Hacking Leopard: Tools and Techniques for Attacking the Newest Mac OS X
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

System Profile
Steve Sample’s Power Mac G5 6/16/08 9:13 AM Hardware: Hardware Overview: Model Name: Power Mac G5 Model Identifier: PowerMac11,2 Processor Name: PowerPC G5 (1.1) Processor Speed: 2.3 GHz Number Of CPUs: 2 L2 Cache (per CPU): 1 MB Memory: 12 GB Bus Speed: 1.15 GHz Boot ROM Version: 5.2.7f1 Serial Number: G86032WBUUZ Network: Built-in Ethernet 1: Type: Ethernet Hardware: Ethernet BSD Device Name: en0 IPv4 Addresses: 192.168.1.3 IPv4: Addresses: 192.168.1.3 Configuration Method: DHCP Interface Name: en0 NetworkSignature: IPv4.Router=192.168.1.1;IPv4.RouterHardwareAddress=00:0f:b5:5b:8d:a4 Router: 192.168.1.1 Subnet Masks: 255.255.255.0 IPv6: Configuration Method: Automatic DNS: Server Addresses: 192.168.1.1 DHCP Server Responses: Domain Name Servers: 192.168.1.1 Lease Duration (seconds): 0 DHCP Message Type: 0x05 Routers: 192.168.1.1 Server Identifier: 192.168.1.1 Subnet Mask: 255.255.255.0 Proxies: Proxy Configuration Method: Manual Exclude Simple Hostnames: 0 FTP Passive Mode: Yes Auto Discovery Enabled: No Ethernet: MAC Address: 00:14:51:67:fa:04 Media Options: Full Duplex, flow-control Media Subtype: 100baseTX Built-in Ethernet 2: Type: Ethernet Hardware: Ethernet BSD Device Name: en1 IPv4 Addresses: 169.254.39.164 IPv4: Addresses: 169.254.39.164 Configuration Method: DHCP Interface Name: en1 Subnet Masks: 255.255.0.0 IPv6: Configuration Method: Automatic AppleTalk: Configuration Method: Node Default Zone: * Interface Name: en1 Network ID: 65460 Node ID: 139 Proxies: Proxy Configuration Method: Manual Exclude Simple Hostnames: 0 FTP Passive Mode: -

Mis Chuletas De Mac OS X Impreso El 9 De Junio De 2009, a Las 11:03 Horas
Mis chuletas de Mac OS X Impreso el 9 de junio de 2009, a las 11:03 horas Índice 1 Versiones de Mac OS X 2 2 Hardware 2 2.1 MacBook casa 2 2.2 iMac trabajo 2 3 Uso 2 3.1 Atajos de teclado 2 3.2 Terminal (y comandos) 3 3.3 Aplicación por defecto 3 3.4 Arranque 4 3.4.1 Modo usuario único 4 3.4.2 Modo seguro 4 3.4.3 Arranque múltiple 4 3.4.4 Arranque de unidad de CD/DVD 4 3.5 Capturas de pantalla 4 3.5.1 Captura de pantalla de ordenador remoto 4 3.6 Redes mixtas: Windows 4 3.6.1 Compartiendo FAT32 y NTFS con Samba 5 3.7 Cambio de nombre de carpeta en red 5 3.8 Buscando símbolos 6 3.9 Dos instancias simultáneas de una aplicación 6 3.10 Finder 6 3.10.1 Atajo a carpeta superior 6 3.10.2 Ordena alfabéticamente 6 3.10.3 Ruta en Finder 6 3.10.4 Preferencias vista columnas 7 3.11 Vista previa 7 3.11.1 Añadir extensiones 7 3.11.2 Ver pdf inmediatamente o descargarlo 7 3.11.3 Zoom en modo vista previa 7 3.11.4 Crear pdf multipáginas desde imágenes en Vista Previa 7 3.12 Calendarios 8 3.12.1 Mezclar múltiples calendarios en uno 8 3.12.2 Sincronizar iCal y Google Calendar 8 3.13 Opciones avanzadas en cuentas 8 3.14 Correo 8 3.14.1 Thunderbird es indexado por Spotlight 8 3.14.2 Reparar índice en Mail 8 3.14.3 Correos con CCO (con copia oculta) 8 3.14.4 Copia del perfil de Mail 8 3.14.5 MS Entourage 9 3.15 Conexión a escritorio remoto 9 3.16 Añadir radios a iTunes 9 3.17 CD / DVD 9 3.17.1 Quemar un DVD-Video 9 3.17.2 Pasdar de .iso a .dmg y al revés 9 3.17.3 Crear una imagen ISO 9 3.18 Borrado seguro espacio libre 10 3.19 Borrar todas las papeleras de -

