Web and Mail Filter White Paper
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

ERNW Newsletter 31 / June 2010 Secure Configuration of Microsoft
ERNW Newsletter 31 / June 2010 Dear Partners, dear Colleagues, Welcome to the 31th edition of the ERNW Newsletter with the title: Secure Configuration of Microsoft Internet Explorer, Version 8 Version 1.0, 11th of June 2010 By: Enno Rey ([email protected]) Christopher Werny ([email protected]) Oliver Röschke ([email protected]) Abstract This newsletter evaluates configuration options, reflecting security and possible usability impact, incorporating typical large scale enterprise usage of browser based content. The evaluation was done for a globally operating enterprise. Note We provide some supporting files, namely: some regfiles containing the settings we recommended for the given environment. Use at your own risk and only if you fully understand the impact! an XLS with the recommended settings, based on the Microsoft XLS doc on GPO settings. miscellaneous stuff, e.g. an XLS with some documentation on potentially needed CLSIDs. A ZIP file with these can be found at http://www.ernw.de/download/ernw_nl_31_ie8config_supporting_docs.zip Disclaimer: the recommended settings are deployed in a sufficiently large global network. So they "work in production". Still, your mileage might vary. Please use the stuff cautiously. Any use is at your own risk. Definition – Umsetzung – Kontrolle 1 1 INTRODUCTION ............................................................................................. 5 1.1 Project Goals ............................................................................................................ 5 1.2 Technical goals ........................................................................................................ -

Automated Malware Analysis Report for Authorizationform.Vbs
ID: 42946 Sample Name: AuthorizationForm.vbs Cookbook: default.jbs Time: 20:25:46 Date: 17/01/2018 Version: 20.0.0 Table of Contents Table of Contents 2 Analysis Report 4 Overview 4 General Information 4 Detection 4 Confidence 4 Classification 5 Analysis Advice 5 Signature Overview 6 AV Detection: 6 Networking: 6 Boot Survival: 6 Stealing of Sensitive Information: 6 Persistence and Installation Behavior: 6 Spreading: 6 System Summary: 6 HIPS / PFW / Operating System Protection Evasion: 7 Anti Debugging: 7 Malware Analysis System Evasion: 7 Hooking and other Techniques for Hiding and Protection: 7 Lowering of HIPS / PFW / Operating System Security Settings: 7 Language, Device and Operating System Detection: 7 Behavior Graph 7 Simulations 8 Behavior and APIs 8 Antivirus Detection 8 Initial Sample 8 Dropped Files 8 Domains 9 Yara Overview 9 Initial Sample 9 PCAP (Network Traffic) 9 Dropped Files 9 Memory Dumps 9 Unpacked PEs 9 Joe Sandbox View / Context 9 IPs 9 Domains 9 ASN 9 Dropped Files 9 Screenshot 9 Startup 10 Created / dropped Files 10 Contacted Domains/Contacted IPs 12 Contacted Domains 12 Contacted IPs 12 Static File Info 12 General 12 File Icon 13 Network Behavior 13 Snort IDS Alerts 13 Network Port Distribution 13 TCP Packets 14 Copyright Joe Security LLC 2018 Page 2 of 30 UDP Packets 15 DNS Queries 16 DNS Answers 16 HTTP Request Dependency Graph 16 HTTP Packets 16 Code Manipulations 19 Statistics 19 Behavior 19 System Behavior 20 Analysis Process: wscript.exe PID: 3100 Parent PID: 2852 20 General 20 File Activities 20 File Created -

