Release Notes for Debian 10 (Buster), 64-Bit PC
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Oldschool E-Mail Setup Eine Freakshow
Oldschool E-mail Setup Eine Freakshow [email protected] Chemnitzer Linuxtage, 2016 (Screenshot GMX vor >15 Jahren: Waybackmachine zu www.gmx.net) (Screenshot GMX heute) (Screenshot Gmail heute) Lösungen? ● Claws ● Mutt ● Eudora ● Netscape Navigator ● Evolution ● Opera M2 ● GMX ● Outlook ● Gnus ● SquirrelMail ● Hotmail ● The Bat! ● Hushmail ● Thunderbird ● KMail ● … Flußgrafik Email Netz MTA MRA MDA MUA MSA MTA Netz Hipster! ● KISS ● YAGNI ● DRY ● NIH ● Divide And Conquer ● Everything is a file ● No vendor lock-in ● Mißtraue Autoritäten – fördere Dezentralisierung Netz Netz Emails Client, den ich Remote verwenden kann Leicht erweiterbar Emails lokal Filter Offenes Format Adressen Netz Netz Abholen Transportformat? Pull Subject 1 Email = 1 File Keine Spuren X-List-ID Mit Hierarchien am Server Beliebige Einfaches Suchen Header Verlässliches Suchen Verarbeitung mit Unix Tools Client, den ich Remote verwenden kann Leicht erweiterbar Emails lokal Filter Offenes Format Adressen Netz Netz Abholen Transportformat? Pull Subject 1 Email = 1 File Keine Spuren X-List-ID Mit Hierarchien am Server Beliebige Einfaches Suchen Header Verlässliches Suchen Verarbeitung mit Unix Tools mbox Maildir mh Client, den ich Remote verwenden kann Leicht erweiterbar Emails lokal Filter Offenes Format Adressen Netz Netz Abholen Transportformat? Pull Subject 1 Email = 1 File Keine Spuren X-List-ID Mit Hierarchien am Server Beliebige Einfaches Suchen Header Verlässliches Suchen Verarbeitung mit Unix Tools mbox Maildir mh tmp 1439306571.1269_0.elvis ~/Post/Technik/Wikitech new 1448267819.5940_0.spencer ... 1457079728.2000_0.spencer:2, cur 1456839383.9873_0.nepomuk:2,SR 1457166567.23654_0.spencer:2,S ... Client, den ich Remote verwenden kann Leicht erweiterbar Filter Adressen Netz Netz Abholen Pull Subject Maildir Keine Spuren X-List-ID am Server Beliebige Header Client, den ich Remote verwenden kann Leicht erweiterbar Filter Adressen Netz Netz Abholen Pull Subject Maildir Keine Spuren X-List-ID am Server Beliebige Header fetchmail getmail mpop .. -

