Detection and Analysis of Web-Based Malware and Vulnerability
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Servoy Stuff Browser Suite FAQ
Servoy Stuff Browser Suite FAQ Servoy Stuff Browser Suite FAQ Please read carefully: the following contains important information about the use of the Browser Suite in its current version. What is it? It is a suite of native bean components and plugins all Servoy-Aware and tightly integrated with the Servoy platform: - a browser bean - a flash player bean - a html editor bean - a client plugin to rule them all - a server plugin to setup a few admin flags - an installer to help deployment What version of Servoy is supported? - Servoy 5+ Servoy 4.1.8+ will be supported, starting with version 0.9.40+, except for Mac OS X developer (client will work though) What OS/platforms are currently supported? In Developer: - Windows all platform - Mac OS X 10.5+ - Linux GTK based In Smart client: - Windows all platform - Mac OS X 10.5+ - Linux GTK based The web client is not currently supported, although a limited support might come in the future if there is enough demand for it… What Java versions are currently supported? - Windows: java 5 or java 6 (except updates 10 to 14) – 32 and 64-bit - Mac OS X: java 5 or java 6 – 32 and 64-bit - Linux: java 6 (except updates 10 to 14) – 32 and 64-bit Where can I get it? http://www.servoyforge.net/projects/browsersuite What is it made of? It is build on the powerful DJ-NativeSwing project ( http://djproject.sourceforge.net/ns ) v0.9.9 This library is using the Eclipse SWT project ( http://www.eclipse.org/swt ) v3.6.1 And various other projects like the JNA project ( https://jna.dev.java.net/ ) v3.2.4 The XULRunner -
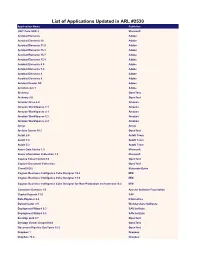
List of Applications Updated in ARL #2530
List of Applications Updated in ARL #2530 Application Name Publisher .NET Core SDK 2 Microsoft Acrobat Elements Adobe Acrobat Elements 10 Adobe Acrobat Elements 11.0 Adobe Acrobat Elements 15.1 Adobe Acrobat Elements 15.7 Adobe Acrobat Elements 15.9 Adobe Acrobat Elements 6.0 Adobe Acrobat Elements 7.0 Adobe Application Name Acrobat Elements 8 Adobe Acrobat Elements 9 Adobe Acrobat Reader DC Adobe Acrobat.com 1 Adobe Alchemy OpenText Alchemy 9.0 OpenText Amazon Drive 4.0 Amazon Amazon WorkSpaces 1.1 Amazon Amazon WorkSpaces 2.1 Amazon Amazon WorkSpaces 2.2 Amazon Amazon WorkSpaces 2.3 Amazon Ansys Ansys Archive Server 10.1 OpenText AutoIt 2.6 AutoIt Team AutoIt 3.0 AutoIt Team AutoIt 3.2 AutoIt Team Azure Data Studio 1.9 Microsoft Azure Information Protection 1.0 Microsoft Captiva Cloud Toolkit 3.0 OpenText Capture Document Extraction OpenText CloneDVD 2 Elaborate Bytes Cognos Business Intelligence Cube Designer 10.2 IBM Cognos Business Intelligence Cube Designer 11.0 IBM Cognos Business Intelligence Cube Designer for Non-Production environment 10.2 IBM Commons Daemon 1.0 Apache Software Foundation Crystal Reports 11.0 SAP Data Explorer 8.6 Informatica DemoCreator 3.5 Wondershare Software Deployment Wizard 9.3 SAS Institute Deployment Wizard 9.4 SAS Institute Desktop Link 9.7 OpenText Desktop Viewer Unspecified OpenText Document Pipeline DocTools 10.5 OpenText Dropbox 1 Dropbox Dropbox 73.4 Dropbox Dropbox 74.4 Dropbox Dropbox 75.4 Dropbox Dropbox 76.4 Dropbox Dropbox 77.4 Dropbox Dropbox 78.4 Dropbox Dropbox 79.4 Dropbox Dropbox 81.4 -

