Tree-Decompositions of Small Pathwidthଁ
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
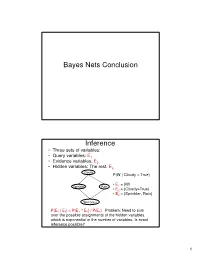
Bayes Nets Conclusion Inference
Bayes Nets Conclusion Inference • Three sets of variables: • Query variables: E1 • Evidence variables: E2 • Hidden variables: The rest, E3 Cloudy P(W | Cloudy = True) • E = {W} Sprinkler Rain 1 • E2 = {Cloudy=True} • E3 = {Sprinkler, Rain} Wet Grass P(E 1 | E 2) = P(E 1 ^ E 2) / P(E 2) Problem: Need to sum over the possible assignments of the hidden variables, which is exponential in the number of variables. Is exact inference possible? 1 A Simple Case A B C D • Suppose that we want to compute P(D = d) from this network. A Simple Case A B C D • Compute P(D = d) by summing the joint probability over all possible values of the remaining variables A, B, and C: P(D === d) === ∑∑∑ P(A === a, B === b,C === c, D === d) a,b,c 2 A Simple Case A B C D • Decompose the joint by using the fact that it is the product of terms of the form: P(X | Parents(X)) P(D === d) === ∑∑∑ P(D === d | C === c)P(C === c | B === b)P(B === b | A === a)P(A === a) a,b,c A Simple Case A B C D • We can avoid computing the sum for all possible triplets ( A,B,C) by distributing the sums inside the product P(D === d) === ∑∑∑ P(D === d | C === c)∑∑∑P(C === c | B === b)∑∑∑P(B === b| A === a)P(A === a) c b a 3 A Simple Case A B C D This term depends only on B and can be written as a 2- valued function fA(b) P(D === d) === ∑∑∑ P(D === d | C === c)∑∑∑P(C === c | B === b)∑∑∑P(B === b| A === a)P(A === a) c b a A Simple Case A B C D This term depends only on c and can be written as a 2- valued function fB(c) === === === === === === P(D d) ∑∑∑ P(D d | C c)∑∑∑P(C c | B b)f A(b) c b …. -

On Treewidth and Graph Minors
On Treewidth and Graph Minors Daniel John Harvey Submitted in total fulfilment of the requirements of the degree of Doctor of Philosophy February 2014 Department of Mathematics and Statistics The University of Melbourne Produced on archival quality paper ii Abstract Both treewidth and the Hadwiger number are key graph parameters in structural and al- gorithmic graph theory, especially in the theory of graph minors. For example, treewidth demarcates the two major cases of the Robertson and Seymour proof of Wagner's Con- jecture. Also, the Hadwiger number is the key measure of the structural complexity of a graph. In this thesis, we shall investigate these parameters on some interesting classes of graphs. The treewidth of a graph defines, in some sense, how \tree-like" the graph is. Treewidth is a key parameter in the algorithmic field of fixed-parameter tractability. In particular, on classes of bounded treewidth, certain NP-Hard problems can be solved in polynomial time. In structural graph theory, treewidth is of key interest due to its part in the stronger form of Robertson and Seymour's Graph Minor Structure Theorem. A key fact is that the treewidth of a graph is tied to the size of its largest grid minor. In fact, treewidth is tied to a large number of other graph structural parameters, which this thesis thoroughly investigates. In doing so, some of the tying functions between these results are improved. This thesis also determines exactly the treewidth of the line graph of a complete graph. This is a critical example in a recent paper of Marx, and improves on a recent result by Grohe and Marx. -