Bustersimpson-Surveyor.Pdf
BUSTER SIMPSON // SURVEYOR BUSTER SIMPSON // SURVEYOR FRYE ART MUSEUM 2013 EDITED BY SCOTT LAWRIMORE 6 Foreword 8 Acknowledgments Carol Yinghua Lu 10 A Letter to Buster Simpson Charles Mudede 14 Buster Simpson and a Philosophy of Urban Consciousness Scott Lawrimore 20 The Sky's the Limit 30 Selected Projects 86 Selected Art Master Plans and Proposals Buster Simpson and Scott Lawrimore 88 Rearview Mirror: A Conversation 100 Buster Simpson // Surveyor: Installation Views 118 List of Works 122 Artist Biography 132 Maps and Legends FOREWORD WOODMAN 1974 Seattle 6 In a letter to Buster Simpson published in this volume, renowned Chinese curator and critic Carol Yinghua Lu asks to what extent his practice is dependent on the ideological and social infrastructure of the city and the society in which he works. Her question from afar ruminates on a lack of similar practice in her own country: Is it because China lacks utopian visions associated with the hippie ethos of mid-twentieth-century America? Is it because a utilitarian mentality pervades the social and political context in China? Lu’s meditations on the nature of Buster Simpson’s artistic practice go to the heart of our understanding of his work. Is it utopian? Simpson would suggest it is not: his experience at Woodstock “made me realize that working in a more urban context might be more interesting than this utopian, return-to-nature idea” (p. 91). To understand the nature of Buster Simpson’s practice, we need to accompany him to the underbelly of the city where he has lived and worked for forty years. -
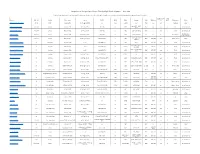
Comparison of 116 Open Spec, Hacker Friendly Single Board Computers -- June 2018
Comparison of 116 Open Spec, Hacker Friendly Single Board Computers -- June 2018 Click on the product names to get more product information. In most cases these links go to LinuxGizmos.com articles with detailed product descriptions plus market analysis. HDMI or DP- USB Product Price ($) Vendor Processor Cores 3D GPU MCU RAM Storage LAN Wireless out ports Expansion OSes 86Duino Zero / Zero Plus 39, 54 DMP Vortex86EX 1x x86 @ 300MHz no no2 128MB no3 Fast no4 no5 1 headers Linux Opt. 4GB eMMC; A20-OLinuXino-Lime2 53 or 65 Olimex Allwinner A20 2x A7 @ 1GHz Mali-400 no 1GB Fast no yes 3 other Linux, Android SATA A20-OLinuXino-Micro 65 or 77 Olimex Allwinner A20 2x A7 @ 1GHz Mali-400 no 1GB opt. 4GB NAND Fast no yes 3 other Linux, Android Debian Linux A33-OLinuXino 42 or 52 Olimex Allwinner A33 4x A7 @ 1.2GHz Mali-400 no 1GB opt. 4GB NAND no no no 1 dual 40-pin 3.4.39, Android 4.4 4GB (opt. 16GB A64-OLinuXino 47 to 88 Olimex Allwinner A64 4x A53 @ 1.2GHz Mali-400 MP2 no 1GB GbE WiFi, BT yes 1 40-pin custom Linux eMMC) Banana Pi BPI-M2 Berry 36 SinoVoip Allwinner V40 4x A7 Mali-400 MP2 no 1GB SATA GbE WiFi, BT yes 4 Pi 40 Linux, Android 8GB eMMC (opt. up Banana Pi BPI-M2 Magic 21 SinoVoip Allwinner A33 4x A7 Mali-400 MP2 no 512MB no Wifi, BT no 2 Pi 40 Linux, Android to 64GB) 8GB to 64GB eMMC; Banana Pi BPI-M2 Ultra 56 SinoVoip Allwinner R40 4x A7 Mali-400 MP2 no 2GB GbE WiFi, BT yes 4 Pi 40 Linux, Android SATA Banana Pi BPI-M2 Zero 21 SinoVoip Allwinner H2+ 4x A7 @ 1.2GHz Mali-400 MP2 no 512MB no no WiFi, BT yes 1 Pi 40 Linux, Android Banana -

Designing a User Interface for the Innovative E-Mail Client Semester Thesis
Designing a User Interface for the Innovative E-mail Client Semester Thesis Student: Alexandra Burns Supervising Professor: Prof. Bertrand Meyer Supervising Assistants: Stephanie Balzer, Joseph N. Ruskiewicz December 2005 - April 2006 1 Abstract Email Clients have become a crucial application, both in business and for per- sonal use. The term information overload refers to the time consuming issue of keeping up with large amounts of incoming and stored email. Users face this problem on a daily basis and therefore benefit from an email client that allows them to efficiently search, display and store their email. The goal of this thesis is to build a graphical user interface for the innovative email client developed in a previous master thesis. It also explores the possibilities of designing a user interface outside of the business rules that apply for commercial solutions. 1 Contents 1 Introduction 4 2 Existing Work 6 2.1 ReMail ................................. 6 2.1.1 Methods ............................ 6 2.1.2 Problems Identified ...................... 7 2.1.3 Proposed Solutions ...................... 7 2.1.4 Assessment .......................... 8 2.2 Inner Circle .............................. 8 2.2.1 Methods ............................ 8 2.2.2 Problems Identified ...................... 9 2.2.3 Proposed Solutions ...................... 9 2.2.4 Assessment .......................... 10 2.3 TaskMaster .............................. 10 2.3.1 Methods ............................ 10 2.3.2 Problems Identified ...................... 11 2.3.3 Proposed Solution ...................... 11 2.3.4 Assessment .......................... 12 2.4 Email Overload ............................ 12 2.4.1 Methods ............................ 12 2.4.2 Problems Identified ...................... 13 2.4.3 Proposed Solutions ...................... 13 2.4.4 Assessment .......................... 14 3 Existing Solutions 16 3.1 Existing Email Clients ....................... -

