Understanding the Security of ARM Debugging Features
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

7.5W Fast-Charging Mode and 5W Standard Mode
Before you start: For Anker 7.5W Wireless Chargers This document will help you identify problems and get the most out of your experience with our wireless chargers. It is important to note that although wireless chargers are a transformatively convenient way to charge, they are not yet capable of the charging speeds provided by traditional wired chargers. Attachments (Must-Read!) If you're experiencing interrupted or slow charging, check the following: The back of your phone should not have any metal, pop sockets, or credit cards. Put the phone in the center of the charging surface (this lets the charging coil in your phone line up with the one inside the wireless charger). The wireless charging coil on Sony phones is located slightly below center. Phone cases should be no thicker than 5 mm for effective charging. Choose the correct adapter for your wireless charger: Quick Charge or Power Delivery adapter for Fast Charge Modes. 5V/2A adapter for Standard Charge Mode. Not compatible with 5V/1A adapters. Phone Brands & Power Input For Anker 7.5W Wireless Chargers Apple iPhone X iPhone XS iPhone XS Max iPhone 8 / 8 Plus iPhone XR Two charging modes: 7.5W fast-charging mode and 5W standard mode. For the best results, use a Quick Charge wall charger, desktop charger, car charger, power strip (output power of 9V/2A or 12V/1.5A). For standard 5W charging mode, use with wall chargers, desktop chargers, car chargers, and power strips with an output of 5V/2A or above.Not compatible with the iPhone stock charger (5V/1A). -

Mobiliųjų Telefonų Modeliai, Kuriems Tinka Ši Programinė Įranga
Mobiliųjų telefonų modeliai, kuriems tinka ši programinė įranga Telefonai su BlackBerry operacinė sistema 1. Alltel BlackBerry 7250 2. Alltel BlackBerry 8703e 3. Sprint BlackBerry Curve 8530 4. Sprint BlackBerry Pearl 8130 5. Alltel BlackBerry 7130 6. Alltel BlackBerry 8703e 7. Alltel BlackBerry 8830 8. Alltel BlackBerry Curve 8330 9. Alltel BlackBerry Curve 8530 10. Alltel BlackBerry Pearl 8130 11. Alltel BlackBerry Tour 9630 12. Alltel Pearl Flip 8230 13. AT&T BlackBerry 7130c 14. AT&T BlackBerry 7290 15. AT&T BlackBerry 8520 16. AT&T BlackBerry 8700c 17. AT&T BlackBerry 8800 18. AT&T BlackBerry 8820 19. AT&T BlackBerry Bold 9000 20. AT&T BlackBerry Bold 9700 21. AT&T BlackBerry Curve 22. AT&T BlackBerry Curve 8310 23. AT&T BlackBerry Curve 8320 24. AT&T BlackBerry Curve 8900 25. AT&T BlackBerry Pearl 26. AT&T BlackBerry Pearl 8110 27. AT&T BlackBerry Pearl 8120 28. BlackBerry 5810 29. BlackBerry 5820 30. BlackBerry 6210 31. BlackBerry 6220 32. BlackBerry 6230 33. BlackBerry 6280 34. BlackBerry 6510 35. BlackBerry 6710 36. BlackBerry 6720 37. BlackBerry 6750 38. BlackBerry 7100g 39. BlackBerry 7100i 40. BlackBerry 7100r 41. BlackBerry 7100t 42. BlackBerry 7100v 43. BlackBerry 7100x 1 44. BlackBerry 7105t 45. BlackBerry 7130c 46. BlackBerry 7130e 47. BlackBerry 7130g 48. BlackBerry 7130v 49. BlackBerry 7210 50. BlackBerry 7230 51. BlackBerry 7250 52. BlackBerry 7270 53. BlackBerry 7280 54. BlackBerry 7290 55. BlackBerry 7510 56. BlackBerry 7520 57. BlackBerry 7730 58. BlackBerry 7750 59. BlackBerry 7780 60. BlackBerry 8700c 61. BlackBerry 8700f 62. BlackBerry 8700g 63. BlackBerry 8700r 64. -

