A Survey on Tor Encrypted Traffic Monitoring Using Machine Learning Techniques
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

<Document Title>
TLS Specification for Storage Systems Version 1.0.1 ABSTRACT: This document specifies the requirements and guidance for use of the Transport Layer Security (TLS) protocol in conjunction with data storage technologies. The requirements are intended to facilitate secure interoperability of storage clients and servers as well as non-storage technologies that may have similar interoperability needs. This document was developed with the expectation that future versions of SMI-S and CDMI could leverage these requirements to ensure consistency between these standards as well as to more rapidly adjust the security functionality in these standards. This document has been released and approved by the SNIA. The SNIA believes that the ideas, methodologies and technologies described in this document accurately represent the SNIA goals and are appropriate for widespread distribution. Suggestion for revision should be directed to http://www.snia.org/feedback/. SNIA Technical Position November 20, 2014 USAGE The SNIA hereby grants permission for individuals to use this document for personal use only, and for corporations and other business entities to use this document for internal use only (including internal copying, distribution, and display) provided that: 1. Any text, diagram, chart, table or definition reproduced shall be reproduced in its entirety with no alteration, and, 2. Any document, printed or electronic, in which material from this document (or any portion hereof) is reproduced shall acknowledge the SNIA copyright on that material, and shall credit the SNIA for granting permission for its reuse. Other than as explicitly provided above, you may not make any commercial use of this document, sell any or this entire document, or distribute this document to third parties. -

Tracking Users Across the Web Via TLS Session Resumption
Tracking Users across the Web via TLS Session Resumption Erik Sy Christian Burkert University of Hamburg University of Hamburg Hannes Federrath Mathias Fischer University of Hamburg University of Hamburg ABSTRACT modes, and browser extensions to restrict tracking practices such as User tracking on the Internet can come in various forms, e.g., via HTTP cookies. Browser fingerprinting got more difficult, as trackers cookies or by fingerprinting web browsers. A technique that got can hardly distinguish the fingerprints of mobile browsers. They are less attention so far is user tracking based on TLS and specifically often not as unique as their counterparts on desktop systems [4, 12]. based on the TLS session resumption mechanism. To the best of Tracking based on IP addresses is restricted because of NAT that our knowledge, we are the first that investigate the applicability of causes users to share public IP addresses and it cannot track devices TLS session resumption for user tracking. For that, we evaluated across different networks. As a result, trackers have an increased the configuration of 48 popular browsers and one million of the interest in additional methods for regaining the visibility on the most popular websites. Moreover, we present a so-called prolon- browsing habits of users. The result is a race of arms between gation attack, which allows extending the tracking period beyond trackers as well as privacy-aware users and browser vendors. the lifetime of the session resumption mechanism. To show that One novel tracking technique could be based on TLS session re- under the observed browser configurations tracking via TLS session sumption, which allows abbreviating TLS handshakes by leveraging resumptions is feasible, we also looked into DNS data to understand key material exchanged in an earlier TLS session. -

TLS Security Upgrade Effective Thursday, May 3, 2018
TLS Security Upgrade Effective Thursday, May 3, 2018 You May Need to Upgrade Your Browser/Operating System to Ensure Online and Mobile Banking Functionality. Apple Bank is informing you of a change to our security protocol. We will be officially retiring TLS 1.0 security protocol support on all of our services and upgrading to TLS 1.1 or higher to align with industry best practices and ensure that your data continues to be highly secure. TLS stands for “Transport Layer Security.” It is a protocol that provides privacy and data integrity between two communicating applications. It’s the most widely deployed security protocol used today, and is used for web browsers and other applications that require data to be securely exchanged over a network. On or before May 3, 2018, we will disable the TLS 1.0 encryption protocol, which may prevent users like you from accessing some or all of your online and mobile banking functionality. This means that you may need to upgrade your browser/operating system to disable TLS 1.0 and use TLS 1.1 or higher. This security upgrade will not affect you in any other way. We want to make this process as smooth as possible for you with specific instructions below. Our primary goal for users is to maintain the highest possible security standards and help keep your data secure. Depending on your browser/device, you may need to upgrade to the following versions that support TLS 1.1 or higher. Browser • Microsoft Internet Explorer (IE): version 11 and higher • Microsoft Edge: all versions • Mozilla Firefox: version -