Vcenter Server Upgrade
vCenter Server Upgrade Update 2 VMware vSphere 7.0 vCenter Server 7.0 vCenter Server Upgrade You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ VMware, Inc. 3401 Hillview Ave. Palo Alto, CA 94304 www.vmware.com © Copyright 2018-2021 VMware, Inc. All rights reserved. Copyright and trademark information. VMware, Inc. 2 Contents 1 About vCenter Server Upgrade 7 2 vCenter Server Upgrade Options 8 Overview of the vSphere Upgrade Process 8 Overview of the vCenter Server Upgrade Process 10 vCenter Server Upgrade Compatibility 12 vCenter Server 7.0 Component Behavior Changes That Affect Upgrade 13 Removal of Platform Services Controller 14 Upgrade or Migration for vCenter Server Instances with an External Platform Services Controller 14 Upgrading or Migrating to vSphere License Service 15 Upgrading the Trust Authority vCenter Server 16 Differences Between vSphere Upgrades, Patches, Updates, and Migrations 16 Support for Upgrading a vCenter Server with Multi-Homing 17 Support for Federal Information Processing Standard 140-2 17 Support for Transport Security Layer 1.2 17 Moving from a Deprecated to a Supported vCenter Server Deployment Topology Before Upgrade or Migration 18 Example Upgrade Paths from vCenter Server 6.5 and 6.7 to vCenter Server 7.0 19 Example Migration Paths from vCenter Server for Windows to vCenter Server 7.0 20 3 Upgrading the vCenter Server Appliance 22 About the Upgrade Process of the vCenter Server Appliance 24 System Requirements for the New vCenter Server Appliance -

INSTALLING the PRINT DRIVER Ignore the Detailed Instructions: PRINTING
INSTALLING THE PRINT DRIVER Ignore the detailed instructions: PRINTING To print wirelessly from your Mac at SMPL, In any program, print as you would you must install a driver. This will only work normally. When the Print dialog box with Mac OS 10.4 or later (Tiger or appears, the printer you chose will be one Leopard). of your choices: Go to www.smpl.org/depts/im/WiFiPrinting.html Choose the first or second floor location and click MacOS . Choose Open with DiskImageMounter in the dialog box: SMPL has already customized this software for our network. Click Continue. When the installer finishes, you are ready to print. If you’d like to verify your installation, open System Preferences: Select it, and click Print. This will mount the disk image Choose Print & Fax and Choose a name and password (optional) Popup 8.0: look for Mac_WiFi_Printer or for your document and click Print again to 2nd_Floor_Mac_Wifi_Printer on your list of send it off: printers: The installer is inside: Double click to launch it, then click through the menus. Note: Passwords are case sensitive. TO GET YOUR PRINT JOB Wi-Fi Printing There are two locations: 1st Floor Copy Santa Monica Public Center and 2nd Floor to the left of the UNINSTALLING THE PRINT DRIVER Reference Desk. Insert your library card Main Library or print card into the box located next If you plan to print at SMPL in the future, to the printer. you can leave the driver installed. It is very small and will not affect your computer’s other functions. -

