Sun Enterprise Symon 2.0 User's Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Sun Fire E2900 Server
Sun FireTM E2900 Server Just the Facts February 2005 SunWin token 401325 Sun Confidential – Internal Use Only Just The Facts Sun Fire E2900 Server Copyrights ©2005 Sun Microsystems, Inc. All Rights Reserved. Sun, Sun Microsystems, the Sun logo, Sun Fire, Netra, Ultra, UltraComputing, Sun Enterprise, Sun Enterprise Ultra, Starfire, Solaris, Sun WebServer, OpenBoot, Solaris Web Start Wizards, Solstice, Solstice AdminSuite, Solaris Management Console, SEAM, SunScreen, Solstice DiskSuite, Solstice Backup, Sun StorEdge, Sun StorEdge LibMON, Solstice Site Manager, Solstice Domain Manager, Solaris Resource Manager, ShowMe, ShowMe How, SunVTS, Solstice Enterprise Agents, Solstice Enterprise Manager, Java, ShowMe TV, Solstice TMNscript, SunLink, Solstice SunNet Manager, Solstice Cooperative Consoles, Solstice TMNscript Toolkit, Solstice TMNscript Runtime, SunScreen EFS, PGX, PGX32, SunSpectrum, SunSpectrum Platinum, SunSpectrum Gold, SunSpectrum Silver, SunSpectrum Bronze, SunStart, SunVIP, SunSolve, and SunSolve EarlyNotifier are trademarks or registered trademarks of Sun Microsystems, Inc. in the United States and other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. in the United States and other countries. Products bearing SPARC trademarks are based upon an architecture developed by Sun Microsystems, Inc. UNIX is a registered trademark in the United States and other countries, exclusively licensed through X/Open Company, Ltd. All other product or service names mentioned -

Sun Ultratm 5 Workstation Just the Facts
Sun UltraTM 5 Workstation Just the Facts Copyrights 1999 Sun Microsystems, Inc. All Rights Reserved. Sun, Sun Microsystems, the Sun logo, Ultra, PGX, PGX24, Solaris, Sun Enterprise, SunClient, UltraComputing, Catalyst, SunPCi, OpenWindows, PGX32, VIS, Java, JDK, XGL, XIL, Java 3D, SunVTS, ShowMe, ShowMe TV, SunForum, Java WorkShop, Java Studio, AnswerBook, AnswerBook2, Sun Enterprise SyMON, Solstice, Solstice AutoClient, ShowMe How, SunCD, SunCD 2Plus, Sun StorEdge, SunButtons, SunDials, SunMicrophone, SunFDDI, SunLink, SunHSI, SunATM, SLC, ELC, IPC, IPX, SunSpectrum, JavaStation, SunSpectrum Platinum, SunSpectrum Gold, SunSpectrum Silver, SunSpectrum Bronze, SunVIP, SunSolve, and SunSolve EarlyNotifier are trademarks, registered trademarks, or service marks of Sun Microsystems, Inc. in the United States and other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. in the United States and other countries. Products bearing SPARC trademarks are based upon an architecture developed by Sun Microsystems, Inc. UNIX is a registered trademark in the United States and other countries, exclusively licensed through X/Open Company, Ltd. OpenGL is a registered trademark of Silicon Graphics, Inc. Display PostScript and PostScript are trademarks of Adobe Systems, Incorporated, which may be registered in certain jurisdictions. Netscape is a trademark of Netscape Communications Corporation. DLT is claimed as a trademark of Quantum Corporation in the United States and other countries. Just the Facts May 1999 Positioning The Sun UltraTM 5 Workstation Figure 1. The Ultra 5 workstation The Sun UltraTM 5 workstation is an entry-level workstation based upon the 333- and 360-MHz UltraSPARCTM-IIi processors. The Ultra 5 is Sun’s lowest-priced workstation, designed to meet the needs of price-sensitive and volume-purchase customers in the personal workstation market without sacrificing performance. -

