THE NUMBER of BIT COMPARISONS USED by QUICKSORT: an AVERAGE-CASE ANALYSIS 1. Introduction and Summary Algorithms for Sorting
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mock In-Class Test COMS10007 Algorithms 2018/2019
Mock In-class Test COMS10007 Algorithms 2018/2019 Throughout this paper log() denotes the binary logarithm, i.e, log(n) = log2(n), and ln() denotes the logarithm to base e, i.e., ln(n) = loge(n). 1 O-notation 1. Let f : N ! N be a function. Define the set Θ(f(n)). Proof. Θ(f(n)) = fg(n) : There exist positive constants c1; c2 and n0 s.t. 0 ≤ c1f(n) ≤ g(n) ≤ c2f(n) for all n ≥ n0g 2. Give a formal proof of the statement: p 10 n 2 O(n) : p Proof. We need to show that there are positive constants c; n0 such that 10 n ≤ c · n, 10 p for every n ≥ n0. The previous inequality is equivalent to c ≤ n, which in turn 100 100 gives c2 ≤ n. Hence, we can pick c = 1 and n0 = 12 = 100. 3. Use the racetrack principle to prove the following statement: n 2 O(2n) : Hint: The following facts can be useful: • The derivative of 2n is ln(2)2n. 1 • 2 ≤ ln(2) ≤ 1 holds. n Proof. We need to show that there are positive constants c; n0 such that n ≤ c·2 . We n pick c = 1 and n0 = 1. Observe that n ≤ 2 holds for n = n0(= 1). It remains to show n that n ≤ 2 also holds for every n ≥ n0. To show this, we use the racetrack principle. Observe that the derivative of n is 1 and the derivative of 2n is ln(2)2n. Hence, by n the racetrack principle it is enough to show that 1 ≤ ln(2)2 holds for every n ≥ n0, 1 1 1 1 or log( ln 2 ) ≤ n. -

Optimizing MPC for Robust and Scalable Integer and Floating-Point Arithmetic
Optimizing MPC for robust and scalable integer and floating-point arithmetic Liisi Kerik1, Peeter Laud1, and Jaak Randmets1,2 1 Cybernetica AS, Tartu, Estonia 2 University of Tartu, Tartu, Estonia {liisi.kerik, peeter.laud, jaak.randmets}@cyber.ee Abstract. Secure multiparty computation (SMC) is a rapidly matur- ing field, but its number of practical applications so far has been small. Most existing applications have been run on small data volumes with the exception of a recent study processing tens of millions of education and tax records. For practical usability, SMC frameworks must be able to work with large collections of data and perform reliably under such conditions. In this work we demonstrate that with the help of our re- cently developed tools and some optimizations, the Sharemind secure computation framework is capable of executing tens of millions integer operations or hundreds of thousands floating-point operations per sec- ond. We also demonstrate robustness in handling a billion integer inputs and a million floating-point inputs in parallel. Such capabilities are ab- solutely necessary for real world deployments. Keywords: Secure Multiparty Computation, Floating-point operations, Protocol design 1 Introduction Secure multiparty computation (SMC) [19] allows a group of mutually distrust- ing entities to perform computations on data private to various members of the group, without others learning anything about that data or about the intermedi- ate values in the computation. Theory-wise, the field is quite mature; there exist several techniques to achieve privacy and correctness of any computation [19, 28, 15, 16, 21], and the asymptotic overheads of these techniques are known. -