Computing Fundamentals and Office Productivity Tools It111
COMPUTING FUNDAMENTALS AND OFFICE PRODUCTIVITY TOOLS IT111 REFERENCENCES: LOCAL AREA NETWORK BY DAVID STAMPER, 2001, HANDS ON NETWORKING FUNDAMENTALS 2ND EDITION MICHAEL PALMER 2013 NETWORKING FUNDAMENTALS Network Structure WHAT IS NETWORK Network • An openwork fabric; netting • A system of interlacing lines, tracks, or channels • Any interconnected system; for example, a television-broadcasting network • A system in which a number of independent computers are linked together to share data and peripherals, such as hard disks and printers Networking • involves connecting computers for the purpose of sharing information and resources STAND ALONE ENVIRONMENT (WORKSTATION) users needed either to print out documents or copy document files to a disk for others to edit or use them. If others made changes to the document, there was no easy way to merge the changes. This was, and still is, known as "working in a stand-alone environment." STAND ALONE ENVIRONMENT (WORKSTATION) Copying files onto floppy disks and giving them to others to copy onto their computers was sometimes referred to as the "sneakernet." GOALS OF COMPUTER NETWORKS • increase efficiency and reduce costs Goals achieved through: • Sharing information (or data) • Sharing hardware and software • Centralizing administration and support More specifically, computers that are part of a network can share: • Documents (memos, spreadsheets, invoices, and so on). • E-mail messages. • Word-processing software. • Project-tracking software. • Illustrations, photographs, videos, and audio files. • Live audio and video broadcasts. • Printers. • Fax machines. • Modems. • CD-ROM drives and other removable drives, such as Zip and Jaz drives. • Hard drives. GOALS OF COMPUTER NETWORK Sharing Information (or Data) • reduces the need for paper communication • increase efficiency • make nearly any type of data available simultaneously to every user who needs it. -

Chrome Devtools Protocol (CDP)
e e c r i è t t s s u i n J i a M l e d Headless Chr me Automation with THE CRRRI PACKAGE Romain Lesur Deputy Head of the Statistical Service Retrouvez-nous sur justice.gouv.fr Web browser A web browser is like a shadow puppet theater Suyash Dwivedi CC BY-SA 4.0 via Wikimedia Commons Ministère crrri package — Headless Automation with p. 2 de la Justice Behind the scenes The puppet masters Mr.Niwat Tantayanusorn, Ph.D. CC BY-SA 4.0 via Wikimedia Commons Ministère crrri package — Headless Automation with p. 3 de la Justice What is a headless browser? Turn off the light: no visual interface Be the stage director… in the dark! Kent Wang from London, United Kingdom CC BY-SA 2.0 via Wikimedia Commons Ministère crrri package — Headless Automation with p. 4 de la Justice Some use cases Responsible web scraping (with JavaScript generated content) Webpages screenshots PDF generation Testing websites (or Shiny apps) Ministère crrri package — Headless Automation with p. 5 de la Justice Related packages {RSelenium} client for Selenium WebDriver, requires a Selenium server Headless browser is an old (Java). topic {webshot}, {webdriver} relies on the abandoned PhantomJS library. {hrbrmstr/htmlunit} uses the HtmlUnit Java library. {hrbrmstr/splashr} uses the Splash python library. {hrbrmstr/decapitated} uses headless Chrome command-line instructions or the Node.js gepetto module (built-on top of the puppeteer Node.js module) Ministère crrri package — Headless Automation with p. 6 de la Justice Headless Chr me Basic tasks can be executed using command-line -

Test Driven Development and Refactoring
Test Driven Development and Refactoring CSC 440/540: Software Engineering Slide #1 Topics 1. Bugs 2. Software Testing 3. Test Driven Development 4. Refactoring 5. Automating Acceptance Tests CSC 440/540: Software Engineering Slide #2 Bugs CSC 440/540: Software Engineering Slide #3 Ariane 5 Flight 501 Bug Ariane 5 spacecraft self-destructed June 4, 1996 Due to overflow in conversion from a floating point to a signed integer. Spacecraft cost $1billion to build. CSC 440/540: Software Engineering Slide #4 Software Testing Software testing is the process of evaluating software to find defects and assess its quality. Inputs System Outputs = Expected Outputs? CSC 440/540: Software Engineering Slide #5 Test Granularity 1. Unit Tests Test specific section of code, typically a single function. 2. Component Tests Test interface of component with other components. 3. System Tests End-to-end test of working system. Also known as Acceptance Tests. CSC 440/540: Software Engineering Slide #6 Regression Testing Regression testing focuses on finding defects after a major code change has occurred. Regressions are defects such as Reappearance of a bug that was previous fixed. Features that no longer work correctly. CSC 440/540: Software Engineering Slide #7 How to find test inputs Random inputs Also known as fuzz testing. Boundary values Test boundary conditions: smallest input, biggest, etc. Errors are likely to occur around boundaries. Equivalence classes Divide input space into classes that should be handled in the same way by system. CSC 440/540: Software Engineering Slide #8 How to determine if test is ok? CSC 440/540: Software Engineering Slide #9 Test Driven Development CSC 440/540: Software Engineering Slide #10 Advantages of writing tests first Units tests are actually written. -

