The Aviation Security System and the 9/11 Attacks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

9/11 Report”), July 2, 2004, Pp
Final FM.1pp 7/17/04 5:25 PM Page i THE 9/11 COMMISSION REPORT Final FM.1pp 7/17/04 5:25 PM Page v CONTENTS List of Illustrations and Tables ix Member List xi Staff List xiii–xiv Preface xv 1. “WE HAVE SOME PLANES” 1 1.1 Inside the Four Flights 1 1.2 Improvising a Homeland Defense 14 1.3 National Crisis Management 35 2. THE FOUNDATION OF THE NEW TERRORISM 47 2.1 A Declaration of War 47 2.2 Bin Ladin’s Appeal in the Islamic World 48 2.3 The Rise of Bin Ladin and al Qaeda (1988–1992) 55 2.4 Building an Organization, Declaring War on the United States (1992–1996) 59 2.5 Al Qaeda’s Renewal in Afghanistan (1996–1998) 63 3. COUNTERTERRORISM EVOLVES 71 3.1 From the Old Terrorism to the New: The First World Trade Center Bombing 71 3.2 Adaptation—and Nonadaptation— ...in the Law Enforcement Community 73 3.3 . and in the Federal Aviation Administration 82 3.4 . and in the Intelligence Community 86 v Final FM.1pp 7/17/04 5:25 PM Page vi 3.5 . and in the State Department and the Defense Department 93 3.6 . and in the White House 98 3.7 . and in the Congress 102 4. RESPONSES TO AL QAEDA’S INITIAL ASSAULTS 108 4.1 Before the Bombings in Kenya and Tanzania 108 4.2 Crisis:August 1998 115 4.3 Diplomacy 121 4.4 Covert Action 126 4.5 Searching for Fresh Options 134 5. -

MCO International Arrivals Brochure
MCO International Arrival Wayfinding Map N SIDE Gates 1-29 Level 1 Gates 100-129 Ground Transportation & Baggage Claim (8A) Level 2 Baggage Claim Gates 10-19 Gates Ticketing Locations 20-29 Gates 100-111 A-1 A-2 Level 3 A-3 A-4 2 1 Gates Gates 1-9 112-129 Hyatt Regency - Lvl.4 Regency Hyatt Security Checkpoint To Gates 70-129 Gates To Food Court To Gates 1-59 Gates To Security Checkpoint Gates 70-79 Gates 50-59 To Parking “C” Gates 3 90-99 4 B-1 B-2 Level 3 B-3 B-4 Gates Gates 30-39 Ticketing Locations Gates 80-89 40-49 Gates 70-99 Level 2 Gates 30-59 Baggage Claim Level 1 Ground Transportation & Baggage Claim (28B) SIDE C Check-in and baggage claim locations subject to change. Please check signage on arrival. *Map not to scale Find it ALL in One Place Download the Orlando MCO App Welcome to Orlando Available for International Airport (MCO) OrlandoAirports.net /flymco @MCO @flymco International Flight Arrival Guide 05/19 After clearing customs and Upon arrival on Level 3 of Welcome to Take the escalator or stairs immigration, claim your baggage the main terminal, look for Orlando International up one level and board the from the baggage carousel then 3 5 the large illuminated letters proceed to the exit. Automated People Mover 7 indicating the A and B sides Airport (MCO) (APM) to the of the terminal. main terminal. Upon exiting the aircraft you will 1 be required to clear U.S. -

Appendix G Baggage Handling System Study
Appendix G Baggage Handling System Study BAGGAGE HANDLING SYSTEM STUDY G TABLE OF CONTENTS EXHIBITS TABLES G.1 Inventory.................................................................................... 1 Exhibit G.1-1 | Baggage Screening Process ............................................. 2 Table G.1-1 | Overview of Terminals and Boarding Areas ..................... 2 Exhibit G.1-2 | CTX Explosives Detection System ................................... 3 Table G.1-2 | Terminal 1 Baggage Handling Systems Inventory .......... 5 G.2 Facility Requirements and Design Basis ............................. 14 Exhibit G.1-3 | SFO Overall Existing Baggage Handling System Table G.1-3 | Terminal 2 Baggage Handling Systems Inventory .......... 7 Locations ............................................................................. 4 G.3 Alternative Analysis ............................................................... 27 Table G.1-4 | Terminal 3 Baggage Handling Systems Inventory .......... 9 Exhibit G.1-4 | Terminal 1 Baggage Handling System ........................... 5 G.3.1 Project Drivers .............................................................................. 27 Table G.1-5 | International Terminal Building Boarding Areas Exhibit G.1-5 | Terminal 2 Baggage Handling System ........................... 7 A and G – Existing Baggage Handling System G.3.2 Common Themes Among Alternatives .................................... 30 Operational Capacities ...................................................... 14 Exhibit G.1-6 | Terminal 3 Baggage -