Warptcptm SPDY
What Warp TCP TM does for SPDY WHITE PAPER Turbcharge Web Performance BADU networks - Improving the way the world connects - WarpTCP TM & SPDY Web performance is increasingly becoming a key focal point One among them is SPDY – a companion protocol to HTTP for many web properties. There are several approaches to that is aimed at reducing web page load latency and improv- help deliver rich, dynamic content with significantly lower ing web security among other things. latencies and improved user experience. Google’s “Make the Web Faster” initiative has proposed several techniques to This document describes how SPDY and Badu technology can improve web performance. These techniques are currently be combined to boost web performance. The approaches are being evaluated for inclusion in future standards. different but complementary to each other and can be implemented individually or together for maximum benefit. * The following diagram illustrates where SPDY and WarpTCP™ sit in the network protocol stack. Application Layer Web Cloud Computing Video File Transfer Amazon AWS HTML JS CSS H.264 MP4 Flash - EC2, S3 HTTP HTTP/REST/SOAP RTSP RTMP HLS FTP SCP SPDY Presentation Layer SSL Transport Layer WarpTCPTM SPDY SPDY operates at the Application/Session Layer. SPDY does not replace HTTP; it modifies the way HTTP requests and responses are sent over the Internet. This means that all the existing server-side applications can be used without modification if a SPDY-compatible translation layer is put in place. SPDY is similar to HTTP, with particular goals to reduce web page load latency and improve web security. SPDY achieves reduced latency through compression, multiplexing, and prioritization. -

The Fundamentals of Http/2 the Fundamentals of Http/2
Ali Jawad THE FUNDAMENTALS OF HTTP/2 THE FUNDAMENTALS OF HTTP/2 Ali Jawad Bachelor’s Thesis June 2016 Information Technology Oulu University of Applied Sciences ABSTRACT Oulu University of Applied Sciences Degree Programme, Option of Internet Services Author: Ali Jawad Title of the bachelor’s thesis: Fundamentals Of HTTP/2 Supervisor: Teemu Korpela Term and year of completion: June 2016 Number of pages: 31 The purpose of this Bachelor’s thesis was to research and study the new ver- sion of HTTP ”HTTP2.0”, which is considered to be the future of the web. Http/2 is drawing a great attention from the web industry. Most of the Http/2 features are inherited from SPDY. This thesis shows how HTTP/2 enables a more efficient use of network re- sources and a reduced perception of latency by introducing a header field com- pression and allowing multiple concurrent exchanges on the same connection ”multiplexing” and more other features. Also, it discusses the security of Http/2 and the new risks and dangerous at- tacks that resurfaces with the arrival of this new protocol version. The simulation results show how HTTP/2 influences the page load time compar- ing to the other previous versions of HTTP. Keywords: HTTP1, HTTP/2, SPDY, SNI, DOS, CRIME, Downgrade-attack. 3 PREFACE This thesis was written for Oulu University of Applied Sciences and done during 1 February – 23 May 2016. The role of the instructor was guiding the thesis from the requirements and bases of writing a thesis document through meet- ings. The role of the supervisor was instructing the thesis plan and its require- ments which were done by the author. -

Instructions for Setting TLS 1.2
Instructions for Setting TLS 1.2 In order to better protect your agency’s financial transactions, ASAP.gov is updating its minimum computer and internet browser requirements. Starting in August 2016, ASAP.gov will no longer support Transport Layer Security (TLS) 1.0 and 1.1. As a result, your computers need to use an operating system and internet browser that supports TLS 1.2. As outlined in the table below, organizations using Windows 7 or above must ensure their internet browsers support TLS 1.2. Computers using either a Windows XP or Vista operating system or an Internet Explorer version prior to version 8 will become unsupported. Minimum Computer Software Required to use ASAP.gov Software Supported Unsupported (no longer able to use ASAP.gov) Operating System Windows 7 and above Windows XP or Vista Internet Browser Browsers that support TLS 1.2 Internet Explorer version 7 or below The ASAP.gov team is providing this information now so you can start updating internet browsers and changing workstation security policies today. The following are a condensed list of instructions for adjusting the settings of supported internet browsers. Please communicate this change to your recipient organizations so they too can start today. Internet Explorer Instructions 1. Select [Tools] from the menu bar 2. Select [Internet Options] 3. Click on the [Advanced] tab. 4. Scroll down and determine if the “Use TLS v 1.0”, “Use TLS v 1.1”, and “Use TLS v 1.2” boxes are selected. If they are not selected, select them. This ensures your browser is able to use the most secure connection ASAP.gov. -

