Crypto Programming with Gcrypt What Is Gcrypt
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

On the Impact of Exception Handling Compatibility on Binary Instrumentation†
On the Impact of Exception Handling Compatibility on Binary Instrumentation† Soumyakant Priyadarshan Huan Nguyen R. Sekar Stony Brook University Stony Brook University Stony Brook University Stony Brook, NY, USA Stony Brook, NY, USA Stony Brook, NY, USA [email protected] [email protected] [email protected] Abstract overheads, but has been held back by challenges in accurate dis- assembly and code pointer identification. With the emergence of To support C++ exception handling, compilers generate metadata position-independent (or relocatable) binaries as the dominant for- that is a rich source of information about the code layout. On mat in recent years, researchers have been able to address these Linux, this metadata is also used to support stack tracing, thread challenges, e.g., in Egalito [41], RetroWrite [11] and SBR[28, 29] cleanup and other functions. For this reason, Linux binaries contain systems. code-layout-revealing metadata for C-code as well. Even hand- written assembly in low-level system libraries is covered by such Despite recent advances, deployability of binary instrumentation metadata. We investigate the implications of this metadata in this continues to face significant challenges. One of the major concerns paper, and show that it can be used to (a) improve accuracy of is compatibility. In particular, existing static binary instrumentation disassembly, (b) achieve significantly better accuracy at function tools tend to break stack tracing (for C and C++) as well as C++ boundary identification as compared to previous research, and(c) exception handling. While compatibility with these features may as a rich source of information for defeating fine-grained code not be important for proof-of-concept instrumentations, it is hardly randomization. -

MASTERCLASS GNUPG MASTERCLASS You Wouldn’T Want Other People Opening Your Letters and BEN EVERARD Your Data Is No Different
MASTERCLASS GNUPG MASTERCLASS You wouldn’t want other people opening your letters and BEN EVERARD your data is no different. Encrypt it today! SECURE EMAIL WITH GNUPG AND ENIGMAIL Send encrypted emails from your favourite email client. our typical email is about as secure as a The first thing that you need to do is create a key to JOHN LANE postcard, which is good news if you’re a represent your identity in the OpenPGP world. You’d Ygovernment agency. But you wouldn’t use a typically create one key per identity that you have. postcard for most things sent in the post; you’d use a Most people would have one identity, being sealed envelope. Email is no different; you just need themselves as a person. However, some may find an envelope – and it’s called “Encryption”. having separate personal and professional identities Since the early 1990s, the main way to encrypt useful. It’s a personal choice, but starting with a single email has been PGP, which stands for “Pretty Good key will help while you’re learning. Privacy”. It’s a protocol for the secure encryption of Launch Seahorse and click on the large plus-sign email that has since evolved into an open standard icon that’s just below the menu. Select ‘PGP Key’ and called OpenPGP. work your way through the screens that follow to supply your name and email address and then My lovely horse generate the key. The GNU Privacy Guard (GnuPG), is a free, GPL-licensed You can, optionally, use the Advanced Key Options implementation of the OpenPGP standard (there are to add a comment that can help others identify your other implementations, both free and commercial – key and to select the cipher, its strength and set when the PGP name now refers to a commercial product the key should expire. -

Open Source Used in 250 350 550 Switches 2.5.7.X
Open Source Used In 250 350 550 switches 2.5.7.x Cisco Systems, Inc. www.cisco.com Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at www.cisco.com/go/offices. Text Part Number: 78EE117C99-1099179018 Open Source Used In 250 350 550 switches 2.5.7.x 1 This document contains licenses and notices for open source software used in this product. With respect to the free/open source software listed in this document, if you have any questions or wish to receive a copy of any source code to which you may be entitled under the applicable free/open source license(s) (such as the GNU Lesser/General Public License), please contact us at [email protected]. In your requests please include the following reference number 78EE117C99-1099179018 Contents 1.1 jq 1.6-1 1.1.1 Available under license 1.2 avahi 0.6.32-3 1.2.1 Available under license 1.3 dnsmasq 2.78-1 1.3.1 Available under license 1.4 ejdb 1.2.12 1.4.1 Available under license 1.5 procd 2015/10/29 1.5.1 Available under license 1.6 jsonfilter 2014/6/19 1.6.1 Available under license 1.7 libnetconf 0.10.0-2 1.7.1 Available under license 1.8 libcgroup 0.41 1.8.1 Available under license 1.9 d-bus 1.10.4 1.9.1 Available under license 1.10 net-snmp 5.9 1.10.1 Available under license 1.11 nmap 6.47-2 1.11.1 Available under license 1.12 u-boot 2013.01 1.12.1 Available under license 1.13 bzip2 1.0.6 1.13.1 Available under license Open Source Used In 250 350 550 switches 2.5.7.x 2 1.14 openssl 1.1.1c 1.14.1 Available -