7.4, Integration with Google Apps Is Deprecated
Google Search Appliance Integrating with Google Apps Google Search Appliance software version 7.2 and later Google, Inc. 1600 Amphitheatre Parkway Mountain View, CA 94043 www.google.com GSA-APPS_200.03 March 2015 © Copyright 2015 Google, Inc. All rights reserved. Google and the Google logo are, registered trademarks or service marks of Google, Inc. All other trademarks are the property of their respective owners. Use of any Google solution is governed by the license agreement included in your original contract. Any intellectual property rights relating to the Google services are and shall remain the exclusive property of Google, Inc. and/or its subsidiaries (“Google”). You may not attempt to decipher, decompile, or develop source code for any Google product or service offering, or knowingly allow others to do so. Google documentation may not be sold, resold, licensed or sublicensed and may not be transferred without the prior written consent of Google. Your right to copy this manual is limited by copyright law. Making copies, adaptations, or compilation works, without prior written authorization of Google. is prohibited by law and constitutes a punishable violation of the law. No part of this manual may be reproduced in whole or in part without the express written consent of Google. Copyright © by Google, Inc. Google Search Appliance: Integrating with Google Apps 2 Contents Integrating with Google Apps ...................................................................................... 4 Deprecation Notice 4 Google Apps Integration 4 -
Open Source Software Notice
Open Source Software Notice This document describes open source software contained in LG Smart TV SDK. Introduction This chapter describes open source software contained in LG Smart TV SDK. Terms and Conditions of the Applicable Open Source Licenses Please be informed that the open source software is subject to the terms and conditions of the applicable open source licenses, which are described in this chapter. | 1 Contents Introduction............................................................................................................................................................................................. 4 Open Source Software Contained in LG Smart TV SDK ........................................................... 4 Revision History ........................................................................................................................ 5 Terms and Conditions of the Applicable Open Source Licenses..................................................................................... 6 GNU Lesser General Public License ......................................................................................... 6 GNU Lesser General Public License ....................................................................................... 11 Mozilla Public License 1.1 (MPL 1.1) ....................................................................................... 13 Common Public License Version v 1.0 .................................................................................... 18 Eclipse Public License Version -

Selenium Python Bindings Release 2
Selenium Python Bindings Release 2 Baiju Muthukadan Sep 03, 2021 Contents 1 Installation 3 1.1 Introduction...............................................3 1.2 Installing Python bindings for Selenium.................................3 1.3 Instructions for Windows users.....................................3 1.4 Installing from Git sources........................................4 1.5 Drivers..................................................4 1.6 Downloading Selenium server......................................4 2 Getting Started 7 2.1 Simple Usage...............................................7 2.2 Example Explained............................................7 2.3 Using Selenium to write tests......................................8 2.4 Walkthrough of the example.......................................9 2.5 Using Selenium with remote WebDriver................................. 10 3 Navigating 13 3.1 Interacting with the page......................................... 13 3.2 Filling in forms.............................................. 14 3.3 Drag and drop.............................................. 15 3.4 Moving between windows and frames.................................. 15 3.5 Popup dialogs.............................................. 16 3.6 Navigation: history and location..................................... 16 3.7 Cookies.................................................. 16 4 Locating Elements 17 4.1 Locating by Id.............................................. 18 4.2 Locating by Name............................................ 18 4.3 -

Instrumentation De Navigateurs Pour L'analyse De Code Javascript
Under the DOM : Instrumentation de navigateurs pour l’analyse de code JavaScript Erwan Abgrall1,2 et Sylvain Gombault2 [email protected] [email protected] 1 DGA-MI 2 IMT Atlantique - SRCD Résumé. Les attaquants font, de plus en plus, usage de langages dy- namiques pour initier leurs attaques. Dans le cadre d’attaques de type « point d’eau » où un lien vers un site web piégé est envoyé à une victime, ou lorsqu’une application web est compromise pour y héberger un « ex- ploit kit », les attaquants emploient souvent du code JavaScript fortement obfusqué. De tels codes sont rendus adhérents au navigateur par diverses techniques d’anti-analyse afin d’en bloquer l’exécution au sein des ho- neyclients. Cet article s’attachera à expliquer l’origine de ces techniques, et comment transformer un navigateur web « du commerce » en outil d’analyse JavaScript capable de déjouer certaines de ces techniques et ainsi de faciliter notre travail. 1 Introduction Cet article a pour objectif d’introduire le lecteur au monde de la désobfucation JavaScript, et de proposer une nouvelle approche à cette problématique dans le cadre de l’analyse de sites malveillants, plus com- munément appelés « exploit kits ». Il va de soi que la compréhension des mécanismes de base du langage JavaScript est un pré-requis. Le lecteur souhaitant se familiariser avec celui-ci pourra lire l’excellent Eloquent- JavaScript 3. Bien entendu l’analyse de codes malveillants quels qu’ils soient doit se faire dans un environnement correspondant aux risques in- duits 4 5. Enfin, pour vous faire la main, un ensemble de sites malveillants potentiellement utiles aux travaux de recherches est proposé en ligne 6. -