Sun Ultratm 2 Workstation Just the Facts
Sun UltraTM 2 Workstation Just the Facts Copyrights 1999 Sun Microsystems, Inc. All Rights Reserved. Sun, Sun Microsystems, the Sun Logo, Ultra, SunFastEthernet, Sun Enterprise, TurboGX, TurboGXplus, Solaris, VIS, SunATM, SunCD, XIL, XGL, Java, Java 3D, JDK, S24, OpenWindows, Sun StorEdge, SunISDN, SunSwift, SunTRI/S, SunHSI/S, SunFastEthernet, SunFDDI, SunPC, NFS, SunVideo, SunButtons SunDials, UltraServer, IPX, IPC, SLC, ELC, Sun-3, Sun386i, SunSpectrum, SunSpectrum Platinum, SunSpectrum Gold, SunSpectrum Silver, SunSpectrum Bronze, SunVIP, SunSolve, and SunSolve EarlyNotifier are trademarks, registered trademarks, or service marks of Sun Microsystems, Inc. in the United States and other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. in the United States and other countries. Products bearing SPARC trademarks are based upon an architecture developed by Sun Microsystems, Inc. OpenGL is a registered trademark of Silicon Graphics, Inc. UNIX is a registered trademark in the United States and other countries, exclusively licensed through X/Open Company, Ltd. Display PostScript and PostScript are trademarks of Adobe Systems, Incorporated. DLT is claimed as a trademark of Quantum Corporation in the United States and other countries. Just the Facts May 1999 Sun Ultra 2 Workstation Figure 1. The Sun UltraTM 2 workstation Sun Ultra 2 Workstation Scalable Computing Power for the Desktop Sun UltraTM 2 workstations are designed for the technical users who require high performance and multiprocessing (MP) capability. The Sun UltraTM 2 desktop series combines the power of multiprocessing with high-bandwidth networking, high-performance graphics, and exceptional application performance in a compact desktop package. Users of MP-ready and multithreaded applications will benefit greatly from the performance of the Sun Ultra 2 dual-processor capability. -
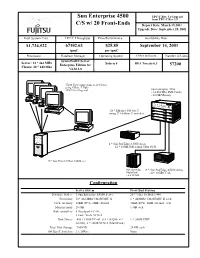
Sun Enterprise 4500 C/S W
Sun Enterprise 4500 TPC-C Rev. 5.0 Upgrade from TPC-C Rev 3.5 C/S w/ 20 Front-Ends Report Date: March 19,2001 Upgrade Date: September 25, 2001 Total System Cost TPC-C Throughput Price/Performance Availability Date $1,734,522 67102.63 $25.85 September 14, 2001 tpmC per tpmC Processors Database Manager Operating System Other Software Number of Users SymfoWARE Server Server: 14 * 464 MHz Solaris 8 BEA Tuxedo 6.3 Enterprise Edition for 57200 Clients: 20 * 440 Mhz VLM 3.0 57200 User Connections to 20 Clients using 10Base T Hubs 1000 Users/Segment Sun Enterprise 4500 - 14 464 Mhz 8Mb Cache - 28 GB Memory 20 * Ethernet 100 baseT using 2* 100Base T switches 4 * Sun StorEdge A1000 Array - 12 * 18GB Differential Ultra-SCSI 20 * Sun Ultra 10 Model 440Server Sun StorEdge 18 * Sun StorEdge A5200 Array MultiPack - 22* 18GB FCAL - 6 x 18 GB Configuration Server System Front End Systems Database Nodes: 1 Sun Enterprise E4500 Server 20 * Ultra 10 Model 440 Processors 14* 464 MHz UltraSPARC II 1 * 440MHz UltraSPARC II each Cache memory 32KB (D+I), 8MB external 32KB (D+I), 2MB external, each Main memory 28 GB 1 GB each Disk controllers 3 Dualport FC-AL, 2 Fast/Wide SCSI-2 Disk Drives 450 * 18GB FC-AL (18 * A5200, 4 * 1 * 20GB EIDE A1000), 6 * 18GB SCSI-2 (MultiPack) Total Disk Storage 7560GB 20 GB each 100 BaseT Switches 3 x 24Port None Sun Enterprise 4500 TPC-C Rev. 5.0 Upgrade from TPC-C Rev. 3.5 C/S w/ 20 Front-Ends Report Date: March 24, 2001 Upgrade Date: September 25, 2001 Pricing Summary Description Part Number Source Unit Price Qty Ext Price 3 Yr. -

