Internet Gambling Investigations Ω
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Poster: Introducing Massbrowser: a Censorship Circumvention System Run by the Masses
Poster: Introducing MassBrowser: A Censorship Circumvention System Run by the Masses Milad Nasr∗, Anonymous∗, and Amir Houmansadr University of Massachusetts Amherst fmilad,[email protected] ∗Equal contribution Abstract—We will present a new censorship circumvention sys- side the censorship regions, which relay the Internet traffic tem, currently being developed in our group. The new system of the censored users. This includes systems like Tor, VPNs, is called MassBrowser, and combines several techniques from Psiphon, etc. Unfortunately, such circumvention systems are state-of-the-art censorship studies to design a hard-to-block, easily blocked by the censors by enumerating their limited practical censorship circumvention system. MassBrowser is a set of proxy server IP addresses [14]. (2) Costly to operate: one-hop proxy system where the proxies are volunteer Internet To resist proxy blocking by the censors, recent circumven- users in the free world. The power of MassBrowser comes from tion systems have started to deploy the proxies on shared-IP the large number of volunteer proxies who frequently change platforms such as CDNs, App Engines, and Cloud Storage, their IP addresses as the volunteer users move to different a technique broadly referred to as domain fronting [3]. networks. To get a large number of volunteer proxies, we This mechanism, however, is prohibitively expensive [11] provide the volunteers the control over how their computers to operate for large scales of users. (3) Poor QoS: Proxy- are used by the censored users. Particularly, the volunteer based circumvention systems like Tor and it’s variants suffer users can decide what websites they will proxy for censored from low quality of service (e.g., high latencies and low users, and how much bandwidth they will allocate. -

Network Working Group T. Berners-Lee Request for Comments: 3986 W3C/MIT STD: 66 R
Network Working Group T. Berners-Lee Request for Comments: 3986 W3C/MIT STD: 66 R. Fielding Updates: 1738 Day Software Obsoletes: 2732, 2396, 1808 L. Masinter Category: Standards Track Adobe Systems January 2005 Uniform Resource Identifier (URI): Generic Syntax Status of This Memo This document specifies an Internet standards track protocol for the Internet community, and requests discussion and suggestions for improvements. Please refer to the current edition of the "Internet Official Protocol Standards" (STD 1) for the standardization state and status of this protocol. Distribution of this memo is unlimited. Copyright Notice Copyright (C) The Internet Society (2005). Abstract A Uniform Resource Identifier (URI) is a compact sequence of characters that identifies an abstract or physical resource. This specification defines the generic URI syntax and a process for resolving URI references that might be in relative form, along with guidelines and security considerations for the use of URIs on the Internet. The URI syntax defines a grammar that is a superset of all valid URIs, allowing an implementation to parse the common components of a URI reference without knowing the scheme-specific requirements of every possible identifier. This specification does not define a generative grammar for URIs; that task is performed by the individual specifications of each URI scheme. Berners-Lee, et al. Standards Track [Page 1] RFC 3986 URI Generic Syntax January 2005 Table of Contents 1. Introduction . 4 1.1. Overview of URIs . 4 1.1.1. Generic Syntax . 6 1.1.2. Examples . 7 1.1.3. URI, URL, and URN . 7 1.2. Design Considerations . -

A Framework for Auto-ID Enabled Business
A Framework for Auto-ID Enabled Business by Timothy Porter Milne M.S. Mechanical Engineering, 1995 Brigham Young University B.S. Mechanical Engineering, 1992 Brigham Young University Submitted to the Department of Mechanical Engineering in partial fulfillment of the requirements for the degree of MASTER OF SCIENCE at the MASSACHUSETTS INSTITUTE OF TECHNOLOGY MASSACHUSETTS INSTITUTEINSTITUTE August 8, 2003 OF TECHNOL OGY OCT 0 6 ©2003 Massachusetts Institute of Technology All Rights Reserved. LIBRAR IES Signature of Author:................................ ....... .. ............. Departm of Mechanic Engineering (V August 8, 2003 C ertified by:............................................... Sanjay E. Sarma Associat e Professor of Mechanical Engineering Thesis Supervisor A ccepted by:......................................... Ain A. Sonin Chairman, Department Committee on Graduate Students BARKER A Framework for Auto-ID Enabled Business by Timothy Porter Milne Submitted to the Department of Mechanical Engineering August 8, 2003 In partial fulfillment of the requirements for the degree of Master of Science ABSTRACT Modern commerce is as much about trading information as it is about exchanging goods and money. With an Auto-ID enabled future, the expeditious exchange of information will be even more critical. The fundamental problem with e-commerce today is the soft connection between goods and their related information, which frequently results in breakdowns between the physical and information worlds. The Auto-ID Center at MIT has proposed a system using Radio Frequency Identification (RFID) tags on objects, coupled with a distributed information system using the Internet, that will allow the tracking of physical objects and the automatic association of relevant data about those objects. This thesis outlines a framework for a new method of using Auto-ID to connect the physical world to the information world using an example from commerce: Shipping and Receiving Verification. -