T U M a Digital Wallet Implementation for Anonymous Cash
Technische Universität München Department of Informatics Bachelor’s Thesis in Information Systems A Digital Wallet Implementation for Anonymous Cash Oliver R. Broome Technische Universität München Department of Informatics Bachelor’s Thesis in Information Systems A Digital Wallet Implementation for Anonymous Cash Implementierung eines digitalen Wallets for anonyme Währungen Author Oliver R. Broome Supervisor Prof. Dr.-Ing. Georg Carle Advisor Sree Harsha Totakura, M. Sc. Date October 15, 2015 Informatik VIII Chair for Network Architectures and Services I conrm that this thesis is my own work and I have documented all sources and material used. Garching b. München, October 15, 2015 Signature Abstract GNU Taler is a novel approach to digital payments with which payments are performed with cryptographically generated representations of actual currencies. The main goal of GNU Taler is to allow taxable anonymous payments to non-anonymous merchants. This thesis documents the implementation of the Android version of the GNU Taler wallet, which allows users to create new Taler-based funds and perform payments with them. Zusammenfassung GNU Taler ist ein neuartiger Ansatz für digitales Bezahlen, bei dem Zahlungen mit kryptographischen Repräsentationen von echten Währungen getätigt werden. Das Hauptziel von GNU Taler ist es, versteuerbare, anonyme Zahlungen an nicht-anonyme Händler zu ermöglichen. Diese Arbeit dokumentiert die Implementation der Android-Version des Taler-Portemonnaies, der es Benutzern erlaubt, neues Taler-Guthaben zu erzeugen und mit ihnen Zahlungen zu tätigen. I Contents 1 Introduction 1 1.1 GNU Taler . .2 1.2 Goals of the thesis . .2 1.3 Outline . .3 2 Implementation prerequisites 5 2.1 Native libraries . .5 2.1.1 Libgcrypt . -

Demarinis Kent Williams-King Di Jin Rodrigo Fonseca Vasileios P
sysfilter: Automated System Call Filtering for Commodity Software Nicholas DeMarinis Kent Williams-King Di Jin Rodrigo Fonseca Vasileios P. Kemerlis Department of Computer Science Brown University Abstract This constant stream of additional functionality integrated Modern OSes provide a rich set of services to applications, into modern applications, i.e., feature creep, not only has primarily accessible via the system call API, to support the dire effects in terms of security and protection [1, 71], but ever growing functionality of contemporary software. How- also necessitates a rich set of OS services: applications need ever, despite the fact that applications require access to part of to interact with the OS kernel—and, primarily, they do so the system call API (to function properly), OS kernels allow via the system call (syscall) API [52]—in order to perform full and unrestricted use of the entire system call set. This not useful tasks, such as acquiring or releasing memory, spawning only violates the principle of least privilege, but also enables and terminating additional processes and execution threads, attackers to utilize extra OS services, after seizing control communicating with other programs on the same or remote of vulnerable applications, or escalate privileges further via hosts, interacting with the filesystem, and performing I/O and exploiting vulnerabilities in less-stressed kernel interfaces. process introspection. To tackle this problem, we present sysfilter: a binary Indicatively, at the time of writing, the Linux -

