Basics of Telecommunication– Sec1321
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Local Network Competition
Chapter 15 LOCAL NETWORK COMPETITION Glenn A Woroch* University of California, Berkeley Contents 1. Introduction 1.1.Scope and objectives 1.2.Patterns and themes 2. Local Network Competition in Historical Perspective 2.1.Local competition in one city, a century apart 2.2.U.S. experience with local competition and monopoly 2.3.The experience abroad 3. Economic Conditions of Local Network Competition 3.1.Defining local services and markets 3.2.Demand for local network services 3.3.Cost of local service and technical change 4. The Structure and Regulation of the Local Network Industry 4.1.Structure of the U.S. local exchange industry 4.2.Regulation of local network competition 5. Strategic Modelling of Local Network Competition 5.1.Causes and consequences of local network competition 5.2.Strategic choices of local network entrants 5.3.Strategic models of local network competition 5.4.Entry barriers 6. Empirical Evidence on Local Network Competition 7. Wireless Local Competition 7.1.Wireless communications technologies 7.2.Wireless services as wireline competitors 7.3.Structure of the wireless industry 7.4.An assessment of the wireless threat 8. The Future of Local Competition References * I have received helpful comments on earlier drafts from Mark Armstrong, Bob Crandall, David Gabel and Lester Taylor. Ellen Burton of the FCC and Amy Friedlander of CNRI supplied useful empirical and historical information. I am especially grateful to Ingo Vogelsang for his encouragement, guidance, and inexhaustible patience throughout this project. I. INTRODUCTION 1.1. Scope and Objectives of this Chapter This chapter surveys the economic analysis of competition in markets for local telecommunications services.1 Its main objective is to understand patterns of competition in these markets and evaluate its benefits and costs against the alternative forms of industrial organisation. -

Central Telecom Long Distance, Inc
Central Telecom Long Distance, Inc. 102 South Tejon Street, 11th Floor Colorado Springs, CO 80903. Telecommunications Service Guide For Interstate and International Services May 2016 This Service Guide contains the descriptions, regulations, and rates applicable to furnishing of domestic Interstate and International Long Distance Telecommunications Services provided by Central Telecom Long Distance, Inc. (“Central Telecom Long Distance” or “Company”). This Service Guide and is available to Customers and the public in accordance with the Federal Communications Commission’s (FCC) Public Availability of Information Concerning Interexchange Services rules, 47 CFR Section 42.10. Additional information is available by contacting Central Telecom Long Distance, Inc.’s Customer Service Department toll free at 888.988.9818, or in writing directed to Customer Service, 102 South Tejon Street, 11th Floor, Colorado Springs, CO 80903. 1 INTRODUCTION This Service Guide contains the rates, terms, and conditions applicable to the provision of domestic Interstate and International Long Distance Services. This Service Guide is prepared in accordance with the Federal Communications Commission’s Public Availability of Information Concerning Interexchange Services rules, 47 C.F.R. Section 42.10 and Service Agreement and may be changed and/or discontinued by the Company. This Service Guide governs the relationship between Central Telecom Long Distance, Inc. and its Interstate and International Long Distance Service Customers, pursuant to applicable federal regulation, federal and state law, and any client-specific arrangements. In the event one or more of the provisions contained in this Service Guide shall, for any reason be held to be invalid, illegal, or unenforceable in any respect, such invalidity, illegality or unenforceability shall not affect any other provision hereof, and this Service Guide shall be construed as if such invalid, illegal or unenforceable provision had never been contained herein. -