CS 270 Algorithms
CS 270 Algorithms Week 10 Oliver Kullmann Binary heaps Sorting Heapification Building a heap 1 Binary heaps HEAP- SORT Priority 2 Heapification queues QUICK- 3 Building a heap SORT Analysing 4 QUICK- HEAP-SORT SORT 5 Priority queues Tutorial 6 QUICK-SORT 7 Analysing QUICK-SORT 8 Tutorial CS 270 General remarks Algorithms Oliver Kullmann Binary heaps Heapification Building a heap We return to sorting, considering HEAP-SORT and HEAP- QUICK-SORT. SORT Priority queues CLRS Reading from for week 7 QUICK- SORT 1 Chapter 6, Sections 6.1 - 6.5. Analysing 2 QUICK- Chapter 7, Sections 7.1, 7.2. SORT Tutorial CS 270 Discover the properties of binary heaps Algorithms Oliver Running example Kullmann Binary heaps Heapification Building a heap HEAP- SORT Priority queues QUICK- SORT Analysing QUICK- SORT Tutorial CS 270 First property: level-completeness Algorithms Oliver Kullmann Binary heaps In week 7 we have seen binary trees: Heapification Building a 1 We said they should be as “balanced” as possible. heap 2 Perfect are the perfect binary trees. HEAP- SORT 3 Now close to perfect come the level-complete binary Priority trees: queues QUICK- 1 We can partition the nodes of a (binary) tree T into levels, SORT according to their distance from the root. Analysing 2 We have levels 0, 1,..., ht(T ). QUICK- k SORT 3 Level k has from 1 to 2 nodes. Tutorial 4 If all levels k except possibly of level ht(T ) are full (have precisely 2k nodes in them), then we call the tree level-complete. CS 270 Examples Algorithms Oliver The binary tree Kullmann 1 ❚ Binary heaps ❥❥❥❥ ❚❚❚❚ ❥❥❥❥ ❚❚❚❚ ❥❥❥❥ ❚❚❚❚ Heapification 2 ❥ 3 ❖ ❄❄ ❖❖ Building a ⑧⑧ ❄ ⑧⑧ ❖❖ heap ⑧⑧ ❄ ⑧⑧ ❖❖❖ 4 5 6 ❄ 7 ❄ HEAP- ⑧ ❄ ⑧ ❄ SORT ⑧⑧ ❄ ⑧⑧ ❄ Priority 10 13 14 15 queues QUICK- is level-complete (level-sizes are 1, 2, 4, 4), while SORT ❥ 1 ❚❚ Analysing ❥❥❥❥ ❚❚❚❚ QUICK- ❥❥❥ ❚❚❚ SORT ❥❥❥ ❚❚❚❚ 2 ❥❥ 3 ♦♦♦ ❄❄ ⑧ Tutorial ♦♦ ❄❄ ⑧⑧ ♦♦♦ ⑧ 4 ❄ 5 ❄ 6 ❄ ⑧⑧ ❄❄ ⑧ ❄ ⑧ ❄ ⑧⑧ ❄ ⑧⑧ ❄ ⑧⑧ ❄ 8 9 10 11 12 13 is not (level-sizes are 1, 2, 3, 6). -

CS211 ❒ Overview • Code (Number Guessing Example)
CS211 1. Number Guessing Example ASYMPTOTIC COMPLEXITY 1.1 Code ❒ Overview import java.io.*; • code (number guessing example) public class NumberGuess { • approximate analysis to motivate math public static void main(String[] args) throws IOException { int guess; • machine model int count; final int LOW=Integer.parseInt(args[0]); • analysis (space, time) final int HIGH=Integer.parseInt(args[1]); final int STOP=HIGH-LOW+1; • machine architecture and time assumptions int target = (int)(Math.random()*(HIGH-LOW+1))+(int)(LOW); BufferedReader in = new BufferedReader(new • code analysis InputStreamReader(System.in)); • more assumptions System.out.print("\nGuess an integer: "); guess = Integer.parseInt(in.readLine()); • Big Oh notation count = 1; • examples while (guess != target && guess >= LOW && • extra material (theory, background, math) guess <= HIGH && count < STOP ) { if (guess < target) System.out.println("Too low!"); else if (guess>target) System.out.println("Too high!"); else System.exit(0); System.out.print("\nGuess an integer: "); guess = Integer.parseInt(in.readLine()); count++ ; } if (target == guess) System.out.println("\nCongratulations!\n"); } } 12 1.2 Solution Algorithms 1.4 More General • random: • count only comparisons of guess to target - pick any number (same number as guesses) - worst-case time could be infinite • other examples: • linear: range linea binar pattern r y - guess one number at a time 1111→1 - start from bottom and head to top 1–10 10 5 5→7→8→9→10 1–100 100 8 50→75→87→93→96→98→99→100 - worst-case time could -

