Debugger Basics - Training
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Hacker's Handbook for Ringzer0 Training, by Steve Lord
Hacker’s Handbook For Ringzer0 Training, by Steve Lord This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License. Copyright ©2021 Raw Hex Ltd. All Rights Reserved. Retro Zer0 is a trademark of Ring Zer0 Training. Raw Hex is a trademark of Raw Hex Ltd. All other trademarks are the property of their respective owners. Raw Hex Ltd reserve the right to make changes or improvements to equipment, software and documentation herein described at any time and without notice. Notice: Please be advised that your Retro Zer0 has no warranty, and that tampering with the internal hardware and software of your Ring Zer0 is widely encouraged as long as you do so with appropriate regard to safety. Contents 1 Preface 5 1.1 Safety ........................... 6 1.2 Understanding This Document ............ 6 2 Before You Start 7 2.1 Check You Have Everything .............. 7 2.2 Back Up The SD Card ................. 8 2.3 Connecting Up Your Retro Zer0 ............ 8 2.4 Powering Up ....................... 10 2.5 Resetting Your Retro Zer0 . 10 2.6 Powering Down ..................... 10 3 First Steps 11 3 4 CONTENTS 3.1 Testing The Keyboard . 11 3.2 Using CP/M ....................... 12 3.3 Would You Like To Play A Game? . 14 3.4 MultiCPM Extras ..................... 17 3.5 Useful Tools ....................... 19 3.6 What’s On The Card? . 20 3.7 Putting It All Together . 23 3.8 Where To Read More . 25 4 Being Productive With Retro Zer0 27 4.1 WordStar .........................27 4.2 Supercalc .........................30 4.3 DBase ...........................32 4.4 Microsoft BASIC .....................32 4.5 Turbo Pascal .......................34 4.6 Forth 83 .........................36 4.7 ZDE ............................38 4.8 Z80 Assembler .....................39 4.9 Hi-Tech C .........................43 4.10 XLisp ...........................46 CONTENTS 5 4.11 Installing New Software . -

E2 Studio Integrated Development Environment User's Manual: Getting
User’s Manual e2 studio Integrated Development Environment User’s Manual: Getting Started Guide Target Device RX, RL78, RH850 and RZ Family Rev.4.00 May 2016 www.renesas.com Notice 1. Descriptions of circuits, software and other related information in this document are provided only to illustrate the operation of semiconductor products and application examples. You are fully responsible for the incorporation of these circuits, software, and information in the design of your equipment. Renesas Electronics assumes no responsibility for any losses incurred by you or third parties arising from the use of these circuits, software, or information. 2. Renesas Electronics has used reasonable care in preparing the information included in this document, but Renesas Electronics does not warrant that such information is error free. Renesas Electronics assumes no liability whatsoever for any damages incurred by you resulting from errors in or omissions from the information included herein. 3. Renesas Electronics does not assume any liability for infringement of patents, copyrights, or other intellectual property rights of third parties by or arising from the use of Renesas Electronics products or technical information described in this document. No license, express, implied or otherwise, is granted hereby under any patents, copyrights or other intellectual property rights of Renesas Electronics or others. 4. You should not alter, modify, copy, or otherwise misappropriate any Renesas Electronics product, whether in whole or in part. Renesas Electronics assumes no responsibility for any losses incurred by you or third parties arising from such alteration, modification, copy or otherwise misappropriation of Renesas Electronics product. 5. Renesas Electronics products are classified according to the following two quality grades: “Standard” and “High Quality”. -

Tutorial for VCS
Tutorial for VCS STEP 1: login to the Linux system on Linuxlab server. Start a terminal (the shell prompt). Click here to open a shell window Fig. 1 The screen when you login to the Linuxlab through equeue STEP 2: In the terminal, execute the following command: module add ese461 You could perform “module avail” in the terminal to find the available modules on Linuxlab. Make sure ese461 is presented when you execute this command. 1.Find the available modules 2.Make sure ese461 is presented 3.This command will set up the work environment for class ESE461 Fig. 2 Build work environment for class ESE461 using module 1 STEP 3: Getting started with Verilog • Creating a new folder (better if you have all the files for a project in a specific folder). • Enter into this new folder and start writing your Verilog script in a new file (.v file). Example code for modeling an counter is here • In addition to model code, Test Bench script has to be given in order to verify the functionality of your model (.v file). Example code of test bench for counter is here. Use gedit to edit the .v files (gedit is a commonly used GUI editor on Linux ) Fig. 3 Open gedit through teminal STEP 4: Compiling and simulating your code • In the terminal, change the directory to where your model and test bench files (Counter.v and Counter_tb.v) are present by using this command: cd <path> For example: cd ~/ESE461/VcsTutorial/ (Remark: ‘~’ means home directory on Linux) • Compile the files by typing in the terminal: vcs <file>.v <file_tb>.v In the above example, it should be: vcs Counter.v Counter_tb.v There should be no error presented in the terminal. -