J I Truste Ne Ork
Internet Security A Jumpstart for Systems Administrators and IT Managers Tim Speed Juanita Ellis Digital Press An imprint of Elsevier Science Amsterdam, Boston • London • New York o Oxford • Paris • San Diego San Francisco • Singapore • Sydney • Tokyo Digital Press is an imprint of Elsevier Science. Copyright © 2003, Elsevier Science (USA). All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written permission of the publisher. Recognizing the importance of preserving what has been written, Elsevier Science prints its books on acid-free paper whenever possible. Library of Congress Cataloging-in-Publication Data ISBN 1-55558-298-2 British Library Cataloguing-in-Publication Data A catalogue record for this book is available from the British Library. The publisher offers special discounts on bulk orders of this book. For information, please contact: Manager of Special Sales Elsevier Science 200 Wheeler Road Burlington, MA 01803 Tel: 781-313-4700 Fax: 781-313-4882 For information on all Digital Press publications available, contact our World Wide Web home page at: http://www.digitalpress.com or http://www.bh.com/digitalpress 1098765432 1 Printed in the United States of America To Linda Speed~my split apart. -T.S. To my dad, Charles Ellis. -J.E. This Page Intentionally Left Blank Contents Foreword ix Acknowledgments xi Introduction xiii The Internet and Security I. I The -

Desktop Troubleshooting and Configuration Guide
Desktop Troubleshooting and Configuration Guide Product and Versions Contract Version 6.8.1 Document Dated August, 2011, Updated November, 2013 Overview of Known Issues Prodagio Contract is a browser based application. This Guide details the known issues and troubleshooting recommendations, as well as the desktop hardware and software requirements to optimize Prodagio Contact 6.8.1 performance. This document is intended for use by those IT members responsible for desktop management and third-party software configuration. Troubleshooting issues are grouped as follows: UCF and Java related issues Java only issues Browser issues Drag and Drop issues Add-On issues Workflow Instances issues An Appendix details recommended browser hardware, software and operating environments and provides more details about the role of UCF and how it can be pre-installed. The Table of Contents on the next page lists more details of this Guide’s various sections. Note: the screen captures used in this document are from Internet Explorer 9 and Windows 7. The appearance of your screen captures many differ if using other browsers and browser versions and operating system versions. If at all possible, troubleshooting issues in the order presented in this document. Desktop Troubleshooting and Configuration Guide — Prodagio Contract Page 1 Table of Contents Overview of Known Issues ........................................................................................................................ 1 UCF and Java Issues Defined ................................................................................................................. -
Download New Version Internet Explorer 4.01 Free "You Need Windows Internet Explorer 4.01 Or Later" Error Message When Attempting to Open Outlook 2013
download new version internet explorer 4.01 free "You need Windows Internet Explorer 4.01 or later" error message when attempting to open Outlook 2013. I am using Windows 7 and Internet Explorer 10, but when I attempt to open Outlook 2013, an error message always pops up which says: You need Windows Internet Explorer 4.01 or later to use this feature. You can download the latest version of Internet Explorer from http://www.microsoft.com. I have attempted to find corrections for this problem for months, and cannot find anything that works. Microsoft Internet Explorer 4.0 (4.00.1812) for Windows 3.1. You have used 0 of your current 25 downloads. This count will reset daily. Having trouble with downloads? You may want to check what the site and mirrors report if they aren't working when reporting an issue. (Kansas City, US) (Quebec, CA) This file is also available over IPFS. IPFS is a decentralised distributed file store, and thus downloads do not count towards your daily download limit. Warning: IPFS support is currently experimental and your download might not work. How to Move IE Temporary Internet Files Folder to Default Location. Tim Fisher has 30+ years' professional technology experience. He focuses on support and Microsoft topics but is an expert in all areas of tech. He's also the VP and General Manager of Lifewire. Facebook Twitter LinkedIn. Tweet Share Email. Chrome Safari Firefox Microsoft. By default, the Temporary Internet Files folder in Internet Explorer is buried deep within several folders. As the name would suggest, the IE browser uses this folder to store temporary internet files. -

Sitecore CMS 7.0-7.5 Browser Configuration Reference Rev: 2014-12-11
Sitecore CMS 7.0-7.5 Browser Configuration Reference Rev: 2014-12-11 Sitecore CMS 7.0-7.5 Browser Configuration Reference Optimizing Internet Explorer and other web browsers to work with Sitecore Sitecore® is a registered trademark. All other brand and product names are the property of their respective holders. The contents of this document are the property of Sitecore. Copyright © 2001-2014 Sitecore. All rights reserved. Sitecore CMS 7.0-7.5 Browser Configuration Reference Table of Contents Chapter 1 Introduction ................................................................................................................................ 3 1.1 Supported Web Browsers ............................................................................................................. 4 Chapter 2 Configuring Microsoft Internet Explorer..................................................................................... 5 2.1 How to Determine the Internet Explorer Version .......................................................................... 6 2.2 Internet Explorer Configuration Summary ..................................................................................... 7 2.3 Required Configuration ................................................................................................................. 9 2.3.1 Trusted Sites Zone .................................................................................................................... 9 2.3.2 Pop-up Blocker ....................................................................................................................... -