Binary Search Algorithm Anthony Lin¹* Et Al
WikiJournal of Science, 2019, 2(1):5 doi: 10.15347/wjs/2019.005 Encyclopedic Review Article Binary search algorithm Anthony Lin¹* et al. Abstract In In computer science, binary search, also known as half-interval search,[1] logarithmic search,[2] or binary chop,[3] is a search algorithm that finds a position of a target value within a sorted array.[4] Binary search compares the target value to an element in the middle of the array. If they are not equal, the half in which the target cannot lie is eliminated and the search continues on the remaining half, again taking the middle element to compare to the target value, and repeating this until the target value is found. If the search ends with the remaining half being empty, the target is not in the array. Binary search runs in logarithmic time in the worst case, making 푂(log 푛) comparisons, where 푛 is the number of elements in the array, the 푂 is ‘Big O’ notation, and 푙표푔 is the logarithm.[5] Binary search is faster than linear search except for small arrays. However, the array must be sorted first to be able to apply binary search. There are spe- cialized data structures designed for fast searching, such as hash tables, that can be searched more efficiently than binary search. However, binary search can be used to solve a wider range of problems, such as finding the next- smallest or next-largest element in the array relative to the target even if it is absent from the array. There are numerous variations of binary search. -

Introduction to Algorithms
CS 5002: Discrete Structures Fall 2018 Lecture 9: November 8, 2018 1 Instructors: Adrienne Slaughter, Tamara Bonaci Disclaimer: These notes have not been subjected to the usual scrutiny reserved for formal publications. They may be distributed outside this class only with the permission of the Instructor. Introduction to Algorithms Readings for this week: Rosen, Chapter 2.1, 2.2, 2.5, 2.6 Sets, Set Operations, Cardinality of Sets, Matrices 9.1 Overview Objective: Introduce algorithms. 1. Review logarithms 2. Asymptotic analysis 3. Define Algorithm 4. How to express or describe an algorithm 5. Run time, space (Resource usage) 6. Determining Correctness 7. Introduce representative problems 1. foo 9.2 Asymptotic Analysis The goal with asymptotic analysis is to try to find a bound, or an asymptote, of a function. This allows us to come up with an \ordering" of functions, such that one function is definitely bigger than another, in order to compare two functions. We do this by considering the value of the functions as n goes to infinity, so for very large values of n, as opposed to small values of n that may be easy to calculate. Once we have this ordering, we can introduce some terminology to describe the relationship of two functions. 9-1 9-2 Lecture 9: November 8, 2018 Growth of Functions nn 4096 n! 2048 1024 512 2n 256 128 n2 64 32 n log(n) 16 n 8 p 4 n log(n) 2 1 1 2 3 4 5 6 7 8 From this chart, we see: p 1 log n n n n log(n) n2 2n n! nn (9.1) Complexity Terminology Θ(1) Constant Θ(log n) Logarithmic Θ(n) Linear Θ(n log n) Linearithmic Θ nb Polynomial Θ(bn) (where b > 1) Exponential Θ(n!) Factorial 9.2.1 Big-O: Upper Bound Definition 9.1 (Big-O: Upper Bound) f(n) = O(g(n)) means there exists some constant c such that f(n) ≤ c · g(n), for large enough n (that is, as n ! 1). -

Comparison of Parallel Sorting Algorithms
Comparison of parallel sorting algorithms Darko Božidar and Tomaž Dobravec Faculty of Computer and Information Science, University of Ljubljana, Slovenia Technical report November 2015 TABLE OF CONTENTS 1. INTRODUCTION .................................................................................................... 3 2. THE ALGORITHMS ................................................................................................ 3 2.1 BITONIC SORT ........................................................................................................................ 3 2.2 MULTISTEP BITONIC SORT ................................................................................................. 3 2.3 IBR BITONIC SORT ................................................................................................................ 3 2.4 MERGE SORT .......................................................................................................................... 4 2.5 QUICKSORT ............................................................................................................................ 4 2.6 RADIX SORT ........................................................................................................................... 4 2.7 SAMPLE SORT ........................................................................................................................ 4 3. TESTING ENVIRONMENT .................................................................................... 5 4. RESULTS ................................................................................................................ -