Ultra 80 Workstations
Sun UltraTM 80 Workstation Just the Facts Copyrights 2001 Sun Microsystems, Inc. All Rights Reserved. Sun, Sun Microsystems, the Sun logo, Ultra, PGX, PGX32, Sun Workstation, Sun Enterprise, Starfire, Solaris, UltraComputing, VIS, Java, Java 3D, SunCD, Sun StorEdge, Solstice, Solstice AdminTools, SunVTS, Solstice Enterprise Agents, ShowMe, ShowMe How, ShowMe TV, iPlanet, SunPCi, StarOffice, Solaris Resource Manager, TurboGX, TurboGXplus, S24, OpenWindows, SunCD 2Plus, Netra, SunButtons, SunDials, Sun Quad FastEthernet, SunFDDI, SunLink, SunATM, SunVideo, SunVideo Plus, SunCamera, SunMicrophone, SunForum, SunSpectrum, SunSpectrum Platinum, SunSpectrum Gold, SunSpectrum Silver, SunSpectrum Bronze, SunStart, SunSolve, SunSolve EarlyNotifier, and SunClient are trademarks, registered trademarks, or service marks of Sun Microsystems, Inc. in the United States and other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. in the United States and other countries. Products bearing SPARC trademarks are based upon an architecture developed by Sun Microsystems, Inc. UNIX is a registered trademark in the United States and in other countries, exclusively licensed through X/Open Company, Ltd. OpenGL is a trademark of Silicon Graphics, Inc., which may be registered in certain jurisdictions. Netscape is a trademark of Netscape Communications Corporation. PostScript and Display PostScript are trademarks of Adobe Systems, Inc., which may be registered in certain jurisdictions. Last -

Cluster Platform 4500/3 User's Guide
Cluster Platform 4500/3 User’s Guide A product from the SunTone™ Platforms portfolio Sun Microsystems, Inc. 901 San Antonio Road Palo Alto, CA 94303-4900 U.S.A. 650-960-1300 Part No. 816-0445-11 July 2001, Revision A Send comments about this document to: [email protected] Copyright 2001 Sun Microsystems, Inc., 901 San Antonio Road, Palo Alto, CA 94303-4900 U.S.A. All rights reserved. This product or document is distributed under licenses restricting its use, copying, distribution, and decompilation. No part of this product or document may be reproduced in any form by any means without prior written authorization of Sun and its licensors, if any. Third-party software, including font technology, is copyrighted and licensed from Sun suppliers. Parts of the product may be derived from Berkeley BSD systems, licensed from the University of California. UNIX is a registered trademark in the U.S. and other countries, exclusively licensed through X/Open Company, Ltd. Sun, Sun Microsystems, the Sun logo, AnswerBook2, docs.sun.com, Solstice DiskSuite, OpenBoot, Sun Enterprise, BluePrints, JumpStart, Sun StorEdge, Netra, Solaris, and SunTone are trademarks, registered trademarks, or service marks of Sun Microsystems, Inc. in the U.S. and other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. in the U.S. and other countries. Products bearing SPARC trademarks are based upon an architecture developed by Sun Microsystems, Inc. Netscape Navigator is a trademark or registered trademark of Netscape Communications Corporation. Oracle is a registered trademark of Oracle Corporation. -

The Soa Platform Guide: Evaluate, Extend, Embrace
THE SOA PLATFORM GUIDE: EVALUATE, EXTEND, EMBRACE White Paper February 2006 2 Table of Contents Sun Microsystems, Inc. Table of Contents Executive Summary . 3 Service Oriented Architecture — Introduction . 4 Definition of SOA . 5 SOA Characteristics . 6 Standards . 6 Loose Coupling . 6 Accessibility and Reuse . 6 SOA Governance . 6 Service Descriptions . 7 An SOA Platform . 8 SOA Platform Design Centers . 8 Service Composition . 9 Service Control . 11 Service Delivery . 12 Service Access . 13 Composite Application Platform . 14 Sun SOA . 16 SOA and Data Center Architecture . 17 Summary . 18 Product Information . 18 For More Information . 19 3 Executive Summary Sun Microsystems, Inc. Chapter 1 Executive Summary In today’s world of shortened product cycles and heightened competition, IT’s task is to create a flexible environment; to ensure that the enterprise is strategically positioned to foster innovation; to respond to changing needs faster than ever before by reducing time to market for new services; and to drive down the cost of integration and total cost of ownership (TCO). This flexibility is made possible through the use of a Service-Oriented Architecture (SOA) — a design paradigm based on a loosely coupled collection of reusable services. The SOA enables agility through aligning the business and IT, providing business processes that embody core capabilities to employees, customers, suppliers, and partners. The set of infrastructure tools employed by IT to build, configure, deploy, monitor, and manage services is called the SOA platform. As technologies that facilitate service communication and orchestration are standardized, enterprises are able to fully realize the benefits of SOA without fear of vendor lock-in. -