Automated Malware Analysis Report For
ID: 71345 Cookbook: browseurl.jbs Time: 11:22:46 Date: 07/08/2018 Version: 23.0.0 Table of Contents Table of Contents 2 Analysis Report 4 Overview 4 General Information 4 Detection 4 Confidence 4 Classification 5 Signature Overview 5 AV Detection: 6 Bitcoin Miner: 6 Software Vulnerabilities: 6 Networking: 6 System Summary: 6 Hooking and other Techniques for Hiding and Protection: 6 Malware Analysis System Evasion: 6 Anti Debugging: 7 Language, Device and Operating System Detection: 7 Behavior Graph 7 Simulations 7 Behavior and APIs 7 Antivirus Detection 7 Initial Sample 7 Dropped Files 8 Unpacked PE Files 8 Domains 8 URLs 8 Yara Overview 8 Initial Sample 8 PCAP (Network Traffic) 8 Dropped Files 8 Memory Dumps 8 Unpacked PEs 8 Joe Sandbox View / Context 8 IPs 8 Domains 8 ASN 8 Dropped Files 9 Screenshots 9 Startup 9 Created / dropped Files 9 Contacted Domains/Contacted IPs 11 Contacted Domains 11 Contacted URLs 12 Contacted IPs 12 Public 12 Static File Info 12 No static file info 12 Network Behavior 12 Network Port Distribution 12 TCP Packets 13 UDP Packets 13 DNS Queries 13 Copyright Joe Security LLC 2018 Page 2 of 16 DNS Answers 13 HTTP Request Dependency Graph 13 HTTP Packets 13 Code Manipulations 14 Statistics 14 Behavior 14 System Behavior 14 Analysis Process: iexplore.exe PID: 2056 Parent PID: 548 14 General 15 File Activities 15 Registry Activities 15 Analysis Process: iexplore.exe PID: 1900 Parent PID: 2056 15 General 15 File Activities 15 Registry Activities 16 Analysis Process: wscript.exe PID: 3104 Parent PID: 2056 16 General -

Checking Settings
S2P Browser Setup and System Requirements Note: If your operating system is Windows NT 4.0, 2000, XP, Vista, or Windows 7, you must be logged into Windows as the local administrator before making any of the changes below. Configuration involves three processes: checking for correct settings, installing required components, and verifying settings using the Browser Analyzer. CHECKING SETTINGS Supported Browsers Internet Explorer Version 6.0 and higher (Windows PC Only) Firefox Version 2.0 and higher (Windows PC or Mac) Safari Version 4.0 and higher (Mac only) Google Chrome Version 4.0 and higher (Windows PC or Mac) Some test types require specific browsers: Simulation tests that use the SHL simulation player require Windows-based Internet Explorer. These include MS Office simulation tests, the Basic Computer Literacy test, and many Call Center Scenario tests. Tests with audio work with all supported browsers and require Flash 8.0 or higher. Non-simulation tests work with all supported browsers. Call Center simulation tests that require Flash work with all supported browsers. Not Supported: Netscape, the AOL browser, and net appliances. However, those with AOL may use it to connect to the Internet. When connected, minimize AOL and open Internet Explorer and navigate to http://www.Select2Perform.com. Screen Resolution Recommended: 1024x768 or higher If the resolution is set to 800x600, the user will need to scroll on most screens and a low screen resolution message will appear. Some tests may not function correctly at an 800x600 resolution. To change your resolution, click Start , Settings , Control Panel , Display , and then Settings . -