Calculating Logs Manually
calculating logs manually File Name: calculating logs manually.pdf Size: 2113 KB Type: PDF, ePub, eBook Category: Book Uploaded: 3 May 2019, 12:21 PM Rating: 4.6/5 from 561 votes. Status: AVAILABLE Last checked: 10 Minutes ago! In order to read or download calculating logs manually ebook, you need to create a FREE account. Download Now! eBook includes PDF, ePub and Kindle version ✔ Register a free 1 month Trial Account. ✔ Download as many books as you like (Personal use) ✔ Cancel the membership at any time if not satisfied. ✔ Join Over 80000 Happy Readers Book Descriptions: We have made it easy for you to find a PDF Ebooks without any digging. And by having access to our ebooks online or by storing it on your computer, you have convenient answers with calculating logs manually . To get started finding calculating logs manually , you are right to find our website which has a comprehensive collection of manuals listed. Our library is the biggest of these that have literally hundreds of thousands of different products represented. Home | Contact | DMCA Book Descriptions: calculating logs manually And let’s start with the logarithm of 2. As a kid I always wanted to know how to calculate log 2 and nobody was able to tell me. Can we guess the logarithm of 19,683.Let’s follow the chain. We are looking for 1225, so to account for the difference let’s round 3.0876 up to 3.088. How to calculate log 11. Here is a way to do this. We can take the geometric mean of 10 and 12. -

Hardware Implementation of the Logarithm Function
DEPARTMENT OF ELECTRICAL AND INFORMATION TECHNOLOGY,FACULTY OF ENGINEERING, LTH MASTER OF SCIENCE THESIS Hardware Implementation of the Logarithm Function using Improved Parabolic Synthesis Supervisor: Author: Peter Nilsson Jingou Lai Erik Hertz Rakesh Gangarajaiah Lund September 2, 2013 The Department of Electrical and Information Technology Lund University Box 118, S-221 00 LUND SWEDEN This thesis is set in Computer Modern 11pt, with the LATEX Documentation System © Jingou Lai 2013 Abstract This thesis presents a design that approximates the fractional part of the based two logarithm function by using Improved Parabolic Synthesis including its CMOS VLSI implementations. Improved Parabolic Synthesis is a novel methodology in favor of implementing unary functions e.g. trigonometric, logarithm, square root etc. in hardware. It is an evolved approach from Parabolic Synthesis by combining it with Second-Degree Interpolation. In the thesis, the design explores a simple and parallel architecture for fast timing and optimizes wordlengths in computing stages for a small design. The error behavior of the design is described and char- acterized to meet the desired error metrics. This implementation is compared to other approaches e.g. Parabolic Synthesis and CORDIC using 65nm standard cell libraries and it is proved to have better performance in terms of smaller chip area, lower dynamic power, and shorter critical path. iv Acknowledgments This thesis would not have been possible without the support from many people. I would like to express my deepest gratitude to the supervisors, Peter Nilsson, Erik Hertz, and Rakesh Gangarajaiah who patiently, inspiringly guided me through this thesis work. My special thanks would go to my families and dearest friends who always have faith in me and encourage me. -

Comparing Time Complexity of Algorithms from Chapter 3, Standard Notation and Common Functions
Comparing time complexity of algorithms From Chapter 3, standard notation and common functions: • When the base of a log is not mentioned, it is assumed to be base 2. • Analogy between comparisons of functions f(n) and g(n) and comparisons of real num- bers a and b: f(n) = O(g(n)) is like a ≤ b f(n) = Ω(g(n)) is like a ≥ b f(n) = Θ(g(n)) is like a = b f(n) = o(g(n)) is like a < b f(n) = !(g(n)) is like a > b • A polynomial of degree d is Θ(nd). • For all real constants a and b such that a > 1; b > 0; nb lim = 0 x!1 an so nb = o(an). Any exponential function with a base > 1 grows faster than any poly- nomial function. • Notation used for common logarithms: lgn = log2n (binary logarithm) lnn = logen (natural logarithm) • More logarithmic facts: For all real a > 0; b > 0; c > 0, and n, a = b(logba) // Ex: 2(lgn) = n(lg2) = n n logba = nlogba y logbx = y iff x = b logba = (logca)=(logcb) // the base of the log doesn't matter asymptotically a(logbc) = c(logba) lgbn = o(na) // any polynomial grows faster than any polylogarithm n! = o(nn) // factorial grows slower than nn n! = !(2n) // factorial grows faster than exponential with base ≥ 2 lg(n!) = Θ(nlgn) // Stirling's rule 1 • Iterated logarithm function: lg∗n (log star of n) lg(i)n is the log function applied i times in succession. lg∗n = min(i ≥ 0 such that lg(i)n ≤ 1) x lg∗x (−∞; 1] 0 (1; 2] 1 (2; 4] 2 (4; 16] 3 (16; 65536] 4 (65536; 265536] 5 lg∗2 = 1 lg∗4 = 2 lg∗16 = 3 lg∗65536 = 4 Very slow-growing function. -