Semester 1 2018 - 2019
Computer Science 2018 - 2019, Semester 1 - MAC Lab Software Semester 1 2018 - 2019 MacOS 10.11.6 El Capitan 50onPaletteServer 1.1.0 ABAssistandService 9.0 Accessibility Inspector 4.1 Activity Monitor 10.11 AddPrinter 11.4 AddressBook Manager 9.0 AddressBookSourceSync 9.0 AddressBookSync 9.0 AddressBookUrlForwarder 9.0 Adobe Flash Player Install Manager 29.0.0.113 AinuIM 1.0 AirPlayUIAgent 2.0 AirPort Base Station Agent 2.2.1 AirPort Utility 6.3.6 AirScanLegacyDiscovery 11.4 AirScanScanner 11.0 AOSAlertManager 1.07 AOSHeartbeat 1.07 AOSPushRelay 1.07 App Store 2.1 AppDownloadLauncher 1.0 AppleFileServer 2.0 AppleGraphicsWarning 2.3.0 AppleMobileDeviceHelper 5.0 AppleMobileSync 5.0 AppleScript Utility 1.1.2 Application Loader 3.5 Archive Utility 10.10 ARDAgent 3.8.5 AskPermissionUI 1.0 Assistant Audio MIDI Setup 3.0.6 AuthManager_Mac 5.0.0 Autoimporter 6.7 Automator 2.6 Automator Runner 2.6 AVB Audio Configuration 1.0 Bluetooth File Exchange 4.4.6 Bluetooth Setup Assistant 4.4.6 BluetoothUIServer 4.4.6 Boot Camp Assistant 6.0.1 Page 1 of 8 Computer Science 2018 - 2019, Semester 1 - MAC Lab Software Build Web Page 10.1 Calculator 10.8 Calendar 8.0 CalendarFileHandler 8.0 Calibration Assistant 1.0 Canon IJ Printer Utility 10.42.1 Canon IJ Printer Utility 7.27.0 Canon IJScanner2 4.0.0 Canon IJScanner4 4.0.0 Canon IJScanner6 4.0.0 Captive Network Assistant 4.1 CertificateAssistant 5.0 CharacterPalette 2.0.1 check_afp 4.0 Chess 3.13 ChineseTextConverterService 2.1 CIMFindInputCodeTool -

ISO Disk Image Primer
ISO Disk Image Primer Overview Topic Description File Extension .iso MIME Type CD-ROM: application/x-iso9660-image CD-ROM or CD-R: application/x-iso 13490-image DVD/Blu-Ray: application/x-iso13346-image Structure Binary file Versions n/a Primary fields or areas of use .iso can exist in every field of research where data and associated executable programs have been historically distributed on optical discs (CD, DVD, etc.) Source and affiliation Name derived from ISO 9660 file system used with CD-ROM media Metadata standards n/a Key questions for curation review ● What software is required to access the data? ○ Is required (proprietary) software contained in the disk image? ○ Must any required software/hardware be emulated? ● Are data files linked in other ways? ● Is there documentation about each file and their relationships? Tools for curation review Bitcurator1, Tree2, FRED machine 1 See https://confluence.educopia.org/display/BC/BitCurator+Environment 2 Command to produce a recursive directory listing; see https://en.wikipedia.org/wiki/Tree_(command) 1 ISO Disk Image Primer Date Created 2020 Created by Kate Barron (Stanford University) Jonathan Bohan (Cornell Institute for Social and Economic Research) Mentor: Cynthia Hudson-Vitale (Pennsylvania State University) Date updated and summary of N/A changes made Suggested Citation: Barron, Kate and Jonathan Bohan. (2020). ISO Disk Image Data Curation Primer. http://hdl.handle.net/11299/216581. This work was created as part of the “Specialized Data Curation” Workshop #3 held at Washington University in St. Louis in St. Louis, MO on November 5-6, 2019. These workshops have been generously funded by the Institute of Museum and Library Services # RE-85-18-0040-18. -

Download and Install Rootsmagic for Mac
Download and Install RootsMagic for Mac This Magic Guide covers: A. Finding the RootsMagic Installer on RootsMagic.com B. Downloading with Safari C. Downloading with Google Chrome D. Installing RootsMagic E. Adding the RootsMagic shortcut icon to your Dock F. Registering Your Software NOTE: The first few steps of this handout apply to any web browser you use. Likewise, the installation process is identical no matter which web browser you used to download the software. It is only after you click the option to download the RootsMagic (RM) installer, that the web browser takes over and the processes varies from browser to browser. Therefore, there will only be one set of instructions for finding the installer and for installing the program. Separate download instructions will be provided for Safari and Google Chrome. A. Finding the RootsMagic Installer on RootsMagic.com 1. Open the web browser of your choice and go to http://rootsmagic.com/download/. 2. Find the RootsMagic 7 download link. 3. Click “Download”. Download and Install RootsMagic for Mac 12 August 2016 Page 1 4. The “Download RootsMagic 7 window will open. 5. Click on the link to start the download. This ends the instructions for finding the installer. You may proceed to the download instructions for the browser of your choice. B. Downloading with Safari 1. After clicking on the “RootsMagic for Mac Installer” link, the download process indicator will appear in the upper right corner of the screen. 2. Once the download process is finished, the icon will change to a gray circle with a white arrow pointing down. -