Randomly Coloring Graphs of Logarithmically Bounded Pathwidth Shai Vardi
Randomly coloring graphs of logarithmically bounded pathwidth Shai Vardi To cite this version: Shai Vardi. Randomly coloring graphs of logarithmically bounded pathwidth. 2018. hal-01832102 HAL Id: hal-01832102 https://hal.archives-ouvertes.fr/hal-01832102 Preprint submitted on 6 Jul 2018 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Randomly coloring graphs of logarithmically bounded pathwidth Shai Vardi∗ Abstract We consider the problem of sampling a proper k-coloring of a graph of maximal degree ∆ uniformly at random. We describe a new Markov chain for sampling colorings, and show that it mixes rapidly on graphs of logarithmically bounded pathwidth if k ≥ (1 + )∆, for any > 0, using a new hybrid paths argument. ∗California Institute of Technology, Pasadena, CA, 91125, USA. E-mail: [email protected]. 1 Introduction A (proper) k-coloring of a graph G = (V; E) is an assignment σ : V ! f1; : : : ; kg such that neighboring vertices have different colors. We consider the problem of sampling (almost) uniformly at random from the space of all k-colorings of a graph.1 The problem has received considerable attention from the computer science community in recent years, e.g., [12, 17, 24, 26, 33, 44, 45]. -

Mutant Knots and Intersection Graphs 1 Introduction
Mutant knots and intersection graphs S. V. CHMUTOV S. K. LANDO We prove that if a finite order knot invariant does not distinguish mutant knots, then the corresponding weight system depends on the intersection graph of a chord diagram rather than on the diagram itself. Conversely, if we have a weight system depending only on the intersection graphs of chord diagrams, then the composition of such a weight system with the Kontsevich invariant determines a knot invariant that does not distinguish mutant knots. Thus, an equivalence between finite order invariants not distinguishing mutants and weight systems depending on intersections graphs only is established. We discuss relationship between our results and certain Lie algebra weight systems. 57M15; 57M25 1 Introduction Below, we use standard notions of the theory of finite order, or Vassiliev, invariants of knots in 3-space; their definitions can be found, for example, in [6] or [14], and we recall them briefly in Section 2. All knots are assumed to be oriented. Two knots are said to be mutant if they differ by a rotation of a tangle with four endpoints about either a vertical axis, or a horizontal axis, or an axis perpendicular to the paper. If necessary, the orientation inside the tangle may be replaced by the opposite one. Here is a famous example of mutant knots, the Conway (11n34) knot C of genus 3, and Kinoshita–Terasaka (11n42) knot KT of genus 2 (see [1]). C = KT = Note that the change of the orientation of a knot can be achieved by a mutation in the complement to a trivial tangle. -

Attacking Client-Side JIT Compilers.Key
Attacking Client-Side JIT Compilers Samuel Groß (@5aelo) !1 A JavaScript Engine Parser JIT Compiler Interpreter Runtime Garbage Collector !2 A JavaScript Engine • Parser: entrypoint for script execution, usually emits custom Parser bytecode JIT Compiler • Bytecode then consumed by interpreter or JIT compiler • Executing code interacts with the Interpreter runtime which defines the Runtime representation of various data structures, provides builtin functions and objects, etc. Garbage • Garbage collector required to Collector deallocate memory !3 A JavaScript Engine • Parser: entrypoint for script execution, usually emits custom Parser bytecode JIT Compiler • Bytecode then consumed by interpreter or JIT compiler • Executing code interacts with the Interpreter runtime which defines the Runtime representation of various data structures, provides builtin functions and objects, etc. Garbage • Garbage collector required to Collector deallocate memory !4 A JavaScript Engine • Parser: entrypoint for script execution, usually emits custom Parser bytecode JIT Compiler • Bytecode then consumed by interpreter or JIT compiler • Executing code interacts with the Interpreter runtime which defines the Runtime representation of various data structures, provides builtin functions and objects, etc. Garbage • Garbage collector required to Collector deallocate memory !5 A JavaScript Engine • Parser: entrypoint for script execution, usually emits custom Parser bytecode JIT Compiler • Bytecode then consumed by interpreter or JIT compiler • Executing code interacts with the Interpreter runtime which defines the Runtime representation of various data structures, provides builtin functions and objects, etc. Garbage • Garbage collector required to Collector deallocate memory !6 Agenda 1. Background: Runtime Parser • Object representation and Builtins JIT Compiler 2. JIT Compiler Internals • Problem: missing type information • Solution: "speculative" JIT Interpreter 3. -