IT Security Guidelines for Transport Layer Security (TLS)
IT Security Guidelines for Transport Layer Security (TLS) National Cyber Security Centre The National Cyber Security Centre (NCSC), in collaboration with The following organizations and individuals have provided the business community, government bodies and academics, is valuable contributions: working to increase the ability of Dutch society to defend itself in - Autoriteit Persoonsgegevens the digital domain. - Belastingdienst - Centric The NCSC supports the central government and organisations in - Dienst Publiek en Communicatie the critical infrastructure sectors by providing them with expertise - Forum Standaardisatie and advice, incident response and with actions to strengthen crisis - IBD management. In addition, the NCSC provides information and - KPN advice to citizens, the government and the business community - NLnet Labs relating to awareness and prevention. The NCSC thus constitutes - Northwave the central reporting and information point for IT threats and - Platform Internetstandaarden security incidents. - RDW - SURFnet These IT Security Guidelines for Transport Layer Security were frst - de Volksbank published by the NCSC in 2014. This update (v2.1) was published in - Z-CERT 2021. See the appendix Changes to these guidelines for more details. - Daniel Kahn Gillmor, ACLU This publication was produced in collaboration with the following - Tanja Lange, Eindhoven University of Technology partners: - Kenny Paterson, ETH Zurich - the national communication security agency (NBV), part of the - Rich Salz, Akamai Technologies general -

The Effectiveness of the TOR Anonymity Network by David
The Effectiveness of the Tor Anonymity Network David Gingerich 68-590-K 11/30/2014 Abstract Recent reports of government agencies monitoring their own citizens’ internet activity has led to an increasing demand for anonymity on internet. The purpose of this project is to present the research and findings that relate to the reliability of the web anonymity network Tor. Tor works by relaying public internet traffic to a predetermined set of nodes that hide the original sender and receiver’s information from an individual's internet traffic as it travels over the internet. Each Tor node only knows which node the packet came from and where the packet is going. The project explains the core technologies that make Tor work as well as the various attacks that Tor is designed to circumvent. Tor’s roots as an anonymity project designed by the US Naval Laboratory intended to protect the identities of government employees working out of hostile territories, to its current status as a non-profit organization is detailed. The reader will be guided through an explanation of how Tor works, as well as how Tor’s hidden services allow for a website’s physical location to be hidden. The reader is also guided through various examples of when the Tor network’s integrity was faulted, as Tor is a common target of various US government agencies such as the National Security Agency (NSA) and the Federal Bureau of Investigation (FBI). Over the last several years many Tor users’ identities have been exposed due to various factors that were of their own makings. -

Interfaz USB De Red Para Acceso Seguro Basada En Raspberry Pi
Escola Tècnica Superior d’Enginyeria Informàtica Universitat Politècnica de València Interfaz USB de red para acceso seguro basada en Raspberry Pi Trabajo Fin de Grado Grado en Ingeniería Informática Autor: Jornet Calomarde, Raúl Tutor: Ripoll Ripoll, José Ismael Curso 2017-2018 Interfaz USB de red para acceso seguro basada en Raspberry Pi 2 Resumen El proyecto aborda el desarrollo de un dispositivo hardware basado en «Raspberry Pi Zero W» que sirve de punto de acceso a red y que proporciona diversas herramientas orientadas a la seguridad, tales como: firewall, control de intrusos, configuración de seguridad inalámbrica, proxies o auditoría de no- dos. La conectividad del dispositivo con el ordenador personal se establecerá únicamente mediante un cable USB a micro USB y será compatible con la mayoría de sistemas. El proyecto estará basado íntegramente en Raspbian (con posibles modificaciones del kernel) y he- rramientas libres y será publicado con una licencia GPL3. Palabras clave Periférico, Seguridad, Red, "Raspberry Pi", Hardware, GNU/Linux 3 Interfaz USB de red para acceso seguro basada en Raspberry Pi 4 Índice 1. Introducción...........................................................................................................................................7 1.1. Motivación......................................................................................................................................7 1.2. Objetivos........................................................................................................................................7 -

