction to window managers and desktop environments and briefly surveys some of the many window managers and desktop environments available for Linux. FVWM FVWM is a traditional window manager for Linux systems. It is now into its second major version, FVWM2. Window Maker Window Maker is an elegant X11 window manager designed to give integration support to GNUstep-based applications. It emulates the look and feel of OpenStep, the NeXTSTEP GUI. Enlightenment Enlightenment, often shortened to just E, may be the most elaborate and bizarre window manager available. Enlightenment’s motto, “time to rethink everything,” provides a good indication of the uniqueness and flashiness behind Enlightenment. Using GNOME GNOME, which stands for GNU Network Object Model Environment, is a freely available desktop environment that can be used with any of several window managers, including Enlightenment and Sawfish. Using KDE KDE, the K Desktop Environment, is another freely available desktop environment. KDE includes an assortment of games and utilities, as well as an integrated suite of office productivity applications.. -

Easy Slackware
1 Создание легкой системы на базе Slackware I - Введение Slackware пользуется заслуженной популярностью как классический linux дистрибутив, и поговорка "кто знает Red Hat тот знает только Red Hat, кто знает Slackware тот знает linux" несмотря на явный снобизм поклонников "бога Патре га" все же имеет под собой основания. Одним из преимуществ Slackware является возможность простого создания на ее основе практически любой системы, в том числе быстрой и легкой десктопной, о чем далее и пойдет речь. Есть дис трибутивы, клоны Slackware, созданные именно с этой целью, типа Аbsolute, но все же лучше создавать систему под себя, с максимальным учетом именно своих потребностей, и Slackware пожалуй как никакой другой дистрибутив подходит именно для этой цели. Легкость и быстрота системы определяется выбором WM (DM) , набором программ и оптимизацией программ и системы в целом. Первое исключает KDE, Gnome, даже новые версии XFCЕ, остается разве что LXDE, но набор программ в нем совершенно не устраивает. Оптимизация наиболее часто используемых про грамм и нескольких базовых системных пакетов осуществляется их сборкой из сорцов компилятором, оптимизированным именно под Ваш комп, причем каж дая программа конфигурируется исходя из Ваших потребностей к ее возможно стям. Оптимизация системы в целом осуществляется ее настройкой согласно спе цифическим требованиям к десктопу. Такой подход был выбран по банальной причине, возиться с gentoo нет ни какого желания, комп все таки создан для того чтобы им пользоваться, а не для компиляции программ, в тоже время у каждого есть минимальный набор из не большого количества наиболее часто используемых программ, на которые стоит потратить некоторое, не такое уж большое, время, чтобы довести их до ума. Кро ме того, такой подход позволяет иметь самые свежие версии наиболее часто ис пользуемых программ. -

Introduction to the Enlightenment Foundation Libraries
Introduction to the Enlightenment foundation libraries. An overview of EFL Kostis Kapelonis Introduction to the Enlightenment foundation libraries.: An overview of EFL Kostis Kapelonis Abstract The target audience of this document are UNIX programmers who are interested in the Enlightenment Foundation Libraries (EFL). You must already know C programming. You will not however learn how to program using the EFL. Instead, you will learn why you should program with the EFL. If you ever wanted to evaluate the EFL but did not see any advantages over previous graphic libraries then this document is for you! Table of Contents 1. Introduction ............................................................................................................................1 A little History ...................................................................................................................1 Related documentation ......................................................................................................... 2 Obtaining the EFL libraries ................................................................................................... 2 2. The EFL structure .................................................................................................................... 4 Organization of the Libraries ................................................................................................. 4 Brief description of each EFL library ...................................................................................... 5 3. -
Towards a New Enlightenment? a Transcendent Decade
Towards a New Enlightenment? A Transcendent Decade Preface This book, Towards a New Enlightenment? A Transcendent Decade, is the eleventh in an annual series that BBVA’s OpenMind project dedicates to disseminating greater knowledge on the key questions of our time. We began this series in 2008, with the first book, Frontiers of Knowledge, that celebrated the launching of the prizes of the same name awarded annually by the BBVA Foundation. Since then, these awards have achieved worldwide renown. In that first book, over twenty major scientists and experts used language accessible to the general public to rigorously review the most relevant recent advances and perspectives in the different scientific and artistic fields recognized by those prizes. Since then, we have published a new book each year, always following the same model: collections of articles by key figures in their respective fields that address different aspects or perspectives on the fundamental questions that affect our lives and determine our futu- re: from globalization to the impact of exponential technologies, and on to include today’s major ethical problems, the evolution of business in the digital era, and the future of Europe. The excellent reaction to the first books in this series led us, in 2011, to create OpenMind (www.bbvaopenmind.com), an online community for debate and the dissemination of knowle- dge. Since then, OpenMind has thrived, and today it addresses a broad spectrum of scientific, technological, social, and humanistic subjects in different formats, including our books, as well as articles, posts, reportage, infographics, videos, and podcasts, with a growing focus on audiovisual materials. -