Mathematics Department's New Email Service
Mathematics Department’s New Email Service The department’s new email service employs the widely-used IMAP email protocol to allow you to read and organize your email. You may use the Math web-based email service, http://webmail.math.vt.edu, and/or email software on Unix systems, such as elm, mutt or pine. The IMAP protocol stores your email on a department server computer that daily saves your email and files to backup tapes. The server does not have an infinite supply of disk storage, so you will need to periodically delete email you no longer need or transfer it to your PC or Mac for archival.1 You may use the webmail service in conjunction with other email applications. Elm Elm is no longer supported. You may use mutt which is very similar. Pine Before running pine, you must update your existing pine settings with this command, /local/calvin/bin/updatepinerc PID where PID is your Virginia Tech PID. This will create a new .pinerc file in your home directory containing settings for using the new Math Email system. A copy of your original .pinerc file is named .pinerc-pre4.64 in your home directory. If you have previously used an older version of pine, any of your old settings that were not migrated to the new .pinerc will be listed. These are saved in a file named pinerc- settings. If you want to continue using any old settings, you must edit .pinerc to include them. Pine groups mailboxes into collections. One collection will be any mailboxes on the mail server. -

Postfix Catch All and Mutt
Postfix Catch All and Mutt End goal: having postfix saving all of the emails for a domain to a single “mailbox” in maildir format, and being able to send email using mutt (or similar). Specifics to my setup I'm not going to open port 25 on my server, I'm going through Net7's spam filter, which will then forward to my server on port 8025. So I need to open port 8025. The rule was already there for port 25, I just need to edit the thing. Make Postfix listen to another port There is always the plan of using iptables to redirect the traffic. You can do it in Postfix as well. Open master.cf and find this line: smtp inet n - - - - smtpd The smtp word up front is actually a port. You can replace it with this line: 8025 inet n - - - - smtpd If you restart Postfix and check with netstat it should be listening to another port. Setting up Maildir delivery By default Postfix will output emails to a single file in /var/mail/. I'd rather have the Maildir format which separates emails into different files that I can individually move and/or delete. I'm going off the rails here trying out things. Looks like we're going to need these configuration options in main.cf: home_mailbox = Maildir/ mailbox_command = Make sure mailbox_command isn't set somewhere else in the file. Reload Postfix. We should be able to test that this is working using a known user on the system. You can telnet-test like so: EHLO test MAIL FROM:<[email protected]> RCPT TO:<william> DATA Test. -

Building a Datacenter with ARM Devices
Building a Datacenter with ARM Devices Taylor Chien1 1SUNY Polytechnic Institute ABSTRACT METHODS THE CASE CURRENT RESULTS The ARM CPU is becoming more prevalent as devices are shrinking and Physical Custom Enclosure Operating Systems become embedded in everything from medical devices to toasters. Build a fully operational environment out of commodity ARM devices using Designed in QCAD and laser cut on hardboard by Ponoko Multiple issues exist with both Armbian and Raspbian, including four However, Linux for ARM is still in the very early stages of release, with SBCs, Development Boards, or other ARM-based systems Design was originally only for the Raspberry Pis, Orange Pi Ones, Udoo critical issues that would prevent them from being used in a datacenter many different issues, challenges, and shortcomings. Have dedicated hard drives and power system for mass storage, including Quads, PINE64, and Cubieboard 3 multiple drives for GlusterFS operation, and an Archive disk for backups and Issue OS In order to test what level of service commodity ARM devices have, I Each device sits on a tray which can be slid in and out at will rarely-used storage Kernel and uboot are not linked together after a Armbian decided to build a small data center with these devices. This included Cable management and cooling are on the back for easy access Build a case for all of these devices that will protect them from short circuits version update building services usually found in large businesses, such as LDAP, DNS, Designed to be solid and not collapse under its own weight and dust Operating system always performs DHCP request Raspbian Mail, and certain web applications such as Roundcube webmail, Have devices hooked up to a UPS for power safety Design Flaws Allwinner CPUs crash randomly when under high Armbian ownCloud storage, and Drupal content management. -