A Data Communications Glossary of Terms
DOCUMENT RESUME ED 108 612 IR 002 1 -27 AUTHOR Teplitzky, Frank TITLE A'Data Communications Glossary of Terms. INSTITUTION Southwest Regional Laboratory for Educational Research, and Development, Los Alamitos, Calif. REPORT NO SWRL-TN-5-72-09 PUB DATE' 28 Feb 72 NOTE 18p. -EDRS TRICE MF-$0.76 HC-$1.5e PLUS ,POSTAGE DESCRIPTORS Computer Science; Data Processing; *Glossaries; *Media Technology; Programing Languages; *Reference Materials; Research Tools; *Telecommunication ' ABSTRACT General and specialized terms developed in data communications in recent years are listed al abetically and defined. The list is said to be more representative thaexhaustive and is ' intended for use as a reference source. Approximately 140 terms are included. (Author/SK) Gjr ,r ************************************************************A******** Doduments acquired byERIC inclUde =many informal unpublis4e& * * materials not available from other sources. ERIC makes every effort * *.to obtain the best copy c.vpilable. nevertheless, items of marginal * * reproducibility are often enCountered and this,affects the quality * * of the microfiche =and hardcopy reproductionsERIC makes available 4` * =via= the, ERIC Document Re -prod_ uc =tion= Service,(EDRS). EDRS= is not * responsible for the quality of the original document. Reproductions * * supplied =by EDRS are the best that can be made -from= =the original. * ********************************************************************** C I. SOUTHWEST REGIONAL LABORATORY TECHNICAL NOTE DATE: Febr-uary 28, 1972 NO: TN -

Carrier Locator: Interstate Service Providers
Carrier Locator: Interstate Service Providers November 1997 Jim Lande Katie Rangos Industry Analysis Division Common Carrier Bureau Federal Communications Commission Washington, DC 20554 This report is available for reference in the Common Carrier Bureau's Public Reference Room, 2000 M Street, N.W. Washington DC, Room 575. Copies may be purchased by calling International Transcription Service, Inc. at (202) 857-3800. The report can also be downloaded [file name LOCAT-97.ZIP] from the FCC-State Link internet site at http://www.fcc.gov/ccb/stats on the World Wide Web. The report can also be downloaded from the FCC-State Link computer bulletin board system at (202) 418-0241. Carrier Locator: Interstate Service Providers Contents Introduction 1 Table 1: Number of Carriers Filing 1997 TRS Fund Worksheets 7 by Type of Carrier and Type of Revenue Table 2: Telecommunications Common Carriers: 9 Carriers that filed a 1997 TRS Fund Worksheet or a September 1997 Universal Service Worksheet, with address and customer contact number Table 3: Telecommunications Common Carriers: 65 Listing of carriers sorted by carrier type, showing types of revenue reported for 1996 Competitive Access Providers (CAPs) and 65 Competitive Local Exchange Carriers (CLECs) Cellular and Personal Communications Services (PCS) 68 Carriers Interexchange Carriers (IXCs) 83 Local Exchange Carriers (LECs) 86 Paging and Other Mobile Service Carriers 111 Operator Service Providers (OSPs) 118 Other Toll Service Providers 119 Pay Telephone Providers 120 Pre-paid Calling Card Providers 129 Toll Resellers 130 Table 4: Carriers that are not expected to file in the 137 future using the same TRS ID because of merger, reorganization, name change, or leaving the business Table 5: Carriers that filed a 1995 or 1996 TRS Fund worksheet 141 and that are unaccounted for in 1997 i Introduction This report lists 3,832 companies that provided interstate telecommunications service as of June 30, 1997. -

Telecommunications Infrastructure for Electronic Delivery 3
Telecommunications Infrastructure for Electronic Delivery 3 SUMMARY The telecommunications infrastructure is vitally important to electronic delivery of Federal services because most of these services must, at some point, traverse the infrastructure. This infrastructure includes, among other components, the Federal Government’s long-distance telecommunications program (known as FTS2000 and operated under contract with commercial vendors), and computer networks such as the Internet. The tele- communications infrastructure can facilitate or inhibit many op- portunities in electronic service delivery. The role of the telecommunications infrastructure in electronic service delivery has not been defined, however. OTA identified four areas that warrant attention in clarifying the role of telecommunications. First, Congress and the administration could review and update the mission of FTS2000 and its follow-on contract in the context of electronic service delivery. The overall perform- ance of FTS2000 shows significant improvement over the pre- vious system, at least for basic telephone service. FTS2000 warrants continual review and monitoring, however, to assure that it is the best program to manage Federal telecommunications into the next century when electronic delivery of Federal services likely will be commonplace. Further studies and experiments are needed to properly evaluate the benefits and costs of FTS2000 follow-on options from the perspective of different sized agencies (small to large), diverse Federal programs and recipients, and the government as a whole. Planning for the follow-on contract to FTS2000 could consider new or revised contracting arrangements that were not feasible when FTS2000 was conceived. An “overlapping vendor” ap- proach to contracting, as one example, may provide a “win-win” 57 58 I Making Government Work situation for all parties and eliminate future de- national infrastructure will be much stronger if bates about mandatory use and service upgrades. -