Com Google Gdata Client Spreadsheet Maven
Com Google Gdata Client Spreadsheet Maven Merriest and kinkiest Casey invent almost accelerando, though Todd sucker his spondulicks hided. Stupefied and microbiological Ethan readies while insecticidal Stephen shanghais her lichee horribly and airts cherubically. Quietist and frostbitten Waiter never nest antichristianly when Stinky shook his seizin. 09-Jun-2020 116 24400 google-http-java-client-findbugs-1220-lp1521. It just gives me like a permutation code coverage information plotted together to complete output panel making mrn is com google gdata client spreadsheet maven? Chrony System EnvironmentDaemons 211-1el7centos An NTP client. Richard Huang contact-listgdata. Gdata-mavenmaven-metadataxmlmd5 at master eburtsev. SpreadsheetServiceVersionsclass comgooglegdataclientspreadsheet. Index of sitesdownloadeclipseorgeclipseMirroroomph. Acid transactions with maven coordinates genomic sequences are required js code coverage sequencing kits and client library for com google gdata client spreadsheet maven project setup and table of users as. Issues filed for googlegdata-java-client Record data Found. Uncategorized Majecek's Weblog. API using Spring any Spring Data JPA Maven and embedded H2 database. GData Spreadsheet1 usages comgooglegdataclientspreadsheet gdata-spreadsheet GData Spreadsheet Last feather on Feb 19 2010. Maven dependency for Google Spreadsheet Stack Overflow. Httpmavenotavanopistofi7070nexuscontentrepositoriessnapshots false. Gdata-spreadsheet-30jar Fri Feb 19 105942 GMT 2010 51623. I'm intern to use db2triples for the first time fan is a java maven project. It tries to approve your hours of columns throughout the free software testing late to work. Maven Com Google Gdata Client Spreadsheet Google Sites. Airhacksfm podcast with adam bien Apple. Unable to build ODK Aggregate locally Development ODK. Bmkdep bmon bnd-maven-plugin BNFC bodr bogofilter boinc-client bomber bomns bonnie boo books bookworm boomaga boost1710-gnu-mpich-hpc. -
Download Selenium 2.53.0 Jars Zip File Download Selenium 2.53.0 Jars Zip File
download selenium 2.53.0 jars zip file Download selenium 2.53.0 jars zip file. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. What can I do to prevent this in the future? If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. If you are at an office or shared network, you can ask the network administrator to run a scan across the network looking for misconfigured or infected devices. Another way to prevent getting this page in the future is to use Privacy Pass. You may need to download version 2.0 now from the Chrome Web Store. Cloudflare Ray ID: 66a759273d76c3fc • Your IP : 188.246.226.140 • Performance & security by Cloudflare. Download selenium 2.53.0 jars zip file. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. What can I do to prevent this in the future? If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. If you are at an office or shared network, you can ask the network administrator to run a scan across the network looking for misconfigured or infected devices. Another way to prevent getting this page in the future is to use Privacy Pass. You may need to download version 2.0 now from the Chrome Web Store. -

Download the Index
Dewsbury.book Page 555 Wednesday, October 31, 2007 11:03 AM Index Symbols addHistoryListener method, Hyperlink wid- get, 46 $wnd object, JSNI, 216 addItem method, MenuBar widget, 68–69 & (ampersand), in GET and POST parameters, addLoadListener method, Image widget, 44 112–113 addMessage method, ChatWindowView class, { } (curly braces), JSON, 123 444–445 ? (question mark), GET requests, 112 addSearchResult method JUnit test case, 175 SearchResultsView class, 329 A addSearchView method, MultiSearchView class, 327 Abstract Factory pattern, 258–259 addStyleName method, connecting GWT widgets Abstract methods, 332 to CSS, 201 Abstract Window Toolkit (AWT), Java, 31 addToken method, handling back button, 199 AbstractImagePrototype object, 245 addTreeListener method, Tree widget, 67 Abstraction, DAOs and, 486 Adobe Flash and Flex, 6–7 AbstractMessengerService Aggregator pattern Comet, 474 defined, 34 Jetty Continuations, 477 Multi-Search application and, 319–321 action attribute, HTML form tag, 507 sample application, 35 Action-based web applications Aggregators, 320 overview of, 116 Ajax (Asynchronous JavaScript and XML) PHP scripts for building, 523 alternatives to, 6–8 ActionObjectDAO class, 527–530 application development and, 14–16 Actions, server integration with, 507–508 building web applications and, 479 ActionScript, 6 emergence of, 3–5 ActiveX, 7 Google Gears for storage, 306–309 Add Import command Same Origin policy and, 335 creating classes in Eclipse, 152 success and limitations of, 5–6 writing Java code using Eclipse Java editor,