Software Package Licenses
DAVIX 1.0.0 Licenses Package Version Platform License Type Package Origin Operating System SLAX 6.0.4 Linux GPLv2 SLAX component DAVIX 0.x.x Linux GPLv2 - DAVIX Manual 0.x.x PDF GNU FDLv1.2 - Standard Packages Font Adobe 100 dpi 1.0.0 X Adobe license: redistribution possible. Slackware Font Misc Misc 1.0.0 X Public domain Slackware Firefox 2.0.0.16 C Mozilla Public License (MPL), chapter 3.6 and Slackware 3.7 Apache httpd 2.2.8 C Apache License 2.0 Slackware apr 1.2.8 C Apache License 2.0 Slackware apr-util 1.2.8 C Apache License 2.0 Slackware MySQL Client & Server 5.0.37 C GPLv2 Slackware Wireshark 1.0.2 C GPLv2, pidl util GPLv3 Built from source KRB5 N/A C Several licenses: redistribution permitted dropline GNOME: Copied single libraries libgcrypt 1.2.4 C GPLv2 or LGPLv2.1 Slackware: Copied single libraries gnutls 1.6.2 C GPLv2 or LGPLv2.1 Slackware: Copied single libraries libgpg-error 1.5 C GPLv2 or LGPLv2.1 Slackware: Copied single libraries Perl 5.8.8 C, Perl GPL or Artistic License SLAX component Python 2.5.1 C, PythonPython License (GPL compatible) Slackware Ruby 1.8.6 C, Ruby GPL or Ruby License Slackware tcpdump 3.9.7 C BSD License SLAX component libpcap 0.9.7 C BSD License SLAX component telnet 0.17 C BSD License Slackware socat 1.6.0.0 C GPLv2 Built from source netcat 1.10 C Free giveaway with no restrictions Slackware GNU Awk 3.1.5 C GPLv2 SLAX component GNU grep / egrep 2.5 C GPLv2 SLAX component geoip 1.4.4 C LGPL 2.1 Built from source Geo::IPfree 0.2 Perl This program is free software; you can Built from source redistribute it and/or modify it under the same terms as Perl itself. -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae -

Implementing Privacy Preserving Auction Protocols (Master Thesis Final Talk)
Chair of Network Architectures and Services Department of Informatics Technical University of Munich Implementing Privacy Preserving Auction Protocols (Master Thesis Final Talk) Markus Teich, B. Sc. [email protected] March 23, 2017 Chair of Network Architectures and Services Department of Informatics Technical University of Munich Chair of Network Architectures and Services Department of Informatics Technical University of Munich Motivation In many existing auction systems sellers can: • Abuse loosing bid information • Collude with bidder(s) and change the outcome Our goals are: • Reduce requirement of trust in auction platform operators • Create usably fast system M. Teich — Auctions 2 Chair of Network Architectures and Services Department of Informatics Technical University of Munich Related Work Cryptographic auction protocols provide: • Correctness of the outcome • Non-Repudiation • Various degrees of privacy We choose the work of Felix Brandt because: • No trusted third party required • Beneficial privacy properties • Reviewed M. Teich — Auctions 3 first price first price private outcome public outcome M + 1st price M + 1st price private outcome public outcome Chair of Network Architectures and Services Department of Informatics Technical University of Munich Auction Formats Sealed bid vs. Incrementing M. Teich — Auctions 4 Chair of Network Architectures and Services Department of Informatics Technical University of Munich Auction Formats Sealed bid vs. Incrementing first price first price private outcome public outcome M + 1st price M + 1st price private outcome public outcome M. Teich — Auctions 4 Chair of Network Architectures and Services Department of Informatics Technical University of Munich libbrandt Overview • git://gnunet.org/libbrandt • Auction Outcome determination (all four formats) • Algorithms by Felix Brandt translated to Ed25519 • Around 4000 lines of C • Depends on libgcrypt v1.7+ and libgnunetutil v13.0+ • GPLv3+ M. -