The User Friendly Guide to INTERNET & COMPUTER TERMS
The User Friendly Guide to INTERNET & COMPUTER TERMS Charles Steed Gold Standard Press Inc. Reno, Nevada Copyright ã 2001 Charles Steed and Gold Standard Press Inc. Permission is granted to ALL USERS and readers to download, print and freely dis- tribute The User Friendly Guide To Internet & Computer Terms. No changes to this text is authorized. THIS TEXT MAY NOT BE SOLD EXCEPT BY AUTHORIZED AGENTS OR REPRESENTATIVES OF GOLD STANDARD PRESS INC. For information, contact Gold Standard Press Inc. 1475 Terminal Way, Suite E, Reno, Nevada 89502, tel. 360-482-2510. This book contains information gathered from many sources. It is published for gen- eral reference and not as a substitute for independent verification by users when circumstances warrant. It is sold with the understanding that neither the author nor publisher is engaged in rendering legal, psychological, accounting or professional advice. The publisher and author disclaim any personal liability, either directly or indirectly, for advice presented within. Although the author and publisher have used care and diligence in the preparation, and made every effort to ensure the accuracy and completeness of information contained in this book, we assume no responsibility for errors, inaccuracies, omissions, or any inconsistency herein. Any slights of people, places, publishers, books, or organizations are unintentional. The online version of this text has been slightly modified to faciliate easy download- ing. No significant differences from the printed version are present. Library of Congress -

インターネットマガジン1999年6月号―INTERNET Magazine No.53
最新最強のブラウザーとうたわれるインタ ーネットエクスプローラ5 をインストールして みて、「なあんだこれだ け? IE 4と変わら ないじゃん」とがっかりした人は多いのでは ないだろうか。これまで雑誌やウェブで紹介 集中企画 された新機能を見ても、今いちピンとこな いと思ってはいないだろうか。それもその はず、IE 5の便利さはちょっとやそっとで 本誌 は見つけられない。隠れた機能を探し出し、 チュー ン ア ップするのがIE 5活用のポイント だ。インストールしたそのままの状態で使い 続けるだけではもったいない。IE 5の実力 を限界まで引き出してみよう。それには本誌 だけでしか読めないとっておきのチューン ア 公開! ップ術 が 役 に立つだろう。 独占 塩田紳二+編集部 インターネットエクスプローラ5 ューンアップ! 192 INTERNET magazine 1999/6 インターネットマガジン/株式会社インプレスR&D ©1994-2007 Impress R&D INTERNET EXPLORER 5 tune UP! IE 5の本当の 「スゴさ」はここにある。 IE 5では、もっぱら移動ボタンやオートコンプリート機能ばかりが大きく取り上げら れているようだ。確かにユーザーがすばやく効率的にウェブにアクセスできる新機能 は重要だ。しかし、IE 5 で注目すべき点はそれだけだろうか。 かつて大きく宣伝されたチャンネルがIE 5 ではずされたことを考えてみよう。IE 4 では、ユーザーが黙っていてもコンテンツ が自動的にやってくるプッシュ機能に期待が集まった。しかしプッシュは結局流行しなかった。IE 5 はユーザーに積極性を 求めるようになった。自分なりの使いこなし方を見つければそれだけ便利さが増すのがIE 5 の本当の「すごさ」だ。 カスタマイズが柔軟にできる! INTERNET EXPLORER 5 tune UP! ツールバーのボタンが変更できるようになったことに代表されるように、 SP.194 IE 5ではユーザーインターフェイスを自在にカスタマイズできる。イン 1. ストールしたらまず画面の構成を自分好みに変えてみよう。カスタマ 2. SP.196 イズできるのはインターフェイスだけではない。インストールするコン 7. SP.206 ポーネントは細かく選べるようになったし、アドインソフトも豊富に用 意されている。アウトルックエクスプレス5 の振り分け機能は大幅に向 8 . SP.208 上した。ユーザーが上手に設定すればそれだけIE 5 を便利なブラウザ ーに育てることができる。 ウェブ上 のサービスと連 携 できる! INTERNET EXPLORER 5 tune UP! IE 5の目玉機能の1つがウェブを見ながらニュースや音楽を聴けるラジ オバーだ。しかし実際にはラジオバーの本当の機能は「ラジオステー 3 . SP.198 ションガイド」にあると言っていい。またアドレスバーやエクスプロー ラバーを使った検索機能もエキサイトやライコスといった検索サイト 4. SP.200 と結び付いたものだ。関連サイト機能はアレクサ社の技術を使ってい るし、エクスプローラバーにウェブサイトの情報を埋め込むアドインソ フトもある。IE 5ではこれまで以上にウェブ上の各種のサービスと連携 する機能が強化されている。 オフィスでもモバイルで も 使 える! INTERNET EXPLORER 5 tune UP! ブラウザーを漠然とウェブを見て回るために使うだけではつまらない。 役立つ情報を効率よく保管し、整理して再利用するためのツールがIE 5 . SP.202 -