Avaya Call Management System Sun Enterprise 3500 Computer Hardware Installation, Maintenance, and Troubleshooting
Avaya Call Management System Sun Enterprise 3500 Computer Hardware Installation, Maintenance, and Troubleshooting 585-215-873 Issue 6.0 May 2005 © 2005 Avaya Inc. Your responsibility for your company's telecommunications All Rights Reserved. security The final responsibility for securing both this system and its networked Notice equipment rests with you, an Avaya customer's system administrator, While reasonable efforts were made to ensure that the information in this your telecommunications peers, and your managers. Base the fulfillment document was complete and accurate at the time of printing, Avaya Inc. of your responsibility on acquired knowledge and resources from a can assume no liability for any errors. Changes and corrections to the variety of sources, including, but not limited to: information in this document may be incorporated in future releases. • Installation documents Documentation disclaimer • System administration documents • Security documents Avaya Inc. is not responsible for any modifications, additions, or deletions • Hardware-/software-based security tools to the original published version of this documentation unless such • Shared information between you and your peers modifications, additions, or deletions were performed by Avaya. • Telecommunications security experts Customer and/or End User agree to indemnify and hold harmless Avaya, Avaya's agents, servants and employees against all claims, lawsuits, To prevent intrusions to your telecommunications equipment, you and demands and judgments arising out of, or in connection with, subsequent your peers should carefully program and configure: modifications, additions or deletions to this documentation to the extent • Your Avaya-provided telecommunications systems and their made by the Customer or End User. interfaces • Your Avaya-provided software applications, as well as their Link disclaimer underlying hardware/software platforms and interfaces Avaya Inc. -

Sun Enterprise 250 Server Owner's Guide
Sun™ Enterprise™ 250 Server Owner’s Guide Sun Microsystems Computer Company A Sun Microsystems, Inc. Business 901 San Antonio Road Palo Alto, CA 94303-4900 USA 1 650 960-1300 fax 1 650 969-9131 Part No. 805-5160-10 Revision A, June 1998 Send comments about this document to: [email protected] Copyright 1998 Sun Microsystems, Inc., 901 San Antonio Road • Palo Alto, CA 94303 USA. All rights reserved. This product or document is protected by copyright and distributed under licenses restricting its use, copying, distribution, and decompilation. No part of this product or document may be reproduced in any form by any means without prior written authorization of Sun and its licensors, if any. Third-party software, including font technology, is copyrighted and licensed from Sun suppliers. Parts of the product may be derived from Berkeley BSD systems, licensed from the University of California. UNIX is a registered trademark in the U.S. and other countries, exclusively licensed through X/Open Company, Ltd. Sun, Sun Microsystems, the Sun logo, AnswerBook, SunDocs, Solaris, OpenBoot, OpenWindows, Solstice AdminSuite, Solstice Backup, Solstice DiskSuite, Solstice SyMON, SunSwift, SunVTS, and Sun Enterprise are trademarks or registered trademarks of Sun Microsystems, Inc. in the United States and in other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. in the United States and in other countries. Products bearing SPARC trademarks are based upon an architecture developed by Sun Microsystems, Inc. The OPEN LOOK and Sun™ Graphical User Interface was developed by Sun Microsystems, Inc. -