In Computer Networks, A
Practical No.1 Date:- Title:- Installation of Proxy-Server Windows Server 2003 What is proxy server? In computer networks, a proxy server is a server (a computer system or an application program) that acts as an intermediary for requests from clients seeking resources from other servers. A client connects to the proxy server, requesting some service, such as a file, connection, web page, or other resource, available from a different server. The proxy server evaluates the request according to its filtering rules. For example, it may filter traffic by IP address or protocol. If the request is validated by the filter, the proxy provides the resource by connecting to the relevant server and requesting the service on behalf of the client. A proxy server may optionally alter the client's request or the server's response, and sometimes it may serve the request wit hout contacting the specified server. In this case, it 'caches' responses from the remote server, and returns subsequent requests for the same content directly . Most proxies are a web proxy, allowing access to content on the World Wide Web. A proxy server has a large variety of potential purposes, including: To keep machines behind it anonymous (mainly for security).[1] To speed up access to resources (using caching). Web proxies are commonly used to cache web pages from a web server.[2] To apply access policy to network services or content, e.g. to block undesired sites. To log / audit usage, i.e. to provide company employee Internet usage reporting. To bypass security/ parental controls. To scan transmitted content for malware before delivery. -

FAA-STD-075, Creating Service Identifiers
FAA-STD-075 June 29, 2021 SUPERSEDING FAA-STD-063 May 1, 2009 U.S. Department of Transportation Federal Aviation Administration U.S. Department of Transportation Federal Aviation Administration Standard Practice CREATING SERVICE IDENTIFIERS FAA-STD-075 June 29, 2021 FOREWORD This standard is approved for use by all Departments of the Federal Aviation Administration (FAA). This standard sets forth requirements for creating globally-unique identifiers for FAA service-oriented architecture (SOA)-based services. This standard has been prepared in accordance with FAA-STD-068, Department of Transportation Federal Aviation Administration, Preparation of Standards [STD068]. Comments, suggestions, or questions on this document shall be addressed to: Federal Aviation Administration System Wide Information Management (SWIM) Program Office, AJM-316 800 Independence Avenue, SW Washington, DC 20591 https://www.faa.gov/air_traffic/technology/swim/contacts/ i FAA-STD-075 June 29, 2021 Table of Contents 1 SCOPE ..................................................................................................................................................1 1.1 INTRODUCTION ...........................................................................................................................................1 1.2 INTENDED AUDIENCE ....................................................................................................................................1 1.3 BASIC CONCEPTS .........................................................................................................................................2 -

Globally Unique Flight Identifier (GUFI) Format and Content
Globally Unique Flight Identifier (GUFI) Format and Content A collaborative effort to establish the Flight Information Exchange Model (FIXM) has been underway for several years. A key component of the flight model is a Globally Unique Flight Identifier (GUFI) that is included on every Air Traffic Management (ATM) flight data transaction to unambiguously identify the flight to which the data applies. The June 23, purpose of the GUFI is to eliminate problems that have occurred in the past when 2014 systems try to accurately correlate data that is received from many other systems. This paper discusses the format and content of the GUFI. Version: 2.1 GUFI Format Version 2.1 Table of Contents Document History ........................................................................................................................................ 3 1 Introduction .......................................................................................................................................... 4 2 Background/Discussion ......................................................................................................................... 4 2.1 Purpose ..................................................................................................................................... 4 2.2 General Concept ....................................................................................................................... 4 2.3 General Approaches ................................................................................................................. -