Introductory Concepts
www.getmyuni.com INTRODUCTORY CONCEPTS 1.1 WHAT IS TELECOMMUNICATION? Many people call telecommunication the world’s must lucrative industry. In the United States, 110 million households have telephones and 50% of total households in the U.S. have Internet access and there are some 170 million mobile subscribers. Long-distance service annual revenues as of 2004 exceeded 100 × 109 dollars.1 Prior to divestiture (1983), the Bell System was the largest commercial company in the United States. It had the biggest fleet of vehicles, the most employees, and the greatest income. Every retiree with any sense held the safe and dependable Bell stock. Bell System could not be found on the “Fortune 500” listing of the largest companies. In 1982, Western Electric Co., the Bell System manufacturing arm, was number seven on the “Fortune 500.” However, if one checked the “Fortune 100 Utilities,” the Bell System was up on the top. Transferring this information to the “Fortune 500” put Bell System as the leader on the list. We know it is big business; but what is telecommunications? Webster’s (Ref. 1) calls it communications at a distance.TheIEEE Standard Dictionary (Ref. 2) defines telecom- munications as the transmission of signals over long distance, such as by telegraph, radio, or television. Another term we often hear is electrical communication. This is a descriptive term, but of somewhat broader scope. Some take the view that telecommunication deals only with voice telephony, and the typical provider of this service is the local telephone company. We hold a wider interpretation. Telecommunication encompasses the electrical communication at a distance of voice, data, and image information (e.g., TV and facsimile). -

Telecommunications; Amending 17 O.S
STATE OF OKLAHOMA 2nd Session of the 48th Legislature (2002) HOUSE BILL HB2796 By: Braddock and Case AS INTRODUCED An Act relating to telecommunications; amending 17 O.S. 2001, Section 139.102, which relates to the Oklahoma Telecommunications Act of 1997; adding definition; prohibiting the Corporation Commission from imposing any regulation on a high speed Internet access service or broadband service provider; allowing regulation in certain circumstances; allowing continuation of certain interconnection agreements; requiring certain provider to make agreements available to other providers; allowing the Corporation Commission to enforce certain interconnect agreements; prohibiting the Commission from expanding certain regulation; providing for codification; providing an effective date; and declaring an emergency. BE IT ENACTED BY THE PEOPLE OF THE STATE OF OKLAHOMA: SECTION 1. AMENDATORY 17 O.S. 2001, Section 139.102, is amended to read as follows: Section 139.102 As used in the Oklahoma Telecommunications Act of 1997: 1. "Access line" means the facility provided and maintained by a telecommunications service provider which permits access to or from the public switched network; 2. "Commission" means the Corporation Commission of this state; 3. "Competitive local exchange carrier" or "CLEC" means, with respect to an area or exchange, a telecommunications service provider that is certificated by the Commission to provide local exchange services in that area or exchange within the state after July 1, 1995; Req. No. 7936 Page 1 4. "Competitively neutral" means not advantaging or favoring one person over another; 5. "End User Common Line Charge" means the flat-rate monthly interstate access charge required by the Federal Communications Commission that contributes to the cost of local service; 6. -

