NNJ09HD46C Section J-10B155 - MCCS ATTACHMENT J-10
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Command Line Interface
Command Line Interface Squore 21.0.2 Last updated 2021-08-19 Table of Contents Preface. 1 Foreword. 1 Licence. 1 Warranty . 1 Responsabilities . 2 Contacting Vector Informatik GmbH Product Support. 2 Getting the Latest Version of this Manual . 2 1. Introduction . 3 2. Installing Squore Agent . 4 Prerequisites . 4 Download . 4 Upgrade . 4 Uninstall . 5 3. Using Squore Agent . 6 Command Line Structure . 6 Command Line Reference . 6 Squore Agent Options. 6 Project Build Parameters . 7 Exit Codes. 13 4. Managing Credentials . 14 Saving Credentials . 14 Encrypting Credentials . 15 Migrating Old Credentials Format . 16 5. Advanced Configuration . 17 Defining Server Dependencies . 17 Adding config.xml File . 17 Using Java System Properties. 18 Setting up HTTPS . 18 Appendix A: Repository Connectors . 19 ClearCase . 19 CVS . 19 Folder Path . 20 Folder (use GNATHub). 21 Git. 21 Perforce . 23 PTC Integrity . 25 SVN . 26 Synergy. 28 TFS . 30 Zip Upload . 32 Using Multiple Nodes . 32 Appendix B: Data Providers . 34 AntiC . 34 Automotive Coverage Import . 34 Automotive Tag Import. 35 Axivion. 35 BullseyeCoverage Code Coverage Analyzer. 36 CANoe. 36 Cantata . 38 CheckStyle. .. -

A Software Package to Support Mission Analysis and Orbital Mechanics Calculations
A Software Package to Support Mission Analysis and Orbital Mechanics Calculations Jorge Tiago Melo Barbosa da Silva e Vila Thesis to obtain the Master of Science Degree in Aerospace Engineering Supervisor: Prof. Paulo Jorge Soares Gil Examination Committee Chairperson: Prof. João Manuel Lage de Miranda Lemos Supervisor: Prof. Paulo Jorge Soares Gil Members of the Committee: Prof. Bertinho Manuel D'Andrade da Costa July of 2015 Dedicated to the loving memory of my grandfather Joaquim Barbosa, whom I shall always remember. Acknowledgements Firstly, I would like to express my gratitude to my supervisor Prof. Paulo Gil for the ideas, remarks, comments, and many engaging conversations which not only saw me through the learning process of this thesis, but also helped me personally. I want to thank Dr. Carlos del Burgo Díaz for the confidence shown in future applications of the software and the help provided with the star map alignment. I want to acknowledge Patrice-Emmanuel Schmitz, from the Open Source Observatory and Repository, for his legal opinions regarding the EUPL licensing. Furthermore, I want to thank Pavel Holoborodko for the excellent MPFR C++ interface class and the professionalism, sympathy, and cooperation displayed while resolving licensing issues. I would also like to thank my parents for the care and interest shown throughout the years in my education, and for the support given in pursuing the interests which led me here. Lastly, I want to express my deepest gratitude to Ana Morais for the love, patience, and continuous support during the development of this thesis. Without you none of this would have been possible. -