Threat Modeling and Circumvention of Internet Censorship by David Fifield
Threat modeling and circumvention of Internet censorship By David Fifield A dissertation submitted in partial satisfaction of the requirements for the degree of Doctor of Philosophy in Computer Science in the Graduate Division of the University of California, Berkeley Committee in charge: Professor J.D. Tygar, Chair Professor Deirdre Mulligan Professor Vern Paxson Fall 2017 1 Abstract Threat modeling and circumvention of Internet censorship by David Fifield Doctor of Philosophy in Computer Science University of California, Berkeley Professor J.D. Tygar, Chair Research on Internet censorship is hampered by poor models of censor behavior. Censor models guide the development of circumvention systems, so it is important to get them right. A censor model should be understood not just as a set of capabilities|such as the ability to monitor network traffic—but as a set of priorities constrained by resource limitations. My research addresses the twin themes of modeling and circumvention. With a grounding in empirical research, I build up an abstract model of the circumvention problem and examine how to adapt it to concrete censorship challenges. I describe the results of experiments on censors that probe their strengths and weaknesses; specifically, on the subject of active probing to discover proxy servers, and on delays in their reaction to changes in circumvention. I present two circumvention designs: domain fronting, which derives its resistance to blocking from the censor's reluctance to block other useful services; and Snowflake, based on quickly changing peer-to-peer proxy servers. I hope to change the perception that the circumvention problem is a cat-and-mouse game that affords only incremental and temporary advancements. -

How to Download Torrent Anonymously How to Download Torrent Anonymously
how to download torrent anonymously How to download torrent anonymously. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. What can I do to prevent this in the future? If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. If you are at an office or shared network, you can ask the network administrator to run a scan across the network looking for misconfigured or infected devices. Another way to prevent getting this page in the future is to use Privacy Pass. You may need to download version 2.0 now from the Chrome Web Store. Cloudflare Ray ID: 66b6c3aaaba884c8 • Your IP : 188.246.226.140 • Performance & security by Cloudflare. Download Torrents Anonymously: 6 Safe And Easy Ways. Who doesn’t want to know how to download torrents anonymously? The thing is, in order to download torrents anonymously you don’t need to have a lot of technical know-how. All you need to download torrents anonymously is some grit and a computer with an internet connection. The technology world never remains the same. In fact, new development and discoveries come to the surface of this industry every day. They also come into the attention of online users every year. Moreover, this allows us to do much more than we could do in the past, in faster and easier ways. A highly relevant aspect to mention at this stage is that: Now we can also download torrents anonymously from best torrent sites. -

World-Wide Web Proxies
World-Wide Web Proxies Ari Luotonen, CERN Kevin Altis, Intel April 1994 Abstract 1.0 Introduction A WWW proxy server, proxy for short, provides access to The primary use of proxies is to allow access to the Web the Web for people on closed subnets who can only access from within a firewall (Fig. 1). A proxy is a special HTTP the Internet through a firewall machine. The hypertext [HTTP] server that typically runs on a firewall machine. server developed at CERN, cern_httpd, is capable of run- The proxy waits for a request from inside the firewall, for- ning as a proxy, providing seamless external access to wards the request to the remote server outside the firewall, HTTP, Gopher, WAIS and FTP. reads the response and then sends it back to the client. cern_httpd has had gateway features for a long time, but In the usual case, the same proxy is used by all the clients only this spring they were extended to support all the within a given subnet. This makes it possible for the proxy methods in the HTTP protocol used by WWW clients. Cli- to do efficient caching of documents that are requested by ents don’t lose any functionality by going through a proxy, a number of clients. except special processing they may have done for non- native Web protocols such as Gopher and FTP. The ability to cache documents also makes proxies attrac- tive to those not inside a firewall. Setting up a proxy server A brand new feature is caching performed by the proxy, is easy, and the most popular Web client programs already resulting in shorter response times after the first document have proxy support built in. -