Jumpstart™ Technology
JumpStart™ Technology Effective Use in the Solaris™ Operating Environment Sun Microsystems, Inc. 901 San Antonio Road Palo Alto, CA 94303 U.S.A. 650-960-1300 Part No. 806-6872-10 September 2001, Revision 01 Send comments about this document to: [email protected] Copyright 2001 Sun Microsystems, Inc., 901 San Antonio Road • Palo Alto, CA 94303-4900 USA. All rights reserved. This product or document is protected by copyright and distributed under licenses restricting its use, copying, distribution, and decompilation. No part of this product or document may be reproduced in any form by any means without prior written authorization of Sun and its licensors, if any. Third-party software, including font technology, is copyrighted and licensed from Sun suppliers. Parts of the product may be derived from Berkeley BSD systems, licensed from the University of California. UNIX is a registered trademark in the U.S. and other countries, exclusively licensed through X/Open Company, Ltd. For Netscape Communicator™, the following notice applies: Copyright 1995 Netscape Communications Corporation. All rights reserved. Sun, Sun Microsystems, the Sun logo, AnswerBook, Solaris, JumpStart, Sun BluePrints, SunDocs, Sun Enterprise, Ultra Enterprise, OpenBoot, Sun StorEdge, Starfire, SunOs, USunOs, ltra, Netra, Solstice Backup, SunVTS, iPlanet, SunSolve Online, and Solstice Desksuite Solstice DiskSuite, and WebStart Flash are trademarks, registered trademarks, or service marks of Sun Microsystems, Inc. in the U.S. and other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. in the U.S. and other countries. Products bearing SPARC trademarks are based upon an architecture developed by Sun Microsystems, Inc. -

Sun™ Flash PROM Guide for Workstations and Workgroup Servers—Standalone Version
Sun™ Flash PROM Guide for Workstations and Workgroup Servers—Standalone Version for Sun™ Ultra 1, Ultra 2, Ultra 5, Ultra 10, Ultra 30, Ultra 60, Ultra 80, Sun Enterprise™ 220R, Sun Enterprise 250, Sun Enterprise 420R, Ultra Enterprise™ 450 Systems, Sun Blade™ 100, Sun Blade 1000, Sun Fire™ 280R, Sun Fire 880 and Sun Netra™ T4 A Sun Microsystems, Inc. Business 901 San Antonio Road Palo Alto, CA 94303-4900 USA 1 650 960-1300 fax 1 650 969-9131 Part No. 802-3233-22 Revision A, October 2001 Send comments about this document to: [email protected] Copyright 1995 - 2001 Sun Microsystems, Inc., 901 San Antonio Road • Palo Alto, CA 94303 USA. All rights reserved. This product or document is protected by copyright and distributed under licenses restricting its use, copying, distribution, and decompilation. No part of this product or document may be reproduced in any form by any means without prior written authorization of Sun and its licensors, if any. Third-party software, including font technology, is copyrighted and licensed from Sun suppliers. Parts of the product may be derived from Berkeley BSD systems, licensed from the University of California. UNIX is a registered trademark in the U.S. and other countries, exclusively licensed through X/Open Company, Ltd. Sun, Sun Microsystems, the Sun logo, Ultra, Sun Enterprise, Ultra Enterprise, Java, Java Coffee Cup logo, Sun Blade, Sun Fire, Netra and Solaris are trademarks, registered trademarks, or service marks of Sun Microsystems, Inc. in the U.S. and other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. -

Sun Fire 6800 Midframe Server Sun.Com/Store, Or Contact an Authorized Sun Reseller Near You
Datasheet Sun Fire™ 6800 Midframe Server On the Web sun.com/midframe Sun Fire™6800 Midframe Server Highly-available powerhouse for mission-critical applications. Key feature highlights For data warehousing, data mining, server consolidation, and other mission-critical data center Up to 24 high-performance, award-winning applications, the UltraSPARC® III technology-based Sun Fire™ 6800 server is a powerful, highly UltraSPARC® III processors in a symmetric available solution. Full hardware redundancy and a variety of mainframe-class availability multiprocessing architecture. features, such as Dynamic Reconfiguration, online upgrades, concurrent maintenance, and auto diagnosis and recovery help provide maximum uptime. With Solaris™ Resource Manager Investment protection with hot-swappable software and Dynamic System Domains, the server accommodates changing resource require- Uniboard CPU/Memory boards, common ments across multiple applications. For environments where manageability, performance, and across the entire Sun Fire 4800-15K availability are key, the Sun Fire 6800 server delivers. server family. High availability via fault-isolated Dynamic System Domains, Dynamic Reconfiguration, online upgrades, and auto diagnosis and recovery. Fully redundant, reconfigurable Sun™ Fireplane Interconnect delivers outstand- ing real-world performance. Capacity on Demand (COD) purchasing option helps enhance and simplify system scalability, reduce hardware acquisition costs, and increase system availability. ™ Purchase these products from the SunSM