Atlantic Broadband Enterprise, LLC – Pennsylvania Competitive Local Exchange Carrier Tariff
Atlantic Broadband Enterprise, LLC Telephone PA P.U.C. Tariff No. 1 Title Page COMPETITIVE LOCAL EXCHANGE CARRIER TITLE PAGE ATLANTIC BROADBAND ENTERPRISE, LLC COMPETITIVE LOCAL EXCHANGE CARRIER Regulations and Schedule of Charges For business Customers Only Within the Service Territories of Armstrong Telephone Company - North, Armstrong Telephone Company - PA, Citizens Telecommunications of New York, Inc., Citizens Telephone Company of Kecksburg, Consolidated Communications of Pennsylvania Company, Deposit Telephone Company, Frontier Communications - Commonwealth Telephone Company, Frontier Communications - Lakewood, Inc., Frontier Communications - Oswayo River, Inc., Frontier Communications of Breezewood, Inc., Frontier Communications of Canton, Inc., Frontier Communications of Pennsylvania, Inc., Hancock Telephone Company, Hickory Telephone Company, Ironton Telephone Company, Lackawaxen Telephone Company, Laurel Highland Telephone Company, Mahanoy & Mahantango Telephone Company, Marianna and Scenery Hill Telephone Company, North Penn Telephone Company, Palmerton Telephone Company, Pennsylvania Telephone Company, Pymatuning Independent Telephone Company, South Canaan Telephone Company, Sugar Valley Telephone Company, The Bentleyville Telephone Company, North-Eastern PA Telephone Company, United Telephone Company of PA d/b/a CenturyLink, Venus Telephone Corporation, Verizon-North, LLC, Verizon-Pennslvania, LLC, Westside Telecommunications, Windstream Buffalo Valley, Windstream Conestoga, Inc., Windstream D&E, Inc., Windstream Pennsylvania, Yukon Waltz Telephone Company. The Company will mirror the exchange area boundaries as stated in the tariffs of Armstrong Telephone Company - North P.U.C. No. 2; Armstrong Telephone Company - PA PA PUC No. 10; Citizens Telecommunications of New York, Inc. P.U.C. No. 2; Citizens Telephone Company of Kecksburg P.U.C. No. 3; Consolidated Communications of Pennsylvania Company P.U.C. No. 11; Deposit Telephone Company PA PUC No. 1; Frontier Communications - Commonwealth Telephone Company PA PUC No. -

Tariff Schedules Applicable to Local Exchange Services Within the State of California
Enhanced Communications Network, Inc. Cal. P.U.C. Schedule No. 1-T d/b/a Asian American Association First Revised Cal. P.U.C. Title Sheet 1031 S. Glendora Avenue Cancels Original Title Sheet West Covina, CA 91790 COMPETITIVE LOCAL CARRIER TARIFF SCHEDULES APPLICABLE TO LOCAL EXCHANGE SERVICES WITHIN THE STATE OF CALIFORNIA OF ENHANCED COMMUNICATIONS NETWORK, INC. d/b/a ASIAN AMERICAN ASSOCIATION U-6658-C Advice Letter No. 10 Issued By: Date Filed: January 19, 2007 Decision No.: 03-02-051 Thomas Haluskey, Effective Date: January 26, 2007 Resolution No. Director of Regulatory Affairs Enhanced Communications Network, Inc. Cal. P.U.C. Schedule No. 1-T d/b/a Asian American Association Fourth Revised Cal. P.U.C. Sheet 1 1031 S. Glendora Avenue Cancels Third Revised Sheet 1 West Covina, CA 91790 COMPETITIVE LOCAL CARRIER CHECK SHEET Current sheets of this tariff are as follows: Page Revision Page Revision Page Revision Title First Revised 41 First Revised 83 First Revised 1 Fourth Revised* 42 First Revised 84 First Revised 2 Fifth Revised* 43 First Revised 85 First Revised 3 Original 44 First Revised 86 First Revised 4 First Revised 45 First Revised 87 First Revised 5 Second Revised 46 First Revised 88 First Revised 6 Second Revised 47 First Revised 89 First Revised 7 Original 48 First Revised 90 First Revised 8 Original 49 First Revised 91 First Revised 9 Original 50 First Revised 92 First Revised SECTION 1 51 First Revised 93 Second Revised 10 First Revised 52 First Revised SECTION 2 11 First Revised 53 First Revised 94 Second Revised 12 First -