Induced Minors and Well-Quasi-Ordering Jaroslaw Blasiok, Marcin Kamiński, Jean-Florent Raymond, Théophile Trunck
Induced minors and well-quasi-ordering Jaroslaw Blasiok, Marcin Kamiński, Jean-Florent Raymond, Théophile Trunck To cite this version: Jaroslaw Blasiok, Marcin Kamiński, Jean-Florent Raymond, Théophile Trunck. Induced minors and well-quasi-ordering. EuroComb: European Conference on Combinatorics, Graph Theory and Appli- cations, Aug 2015, Bergen, Norway. pp.197-201, 10.1016/j.endm.2015.06.029. lirmm-01349277 HAL Id: lirmm-01349277 https://hal-lirmm.ccsd.cnrs.fr/lirmm-01349277 Submitted on 27 Jul 2016 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Available online at www.sciencedirect.com www.elsevier.com/locate/endm Induced minors and well-quasi-ordering Jaroslaw Blasiok 1,2 School of Engineering and Applied Sciences, Harvard University, United States Marcin Kami´nski 2 Institute of Computer Science, University of Warsaw, Poland Jean-Florent Raymond 2 Institute of Computer Science, University of Warsaw, Poland, and LIRMM, University of Montpellier, France Th´eophile Trunck 2 LIP, ENS´ de Lyon, France Abstract AgraphH is an induced minor of a graph G if it can be obtained from an induced subgraph of G by contracting edges. Otherwise, G is said to be H-induced minor- free. -
![Arxiv:1907.08517V3 [Math.CO] 12 Mar 2021](https://docslib.b-cdn.net/cover/8441/arxiv-1907-08517v3-math-co-12-mar-2021-308441.webp)
Arxiv:1907.08517V3 [Math.CO] 12 Mar 2021
RANDOM COGRAPHS: BROWNIAN GRAPHON LIMIT AND ASYMPTOTIC DEGREE DISTRIBUTION FRÉDÉRIQUE BASSINO, MATHILDE BOUVEL, VALENTIN FÉRAY, LUCAS GERIN, MICKAËL MAAZOUN, AND ADELINE PIERROT ABSTRACT. We consider uniform random cographs (either labeled or unlabeled) of large size. Our first main result is the convergence towards a Brownian limiting object in the space of graphons. We then show that the degree of a uniform random vertex in a uniform cograph is of order n, and converges after normalization to the Lebesgue measure on [0; 1]. We finally an- alyze the vertex connectivity (i.e. the minimal number of vertices whose removal disconnects the graph) of random connected cographs, and show that this statistics converges in distribution without renormalization. Unlike for the graphon limit and for the degree of a random vertex, the limiting distribution of the vertex connectivity is different in the labeled and unlabeled settings. Our proofs rely on the classical encoding of cographs via cotrees. We then use mainly combi- natorial arguments, including the symbolic method and singularity analysis. 1. INTRODUCTION 1.1. Motivation. Random graphs are arguably the most studied objects at the interface of com- binatorics and probability theory. One aspect of their study consists in analyzing a uniform random graph of large size n in a prescribed family, e.g. perfect graphs [MY19], planar graphs [Noy14], graphs embeddable in a surface of given genus [DKS17], graphs in subcritical classes [PSW16], hereditary classes [HJS18] or addable classes [MSW06, CP19]. The present paper focuses on uniform random cographs (both in the labeled and unlabeled settings). Cographs were introduced in the seventies by several authors independently, see e.g. -