Introduction to the Course
Introduction to the course 1 Introduzione alla programmazione web – Marco Ronchetti 2021 – Università di Trento Prerequirements § OOP + Java: essential! (Must have passed Linguaggi di Programmazione!) § Network fundamentals § Database § No need to already know HTML/HTTP etc. 2 Introduzione alla programmazione web – Marco Ronchetti 2021 – Università di Trento Topics § HTTP + HTML + CSS § Server side programming: PHP – Java, parameter passing, state problem… § Data access (DB) § Javascript – EcmaScript – Typescript § Patterns: MV* + … § AJAX/XML/JSON § JS frameworks/libraries: JQuery, (brief remarks on React, Angular…) § General considerations (accessibility, security…) 3 Introduzione alla programmazione web – Marco Ronchetti 2021 – Università di Trento We’ll use Piazza As soon as the dept Buys the licence For now we go with moodle (sigh) 4 Introduzione alla programmazione web – Marco Ronchetti 2021 – Università di Trento Exam § Similar to “Linguaggi di Programmazione – mod.1” § 1st part: output prediction of 8 brief code fragments + 8 true/fase questions (40 minutes) § 2nd part: small project development (4 hours) If possiBle, in presence. Else, Responsus+Moodle+VDI 5 Introduzione alla programmazione web – Marco Ronchetti 2021 – Università di Trento 6 Introduzione alla programmazione web – Marco Ronchetti 2021 – Università di Trento What is the difference between the Web and the Internet? 7 Introduzione alla programmazione web – Marco Ronchetti 2021 – Università di Trento What is the difference between the Web and the Internet? § "The -
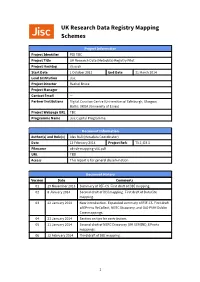
UK Research Data Registry Mapping Schemes
UK Research Data Registry Mapping Schemes Project Information Project Identifier PID TBC Project Title UK Research Data (Metadata) Registry Pilot Project Hashtag #jiscrdr Start Date 1 October 2013 End Date 31 March 2014 Lead Institution Jisc Project Director Rachel Bruce Project Manager — Contact Email — Partner Institutions Digital Curation Centre (Universities of Edinburgh, Glasgow, Bath); UKDA (University of Essex) Project Webpage URL TBC Programme Name Jisc Capital Programme Document Information Author(s) and Role(s) Alex Ball (Metadata Coordinator) Date 12 February 2014 Project Refs T3.1; D3.1 Filename uk-rdr-mapping-v06.pdf URL TBD Access This report is for general dissemination Document History Version Date Comments 01 29 November 2013 Summary of RIF-CS. First draft of DDI mapping. 02 8 January 2014 Second draft of DDI mapping. First draft of DataCite mapping. 03 22 January 2014 New introduction. Expanded summary of RIF-CS. First draft of EPrints ReCollect, NERC Discovery, and OAI-PMH Dublin Core mappings. 04 23 January 2014 Section on tips for contributors. 05 31 January 2014 Second draft of NERC Discovery (UK GEMINI), EPrints mappings. 06 12 February 2014 Third draft of DDI mapping. 1 Contents 1 Introduction 3 1.1 Typographical conventions . 3 2 RIF-CS 4 2.1 Elements . 4 2.2 Controlled vocabularies . 8 3 Internally managed RIF-CS elements 20 4 Mapping from DDI to RIF-CS 21 4.1 Related Objects . 22 5 Mapping from UK GEMINI 2 to RIF-CS 24 5.1 Related Objects . 26 6 Mapping from DataCite to RIF-CS 27 6.1 Related Objects . -

Technical and Legal Overview of the Tor Anonymity Network
Emin Çalışkan, Tomáš Minárik, Anna-Maria Osula Technical and Legal Overview of the Tor Anonymity Network Tallinn 2015 This publication is a product of the NATO Cooperative Cyber Defence Centre of Excellence (the Centre). It does not necessarily reflect the policy or the opinion of the Centre or NATO. The Centre may not be held responsible for any loss or harm arising from the use of information contained in this publication and is not responsible for the content of the external sources, including external websites referenced in this publication. Digital or hard copies of this publication may be produced for internal use within NATO and for personal or educational use when for non- profit and non-commercial purpose, provided that copies bear a full citation. www.ccdcoe.org [email protected] 1 Technical and Legal Overview of the Tor Anonymity Network 1. Introduction .................................................................................................................................... 3 2. Tor and Internet Filtering Circumvention ....................................................................................... 4 2.1. Technical Methods .................................................................................................................. 4 2.1.1. Proxy ................................................................................................................................ 4 2.1.2. Tunnelling/Virtual Private Networks ............................................................................... 5