1.1 X Client/Server
เดสกทอปลินุกซ เทพพิทักษ การุญบุญญานันท 2 สารบัญ 1 ระบบ X Window 5 1.1 ระบบ X Client/Server . 5 1.2 Window Manager . 6 1.3 Desktop Environment . 7 2 การปรับแตง GNOME 11 2.1 การติดตั้งฟอนต . 11 2.2 GConf . 12 2.3 การแสดงตัวอักษร . 13 2.4 พื้นหลัง . 15 2.5 Theme . 16 2.6 เมนู/ทูลบาร . 17 2.7 แปนพิมพ . 18 2.8 เมาส . 20 3 4 บทที่ 1 ระบบ X Window ระบบ GUI ที่อยูคูกับยูนิกซมมานานคือระบบ X Window ซึ่งพัฒนาโดยโครงการ Athena ที่ MIT รวมกับบริษัท Digital Equipment Corporation และบริษัทเอกชนจำนวนหนึ่ง ปจจุบัน X Window ดูแลโดย Open Group เปนระบบที่เปดทั้งในเรื่องโปรโตคอลและซอรสโคด ขณะที่เขียนเอกสารฉบับนี้ เวอรชันลาสุดของ X Window คือ เวอรชัน 11 รีลีส 6.6 (เรียกสั้นๆ วา X11R6.6) สำหรับลินุกซและระบบปฏิบัติการในตระกูลยูนิกซที่ทำงานบน PC ระบบ X Window ที่ใชจะมาจาก โครงการ XFree86 ซึ่งพัฒนาไดรเวอรสำหรับอุปกรณกราฟกตางๆ ที่ใชกับเครื่อง PC รุนลาสุดขณะที่ เขียนเอกสารนี้คือ 4.3.0 1.1 ระบบ X Client/Server X Window เปนระบบที่ทำงานผานระบบเครือขาย โดยแยกเปนสวน X client และ X server สื่อสาร กันผาน X protocol ดังนั้น โปรแกรมที่ทำงานบน X Window จะสามารถแสดงผลบนระบบปฏิบัติการ ที่ตางชนิดกันก็ได ตราบใดที่ระบบนั้นสามารถใหบริการผาน X protocol ได X client ไดแกโปรแกรมประยุกตตางๆ ที่จะขอใชบริการจาก X server ในการติดตอกับฮารดแวร เชน จอภาพ แปนพิมพ เมาส ฯลฯ ดังนั้น X server จึงทำงานอยูบนเครื่องที่อยูใกลผูใชเสมอ ในขณะที่ X client อาจอยูในเครื่องเดียวกันหรืออยูในเครื่องใดเครื่องหนึ่งในระบบเครือขายก็ได X client จะติดตอกับ X server ดวยการเรียก X library (เรียกสั้นๆ วา Xlib) API ตางๆ ใน Xlib มีหนาที่แปลงการเรียกฟงกชันแตละครั้งใหเปน request ในรูปของ X protocol เพื่อสงไปยัง X server -

Enlightement DR17 Enlightement DR17
2021/09/25 13:56 (UTC) 1/5 Enlightement DR17 Enlightement DR17 What is E17? Enlightenment DR17 (E17) is the long awaited successor of E16, a window manager which was distributed in Slackware 10 years ago. It is classed as a “desktop shell”, providing the things you need to operate your desktop (or laptop), but not a whole suite of applications. This includes launching applications, managing their windows, and doing other system tasks like suspending, rebooting, managing files, etc. E17 doesn't come alone. Actually, it uses the Enlightenment Foundation Libraries (EFL) which can be used to develop other applications like in the Qt/KDE world for instance. There are, as in February 2013, 15 libraries in EFL and a lot of external modules or applications that can be used with E17. Installing E17 Pre-built packages SlackE17 The easiest and fastest way to get E17 running on Slackware is to install the E17 packages from the SlackE17 project. You just need to have the latest release of Slackware, Slackware64 or ArmedSlack. Just download the tarball corresponding to your architecture (i486, x86_64 or ARM), unpack it and read the doc. To install the packages, you have several options: Install everything using: # upgradepkg --install-new e17/*.txz Use the supplied script to install only E17 and its dependencies using: # ./slacke17-install.sh std Use the supplied script to install everything using: # ./slacke17-install.sh max Or you can just: # cd e17 && pkgtool Compilation First you need to install the dependencies needed to compile Enlightenment. -