Analysis of Devops Tools to Predict an Optimized Pipeline by Adding Weightage for Parameters
International Journal of Computer Applications (0975 – 8887) Volume 181 – No. 33, December 2018 Analysis of DevOps Tools to Predict an Optimized Pipeline by Adding Weightage for Parameters R. Vaasanthi V. Prasanna Kumari, PhD S. Philip Kingston Research Scholar, HOD, MCA Project Manager SCSVMV University Rajalakshmi Engineering Infosys, Mahindra City, Kanchipuram College, Chennai Chennai ABSTRACT cloud. Now-a-days more than ever, DevOps [Development + Operations] has gained a tremendous amount of attention in 2. SCM software industry. Selecting the tools for building the DevOps Source code management (SCM) is a software tool used for pipeline is not a trivial exercise as there are plethora’s of tools development, versioning and enables team working in available in market. It requires thought, planning, and multiple locations to work together more effectively. This preferably enough time to investigate and consult other plays a vital role in increasing team’s productivity. Some of people. Unfortunately, there isn’t enough time in the day to the SCM tools, considered for this study are GIT, SVN, CVS, dig for top-rated DevOps tools and its compatibility with ClearCase, Mercurial, TFS, Monotone, Bitkeeper, Code co- other tools. Each tool has its own pros/cons and compatibility op, Darcs, Endevor, Fossil, Perforce, Rational Synergy, of integrating with other tools. The objective of this paper is Source Safe, and GNU Bazaar. Table1 consists of SCM tools to propose an approach by adding weightage to each with weightage. parameter for the curated list of the DevOps tools. 3. BUILD Keywords Build is a process that enables source code to be automatically DevOps, SCM, dependencies, compatibility and pipeline compiled into binaries including code level unit testing to ensure individual pieces of code behave as expected [4]. -
Securecrt 7.3.6 Crack for Mac >>>
Securecrt 7.3.6 Crack For Mac >>> http://shurll.com/77o35 1 / 5 2 / 5 hash,,47850D6A1C717CEC4534B14525ED9BF2292DD905,,... VanDyke,,SecureCRT,,and,,SecureFX,,7 .3.6,,[Mac,,Os,,X],,[MAC599],,DOWNLOAD,,TORRENTSecureCRT,,for,,Mac,,OS,,X,,7.1... VanDyke,,Secu reCRT,,and,,SecureFX,,7.3.6,,[Mac,,Os,,X].torrent,,내부,,파일,,..Turn,,,your,,,computer,,,into,,,a,,,terminal,, ,server,,,using,,,Serial,,,to,,,Ethernet,,,Converter,,,with,,,its,,,amazing,,,capability,,,to,,,share,,,serial,,, devices,,,in,,,... Free,,,Download,,,SecureCRT,,,for,,,Mac,,,8.1.3,,,Build,,,1382,,,-,,,A,,,fully-featured,,,te rminal,,,emulator,,,as,,,well,,,as,,,a,,,SSH,,,and,,,Telnet,,,client,,,with,,,advanced,,,session,,,mana... Do wnload,,,VanDyke,,,SecureCRT,,,and,,,SecureFX,,,7.3.6,,,[Mac,,,Os,,,X],,,[MAC599],,,torrent,,,or,,,any,, ,other,,,torrent,,,from,,,Mac,,,category. SecureCRT®,,,7.3.6.963,,,for,,,MAC,,,|,,,40.7MbUsers,,,with,,,PCs,,,installed,,,with,,,Windows,,,8. Secu reCRT,,,provides,,,rock-solid,,,terminal,,,emulation,,,for,,,computing,,,professionals,,,,raising,,,product ivity,,,with,,,advanced,,,session,,,management,,,and,,,a,,,host,,,of,,,ways,,,to,,,save SecureCRT,,,for,,, Mac,,,,free,,,and,,,safe,,,downloadSecureCRT,,,supports,,,SSH2,,,,SSH1,,,,Telnet,,,,Telnet/SSL,,,,Serial, ,,,and,,,other,,,protocols..It,,,has,,,been,,,designed,,,to,,,be,,,used,,,during,,,the,,,high,,,stress,,,produc tion,,,... Torrentz,,,-,,,Fast,,,and,,,convenient,,,Torrents,,,Search,,,EngineApowersoft,,Screen,,Capture, ,Pro,,1.3.1,,InclTurn,,your,,computer,,into,,a,,terminal,,server,,using,,Serial,,to,,Ethernet,,Converter,, -

1 James Webb Space Telescope Initial Mid-Course Correction Monte Carlo Implementation Using Task Parallelism Jeremy Petersen
James Webb Space Telescope Initial Mid-Course Correction Monte Carlo Implementation using Task Parallelism Jeremy Petersen(1), Jason Tichy(2), Geoffrey Wawrzyniak(3), and Karen Richon(4) (1,2,3)a.i. solutions, Inc., 10001 Derekwood Lane, Lanham, MD 20706, 301-306-1756, [email protected]. (4)Code 595.0, NASA Goddard Space Flight Center, 8800 Greenbelt Road, Greenbelt MD, 20771. 301-286-8845, [email protected]. The James Webb Space Telescope will be launched into a highly elliptical orbit that does not possess sufficient energy to achieve a proper Sun-Earth/Moon L2 libration point orbit. Three mid-course correction (MCC) maneuvers are planned to rectify the energy deficit: MCC-1a, MCC-1b, and MCC-2. To validate the propellant budget and trajectory design methods, a set of Monte Carlo analyses that incorporate MCC maneuver modeling and execution are employed. The first analysis focuses on the effects of launch vehicle injection errors on the magnitude of MCC-1a. The second on the spread of potential V based on the performance of the propulsion system as applied to all three MCC maneuvers. The final highlights the slight, but notable, contribution of the attitude thrusters during each MCC maneuver. Given the possible variations in these three scenarios, the trajectory design methods are determined to be robust to errors in the modeling of the flight system. Keywords: James Webb Space Telescope, Task Parallelism, Monte Carlo, Mid-Course Correction, Libration Point Orbit 1. Introduction The James Webb Space Telescope (JWST) is the scientific successor of the Hubble Space Telescope and the Spitzer Space Telescope. -