SAS® Debugging 101 Kirk Paul Lafler, Software Intelligence Corporation, Spring Valley, California
PharmaSUG 2017 - Paper TT03 SAS® Debugging 101 Kirk Paul Lafler, Software Intelligence Corporation, Spring Valley, California Abstract SAS® users are almost always surprised to discover their programs contain bugs. In fact, when asked users will emphatically stand by their programs and logic by saying they are bug free. But, the vast number of experiences along with the realities of writing code says otherwise. Bugs in software can appear anywhere; whether accidentally built into the software by developers, or introduced by programmers when writing code. No matter where the origins of bugs occur, the one thing that all SAS users know is that debugging SAS program errors and warnings can be a daunting, and humbling, task. This presentation explores the world of SAS bugs, providing essential information about the types of bugs, how bugs are created, the symptoms of bugs, and how to locate bugs. Attendees learn how to apply effective techniques to better understand, identify, and repair bugs and enable program code to work as intended. Introduction From the very beginning of computing history, program code, or the instructions used to tell a computer how and when to do something, has been plagued with errors, or bugs. Even if your own program code is determined to be error-free, there is a high probability that the operating system and/or software being used, such as the SAS software, have embedded program errors in them. As a result, program code should be written to assume the unexpected and, as much as possible, be able to handle unforeseen events using acceptable strategies and programming methodologies. -

Agile Playbook V2.1—What’S New?
AGILE P L AY B O OK TABLE OF CONTENTS INTRODUCTION ..........................................................................................................4 Who should use this playbook? ................................................................................6 How should you use this playbook? .........................................................................6 Agile Playbook v2.1—What’s new? ...........................................................................6 How and where can you contribute to this playbook?.............................................7 MEET YOUR GUIDES ...................................................................................................8 AN AGILE DELIVERY MODEL ....................................................................................10 GETTING STARTED.....................................................................................................12 THE PLAYS ...................................................................................................................14 Delivery ......................................................................................................................15 Play: Start with Scrum ...........................................................................................15 Play: Seeing success but need more fexibility? Move on to Scrumban ............17 Play: If you are ready to kick of the training wheels, try Kanban .......................18 Value ......................................................................................................................19 -

Opportunities and Open Problems for Static and Dynamic Program Analysis Mark Harman∗, Peter O’Hearn∗ ∗Facebook London and University College London, UK
1 From Start-ups to Scale-ups: Opportunities and Open Problems for Static and Dynamic Program Analysis Mark Harman∗, Peter O’Hearn∗ ∗Facebook London and University College London, UK Abstract—This paper1 describes some of the challenges and research questions that target the most productive intersection opportunities when deploying static and dynamic analysis at we have yet witnessed: that between exciting, intellectually scale, drawing on the authors’ experience with the Infer and challenging science, and real-world deployment impact. Sapienz Technologies at Facebook, each of which started life as a research-led start-up that was subsequently deployed at scale, Many industrialists have perhaps tended to regard it unlikely impacting billions of people worldwide. that much academic work will prove relevant to their most The paper identifies open problems that have yet to receive pressing industrial concerns. On the other hand, it is not significant attention from the scientific community, yet which uncommon for academic and scientific researchers to believe have potential for profound real world impact, formulating these that most of the problems faced by industrialists are either as research questions that, we believe, are ripe for exploration and that would make excellent topics for research projects. boring, tedious or scientifically uninteresting. This sociological phenomenon has led to a great deal of miscommunication between the academic and industrial sectors. I. INTRODUCTION We hope that we can make a small contribution by focusing on the intersection of challenging and interesting scientific How do we transition research on static and dynamic problems with pressing industrial deployment needs. Our aim analysis techniques from the testing and verification research is to move the debate beyond relatively unhelpful observations communities to industrial practice? Many have asked this we have typically encountered in, for example, conference question, and others related to it. -