Inline HTML Editor Does Not Load Preventing Typing in Text Field
Inline HTML Editor does not load preventing typing in text field Date Published: Oct 04,2013 Category: Product:ANGEL; Version:ANGEL_8_0 Article No.: 000034456 Product: ANGEL Issue Description: The Inline HTML Editor is loaded in text fields in many areas of the application including composing course mail, posting to discussion forums, and grading drop box submissions. If the HTML Editor does not load, the user is unable to type in the text field. This article outlines measures to get the HTML editor to load. Cause: This behavior of the HTML editor not loading is mostly likely to be encountered shortly after installing new ANGEL service packs. The problem arises when a service pack updates javascript files, but an end user's browser continues to use old, cached versions of the javascript files rather than requesting the new, updated versions of the javascript files from the ANGEL web server. Resolution/Workaround: In most cases, the situation can be resolved by having the end user clear their browser cache. For some Internet Explorer users additional steps may be required. Detailed steps for each supported browser are outlined below. Internet Explorer Reminder: Internet Explorer 10 in Metro Mode is not supported. 1. Select "Delete Browsing History" from the Tools menu. 2. Un-select the check box for "Preserve Favorites website data". 3. Select the check boxes for Temporary Internet files, Cookies, and History. 4. Click Delete. For some Internet Explorer users the above steps may not be sufficient to resolve the issue. If the Inline HTML Editor still does not load, continue with the following steps. -
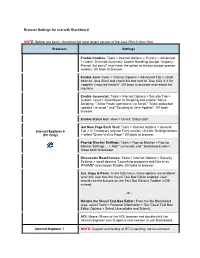
Browser Settings for Use with Blackboard
Browser Settings for use with Blackboard NOTE: Before you begin, download the most recent version of the Java Plug-in from Sun Browsers Settings Enable Cookies: Tools > Internet Options > Privacy > Advanced > Check "Override Automatic Cookie Handling (accept 1st party; Prompt 3rd party)" and check the option to always accept session cookies. OK back to browser. Enable Java: Tools > Internet Options > Advanced Tab > scroll down to Java (Sun) and check the box next to “Use XXX X.X for <applet> (required restart)". OK back to browser and restart the machine. Enable Javascript: Tools > Internet Options > Security Tab > Custom Level > Scroll down to Scripting and enable "Active Scripting," "Allow Paste Operations via Script," "Allow status bar updates via script," and "Scripting of Java Applets". OK back browser. Enable Status bar: View > Check "Status Bar". Get New Page Each Visit: Tools > Internet Options > General Internet Explorer 6 Tab > in Temporary Internet Files section, click the Settings button (PC Only) > select "Every Visit to Page." OK back to browser. Pop-up Blocker Settings: Tools > Pop-up Blocker > Pop-up Blocker Settings ... > Add *.ucmo.edu and *.blackboard.com > Close back to browser. Discussion Board Issues: Tools > Internet Options > Security Settings > scroll down to “Launching programs and files in an IFRAME” and choose Enable. OK back to browser. Cut, Copy & Paste: In the Edit menu, these options are disabled when the user has the Visual Text Box Editor enabled. User should use the buttons on the Text Box Editor’s Toolbar in BB instead. - or - Disable the Visual Text Box Editor: From the My Blackboard area, select Tools > Personal Information > Set Visual Text Box Editor Options > Select Unavailable and Submit.