Algorithms and Data Structures CS 372
Algorithms and Data Structures CS 372 Asymptotic notations (Based on slides by M. Nicolescu) Algorithm Analysis • The amount of resources used by the algorithm –Space – Computational time • Running time: – The number of primitive operations (steps) executed before termination • Order of growth – The leading term of a formula – Expresses the behavior of a function toward infinity 2 Asymptotic Notations • A way to describe behavior of functions in the limit – How we indicate running times of algorithms – Describe the running time of an algorithm as n grows to ∞ • O notation: asymptotic “less than”: f(n) “≤”g(n) • Ω notation: asymptotic “greater than”: f(n) “≥”g(n) • Θ notation: asymptotic “equality”: f(n) “=” g(n) 3 1 Logarithms • In algorithm analysis we often use the notation “log n” without specifying the base y y log x Binary logarithm lgn = log2 n log x = Natural logarithm ln n = loge n log xy = log x + log y x lgk n = (lg n)k log = log x − log y y lglgn = lg(lgn) loga x = loga blogb x alogb x = xlogb a 4 Asymptotic notations •O-notation • Intuitively: O(g(n)) = the set of functions with a smaller or same order of growth as g(n) 5 Examples 2 3 2 3 –2n = O(n ): 2n ≤ cn ⇒ 2 ≤ cn ⇒ c = 1 and n0= 2 2 2 2 2 –n= O(n ): n ≤ cn ⇒ c ≥ 1 ⇒ c = 1 and n0= 1 – 1000n2+1000n = O(n2): 2 2 2 2 1000n +1000n ≤ 1000n +1000n =2000n ⇒ c=2000 and n0 = 1 2 2 –n = O(n): n ≤ cn ⇒ cn ≥ 1 ⇒ c = 1 and n0= 1 6 2 Asymptotic notations (cont.) • Ω -notation • Intuitively: Ω(g(n)) = the set of functions with a larger or same order of growth as g(n) 7 Examples – 5n2 -
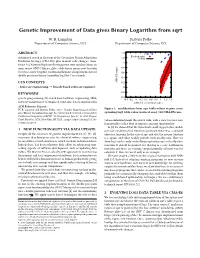
Genetic Improvement of Data Gives Binary Logarithm from Sqrt
Genetic Improvement of Data gives Binary Logarithm from sqrt W. B. Langdon Justyna Petke Department of Computer Science, UCL Department of Computer Science, UCL 1.4 ABSTRACT x Evolved value Automated search in the form of the Covariance Matrix Adaptation 1.2 Theory Evolution Strategy (CMA-ES), plus manual code changes, trans- 1 forms 512 Newton-Raphson floating point start numbers from an open source GNU C library, glibc, table driven square root function 0.8 to create a new bespoke custom mathematical implementation of 0.6 double precision binary logarithm log2 for C in seconds. 0.4 CCS CONCEPTS CMA-ES output 0.2 • Software engineering → Search-based software engineer; 0 KEYWORDS -0.2 -0.4 genetic programming, GI, search based software engineering, SBSE, -0.4 -0.2 0 0.2 0.4 0.6 0.8 1 1.2 1.4 software maintenance of empirical constants, data transplantation CMA-ES seeded from sqrt_t ACM Reference Format: W. B. Langdon and Justyna Petke. 2019. Genetic Improvement of Data Figure 1: modification from sqrt table values to give corre- gives Binary Logarithm from sqrt. In Genetic and Evolutionary Computation sponding log2 table value (vertical axis). 512 CMA-ES runs. Conference Companion (GECCO ’19 Companion), July 13–17, 2019, Prague, Czech Republic. ACM, New York, NY, USA, 2 pages. https://doi.org/10.1145/ values embedded inside the source code, with a view to create new 3319619.3321954 functionality rather than to improve existing functionality. In [4] we claimed that the framework could support other double 1 NEW FUNCTIONALITY VIA DATA UPDATE precision mathematical functions provided there was a suitable Despite all the successes of genetic improvement GI [7], [3], [6], objective function.