Tree Structures
Tree Structures Definitions: o A tree is a connected acyclic graph. o A disconnected acyclic graph is called a forest o A tree is a connected digraph with these properties: . There is exactly one node (Root) with in-degree=0 . All other nodes have in-degree=1 . A leaf is a node with out-degree=0 . There is exactly one path from the root to any leaf o The degree of a tree is the maximum out-degree of the nodes in the tree. o If (X,Y) is a path: X is an ancestor of Y, and Y is a descendant of X. Root X Y CSci 1112 – Algorithms and Data Structures, A. Bellaachia Page 1 Level of a node: Level 0 or 1 1 or 2 2 or 3 3 or 4 Height or depth: o The depth of a node is the number of edges from the root to the node. o The root node has depth zero o The height of a node is the number of edges from the node to the deepest leaf. o The height of a tree is a height of the root. o The height of the root is the height of the tree o Leaf nodes have height zero o A tree with only a single node (hence both a root and leaf) has depth and height zero. o An empty tree (tree with no nodes) has depth and height −1. o It is the maximum level of any node in the tree. CSci 1112 – Algorithms and Data Structures, A. -

A Simple Linear-Time Algorithm for Finding Path-Decompostions of Small Width
Introduction Preliminary Definitions Pathwidth Algorithm Summary A Simple Linear-Time Algorithm for Finding Path-Decompostions of Small Width Kevin Cattell Michael J. Dinneen Michael R. Fellows Department of Computer Science University of Victoria Victoria, B.C. Canada V8W 3P6 Information Processing Letters 57 (1996) 197–203 Kevin Cattell, Michael J. Dinneen, Michael R. Fellows Linear-Time Path-Decomposition Algorithm Introduction Preliminary Definitions Pathwidth Algorithm Summary Outline 1 Introduction Motivation History 2 Preliminary Definitions Boundaried graphs Path-decompositions Topological tree obstructions 3 Pathwidth Algorithm Main result Linear-time algorithm Proof of correctness Other results Kevin Cattell, Michael J. Dinneen, Michael R. Fellows Linear-Time Path-Decomposition Algorithm Introduction Preliminary Definitions Motivation Pathwidth Algorithm History Summary Motivation Pathwidth is related to several VLSI layout problems: vertex separation link gate matrix layout edge search number ... Usefullness of bounded treewidth in: study of graph minors (Robertson and Seymour) input restrictions for many NP-complete problems (fixed-parameter complexity) Kevin Cattell, Michael J. Dinneen, Michael R. Fellows Linear-Time Path-Decomposition Algorithm Introduction Preliminary Definitions Motivation Pathwidth Algorithm History Summary History General problem(s) is NP-complete Input: Graph G, integer t Question: Is tree/path-width(G) ≤ t? Algorithmic development (fixed t): O(n2) nonconstructive treewidth algorithm by Robertson and Seymour (1986) O(nt+2) treewidth algorithm due to Arnberg, Corneil and Proskurowski (1987) O(n log n) treewidth algorithm due to Reed (1992) 2 O(2t n) treewidth algorithm due to Bodlaender (1993) O(n log2 n) pathwidth algorithm due to Ellis, Sudborough and Turner (1994) Kevin Cattell, Michael J. Dinneen, Michael R. -

Minimal Acyclic Forbidden Minors for the Family of Graphs with Bounded Path-Width
Discrete Mathematics 127 (1994) 293-304 293 North-Holland Minimal acyclic forbidden minors for the family of graphs with bounded path-width Atsushi Takahashi, Shuichi Ueno and Yoji Kajitani Department of Electrical and Electronic Engineering, Tokyo Institute of Technology. Tokyo, 152. Japan Received 27 November 1990 Revised 12 February 1992 Abstract The graphs with bounded path-width, introduced by Robertson and Seymour, and the graphs with bounded proper-path-width, introduced in this paper, are investigated. These families of graphs are minor-closed. We characterize the minimal acyclic forbidden minors for these families of graphs. We also give estimates for the numbers of minimal forbidden minors and for the numbers of vertices of the largest minimal forbidden minors for these families of graphs. 1. Introduction Graphs we consider are finite and undirected, but may have loops and multiple edges unless otherwise specified. A graph H is a minor of a graph G if H is isomorphic to a graph obtained from a subgraph of G by contracting edges. A family 9 of graphs is said to be minor-closed if the following condition holds: If GEB and H is a minor of G then H EF. A graph G is a minimal forbidden minor for a minor-closed family F of graphs if G#8 and any proper minor of G is in 9. Robertson and Seymour proved the following deep theorems. Theorem 1.1 (Robertson and Seymour [15]). Every minor-closed family of graphs has a finite number of minimal forbidden minors. Theorem 1.2 (Robertson and Seymour [14]). -