EFL a UI Toolkit Designed for the Embedded World
EFL A UI Toolkit Designed for the Embedded World stosb.com/talks Tom Hacohen [email protected] Samsung Open Source Group @TomHacohen Where We Come From The Enlightenment project is old (1996) - predating GNOME, KDE, etc. Initially a window manager - split to a set of libraries EFL as we know it dates back to at least 2000 Targeted the embedded world since the beginning Where We Come From (image circa 2001) General Information Used in many places, and supported by big industry players Focus on embedded devices A mix of LGPL 2.1 and BSD Three months release cycle Ever improving CI and static analysis (coverity) API/ABI checks before every release Zero compiler warnings with -Wall -Wextra Development Statistics Latest version (1.18.0): 105 unique contributors 3,364 commits Overall: 587 unique contributors 50,000 commits What Does the EFL Provide? What Does the EFL Provide? General Purpose Library Stringshares for reducing memory footprint In-line lists/arrays for reducing memory usage and fragmentation Copy-on-write support for C structures and unions Magic checks for structures Many others - list, hash, rb-tree and more What Does the EFL Provide? Binary Serialization Library Serialize, de-serialize C structures and unions Decompile to text, and re-compile from text Reduces memory usage (mmap) Faster to load Supports compression and signing What Does the EFL Provide? Mainloop and General-Glue Library Animators - Timers that tick at most on every frame Easy support for thread-workers Execute, monitor and pipe input/output of executables Integrates with other main loop implementations Networking, IPC, HTTP and etc. -

An Extensible Constraint-Enabled Window Manager
Scwm: An Extensible Constraint-Enabled Window Manager Greg J. Badros Jeffrey Nichols Alan Borning gjb,jwnichls,borning @cs.washington.edu f Dept. of Computer Scienceg and Engineering University of Washington, Box 352350 Seattle, WA 98195-2350, USA Abstract powerful, and satisfying. We desired a platform for researching advanced Using C to implement a highly-interactive applica- window layout paradigms including the use of con- tion also complicates extensibility and customiz- straints. Typical window management systems ability. To add a new feature, the user likely must are written entirely in C or C++, complicating write C code, recompile, relink, and restart the extensibility and programmability. Because no ex- application before changes are finally available for isting window manager was well-suited to our goal, testing and use. This development cycle is es- we developed the Scwm window manager. In pecially problematic for software such as a win- Scwm, only the core window-management primi- dow manager that generally is expected to run for tives are written in C while the rest of the pack- weeks at a time. Additionally, maintaining all the age is implemented in its Guile/Scheme exten- features that any user desires would result in ter- sion language. This architecture, first seen in rible code bloat. Emacs, enables programming substantial new fea- tures in Scheme and provides a solid infrastructure An increasingly popular solution to these prob- for constraint-based window layout research and lems is the use of a scripting language on top of other advanced capabilities such as voice recogni- a core system that defines new domain-specific tion. -

Getting Started with Ubuntu and Kubuntu
Getting Started With Ubuntu and Kubuntu IN THIS PART Chapter 1 The Ubuntu Linux Project Chapter 2 Installing Ubuntu and Kubuntu Chapter 3 Installing Ubuntu and Kubuntu on Special-Purpose Systems COPYRIGHTED MATERIAL 94208c01.indd 1 3/16/09 11:43:23 PM 94208c01.indd 2 3/16/09 11:43:24 PM The Ubuntu Linux Project ersonal computers and their operating systems have come a long way since the late 1970s, when the first home computer hit the market. At IN THIS cHAPTER that time, you could only toggle in a program by flipping switches on the P Introducing Ubuntu Linux front of the machine, and the machine could then run that program and only that program until you manually loaded another, at which time the first program Choosing Ubuntu was kicked off the system. Today’s personal computers provide powerful graph- ics and a rich user interface that make it easy to select and run a wide variety of Reviewing hardware and software concurrently. software requirements The first home computer users were a community of interested people who just Using Ubuntu CDs wanted to do something with these early machines. They formed computer clubs and published newsletters to share their interests and knowledge — and often the Getting help with Ubuntu Linux software that they wrote for and used on their machines. Sensing opportunities and a growing market, thousands of computer companies sprang up to write and Getting more information sell specific applications for the computer systems of the day. This software ranged about Ubuntu from applications such as word processors, spreadsheets, and games to operating systems that made it easier to manage, load, and execute different programs. -