Electronic 3D Models Catalogue (On July 26, 2019)
Electronic 3D models Catalogue (on July 26, 2019) Acer 001 Acer Iconia Tab A510 002 Acer Liquid Z5 003 Acer Liquid S2 Red 004 Acer Liquid S2 Black 005 Acer Iconia Tab A3 White 006 Acer Iconia Tab A1-810 White 007 Acer Iconia W4 008 Acer Liquid E3 Black 009 Acer Liquid E3 Silver 010 Acer Iconia B1-720 Iron Gray 011 Acer Iconia B1-720 Red 012 Acer Iconia B1-720 White 013 Acer Liquid Z3 Rock Black 014 Acer Liquid Z3 Classic White 015 Acer Iconia One 7 B1-730 Black 016 Acer Iconia One 7 B1-730 Red 017 Acer Iconia One 7 B1-730 Yellow 018 Acer Iconia One 7 B1-730 Green 019 Acer Iconia One 7 B1-730 Pink 020 Acer Iconia One 7 B1-730 Orange 021 Acer Iconia One 7 B1-730 Purple 022 Acer Iconia One 7 B1-730 White 023 Acer Iconia One 7 B1-730 Blue 024 Acer Iconia One 7 B1-730 Cyan 025 Acer Aspire Switch 10 026 Acer Iconia Tab A1-810 Red 027 Acer Iconia Tab A1-810 Black 028 Acer Iconia A1-830 White 029 Acer Liquid Z4 White 030 Acer Liquid Z4 Black 031 Acer Liquid Z200 Essential White 032 Acer Liquid Z200 Titanium Black 033 Acer Liquid Z200 Fragrant Pink 034 Acer Liquid Z200 Sky Blue 035 Acer Liquid Z200 Sunshine Yellow 036 Acer Liquid Jade Black 037 Acer Liquid Jade Green 038 Acer Liquid Jade White 039 Acer Liquid Z500 Sandy Silver 040 Acer Liquid Z500 Aquamarine Green 041 Acer Liquid Z500 Titanium Black 042 Acer Iconia Tab 7 (A1-713) 043 Acer Iconia Tab 7 (A1-713HD) 044 Acer Liquid E700 Burgundy Red 045 Acer Liquid E700 Titan Black 046 Acer Iconia Tab 8 047 Acer Liquid X1 Graphite Black 048 Acer Liquid X1 Wine Red 049 Acer Iconia Tab 8 W 050 Acer -

RELEASE NOTES UFED PHYSICAL ANALYZER, Version 5.0 | March 2016 UFED LOGICAL ANALYZER
NOW SUPPORTING 19,203 DEVICE PROFILES +1,528 APP VERSIONS UFED TOUCH, UFED 4PC, RELEASE NOTES UFED PHYSICAL ANALYZER, Version 5.0 | March 2016 UFED LOGICAL ANALYZER COMMON/KNOWN HIGHLIGHTS System Images IMAGE FILTER ◼ Temporary root (ADB) solution for selected Android Focus on the relevant media files and devices running OS 4.3-5.1.1 – this capability enables file get to the evidence you need fast system and physical extraction methods and decoding from devices running OS 4.3-5.1.1 32-bit with ADB enabled. In addition, this capability enables extraction of apps data for logical extraction. This version EXTRACT DATA FROM BLOCKED APPS adds this capability for 110 devices and many more will First in the Industry – Access blocked application data with file be added in coming releases. system extraction ◼ Enhanced physical extraction while bypassing lock of 27 Samsung Android devices with APQ8084 chipset (Snapdragon 805), including Samsung Galaxy Note 4, Note Edge, and Note 4 Duos. This chipset was previously supported with UFED, but due to operating system EXCLUSIVE: UNIFY MULTIPLE EXTRACTIONS changes, this capability was temporarily unavailable. In the world of devices, operating system changes Merge multiple extractions in single unified report for more frequently, and thus, influence our support abilities. efficient investigations As our ongoing effort to continue to provide our customers with technological breakthroughs, Cellebrite Logical 10K items developed a new method to overcome this barrier. Physical 20K items 22K items ◼ File system and logical extraction and decoding support for iPhone SE Samsung Galaxy S7 and LG G5 devices. File System 15K items ◼ Physical extraction and decoding support for a new family of TomTom devices (including Go 1000 Point Trading, 4CQ01 Go 2505 Mm, 4CT50, 4CR52 Go Live 1015 and 4CS03 Go 2405). -