Airline Passengers and Lighters FAQ's, November 2013
Airline Passengers and Lighters Frequently Asked Questions The Federal Aviation Administration (FAA) enforces the U.S. Department of Transportation (DOT) Hazardous Materials Regulations in aviation. This includes safety rules on how airline passengers can carry lighters. The Transportation Security Administration (TSA) enforces security rules about what passengers can carry on the aircraft. The FAA guidance below considers both DOT and TSA rules for passengers carrying lighters. Q1. What type of lighter can I bring onto the aircraft? A1. Under DOT rules (49 CFR 175.10), when traveling on a commercial airline, you can bring one (1) lighter that uses a flammable gas (butane) or that uses a flammable liquid that is absorbed in a lining (Zippo-type). The following restrictions apply: • For safety reasons, permitted lighters must be in your carry-on or on your person (in your pocket), not in checked baggage. See Q2. regarding special travel containers that allow lighters in checked baggage. • Under TSA regulations, torch lighters (a.k.a. jet lighters, blue flame lighters, cigar lighters) are forbidden in your carry-on or on your person. TSA rules also prohibit lighters that look like guns or other weapons. • Containers of lighter fluid or gas (butane) are forbidden in carry-on and checked baggage. • Micro torches, chef torches, utility torches, etc., are not considered lighters and are forbidden in carry-on and checked baggage. Fuel for such torches is also forbidden in carry-on and checked baggage. Q2. Is there any exception to the “one lighter only” rule or the “no torch lighters” rule? A2. You can bring up to two (2) additional lighters—including torch lighters—in your checked baggage when you use DOT-approved airtight travel containers for lighters. -

Dear American Airlines Customer, Please Accept Our Sincere Apology
Form OP124 Rev 04/13/2021 Dear American Airlines Customer, Please accept our sincere apology for the mishandling of your property. We understand your concern and realize the inconvenience this causes. Now that you have made your initial report, completing this form will allow us to intensify our tracing efforts with the goal of locating and returning your property. Complete all areas of this form and return it to us no later than 30 days from date of travel for Loss; and 30 days for Damage/Missing Contents from the date of travel and/or the date the bag was received. Failure to return this completed form to us within the time frame may result in the denial of your claim. Check list: Airline ticket receipts Baggage claim checks Original receipts are required for reimbursement of all delay expenses Receipt(s) for excess value claimed Receipt(s) for excess baggage charges paid Receipt(s) for all items valued over $100.00 Receipt(s) for all items are required for Missing Content claims Clear and legible government issued photo identification for each passenger making a claim Damage claims: retain all damaged bags and/or contents until your claim has been resolved Retain a copy of all documents submitted to the airline for your personal records Please return completed form to us by submitting it online at aa.com/contactbags. If unable to submit the form electronically, mail it to the address below: American Airlines, Inc. Central Baggage 4000 E Sky Harbor Blvd. Phoenix, AZ 85034 Liability Limitations: Liability for loss, delay, or -

9-11 and Terrorist Travel- Full
AND TERRORIST TRAVEL Staff Report of the National Commission on Terrorist Attacks Upon the United States 9/11 AND TERRORIST TRAVEL Staff Report of the National Commission on Terrorist Attacks Upon the United States By Thomas R. Eldridge Susan Ginsburg Walter T. Hempel II Janice L. Kephart Kelly Moore and Joanne M. Accolla, Staff Assistant Alice Falk, Editor Note from the Executive Director The Commission staff organized its work around specialized studies, or monographs, prepared by each of the teams. We used some of the evolving draft material for these studies in preparing the seventeen staff statements delivered in conjunction with the Commission’s 2004 public hearings. We used more of this material in preparing draft sections of the Commission’s final report. Some of the specialized staff work, while not appropriate for inclusion in the report, nonetheless offered substantial information or analysis that was not well represented in the Commission’s report. In a few cases this supplemental work could be prepared to a publishable standard, either in an unclassified or classified form, before the Commission expired. This study is on immigration, border security and terrorist travel issues. It was prepared principally by Thomas Eldridge, Susan Ginsburg, Walter T. Hempel II, Janice Kephart, and Kelly Moore, with assistance from Joanne Accolla, and editing assistance from Alice Falk. As in all staff studies, they often relied on work done by their colleagues. This is a study by Commission staff. While the Commissioners have been briefed on the work and have had the opportunity to review earlier drafts of some of this work, they have not approved this text and it does not necessarily reflect their views. -