X Window System Architecture Overview HOWTO
X Window System Architecture Overview HOWTO Daniel Manrique [email protected] Revision History Revision 1.0.1 2001−05−22 Revised by: dm Some grammatical corrections, pointed out by Bill Staehle Revision 1.0 2001−05−20 Revised by: dm Initial LDP release. This document provides an overview of the X Window System's architecture, give a better understanding of its design, which components integrate with X and fit together to provide a working graphical environment and what choices are there regarding such components as window managers, toolkits and widget libraries, and desktop environments. X Window System Architecture Overview HOWTO Table of Contents 1. Preface..............................................................................................................................................................1 2. Introduction.....................................................................................................................................................2 3. The X Window System Architecture: overview...........................................................................................3 4. Window Managers..........................................................................................................................................4 5. Client Applications..........................................................................................................................................5 6. Widget Libraries or toolkits...........................................................................................................................6 -
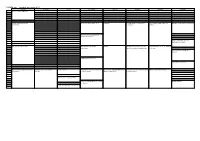
FOSDEM 2013 Schedule
FOSDEM 2013 - Saturday 2013-02-02 (1/9) Janson K.1.105 Ferrer Chavanne Lameere H.1301 H.1302 H.1308 10:30 Welcome to FOSDEM 2013 10:45 11:00 How we made the Jenkins QEMU USB status report 2012 Rockbuild The neat guide to Fedora RPM LinuxonAndroid and SlapOS on Wayland for Application Developers community Packaging Android 11:15 11:30 CRIU: Checkpoint and Restore (mostly) In Userspace 11:45 Ubuntu Online Accounts for application developers 12:00 The Devil is in the Details Vtrill: Rbridges for Virtual PTXdist Building RPM packages from Git Emdedded distro shootout: buildroot Networking repositories with git-buildpackage vs. Debian Better software through user 12:15 research 12:30 Bringing Xen to CentOS-6 Sketching interactions 12:45 13:00 The Open Observatory of Network Porting Fedora to 64-bit ARM Coding Goûter A brief tutorial on Xen's advanced Guacamayo -- Building Multimedia Package management and creation ARM v7 State of the Body ↴ Interference systems security features Appliance with Yocto ↴ in Gentoo Linux ↴ 13:15 Spoiling and Counter-spoiling 13:30 oVirt Live Storage Migration - Under Modern CMake ↴ the Hood ↴ ZONE: towards a better news feed ↴ 13:45 FOSDEM 2013 - Saturday 2013-02-02 (2/9) H.1309 H.2213 H.2214 AW1.120 AW1.121 AW1.125 AW1.126 Guillissen 10:30 10:45 11:00 Metaphor and BDD XMPP 101 Storytelling FLOSS Welcome and Introduction The room open() process Scripting Apache OpenOffice: Welcome to the Perl d… Introductory Nutshell Programs Inheritance versus Roles (Writer, Calc, Impress) 11:15 Signal/Collect: Processing Large -

Turbo-Charge Your Desktop
Turbo-charge your desktop Turbo-charge your desktop rge ha -c p o to rb sk Enlightenment 0.16.8.14 u e Fluxbox 1.0.0 T d Ratpoison 1.4.3 r Mike Saunders explores the slick u Enlightenment, speedy Fluxbox o and keyboard-tastic Ratpoison y window managers. Aye caramba! anufacturers and PC vendors would have the internet. Click Applications > Accessories > Terminal (in you believe that there’s only one way to Gnome) to enter the commands. Then, after installing, log out speed up your machine: buy new kit! And and click Options > Select Session to choose the WM that M then, in 18 months, buy new kit again. runs when you log in. Let’s go! However, it’s usually our software that’s the real bottleneck. If you’ve been using Linux for a while, you’ll already have discovered lighter alternatives to some of DESKTOP ENVIRONMENT Builds upon the window manager, the platform’s bloatfests – for example, using AbiWord adding panels, system trays, and Gnumeric in the place of OpenOffice.org. a file manager and so on. But what about the desktop itself? To start with, let’s look at how the layers of the Linux GUI fit together, right. WINDOW MANAGER (AKA WM) Uses the widget tookit to produce title That’s the setup when you’re running one of the big three bars, resize handles and menus. desktops (Gnome, KDE, Xfce). However, if you choose a standalone window manager (WM), you can cut out the first WIDGET TOOLKIT and third layers in this stack.