Internet Browser Settings to Protect Yourself and Continue Access to Banknet – Security Upgrade
Check Internet Browser Settings to Protect Yourself and Continue Access to BankNet – Security Upgrade The OCC is implementing Transport Layer Security (TLS) 1.1 and 1.2 on BankNet since industry reports state that prior versions have been compromised. If you do not have TLS 1.1 or 1.2 enabled in your browser (see instructions below), you will not be able to access BankNet after September 2016. Although you will continue to have access to BankNet until September 2016 without making any changes, updating your settings now will provide better protection when you use the Internet. TLS is a security protocol that enables private communication between Users and Web Servers. When the user and server communicate, TLS ensures that no one can eavesdrop or tamper with any of the communication. To ensure you have the best protection and can access BankNet after September 2016, configure Internet Explorer, Firefox, Chrome, Safari, or Opera to support TLS 1.1 and 1.2 by following the steps below. If you are using a web browser other than those listed here, consult the ‘Help’ for your web browser to enable TLS 1.1 and 1.2. FAQs and Troubleshooting Tips are contained at the end of this document. Internet Explorer To enable TLS 1.1 and 1.2 in Internet Explorer, perform the following steps: 1. Open Internet Explorer. 2. Click the Tools drop down menu on the toolbar. 3. Select Internet Options to open the Internet Options dialog window. 4. Click the Advanced tab at the top of the Internet Options dialog window. -
![[MS-HTTP2E]: Hypertext Transfer Protocol Version 2 (HTTP/2)](https://docslib.b-cdn.net/cover/1960/ms-http2e-hypertext-transfer-protocol-version-2-http-2-2901960.webp)
[MS-HTTP2E]: Hypertext Transfer Protocol Version 2 (HTTP/2)
[MS-HTTP2E]: Hypertext Transfer Protocol Version 2 (HTTP/2) Extension Intellectual Property Rights Notice for Open Specifications Documentation . Technical Documentation. Microsoft publishes Open Specifications documentation (“this documentation”) for protocols, file formats, data portability, computer languages, and standards support. Additionally, overview documents cover inter-protocol relationships and interactions. Copyrights. This documentation is covered by Microsoft copyrights. Regardless of any other terms that are contained in the terms of use for the Microsoft website that hosts this documentation, you can make copies of it in order to develop implementations of the technologies that are described in this documentation and can distribute portions of it in your implementations that use these technologies or in your documentation as necessary to properly document the implementation. You can also distribute in your implementation, with or without modification, any schemas, IDLs, or code samples that are included in the documentation. This permission also applies to any documents that are referenced in the Open Specifications documentation. No Trade Secrets. Microsoft does not claim any trade secret rights in this documentation. Patents. Microsoft has patents that might cover your implementations of the technologies described in the Open Specifications documentation. Neither this notice nor Microsoft's delivery of this documentation grants any licenses under those patents or any other Microsoft patents. However, a given Open Specifications document might be covered by the Microsoft Open Specifications Promise or the Microsoft Community Promise. If you would prefer a written license, or if the technologies described in this documentation are not covered by the Open Specifications Promise or Community Promise, as applicable, patent licenses are available by contacting [email protected]. -
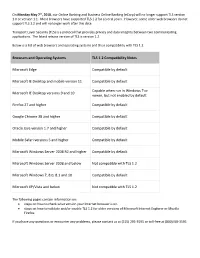
Browsers and Operating Systems TLS 1.2 Compatibility Notes Microsoft
On Monday May 7th, 2018, our Online Banking and Business Online Banking (eCorp) will no longer support TLS version 1.0 or version 1.1. Most browsers have supported TLS 1.2 for several years. However, some older web browsers do not support TLS 1.2 and will no longer work after this date. Transport Layer Security (TLS) is a protocol that provides privacy and data integrity between two communicating applications. The latest release version of TLS is version 1.2 Below is a list of web browsers and operating systems and their compatibility with TLS 1.2. Browsers and Operating Systems TLS 1.2 Compatibility Notes Microsoft Edge Compatible by default Microsoft IE Desktop and mobile version 11 Compatible by default Capable when run in Windows 7 or Microsoft IE Desktop versions 9 and 10 newer, but not enabled by default Firefox 27 and higher Compatible by default Google Chrome 38 and higher Compatible by default Oracle Java version 1.7 and higher Compatible by default Mobile Safari versions 5 and higher Compatible by default Microsoft Windows Server 2008 R2 and higher Compatible by default Microsoft Windows Server 2008 and below Not compatible with TLS 1.2 Microsoft Windows 7, 8.0, 8.1 and 10 Compatible by default Microsoft XP/Vista and below Not compatible with TLS 1.2 The following pages contain information on: steps on how to check what version your Internet browser is on. steps on how to validate and/or enable TLS 1.2 for older versions of Microsoft Internet Explorer or Mozilla Firefox.