Zain Kuwait Partners with Cisco Meraki to Deliver Cloud-Based Solutions to Enterprises in Kuwait the Solutions Offer Competitive Advantage to Enterprises in Kuwait
15 Technology Sunday, October 21, 2018 Zain Kuwait partners with Cisco Meraki to deliver cloud-based solutions to enterprises in Kuwait The solutions offer competitive advantage to enterprises in Kuwait DUBAI/KUWAIT: Zain Kuwait, the leading digital serv- meet our enterprise customers’ aspirations, and deliver ice provider in the country, announced a strategic part- on our promise of unlocking opportunities and offering nership with Cisco to deliver secure, cloud-based, man- unrivalled services and latest technologies.” aged network solutions to enterprises of all sizes in Stephen Koza, Head of Service Provider Worldwide Kuwait. This partnership aims at empowering a more effi- Sales, Cisco stated: “Cisco Meraki is proud to partner cient enterprise sector in Kuwait in alignment with the with Zain Kuwait on their mission to be a leader on the country’s National Development Plan (New Kuwait 2035). path to digital transformation in Kuwait. With Meraki’s The announcement was made during Zain’s participation innovative network infrastructure, built around simplicity at the fifth day of the 38th edition of The Gulf Information and managed through Meraki’s web-based dashboard, Technology Exhibition (GITEX Technology Week 2018). we know this partnership will allow Zain to deliver their The international event, hosted in the United Arab customers a secure and high-performing network experi- Emirates, is organized by the Dubai World Trade Center, ence. We are excited to help deliver a solution that will and features the biggest global companies, organizations, allow Zain’s customers to scale and accelerate their and entities from the Telecom and IT industry. growth in Kuwait and beyond. -

T Sleep' Concert Jlo Wants to Be Director 13 SHOW
TWITTER CELEBS @newsofbahrain NEWS OF BAHRAIN 4 Banah to headline ‘Manama Doesn’t Sleep’ concert INSTAGRAM Actress Sondra /nobmedia 15 Locke dead at 74 LINKEDIN SATURDAY newsofbahrain DECEMBER 2018 Oscar-nominated actress Sondra Locke has died WHATSAPP 200 FILS 38444680 ISSUE NO. 7961 of cancer at the age of 74, US news outlets reported FACEBOOK /nobmedia Thursday night. Locke died November 3 in California, MAIL [email protected] the reports said, quoting a celebrity news website, WEBSITE newsofbahrain.com Radar Online. P13 JLo wants to be director 13 SHOW WORLD 7 Kushner possible next chief of staff Royal pardon for 89 inmates Manama Patriotism fills the air is Majesty King Ham- Had bin Isa Al Khalifa yesterday issued a royal de- The Kingdom all set to celebrate its 47th National Day cree pardoning 89 inmates, sentenced in different cases, ment Minister Jameel Humaidan. after serving part of their Special arrangements done The celebration featured recreational verdicts. • activities for the ministry’s staff, flag-rais- The royal pardon marks by the traffic directorate to ing, national songs, folklore songs, com- the occasion of the King- ease the flow of traffic during petitions and prize-distribution. dom’s celebration of its Na- the National Day celebrations. Education Minister Dr Majid Al Nu- tional Days on December aimi attended a ceremony organised by 16 and 17. Streets across the Kingdom the ministry marking the National Day. It reflects HM the King’s • Addressing the ceremony which was keenness on the pardoned have been decorated with held at the ministry’s headquarters in Isa inmate’s reintegration in the Bahrain flags and lighting. -