1 More Register Allocation Interference Graph Allocators
More Register Allocation Last time – Register allocation – Global allocation via graph coloring Today – More register allocation – Clarifications from last time – Finish improvements on basic graph coloring concept – Procedure calls – Interprocedural CS553 Lecture Register Allocation II 2 Interference Graph Allocators Chaitin Briggs CS553 Lecture Register Allocation II 3 1 Coalescing Move instructions – Code generation can produce unnecessary move instructions mov t1, t2 – If we can assign t1 and t2 to the same register, we can eliminate the move Idea – If t1 and t2 are not connected in the interference graph, coalesce them into a single variable Problem – Coalescing can increase the number of edges and make a graph uncolorable – Limit coalescing coalesce to avoid uncolorable t1 t2 t12 graphs CS553 Lecture Register Allocation II 4 Coalescing Logistics Rule – If the virtual registers s1 and s2 do not interfere and there is a copy statement s1 = s2 then s1 and s2 can be coalesced – Steps – SSA – Find webs – Virtual registers – Interference graph – Coalesce CS553 Lecture Register Allocation II 5 2 Example (Apply Chaitin algorithm) Attempt to 3-color this graph ( , , ) Stack: Weighted order: a1 b d e c a1 b a e c 2 a2 b a1 c e d a2 d The example indicates that nodes are visited in increasing weight order. Chaitin and Briggs visit nodes in an arbitrary order. CS553 Lecture Register Allocation II 6 Example (Apply Briggs Algorithm) Attempt to 2-color this graph ( , ) Stack: Weighted order: a1 b d e c a1 b* a e c 2 a2* b a1* c e* d a2 d * blocked node CS553 Lecture Register Allocation II 7 3 Spilling (Original CFG and Interference Graph) a1 := .. -

Partitioning a Graph Into Disjoint Cliques and a Triangle-Free Graph
This is a repository copy of Partitioning a graph into disjoint cliques and a triangle-free graph. White Rose Research Online URL for this paper: http://eprints.whiterose.ac.uk/85292/ Version: Accepted Version Article: Abu-Khzam, FN, Feghali, C and Muller, H (2015) Partitioning a graph into disjoint cliques and a triangle-free graph. Discrete Applied Mathematics, 190-19. 1 - 12. ISSN 0166-218X https://doi.org/10.1016/j.dam.2015.03.015 © 2015, Elsevier. Licensed under the Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International http://creativecommons.org/licenses/by-nc-nd/4.0/ Reuse Unless indicated otherwise, fulltext items are protected by copyright with all rights reserved. The copyright exception in section 29 of the Copyright, Designs and Patents Act 1988 allows the making of a single copy solely for the purpose of non-commercial research or private study within the limits of fair dealing. The publisher or other rights-holder may allow further reproduction and re-use of this version - refer to the White Rose Research Online record for this item. Where records identify the publisher as the copyright holder, users can verify any specific terms of use on the publisher’s website. Takedown If you consider content in White Rose Research Online to be in breach of UK law, please notify us by emailing [email protected] including the URL of the record and the reason for the withdrawal request. [email protected] https://eprints.whiterose.ac.uk/ Partitioning a Graph into Disjoint Cliques and a Triangle-free Graph Faisal N. Abu-Khzam, Carl Feghali, Haiko M¨uller Abstract A graph G =(V, E) is partitionable if there exists a partition {A,B} of V such that A induces a disjoint union of cliques and B induces a triangle- free graph.