Webfaction User Guide
WebFaction User Guide WebFaction is a service of Paragon Internet Group Limited CONTENTS 1 Introduction 3 1.1 Services..................................................3 1.2 The Complete System..........................................4 2 The Control Panel 5 2.1 Log in to the Control Panel.......................................5 2.2 Change Your Control Panel Password..................................5 2.3 What to Do About a Lost Password...................................6 2.4 Two-Step Login.............................................6 3 Finding Details About Your Server9 3.1 Finding Your Server’s Name.......................................9 3.2 Finding Your Server’s Operating System................................9 3.3 Finding Your Server’s IP Address.................................... 10 4 Accessing Your Data 11 4.1 Connecting with SSH.......................................... 11 4.2 Connecting with FTP........................................... 14 4.3 Changing Your FTP or SSH Password.................................. 14 4.4 Additional Users............................................. 15 4.5 Backups................................................. 16 5 Accounts 17 5.1 Plans and Services............................................ 17 5.2 Communicating with WebFaction.................................... 18 5.3 Payments................................................. 19 5.4 Affiliate Program............................................. 23 5.5 Canceling Your Account......................................... 24 6 Domains 25 6.1 Getting -

Buster – Ein Gauner Mit Herz Phil Collins
HanseSound – Exklusiv Titel Buster – Ein Gauner mit Herz Phil Collins • Originaltitel: Buster • Produktionsjahr: 1988 • Produktionsland: Großbritannien • Darsteller: Phil Collins, Julie Walters, Larry Lamb • Regisseur: David Green • Format: Dolby Digital 5.1 (deutsch, englisch), PAL, Breitbild • Region: Region B/2 • Bildseitenformat: 1,66:1 • FSK: Freigegeben ab 12 Jahren • Bonus: englische Fassung mit 102,41 Min.(BD), Anwahl der Musikstücke. deutsche Untertitel MediaBook: DVD & Blu ray DVD: Blu ray: EAN: 4250124370893 EAN: EAN: Vö.: 18.09.2020 Vö.: Vö.: HAP: 14,85 HAP: HAP: Laufzeit:. 96,18+100,10 Laufzeit: 96,18 min. Laufzeit: 100,10 min. Das Wichtigste für den Kleinganoven Buster Edwards (Phil Collins) ist die Liebe seiner Frau June (Julie Walters, „Harry Potter“-Filmreihe). Als diese sich ein Haus wünscht, weiß Buster, dass er ein größeres Ding drehen muss. Mit einigen Kumpanen raubt er einen Postzug aus, doch der ausgetüftelte Plan für danach geht gründlich schief und Buster muss am Ende eine schwere Entscheidung treffen… Die Legende um den berühmtesten Postraub aller Zeiten aus völlig neuer Sicht, garniert mit Welthits aus der Feder von Megastar Phil Collins, der auch die Hauptrolle spielt! Es ist die Tragikomödie aus dem Jahr 1988. Die von Phil Collins gesungene Filmmusik wurde zu einem Erfolg in den Hitparaden. Der Film handelt von dem Postzugräuber Ronald Buster Edwards, von seiner Vorgeschichte, dem Raub und der Flucht nach Mexiko bis hin zur Entlassung aus dem Gefängnis. HanseSound – Exklusiv Titel Die Phil-Collins-Singles aus dem Film, A Groovy Kind of Love und Two Hearts, erreichten Platz 1 und Platz 6 in den UK Singles Charts. -

Like Real Computers - Making Distributions Work on Single Board Computers André Przywara 04/02/2018 Apritzel@Freenode
... like real computers - Making distributions work on single board computers André Przywara 04/02/2018 apritzel@Freenode 1 FOSDEM 2018 2 FOSDEM 2018 2 FOSDEM 2018 2 FOSDEM 2018 2 FOSDEM 2018 3 FOSDEM 2018 Agenda Booting Current firmware / boot situation Problems ... ... and how to solve them Linux kernel support New SoC in the kernel - why does it take so long? What can we do about it? Demo? 4 FOSDEM 2018 Glossary / scope Disclaimer: Not an Arm Ltd. story. SBC: single board computer with ARM core, "Fruit-Pis" Not servers! SoCs from Allwinner, Rockchip, Amlogic, Marvell, Realtek, ... DT: device tree, hardware description, for generic OS support Not ACPI! firmware: board-specific low-level software, including boot loader Mainline, not BSP. 5 FOSDEM 2018 Actual technical dependency: kernel support for SoC Current situation Board Ubuntu Debian SuSE Fedora Armbian Pine64 ? ? ! ! ! BananaPi M64 ? ? ! ! NanoPi A64 ? ? ! ! Rock64 ? ? ! Table: Board distribution support 6 FOSDEM 2018 Current situation Board Ubuntu Debian SuSE Fedora Armbian Pine64 ? ? ! ! ! BananaPi M64 ? ? ! ! NanoPi A64 ? ? ! ! Rock64 ? ? ! Table: Board distribution support Actual technical dependency: kernel support for SoC 6 FOSDEM 2018 What are the main problems? Traditionally no well recognised standard way of booting Many boards come without on-board storage - no firmware! Distribution has to ship board DT - explicit board support 7 FOSDEM 2018 How to find and boot the kernel Could be some U-Boot magic, but better: Using the UEFI standard! U-Boot implements (parts of) -