Phone's Model, the Type of Wall Charger
Before you start: For Anker 5W Wireless Chargers This document will help you identify problems and get the most out of your experience with our wireless chargers. It is important to note that although wireless chargers are a transformatively convenient way to charge, they are not yet capable of the charging speeds provided by traditional wired chargers. Attachments (Must-Read!) If you're experiencing interrupted or slow charging, check the following: The back of your phone should not have any metal, pop sockets, or credit cards. Put the phone in the center of the charging surface (this lets the charging coil in your phone line up with the one inside the wireless charger). The wireless charging coil on Sony phones is located slightly below center. Phone cases should be no thicker than 5 mm for effective charging. Choose the correct adapter for your wireless charger: 5V/2A or above adapter for Standard Charge Mode. Not compatible with 5V/1A adapters. Phone Brands & Power Input For Anker 5W Wireless Chargers Apple iPhone X iPhone XS iPhone XS Max iPhone 8 / 8 Plus iPhone XR This wireless charger provides a standard 5W charge (Standard Charge Mode) to all wirelessly-charged devices. Use with wall chargers, desktop chargers, car chargers, and power strips with an output of 5V/2A or above. Not compatible with the iPhone stock charger (5V/1A). Phone Brands & Power Input For Anker 5W Wireless Chargers Samsung Galaxy S9/S9+ Galaxy S10/S10+/S10e Galaxy S8+ / S8+ Galaxy Note 9 Galaxy S7 / S7 edge / S7 Active Galaxy S6 edge This wireless charger provides a standard 5W charge (Standard Charge Mode) to all wirelessly-charged devices. -
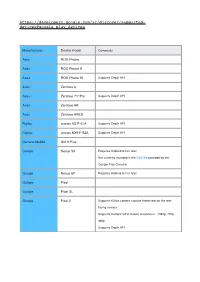
Vuforia Supported Devices
https://developers.google.com/ar/discover/supported- devices#google_play_devices Manufacturer Device model Comments Asus ROG Phone Asus ROG Phone II Asus ROG Phone III Supports Depth API Asus Zenfone 6 Asus Zenfone 7/7 Pro Supports Depth API Asus Zenfone AR Asus Zenfone ARES Fujitsu arrows 5G F-51A Supports Depth API Fujitsu arrows NX9 F-52A Supports Depth API General Mobile GM 9 Plus Google Nexus 5X Requires Android 8.0 or later Not currently included in the CSV file provided by the Google Play Console Google Nexus 6P Requires Android 8.0 or later Google Pixel Google Pixel XL Google Pixel 2 Supports 60 fps camera capture frame rate on the rear- facing camera Supports multiple GPU texture resolutions - 1080p, 720p, 480p Supports Depth API Google Pixel 2 XL Supports 60 fps camera capture frame rate on the rear- facing camera Supports multiple GPU texture resolutions - 1080p, 720p, 480p Supports Depth API Google Pixel 3 Supports 60 fps camera capture frame rate on the rear- facing camera When 60 fps camera capture mode is active, the camera uses fixed focus Supports multiple GPU texture resolutions - 1080p, 720p, 480p Supports Depth API Google Pixel 3 XL Supports 60 fps camera capture frame rate on the rear- facing camera When 60 fps camera capture mode is active, the camera uses fixed focus Supports multiple GPU texture resolutions - 1080p, 720p, 480p Supports Depth API Google Pixel 3a Supports multiple GPU texture resolutions - 1080p, 720p, 480p Supports Depth API Google Pixel 3a XL Supports multiple GPU texture resolutions - 1080p, 720p, -

Huawei Investment & Holding Co., Ltd. 2020 Sustainability Report
Huawei Investment & Holding Co., Ltd. 2020 Sustainability Report Bring digital to every person, home and organization for a fully connected, intelligent world Corporate Profile Who is Huawei? The rotating chairman leads the Board of Directors and its Executive Committee while in office. The Board exercises Founded in 1987, Huawei is a leading global provider decision-making authority for corporate strategy and operations of information and communications technology (ICT) management, and is the highest body responsible for corporate infrastructure and smart devices. We are committed to bringing strategy, operations management, and customer satisfaction. digital to every person, home and organization for a fully connected, intelligent world. We have approximately 197,000 Meanwhile, the Chairman of the Board presides over the employees and we operate in over 170 countries and regions, Representatives' Commission. As Huawei's highest decision- serving more than three billion people around the world. making body, the Commission makes decisions on major company matters, like profit distribution, capital increases, Who owns Huawei? and the elections of members of the Board of Directors and the Supervisory Board. Huawei is a private company wholly owned by its employees. Through the Union of Huawei Investment & Who does Huawei work with? Holding Co., Ltd., we implement an Employee Shareholding Scheme involving 121,269 employees. Only Huawei Externally, we rely on our customers and partners. employees are eligible to participate. No government Customers are at the heart of everything we do, and we agency or outside organization holds shares in Huawei. create value for them with innovative products. Internally, we rely on our hard-working and dedicated employees. -