JAMS 7.X User Guide
User Guide JAMS Scheduler 7.3 Copyright Terms and Conditions Copyright Help/Systems LLC and its group of companies. The content in this document is protected by the Copyright Laws of the United States of America and other countries worldwide. The unauthorized use and/or duplication of this material without express and written permission from HelpSystems is strictly prohibited. Excerpts and links may be used, provided that full and clear credit is given to HelpSystems with appropriate and specific direction to the original content. HelpSystems and its trademarks are properties of the HelpSystems group of companies. All other marks are property of their respective owners. 202108110755 JAMS 7.X User Guide Table of Contents JAMS 7.X Client Features 3 Jobs In JAMS 4 Working with Jobs 5-19 Scheduling Recurring Jobs 20-22 Execution Methods 23-27 Submitting Jobs Manually 28-29 Sequence Jobs 30-34 Managing Sequence Parameters 35-38 Sequence Tasks 39-47 Workflow Jobs 48-51 Workflow Activities 52-59 Migrating JAMS Objects 60-61 File Transfer Features 62-67 Variables 68 Working with Variables 69-71 Elements 72 Documentation Elements 73-74 EventHandler Elements 75-79 Prerequisite Elements 80-83 Result Elements 84-86 Trigger Elements 87-92 Folders 93 Working with Folders 94-104 Dates and Times 105 Date Properties 106-107 Creating Special Date Definitions 108-111 Specifying Dates Using Natural Language 112-114 Named Times in JAMS 115-118 Dashboards and Reports 119 Custom Dashboards 120-129 Creating New Report Templates and Customizing Existing Reports -
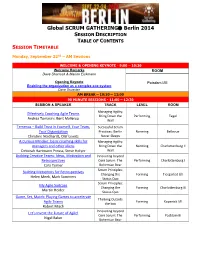
Global SCRUM GATHERING® Berlin 2014
Global SCRUM GATHERING Berlin 2014 SESSION DESCRIPTION TABLE OF CONTENTS SESSION TIMETABLE Monday, September 22nd – AM Sessions WELCOME & OPENING KEYNOTE - 9:00 – 10:30 Welcome Remarks ROOM Dave Sharrock & Marion Eickmann Opening Keynote Potsdam I/III Enabling the organization as a complex eco-system Dave Snowden AM BREAK – 10:30 – 11:00 90 MINUTE SESSIONS - 11:00 – 12:30 SESSION & SPEAKER TRACK LEVEL ROOM Managing Agility: Effectively Coaching Agile Teams Bring Down the Performing Tegel Andrea Tomasini, Bent Myllerup Wall Temenos – Build Trust in Yourself, Your Team, Successful Scrum Your Organization Practices: Berlin Norming Bellevue Christine Neidhardt, Olaf Lewitz Never Sleeps A Curious Mindset: basic coaching skills for Managing Agility: managers and other aliens Bring Down the Norming Charlottenburg II Deborah Hartmann Preuss, Steve Holyer Wall Building Creative Teams: Ideas, Motivation and Innovating beyond Retrospectives Core Scrum: The Performing Charlottenburg I Cara Turner Bohemian Bear Scrum Principles: Building Metaphors for Retrospectives Changing the Forming Tiergarted I/II Helen Meek, Mark Summers Status Quo Scrum Principles: My Agile Suitcase Changing the Forming Charlottenburg III Martin Heider Status Quo Game, Set, Match: Playing Games to accelerate Thinking Outside Agile Teams Forming Kopenick I/II the box Robert Misch Innovating beyond Let's Invent the Future of Agile! Core Scrum: The Performing Postdam III Nigel Baker Bohemian Bear Monday, September 22nd – PM Sessions LUNCH – 12:30 – 13:30 90 MINUTE SESSIONS - 13:30 -

Toolkit Feature Interactive Debug Facility User's Guide
High Level Assembler for z/OS & z/VM & z/VSE IBM Toolkit Feature Interactive Debug Facility User's Guide Version 1 Release 6 GC26-8709-09 High Level Assembler for z/OS & z/VM & z/VSE IBM Toolkit Feature Interactive Debug Facility User's Guide Version 1 Release 6 GC26-8709-09 Note Before using this information and the product it supports, be sure to read the general information under “Notices” on page 311. This edition applies to IBM High Level Assembler for z/OS & z/VM & z/VSE Toolkit Feature, Release 6, Program Number 5696-234 and to any subsequent releases until otherwise indicated in new editions. Make sure that you are using the correct edition for the level of the product. Order publications through your IBM representative or the IBM branch office serving your locality. IBM welcomes your comments. For information on how to send comments, see “How to send your comments to IBM” on page xv. © Copyright IBM Corporation 1992, 2017. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Figures ............... ix Building a module on z/OS ........ 17 Building a module on CMS ........ 17 About this book ........... xi Building a phase on z/VSE ........ 17 Running ASMLANGX ........... 18 Syntax notation ............. xi Extraction file allocation on z/OS ...... 18 Online language extraction on TSO ..... 19 How to send your comments to IBM .. xv Batch language extraction on z/OS ..... 19 If you have a technical problem ....... xv Online language extraction on CMS ..... 20 Batch language extraction on z/VSE .... -