Ansys SCADE Lifecycle®
EMBEDDED SOFTWARE Ansys SCADE LifeCycle® SCADE LifeCycle is part of the Ansys Embedded Software family of products and solutions that includes modules providing unique support for application lifecycle management. This product line features requirements traceability via Application Lifecycle Management (ALM) tools, traceability from models, configuration and change management, and automatic documentation generation. SCADE LifeCycle enhances the functionalities of Ansys SCADE® tools with add-on modules that bridge SCADE solutions and Requirement Management tools or PLM/ALM (Product Lifecycle Management/ Application Lifecycle Management) tools. With SCADE LifeCycle, all systems and software teams involved in critical applications development can manage and control their design and verification activities across the full life cycle of their SCADE applications. / Requirements Traceability SCADE LifeCycle Application Lifecycle Management (ALM) Gateway provides an integrated traceability analysis solution for safety-critical design processes with SCADE Architect, SCADE Suite, SCADE Display, SCADE Solutions for ARINC 661 and SCADE Test: • Connection to ALM tools: linkage to DOORS NG, DOORS (9.6 and up) Jama Connect, Siemens Polarion, Dassault Systèmes Reqtify 2016. • Graphical creation of traceability links between requirements or other structured documents and SCADE models. • Traceability of test cases from SCADE Test Environment projects. • Bidirectional navigation across requirements and tests. • Customizable Export of SCADE artifacts to DOORS or Jama Connect. • Compliant with DO-178B, DO-178C, EN 50128, IEC 61508, ISO 26262, and IEC 60880 standards. EMBEDDED SOFTWARE / SCADE LifeCycle® // 1 / Project Documentation Generation SCADE LifeCycle Reporter automates the time-consuming creation of detailed and complete reports from SCADE Suite, SCADE Display, SCADE Architect and SCADE UA Page Creator for ARINC 661 designs through: • Generation of reports in RTF or HTML formats. -
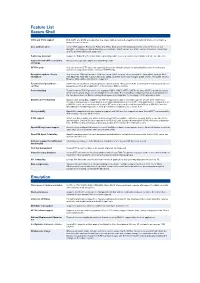
Feature List Secure Shell
Feature List Secure Shell SSH1 and SSH2 support Both SSH1 and SSH2 are supported in a single client, providing the maximum in flexibility when connecting to a range of remote servers. User authentication SecureCRT supports Password, Public Key (RSA, DSA, and X.509 including Smart Cards), Kerberos v5 (via GSSAPI), and Keyboard Interactive when connecting to SSH2 servers. For SSH1 servers, Password, Public Key, and TIS authentications are supported. Public Key Assistant Support for Public Key Assistant makes uploading public keys to an SSH2 server simple and safe for end users. Support for GSSAPI secured key Mechanisms supported depend on GSSAPI provider. exchange SFTP in a tab You can open an SFTP tab to the same SSH2 session without having to re-authenticate to perform file transfer operations using an interactive, text-based SFTP utility. Encryption ciphers: Strong The maximum 2048 bits length of DSA keys under SSH2 provides strong encryption. SecureCRT supports AES- encryption 128, AES-192, AES-256, Twofish, Blowfish, 3DES, and RC4 when connecting to SSH2 servers. For SSH1 servers, Blowfish, DES, 3DES, and RC4 are supported. Password and passphrase SSH2 session passwords and passphrases can be cached, letting SecureCRT and SecureFX share passwords and caching passphrases while either application or the Activator utility is running. Port forwarding Tunnel common TCP/IP protocols (for example, POP3, IMAP4, HTTP, SMTP) via SecureCRT to a remote Secure Shell server using a single, secure, multiplexed connection. Port forwarding configuration has been integrated into the tree-based Session Options dialog allowing easier configuration for securing TCP/IP application data. Dynamic port forwarding Dynamic port forwarding simplifies how TCP/IP application data is routed through the Secure Shell connection. -