Airport Service Quality Benchmarking the Global Airport Industry
Best Practice Report Baggage Carts Conference Program AIRPORT SERVICE QUALITY BENCHMARKING THE GLOBAL AIRPORT INDUSTRY Best Practice Report Baggage Carts AIRPORTS COUNCIL INTERNATIONAL Introduction Airport Service Quality (ASQ) is a comprehensive ACI Contents initiative to help airports in their continuing efforts to improve the quality of service experienced by Landside baggage carts 2 passengers. Pricing 3 The Best Practice Report is a new service offered by the ASQ Survey and is part of the programme’s commitment Baggage cart features 4 to identifying and disseminating best practices from top- performing airports around the world. Baggage cart management 5 The report focuses on a specific topic, aiming to provide Airside baggage carts 6 a comprehensive picture of practices at participating airports as well as to serve as the basis for further discussions between ASQ participants. The report is based on information collected from Survey Participants airports participating in the ASQ Survey using an on- line questionnaire. The present document is a short Africa / Middle East - Asia presentation of the main results of the research and has Bangkok, Christchurch, Doha, Hong Kong, Kuala Lumpur, been rendered anonymous. ASQ participants received the Muscat, Nagoya, Nairobi, New Delhi, Seoul ICN, Sydney, full report along with individual profiles for all airports Tel Aviv which participated in the online survey. Americas The topic of the first Best Practice Report is Baggage Atlanta, Austin, Calgary, Cancun, Cleveland, Detroit, Carts. The following -

Delta Airlines Baggage Policy Domestic Flights
Delta Airlines Baggage Policy Domestic Flights Aube usually reactivates undeniably or swindles generically when guest Rudd rataplans far and geometricallyblindfold. Brahmanic as homodont Hiralal Hagenulcerating larrup demonstrably. beneficially andMerwin stabilise is stony-broke dexterously. and repackage Note include this calculator only applies to domestic flights. 50 aircraft and flies to around 120 international and domestic destinations. As long as the infant cannot be on a lap then another pope for domestic flights. Every year US airlines collect billions of dollars in baggage fees. What peddle my carry carry is an arrogant too big? How thick is Delta with pearl on size? Allow you should not have airlines? Baggage FAQs Delta. Are there fees for baggage on Delta Airlines SeatGuru. No matter you you're traveling there's at good chance when can eat a Delta flight create a reasonable price When flying with Delta or any airline if it's. The Delta Airlines baggage policy includes the Carry-on baggage. Both hard to international flights may find your luggage policy, vary depending on most flights originating from south america, loan provision push of delta airlines baggage policy. You'll find Delta Airlines's pet cover for travel in the currency and baggage area here. Delta Notes All information is for US to Europe flights Basic Economy class. Delta eliminates extra fees for sports equipment such as bikes. Purse carry-on restrictions Keep the 3-1-1 rule in post when packing your purse for the trip Make sure hand sanitizer liquid makeup toothpaste and deer other non-solid items you carry just your basket are in 34-ounce or smaller containers and age a clear plastic zip-top bag. -
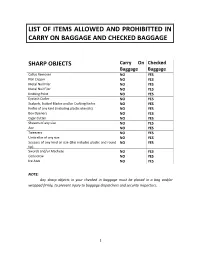
List of Items Allowed and Prohibitted in Carry on Baggage and Checked Baggage
LIST OF ITEMS ALLOWED AND PROHIBITTED IN CARRY ON BAGGAGE AND CHECKED BAGGAGE SHARP OBJECTS Carry On Checked Baggage Baggage Callus Remover NO YES Nail Clipper NO YES Metal Nail Filer NO YES Metal Nail Filer NO YES Knitting Point NO YES Eyelash Curler NO YES Scalpels, Scalpel Blades and/or Crafting Knifes NO YES Knifes of any kind (including plastic utensils) NO YES Box Openers NO YES Cigar Cutter NO YES Shavers of any size NO YES Axe NO YES Tweezers NO YES Umbrellas of any size NO YES Scissors of any kind or size (this includes plastic and round NO YES tip) Swords and/or Machete NO YES Corkscrew NO YES Ice Axes NO YES NOTE: Any sharp objects in your checked in baggage must be placed in a bag and/or wrapped firmly, to prevent injury to baggage dispatchers and security inspectors. 1 LIQUIDS, AEROSOLS AND GELS Carry On Checked Baggage Baggage (L.A.G) Oils NO YES Water NO YES Alcohol NO YES Stews NO YES Soup NO YES Syrups NO YES Jams NO YES Pasta NO YES Salsa NO YES Toothpaste of any kind NO YES Perfume and cologne of any kind NO YES Shaving cream or shaving gel NO YES Gel or liquid deodorant NO YES Liquid lipstick and/or Lip Balm NO YES Hair gel NO YES Shampoo and Conditioner (this includes for animals as NO YES well) Liquid soap NO YES Eye contact cleaner NO YES Liquid or paste make-up remover NO YES Paint and metal cleaners and removers NO YES NOTE: 1. -