The Effect of Liability of Foreignness on Firm's Internationalization Process
The Effect of Liability of Foreignness on Firm’s Internationalization Process: A Study of Chinese Firms by Quentin Tigé Master of Science in Administration International Business A Thesis Submitted in Partial Fulfillment of Requirements for a Master of Science in Administration June, 2019 © Quentin Tigé, 2019 Résumé Jusqu’à présent, en ce qui concerne la littérature portant sur les affaires internationales, le centre de l’attention a toujours été porté sur l’expansion internationale des compagnies provenant de pays développés. Cependant, le 21e siècle a entrainé de sérieux changements en ce qui a trait à l’économie globale. Un nombre grandissant de compagnies provenant de marchés émergents rivalisent maintenant dans les marchés occidentaux. Dans ce contexte, il est intéressant d’étudier la réalité et les défis qu’ont à relever les multinationales provenant de marchés émergents. De plus, avec l’émergence de la Chine comme superpuissance économique, une multitude de firmes chinoises rivalisent à présent sur le marché global. Ceci dit, dans la conjoncture actuelle caractérisée par la guerre commerciale entre les États-Unis et la Chine, ainsi que par les conflits entourant la course vers les réseaux 5G, les firmes chinoises subissent des défis additionnels lorsqu’elles opèrent en Occident. Cette recherche vise à répondre à la question suivante : Comment le processus d’internationalisation des firmes chinoises est-il affecté par leur nationalité? Le but est non seulement d’identifier les défis rencontrés par les firmes chinoises en Occident, mais également d’observer le niveau de succès des différentes stratégies employées par celles-ci, et d’identifier les facteurs qui ont un effet de réduction ou d’aggravation des effets des différents défis rencontrés. -
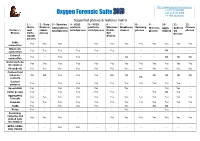
Oxygen Forensic Suite
http://www.oxygen-forensic.com +1 877 9 OXYGEN Oxygen Forensic Suite +44 20 8133 8450 +7 495 222 9278 Supported phones & features matrix 1 – 2 - Sony 3 – Symbian 4 - UIQ2 5 – UIQ3 6 - 7 - 8- 9- 10- 11- 12- Nokia Ericsson S60 platform platform platform Windows Blackberry Samsung Motorola Apple Android Chinese Feature \ and classic smartphones smartphones smartphones Mobile devices phones phones devices OS phones Phones Vertu phones 5/6 devices classic devices phones Cable Yes Yes Yes - Yes Yes Yes Yes Yes Yes Yes Yes connection Bluetooth Yes Yes Yes Yes Yes Yes - - - NA - - connection Infrared Yes - Yes Yes - - NA - - NA NA NA connection General phone Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes information Phonebook Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Custom field labels for NA NA Yes Yes Yes NA NA NA NA NA NA contacts NA Contact Yes - Yes Yes Yes Yes Yes Yes Yes Yes Yes - pictures Speed dials Yes - Yes Yes Yes - Yes - - Yes Yes - Caller groups Yes - Yes Yes Yes Yes - - Yes NA Yes - Aggregated Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Contacts Calendar Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Tasks Yes - Yes Yes Yes - Yes - NA NA - - Notes Yes - - - - - Yes - - Yes - - Incoming, outgoing and Yes Yes Yes - - Yes Yes Yes Yes Yes Yes Yes missed calls information GPRS, EDGE, - - Yes Yes - - - - - - - CSD, HSCSD - and Wi-Fi traffic and sessions log Sent and received SMS, - Sent SMS - Yes Yes Yes(2) - - - - - - MMS, E-mail messages log Deleted - messages - - Yes(1) - Yes(1) - - - Yes(8) - - information Flash SMS -

Rooting Every Android from Extension to Exploitation
Rooting every Android From extension to exploitation Di Shen (@returnsme), James Fang (@id3lr) KEEN LAB TENCENT (@KEEN_LAB) OVERVIEW 3 WI-FI CHIPSETS FOR ANDROID 3 WEXT ATTACK SURFACE ANALYSIS 3 USE DEVICE SPECIFIC VULNERABILITIES TO ROOT THEM ALL 6 CASE STUDIES 7 STACK OVERFLOW VULNERABILITY IN QUALCOMM WEXT 7 DATA SECTION OVERFLOW VULNERABILITY IN MTK WEXT 10 THE OVERFLOW 10 HOW TO EXPLOIT 11 LEAKING VALUES 11 KERNEL CODE EXECUTION 12 USE-AFTER-FREE VULNERABILITY IN BROADCOM WEXT 12 CVE-2016-2475 13 ANDROID-ID-24739315 15 HOW TO TRIGGER 16 RACING AND OBJECT RE-FILLING 18 HEAP SPRAYING BY SENDMMSG 18 HAPPY ROOING 19 GOOGLE’S LATEST MITIGATION 20 CONCLUSION 21 2 From extension to exploitation Rooting every Android Di Shen (@returnsme), James Fang(@idl3r) Keen Lab Tencent (@keen_lab) Overview In this section we are going to discuss the implementation of Wireless Extension (WEXT) subsystem in Android. We are going to analyse the attack surface of WEXT API and reveal its potential weakness. Wi-Fi chipsets for Android All existing Android builds use Linux as its kernel. As a mobile-oriented system, it heavily relies on Wi-Fi and cellular data for communication. For its Wi-Fi part, Android adopted Wireless Extension (WEXT) as its standard API to manage Wi-Fi hardware. The Wireless Extension (WEXT) was designed by Jean Tourrilhes in 1997. It has been widely used for 20 years, yet its design still meets the demanding of modern Wi-Fi hardware. It was designed a wireless API which would allow the user to manipulate any wireless networking device in a standard and uniform way.