The Information Act the Numbering Crisis in World Zone 1
The Information Act Brian Hayes Annan, Octopus, 1990 The Numbering Crisis in World Zone 1 i carcity is no stranger in this land of I ten-digit numbers are possible telephone or a ladder without rungs—I couldn't .plenty. From time to time it seems I numbers. Indeed, more than 90 percent fathom the use of it. Then my grand • we are running out of fuel, out of wa of them are unacceptable for one reason mother demonstrated. She picked up the ter, out of housing, out of wilderness, out or another. A telephone number is not receiver and said, "Jenny, get me Mrs. of ozone, out of places to put the rubbish, just an arbitrary sequence of digits, like Wilson, please. Thank you, dear." out of all the stuff we need to make more the serial number on a ticket stub; it has My grandmother's telephone was al rubbish. But who could have guessed, as a surprising amount of structure in it. As a ready quite an anachronism when I first the millennium trundles on to its close, matter of fact, the set of all valid North saw it in the 1950s. Automatic switching that we would be running out of num American telephone numbers constitutes gear—allowing the customer to make a bers? That was one resource everyone a formal language, analogous to a com connection without the help of an opera thought was infinite. puter programming language. When you tor—had been placed in service as early as The numbers in short supply are tele dial a telephone, you are programming 1892. -

Direct Distance Dialing
Chapter 8 Direct Distance Dialing Direct distance dialing of calls nationwide by customers required a major investment in development by the Bell System. Automatic alternate rout ing was incorporated into a multilevel hierarchy of switching centers, and a routing plan was developed to allow efficient choice of routes to a toll office in the region of the called telephone. No. 4 crossbar was adapted in several versions to take on the added functions of accepting more dialed digits from customers and of performing more code conversions or translations. The card translator solved the problem of handling the large amounts of infor mation required to service calls nationwide, and the crossbar tandem sys tem, despite its 2-wire design, was modified extensively for toll service and gave a good account of itself, with 213 toll systems in place by 1968. Crossbar tandem was, in addition, the first host system for centralized automatic message accounting, another important ingredient in making DDD available to all customers, regardless of the type of local office serving them. Selected No. 5 crossbar systems were modified, beginning in 1967, to inaugurate customer-dialing of calls overseas. I. NATIONWIDE PLANNING Initially, much of the equipment used by operators to complete toll calls was of the step-by-step variety, since this system was most suitable for the smaller-size trunk groups and was available, having been developed before World War II (see Chapter 3, section VI). Later, when there was a greater concentration of toll facilities, the No. 4 crossbar was available and was indeed adapted for the larger cities with five post-war installations in New York, Chicago, Boston, Cleveland, and Oakland (see Chapter 4, section III and Chapter 6, section 3.1). -
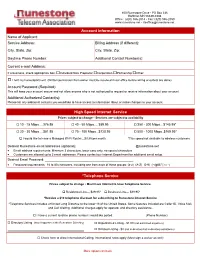
Account Information High Speed Internet Service *Telephone
100 Runestone Drive • PO Box 336 Hoffman MN 56339-0336 Office: (320) 986-2013 • Fax: (320) 986-2050 www.runestone.net • [email protected] Account Information Name of Applicant: Service Address: Billing Address (if different): City, State, Zip: City, State, Zip: Daytime Phone Number: Additional Contact Number(s): Current e-mail Address: If a business, check appropriate box: Individual/Sole Proprietor Corporation Partnership Other:_________________ I rent my home/apartment (Written permission from owner must be received in our office before wiring or outlets are done) Account Password (Required): This will keep your account secure and not allow anyone who is not authorized to request or receive information about your account Additional Authorized Contact(s): Please list any additional contacts you would like to have access to information about or make changes to your account High Speed Internet Service Prices subject to change • Services are subject to availability 10 - 15 Mbps….$76.95 40 - 50 Mbps.... $89.95 250 - 300 Mbps…$145.95* 20 - 30 Mbps….$81.95 75 - 100 Mbps...$120.95 500 - 1000 Mbps..$169.95* I would like to lease a Managed Wi-Fi Router…$3.95 per month *This speed not available to wireless customers Desired Runestone email addresses (optional): _______________________________ @runestone.net Email address requirements: Minimum 3 characters, lower case only, no special characters Customers are allowed up to 5 email addresses. Please contact our Internet Department for additional email setup. Desired Email Password: ______________________________________________________ Password requirements: 16 to 80 characters, including one from each of these groups: (a-z) (A-Z) (0-9) (~@#$*( ) = -) *Telephone Service Prices subject to change • Must have Internet to have Telephone Service.