Copyrighted Material
4354indx.fm Page 427 Wednesday, October 20, 2004 10:58 AM Index Note to the reader: Throughout this index boldfaced page numbers indicate primary discussions of a topic. Italicized page numbers indicate illustrations. Symbols A Applications folder, 161 - (dash), in file names, 51 absolute mode for chmod command, 299 utilities subfolder, 1 !$ shortcut, for substituting arguments, 140 changing permissions, 300–301 apropos command, 41 !! command, 140 and sticky bit, 304 man page for, 44 ! (exclamation point) absolute paths, 53–55 overview, 42 for negating commands, 194 for cd command, 77 archives as shortcut for commands, 144 for symbolic links, 114 adding multiple files to, 264 # symbol for comments accented characters, in file names, 52 disk images for, 270–275 in /etc/sudoers file, 315 active memory, 363 finding text in compressed, 185 in crontab file, 418 Activity Monitor, 367 tar to create, 267–269 in .tcshrc file, 411 administrator accounts, 278–279 arguments for commands, 4, 35, 38–39 $ (prompt character), 2, 13 password for cloning Mac OS X command editing to change, 141 % prompt, 13 startup volume, 126 shortcut for substituting, 140 * (asterisk) as wildcard, 52, 192–193 and sudo command, 306 arrow key shortcuts, 150 cp (copy) command with, 100 –101 administrator processes, 361 asr (Apple Software Restore) command, 393 in find command, 172 Aladdin’s StuffIt, 261, 269 asterisk (*) as wildcard, 52, 192–193 in ls listing, 64 alerts, bell or flashing window as, 17 cp (copy) command with, 100 –101 in wc command, 212 aliases, 112–118 in find command, 172 . (dot) for combining commands, 420–421 in ls listing, 64 for current directory, 7 and command line, 114–115 in wc command, 212 as initial directory file, 79, 81 with open command, 156 attributes for files leading, in file names, 53, 64 properties and usage, 117 GetFileInfo command to return, . -

TURING SOFTWARE Note: Turing-PC Is a Dual-Boot Windows 7 and Windows XP Machine. Turing-PC
TURING SOFTWARE Note: Turing-PC is a Dual-Boot Windows 7 and Windows XP machine. Turing-PC (Windows 7) Turing-PC (Windows XP) Turing-Macmini Turing-PC as of 4/19/12 5:45 PM (DUAL BOOT: WINDOWS XP and WINDOWS 7) WINDOWS 7 SOFTWARE ==================== Commonly Used Programs: - Microsoft Office 2010 (Word, Excel, PowerPoint, Access) - Adobe Reader X - NotePad ++ - FireFox 3.6 - Internet Explorer 9 Complete List: Adobe Reader X (10.1.2) Ver: 10.1.2 Installed: 3/2/2012 Apple Application Support Ver: 2.0.1 Installed: 8/12/2011 Apple Software Update Ver: 2.1.3.127 Installed: 8/12/2011 Definition Update for Microsoft Office 2010 (KB982726) 32-Bit Edition Google Toolbar for Internet Explorer Ver: 1.0.0 Installed: 3/24/2010 Google Toolbar for Internet Explorer Ver: 7.3.2710.138 Google Update Helper Ver: 1.3.21.111 Installed: 3/30/2012 Installed Program Printer 1.5.0 InstEd 1.5.12.21 Ver: 1.5.12.21 Installed: 5/13/2011 Java Auto Updater Ver: 2.0.6.1 Installed: 9/28/2011 Java(TM) 6 Update 27 Ver: 6.0.270 Installed: 9/28/2011 Juniper Networks Network Connect 7.0.0 Ver: 7.0.0.17289 Microsoft Office Access MUI (English) 2010 Ver: 14.0.6029.1000 Installed: 1/27/2012 Microsoft Office Access Setup Metadata MUI (English) 2010 Ver: 14.0.6029.1000 Installed: 1/27/2012 Microsoft Office Excel MUI (English) 2010 Ver: 14.0.6029.1000 Installed: 1/27/2012 Microsoft Office Groove MUI (English) 2010 Ver: 14.0.6029.1000 Installed: 1/27/2012 Microsoft Office InfoPath MUI (English) 2010 Ver: 14.0.6029.1000 Installed: 1/27/2012 Microsoft Office OneNote MUI (English) 2010 Ver: -