Secure Configuration and Management of Linux Systems
Secure Configuration and Management of Linux Systems using a Network Service Orchestrator Vijay Satti A Thesis in The Department of Concordia Institute for Information Systems Engineering Presented in Partial Fulfillment of the Requirements for the Degree of Master of Applied Science at Concordia University Montréal, Québec, Canada May 2019 c Vijay Satti, 2019 CONCORDIA UNIVERSITY School of Graduate Studies This is to certify that the thesis prepared By: Vijay Satti Entitled: Secure Configuration and Management of Linux Systems using a Network Service Orchestrator and submitted in partial fulfillment of the requirements for the degree of Master of Applied Science complies with the regulations of this University and meets the accepted standards with respect to originality and quality. Signed by the Final Examining Committee: Chair Dr. Walter Lucia Examiner Dr. Anjali Agarwal Examiner Dr. Amr Youssef Supervisor Dr. J. William Atwood Approved by Dr. Chadi Assi, Graduate Program Director Department of Concordia Institute for Information Systems Engineering 2019 Dr. Amir Asif, Dean Faculty of Engineering and Computer Science Abstract Secure Configuration and Management of Linux Systems using a Network Service Orchestrator Vijay Satti Manual management of the configuration of network devices and computing devices (hosts) is an error-prone task. Centralized automation of these tasks can lower the costs of management, but can also introduce unknown or unanticipated security risks. Miscon- figuration (deliberate (by outsiders) or inadvertent (by insiders)) can expose a system to significant risks. Centralized network management has seen significant progress in recent years, result- ing in model-driven approaches that are clearly superior to previous "craft" methods. Host management has seen less development. -

List of TCP and UDP Port Numbers from Wikipedia, the Free Encyclopedia
List of TCP and UDP port numbers From Wikipedia, the free encyclopedia This is a list of Internet socket port numbers used by protocols of the transport layer of the Internet Protocol Suite for the establishment of host-to-host connectivity. Originally, port numbers were used by the Network Control Program (NCP) in the ARPANET for which two ports were required for half- duplex transmission. Later, the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP) needed only one port for full- duplex, bidirectional traffic. The even-numbered ports were not used, and this resulted in some even numbers in the well-known port number /etc/services, a service name range being unassigned. The Stream Control Transmission Protocol database file on Unix-like operating (SCTP) and the Datagram Congestion Control Protocol (DCCP) also systems.[1][2][3][4] use port numbers. They usually use port numbers that match the services of the corresponding TCP or UDP implementation, if they exist. The Internet Assigned Numbers Authority (IANA) is responsible for maintaining the official assignments of port numbers for specific uses.[5] However, many unofficial uses of both well-known and registered port numbers occur in practice. Contents 1 Table legend 2 Well-known ports 3 Registered ports 4 Dynamic, private or ephemeral ports 5 See also 6 References 7 External links Table legend Official: Port is registered with IANA for the application.[5] Unofficial: Port is not registered with IANA for the application. Multiple use: Multiple applications are known to use this port. Well-known ports The port numbers in the range from 0 to 1023 are the well-known ports or system ports.[6] They are used by system processes that provide widely used types of network services. -