18.04 Libgcrypt Cryptographic Module Module Versions 1.0 and 1.1 FIPS 140-2 Non-Proprietary Security Policy
18.04 Libgcrypt Cryptographic Module Module Versions 1.0 and 1.1 FIPS 140-2 Non-Proprietary Security Policy Document Version 2.2 Last update: September 15, 2021 © 2021 Canonical Ltd. / atsec information security This document can be reproduced and distributed only whole and intact, including this copyright notice. 18.04 Libgcrypt Cryptographic Module FIPS 140-2 Non-Proprietary Security Policy Prepared by: atsec information security corporation 9130 Jollyville Road, Suite 260 Austin, TX 78759 www.atsec.com © 2021 Canonical Ltd. / atsec information security This document can be reproduced and distributed only whole and intact, including this copyright notice. 2 of 39 18.04 Libgcrypt Cryptographic Module FIPS 140-2 Non-Proprietary Security Policy Table of Contents 1. Cryptographic Module Specification ..................................................................................................... 6 1.1. Module Overview ................................................................................................................................... 6 1.2. Modes of Operation ................................................................................................................................ 9 2. Cryptographic Module Ports and Interfaces ........................................................................................ 10 3. Roles, Services and Authentication ..................................................................................................... 11 3.1. Roles ..................................................................................................................................................... -
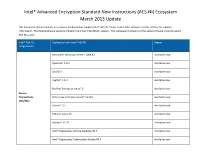
Intel® Advanced Encryption Standard New Instructions (AES-NI) Ecosystem March 2013 Update
Intel® Advanced Encryption Standard New Instructions (AES-NI) Ecosystem March 2013 Update This document doesn’t include all software products that support Intel® AES-NI. Please contact the software vendor directly for support information. The listed software versions indicate the initial Intel AES-NI support. The subsequent versions of the same software should support AES-NI as well. Intel® AES-NI Application with Intel® AES-NI Status Usage Model Microsoft* Windows Server* 2008 R2 Available now OpenSSL* 1.0.1 Available now GnuTLS* Available now CyaSSL* 1.5.4 Available now Red Hat Enterprise Linux* 6 Available now Secure Transactions SUSE Linux Enterprise Linux* 11 SP1 Available now (TLS/SSL) Solaris* 10 Available now Fedora* Linux 13 Available now Ubuntu* 11.10 Available now Intel® Expressway Service Gateway R3.4 Available now Intel® Expressway TokeniZation Broker R3.4 Available now Checkpoint* Endpoint Security R73 FDE 7.4 HFA1 Available now McAfee Endpoint Encryption* 6.0 with ePolicy Orchestrator* 4.5 Available now Microsoft BitLocker* WS2008R2 Available now Symantec* PGP Universal 10.1 Available now Full Disk Encryption WinMagic* SecureDoc* 5.2 Available now Software Dell* Data Protection for windows system Available now FileVault* Version 2 (Mac OS X Lion) Available now TrueCrypt* 7.0 Available now Sophos* SafeGuard Easy 6.0/SafeGuard Device Encryption 6.0 Available now Oracle* Berkeley* DB 11.2.5.0.26 Available now Oracle* Database* 11.2.0.2 Available now IBM* InfoSphere* Guardium Data Encryption for DB2* Available now Enterprise -

Technical Notes All Changes in Fedora 13
Fedora 13 Technical Notes All changes in Fedora 13 Edited by The Fedora Docs Team Copyright © 2010 Red Hat, Inc. and others. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/. The original authors of this document, and Red Hat, designate the Fedora Project as the "Attribution Party" for purposes of CC-BY-SA. In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, MetaMatrix, Fedora, the Infinity Logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. For guidelines on the permitted uses of the Fedora trademarks, refer to https:// fedoraproject.org/wiki/Legal:Trademark_guidelines. Linux® is the registered trademark of Linus Torvalds in the United States and other countries. Java® is a registered trademark of Oracle and/or its affiliates. XFS® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. All other trademarks are the property of their respective owners. Abstract This document lists all changed packages between Fedora 12 and Fedora 13. -

Reproducible Builds in Freebsd
Reproducible Builds in FreeBSD Ed Maste [email protected] BSDCan 2016 (Ottawa, Canada) 2016-06-11 About Me I FreeBSD user since early 2000s I FreeBSD committer since 2005 I FreeBSD Foundation since 2011 I Reproducible builds since 2015 I BSD src contributor or committer? I BSD ports maintainer or committer? I Contributed to Free / Open Source Software? I Have heard about reproducible builds? I Have worked on making software reproducible? About You I BSD ports maintainer or committer? I Contributed to Free / Open Source Software? I Have heard about reproducible builds? I Have worked on making software reproducible? About You I BSD src contributor or committer? I Contributed to Free / Open Source Software? I Have heard about reproducible builds? I Have worked on making software reproducible? About You I BSD src contributor or committer? I BSD ports maintainer or committer? I Have heard about reproducible builds? I Have worked on making software reproducible? About You I BSD src contributor or committer? I BSD ports maintainer or committer? I Contributed to Free / Open Source Software? I Have worked on making software reproducible? About You I BSD src contributor or committer? I BSD ports maintainer or committer? I Contributed to Free / Open Source Software? I Have heard about reproducible builds? About You I BSD src contributor or committer? I BSD ports maintainer or committer? I Contributed to Free / Open Source Software? I Have heard about reproducible builds? I Have worked on making software reproducible? and get the same result Reproducible