Download and Install Personal Historian 2 for Mac
Download and Install Personal Historian 2 for Mac This Magic Guide covers: A. Finding the Personal Historian 2 Installer on RootsMagic.com B. Downloading with Safari C. Downloading with Google Chrome D. Installing Personal Historian 2 E. Adding the Personal Historian 2 shortcut icon to your Dock F. Registering Your Software NOTE: The first few steps of this handout apply to any web browser you use. Likewise, the installation process is identical no matter which web browser you used to download the software. It is only after you click the option to download the Personal Historian 2 (PH 2) installer, that the web browser takes over and the processes varies from browser to browser. Therefore, there will only be one set of instructions for finding the installer and for installing the program. Separate download instructions will be provided for Safari and Google Chrome. A. Finding the Personal Historian 2 Installer on RootsMagic.com 1. Open the web browser of your choice and go to http://rootsmagic.com/download/. 2. Find the Personal Historian 2 download link. 3. Click “Download”. Download and Install PH 2 for Mac 12 August 2016 Page 1 4. The “Download Personal Historian 2” window will open. 5. Click on the link to start the download. This ends the instructions for finding the installer. You may proceed to the download instructions for the browser of your choice. B. Downloading with Safari 1. After clicking on the “Personal Historian 2 for Mac Installer” link, the download process indicator will appear in the upper right corner of the screen. -

Download and Install Family Atlas for Mac
Download and Install Family Atlas for Mac This Magic Guide covers: A. Finding the Family Atlas Installer on RootsMagic.com B. Downloading with Safari C. Downloading with Google Chrome D. Installing Family Atlas E. Adding the Family Atlas shortcut icon to your Dock F. Registering Your Software NOTE: The first few steps of this handout apply to any web browser you use. Likewise, the installation process is identical no matter which web browser you used to download the software. It is only after you click the option to download the Family Atlas (FA) installer, that the web browser takes over and the processes varies from browser to browser. Therefore, there will only be one set of instructions for finding the installer and for installing the program. Separate download instructions will be provided for Safari and Google Chrome. A. Finding the Family Atlas Installer on RootsMagic.com 1. Open the web browser of your choice and go to http://rootsmagic.com/download/. 2. Find the Family Atlas download link. 3. Click “Download”. Download and Install Family Atlas for Mac 12 August 2016 Page 1 4. The “Download Family Atlas window will open. 5. Click on the link to start the download. This ends the instructions for finding the installer. You may proceed to the download instructions for the browser of your choice. B. Downloading with Safari 1. After clicking on the “Family Atlas for Mac Installer” link, the download process indicator will appear in the upper right corner of the screen. 2. Once the download process is finished, the icon will change to a gray circle with a white arrow pointing down. -
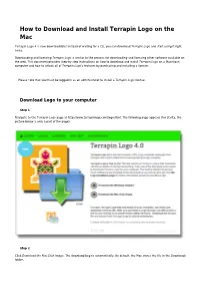
How to Download and Install Terrapin Logo on the Mac
How to Download and Install Terrapin Logo on the Mac Terrapin Logo 4 is now downloadable! Instead of waiting for a CD, you can download Terrapin Logo and start using it right away. Downloading and licensing Terrapin Logo is similar to the process for downloading and licensing other software available on the web. This document provides step-by-step instructions on how to download and install Terrapin Logo on a Macintosh computer and how to unlock all of Terrapin Logo's features by purchasing and installing a license. Please note that you must be logged in as an administrator to install a Terrapin Logo license. Download Logo to your computer Step 1 Navigate to the Terrapin Logo page at http://www.terrapinlogo.com/logo.html. The following page appears (for clarity, the picture below is only a part of the page): Step 2 Click Download the Mac Disk Image. The download begins automatically. By default, the Mac stores the file in the Downloads folder. Page 2 How to Download and Install Terrapin Logo on the Mac Step 3 When the download is complete, the Downloads folder contains the Terrapin Logo disk image file: Double click this file to mount and open the disk image. You will see the window below; it contains the Terrapin Logo program itself, a shortcut to your Applications folder, and three PDF manuals. Terrapin Documentation Printed on 2015/01/21 03:50 How to Download and Install Terrapin Logo on the Mac Page 3 If you see anything else, like for example, a window containing garbage as in the picture to the left, your Mac does not recognize DMG files as mountable disk images.