Les Outils Qui Nous Veulent Du Bien Plus De Temps Pour Développer En Labview
Les outils qui nous veulent du bien Plus de temps pour développer en LabVIEW Rhône-Alpes LUG : Rencontre développeurs 04/07/2013 Luc DESRUELLE – Certifié LabVIEW Architect - MESULOG www.mesulog.fr La société MESULOG en bref Activité : Développement logiciel test et mesure Compétences : LabVIEW (Windows, RT, DSC, PDA, FPGA), TestStand Localisation : Grenoble (Moirans, 38) Partenaire National Instruments (2001) Développeurs certifiés LabVIEW et TestStand www.mesulog.fr (exemples de réalisation) Juillet 2013 Les logiciels qui vous veulent du bien 2 La société MESULOG en bref Ils nous ont fait confiance : AREVA T&D ALSTOM Grid ATMEL BEAMIND CEA (Commissariat à l'Énergie Atomique) CETIAT (Centre Technique des Industries Aérauliques et Thermiques) CNES (Centre National d'Études Spatiales) CNRS (Centre National de la Recherche Scientifique) EDF HONEYWELL Security LNE (Laboratoire National d'Essais) NIST (National Institute of Standards and Technology) NMIJ (National Metrology Institute of Japan) PECHINEY RADIALL STMicroelectronics THALES VALEO ... Juillet 2013 Les logiciels qui vous veulent du bien 3 Le présentateur CLA FORUMS Chef Projet Luc DESRUELLE Juillet 2013 Les logiciels qui vous veulent du bien 4 Le constat Le constat Juillet 2013 Les logiciels qui vous veulent du bien 5 Le constat Départ gestion projet Gestion projet : VITE Faire vite Juste avec ou bien? Coder BIEN BIEN vite ou bien un bloc notes Gestion Projet : Spécifications VITE Réalisation Tâches et Gestion code source Livrer Tests du code code Livrables -

Aas 98-306 a Modernized Approach to Meet Diversified Earth Observing System (Eos) Am-1 Mission Requirements
AAS 98-306 A MODERNIZED APPROACH TO MEET DIVERSIFIED EARTH OBSERVING SYSTEM (EOS) AM-1 MISSION REQUIREMENTS Lauri Kraft Newman NASA GSFC, Code 572 L Mark E. Hametz, Darrei J. Conway AI Solutions, Inc. From a flight dynamics perspective, the EOS AM-1 mission design and maneuver operations present a number of interesting challenges. The mission design itself is relatively complex for a low Earth mission, requiring a frozen, Sun-synchronous, polar orbit with a repeating ground track. Beyond the need to design an orbit that meets these requirements, the recent focus on low-cost, "lights out" operations has encouraged a shift to more automated ground support. Hight dynamics activities previously performed in special facilities created solely for that purpose and staffed by personnel with years of design experience are now being shifted to the mission operations centers (MOCs) staffed by flight operations team (FOT) operators. These operators' responsibilities include flight dynamics as a small subset of their work; therefore, FOT personnel often do not have the experience to make critical maneuver design decisions. Thus, streamlining the analysis and planning work required for such a complicated orbit design and preparing FOT personnel to take on the routine operation of such a spacecraft both necessitated increasing the automation level of the flight dynamics functionality. The FreeFlyer TM software developed by AI Solutions provides a means to achieve both of these goals. The graphic interface enables users to interactively perform analyses that previously required many parametric studies and much data reduction to achieve the same result. In addition, the fuzzy logic engine enables the simultaneous evaluation of multiple conflicting constraints, removing the analyst from the loop and allowing the FOT to perform more of the operations without much background in orbit design. -

Tunneling with Secure Shell (SSH) Secure Shell Tunneling with Secure Shell
White Paper Tunneling with Secure Shell (SSH) 4848 tramway ridge dr. ne suite 101 albuquerque, nm 87111 505 - 332 -5700 www.vandyke.com Tunneling with Secure Shell Remote access to network resources is increasingly a business requirement, but external network threats must be neutralized. A Secure Shell (SSH) capability called port forwarding allows nonsecure TCP/IP data to be tunneled across public and private networks through a secure, encrypted connection. The benefits of port forwarding are illustrated by a series of concrete examples. VanDyke Software's clients and servers provide an end-to-end tunneling solution to secure client/server applications, which may serve as a lightweight alternative to a Virtual Private Network (VPN). With today’s increasingly mobile and distributed workforce, providing remote access to travelers and teleworkers is no longer a “nice to have” option. In many corporations, remote access to business applications has become mission critical. At the same time, Internet access is now cheap, fast, and readily available. Leveraging the Internet to extend the local area network (LAN), provide real-time communications, and immediate file transfer and sharing is a scalable, cost-effective soluti on for corporate network remote access. However, Internet-based remote access also adds significant risk. Sensitive data can be intercepted, modified, or replayed anywhere between remote workers and the corporate firewall. Broadcast access technologies like cable and wireless are especially vulnerable. Whenever a computer is connected to the Internet, it becomes a potential target for intruders. "Always on" broadband greatly increases this exposure by giving intruders a fixed target to attack repeatedly over time.