SPI Annual Report 2015
Software in the Public Interest, Inc. 2015 Annual Report July 12, 2016 To the membership, board and friends of Software in the Public Interest, Inc: As mandated by Article 8 of the SPI Bylaws, I respectfully submit this annual report on the activities of Software in the Public Interest, Inc. and extend my thanks to all of those who contributed to the mission of SPI in the past year. { Martin Michlmayr, SPI Secretary 1 Contents 1 President's Welcome3 2 Committee Reports4 2.1 Membership Committee.......................4 2.1.1 Statistics...........................4 3 Board Report5 3.1 Board Members............................5 3.2 Board Changes............................6 3.3 Elections................................6 4 Treasurer's Report7 4.1 Income Statement..........................7 4.2 Balance Sheet............................. 13 5 Member Project Reports 16 5.1 New Associated Projects....................... 16 5.2 Updates from Associated Projects................. 16 5.2.1 0 A.D.............................. 16 5.2.2 Chakra............................ 16 5.2.3 Debian............................. 17 5.2.4 Drizzle............................. 17 5.2.5 FFmpeg............................ 18 5.2.6 GNU TeXmacs........................ 18 5.2.7 Jenkins............................ 18 5.2.8 LibreOffice.......................... 18 5.2.9 OFTC............................. 19 5.2.10 PostgreSQL.......................... 19 5.2.11 Privoxy............................ 19 5.2.12 The Mana World....................... 19 A About SPI 21 2 Chapter 1 President's Welcome SPI continues to focus on our core services, quietly and competently supporting the activities of our associated projects. A huge thank-you to everyone, particularly our board and other key volun- teers, whose various contributions of time and attention over the last year made continued SPI operations possible! { Bdale Garbee, SPI President 3 Chapter 2 Committee Reports 2.1 Membership Committee 2.1.1 Statistics On January 1, 2015 we had 512 contributing and 501 non-contributing mem- bers. -

Proyecto Fin De Grado
ESCUELA TÉCNICA SUPERIOR DE INGENIERÍA Y SISTEMAS DE TELECOMUNICACIÓN PROYECTO FIN DE GRADO TÍTULO: Despliegue de Liota (Little IoT Agent) en Raspberry Pi AUTOR: Ricardo Amador Pérez TITULACIÓN: Ingeniería Telemática TUTOR (o Director en su caso): Antonio da Silva Fariña DEPARTAMENTO: Departamento de Ingeniería Telemática y Electrónica VºBº Miembros del Tribunal Calificador: PRESIDENTE: David Luengo García VOCAL: Antonio da Silva Fariña SECRETARIO: Ana Belén García Hernando Fecha de lectura: Calificación: El Secretario, Despliegue de Liota (Little IoT Agent) en Raspberry Pi Quizás de todas las líneas que he escrito para este proyecto, estas sean a la vez las más fáciles y las más difíciles de todas. Fáciles porque podría doblar la longitud de este proyecto solo agradeciendo a mis padres la infinita paciencia que han tenido conmigo, el apoyo que me han dado siempre, y el esfuerzo que han hecho para que estas líneas se hagan realidad. Por todo ello y mil cosas más, gracias. Mamá, papá, lo he conseguido. Fáciles porque sin mi tutor Antonio, este proyecto tampoco sería una realidad, no solo por su propia labor de tutor, si no porque literalmente sin su ayuda no se hubiera entregado a tiempo y funcionando. Después de esto Antonio, voy a tener que dejarme ganar algún combate en kenpo como agradecimiento. Fáciles porque, sí melones os toca a vosotros, Alex, Alfonso, Manu, Sama, habéis sido mi apoyo más grande en los momentos más difíciles y oscuros, y mis mejores compañeros en los momentos de felicidad. Amigos de Kulturales, los hermanos Baños por empujarme a mejorar, Pablo por ser un ejemplo a seguir, Chou, por ser de los mejores profesores y amigos que he tenido jamás.