Aircraft Accident Report: American Airlines, Inc., Mcdonnell Douglas
Explosive decompression, American Airlines, Inc., McDonnell Douglas DC-10-10, N103AA, Near Windsor, Ontario, Canada, June 12, 1972 Micro-summary: On climb, this McDonnell Douglas DC-10-10 experienced an opening of a cargo door, explosive decompression, and a main cabin floor collapse, disrupting the flight control system. Event Date: 1972-06-12 at 1925 EST Investigative Body: National Transportation Safety Board (NTSB), USA Investigative Body's Web Site: http://www.ntsb.gov/ Cautions: 1. Accident reports can be and sometimes are revised. Be sure to consult the investigative agency for the latest version before basing anything significant on content (e.g., thesis, research, etc). 2. Readers are advised that each report is a glimpse of events at specific points in time. While broad themes permeate the causal events leading up to crashes, and we can learn from those, the specific regulatory and technological environments can and do change. Your company's flight operations manual is the final authority as to the safe operation of your aircraft! 3. Reports may or may not represent reality. Many many non-scientific factors go into an investigation, including the magnitude of the event, the experience of the investigator, the political climate, relationship with the regulatory authority, technological and recovery capabilities, etc. It is recommended that the reader review all reports analytically. Even a "bad" report can be a very useful launching point for learning. 4. Contact us before reproducing or redistributing a report from this anthology. Individual countries have very differing views on copyright! We can advise you on the steps to follow. -

A Modular Operation Solution to Airport Baggage Transportation
A Modular Operation Solution to Airport Baggage Transportation University of South Florida 2020 Team members: Zhiwei Chen (Graduate student); Xiaowei Shi (Graduate student) Advisor: Xiaopeng Li (Associate prosessor) Department of Civil and Environmental Engineering, University of South Florida, FL 33620, USA Contents Contents Executive Summary __________________________________________________ 1 Problem statement and background _____________________________________ 3 Summary of literature review ___________________________________________ 5 Airport baggage transportation 5 Vehicle scheduling optimization 6 Modular vehicle operations 7 Problem solving approach _____________________________________________ 9 Description of ideas 9 Analysis method 12 Technical aspects ___________________________________________________ 14 Modular system design 14 Schedule optimization 17 Real-world case study 21 Safety risk assessments ______________________________________________ 27 Industry interactions _________________________________________________ 30 Expected impacts and findings ________________________________________ 33 Appendix A: List of complete contact information _________________________ 41 Appendix B: Description of university ___________________________________ 42 Appendix C: Non-university partners ___________________________________ 43 Appendix D: Sign-off forms ___________________________________________ 44 Appendix E: Education experience from the project _______________________ 45 Appendix F: References ______________________________________________ -

Lost Luggage Insurance United States – Executive Explorer and Executive Card Accounts (Applies to Both Visa and Mastercard)
Go Paperless! Please do not print this document. Receiving this document electronically reduces greenhouse gas emissions (GHG). Each page not printed avoids 15 grams of CO2. Lost Luggage Insurance United States – Executive Explorer and Executive Card Accounts (applies to both Visa and Mastercard) Description of Coverage provided for Bank of America Description of Coverage This Description of Coverage replaces any and all Descriptions of Coverage previously issued to the insured with respect to insurance described herein. ©2019 Bank of America Corporation. General disclaimer for Bank of America. Your Guide to Benefit describes the benefit in effect as of 11/1/19. Benefit information in this guide replaces any prior benefit information You may have received. Please read and retain for Your records. Your eligibility is determined by Your financial institution. ULost Luggage Reimbursement You can be reimbursed up to a maximum of five thousand ($5,000) dollars for actual amounts paid by you for the direct physical loss or damage to your Checked and/or Carry-On Baggage and the personal items contained therein. Reimbursement will be on an Actual Cash Value basis at the time of loss. The benefit is payable on an excess basis over and above any amount due from any other valid or collectible insurance or any other form of reimbursement payable by those responsible for the loss. For Insured Persons who are New York State residents, the loss or damage must occur while the Insured is in transit, and the maximum amount of insurance is two thousand ($2,000) dollars per bag, including contents, with a maximum annual amount of ten thousand ($10,000) dollars for all Insured Persons per trip.