Enabling Devops on Premise Or Cloud with Jenkins
Enabling DevOps on Premise or Cloud with Jenkins Sam Rostam [email protected] Cloud & Enterprise Integration Consultant/Trainer Certified SOA & Cloud Architect Certified Big Data Professional MSc @SFU & PhD Studies – Partial @UBC Topics The Context - Digital Transformation An Agile IT Framework What DevOps bring to Teams? - Disrupting Software Development - Improved Quality, shorten cycles - highly responsive for the business needs What is CI /CD ? Simple Scenario with Jenkins Advanced Jenkins : Plug-ins , APIs & Pipelines Toolchain concept Q/A Digital Transformation – Modernization As stated by a As established enterprises in all industries begin to evolve themselves into the successful Digital Organizations of the future they need to begin with the realization that the road to becoming a Digital Business goes through their IT functions. However, many of these incumbents are saddled with IT that has organizational structures, management models, operational processes, workforces and systems that were built to solve “turn of the century” problems of the past. Many analysts and industry experts have recognized the need for a new model to manage IT in their Businesses and have proposed approaches to understand and manage a hybrid IT environment that includes slower legacy applications and infrastructure in combination with today’s rapidly evolving Digital-first, mobile- first and analytics-enabled applications. http://www.ntti3.com/wp-content/uploads/Agile-IT-v1.3.pdf Digital Transformation requires building an ecosystem • Digital transformation is a strategic approach to IT that treats IT infrastructure and data as a potential product for customers. • Digital transformation requires shifting perspectives and by looking at new ways to use data and data sources and looking at new ways to engage with customers. -

Integrating the GNU Debugger with Cycle Accurate Models a Case Study Using a Verilator Systemc Model of the Openrisc 1000
Integrating the GNU Debugger with Cycle Accurate Models A Case Study using a Verilator SystemC Model of the OpenRISC 1000 Jeremy Bennett Embecosm Application Note 7. Issue 1 Published March 2009 Legal Notice This work is licensed under the Creative Commons Attribution 2.0 UK: England & Wales License. To view a copy of this license, visit http://creativecommons.org/licenses/by/2.0/uk/ or send a letter to Creative Commons, 171 Second Street, Suite 300, San Francisco, California, 94105, USA. This license means you are free: • to copy, distribute, display, and perform the work • to make derivative works under the following conditions: • Attribution. You must give the original author, Jeremy Bennett of Embecosm (www.embecosm.com), credit; • For any reuse or distribution, you must make clear to others the license terms of this work; • Any of these conditions can be waived if you get permission from the copyright holder, Embecosm; and • Nothing in this license impairs or restricts the author's moral rights. The software for the SystemC cycle accurate model written by Embecosm and used in this document is licensed under the GNU General Public License (GNU General Public License). For detailed licensing information see the file COPYING in the source code. Embecosm is the business name of Embecosm Limited, a private limited company registered in England and Wales. Registration number 6577021. ii Copyright © 2009 Embecosm Limited Table of Contents 1. Introduction ................................................................................................................ 1 1.1. Why Use Cycle Accurate Modeling .................................................................... 1 1.2. Target Audience ................................................................................................ 1 1.3. Open Source ..................................................................................................... 2 1.4. Further Sources of Information ......................................................................... 2 1.4.1. -

IBM Tivoli Directory Server – Oracle Enterprise Gateway Integration Guide
Oracle Enterprise Gateway An Oracle White Paper June 2011 IBM Tivoli Directory Server – Oracle Enterprise Gateway Integration Guide 1 / 28 Oracle Enterprise Gateway Disclaimer The following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into any contract. It is not a commitment to deliver any material, code, or functionality, and should not be relied upon in making purchasing decisions. The development, release, and timing of any features or functionality described for Oracle’s products remains at the sole discretion of Oracle. 2 / 28 Oracle Enterprise Gateway 1. Introduction ....................................................................................... 4 1.1. Purpose ...................................................................................... 4 1.2. LDAP Architecture ..................................................................... 5 1.3. Setup Used for this Guide: ......................................................... 5 2. Directory Details ................................................................................ 5 2.1. Directory Structure ..................................................................... 5 2.2. Connection Details ..................................................................... 5 3. Authenticate User with HTTP Basic HTTP Filter .............................. 6 3.1. Create a policy to authenticate a user in the LDAP directory .... 6 3.2. Create a new relative path for the Policy ..................................