Google Maps As Cartographic Infrastructure: from Participatory Mapmaking to Database Maintenance
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Recaptcha: Human-Based Character Recognition Via Web Security
REPORTS on September 12, 2008 and blogs. For example, CAPTCHAs prevent www.sciencemag.org reCAPTCHA: Human-Based Character ticket scalpers from using computer programs to buy large numbers of concert tickets, only to re Recognition via Web Security Measures sell them at an inflated price. Sites such as Gmail and Yahoo Mail use CAPTCHAs to stop spam Luis von Ahn,* Benjamin Maurer, Colin McMillen, David Abraham, Manuel Blum mers from obtaining millions of free e mail accounts, which they would use to send spam CAPTCHAs (Completely Automated Public Turing test to tell Computers and Humans Apart) are e mail. Downloaded from widespread security measures on the World Wide Web that prevent automated programs from According to our estimates, humans around abusing online services. They do so by asking humans to perform a task that computers cannot yet the world type more than 100 million CAPTCHAs perform, such as deciphering distorted characters. Our research explored whether such human every day (see supporting online text), in each case effort can be channeled into a useful purpose: helping to digitize old printed material by asking spending a few seconds typing the distorted char users to decipher scanned words from books that computerized optical character recognition failed acters. In aggregate, this amounts to hundreds of to recognize. We showed that this method can transcribe text with a word accuracy exceeding 99%, thousands of human hours per day. We report on matching the guarantee of professional human transcribers. Our apparatus is deployed in more an experiment that attempts to make positive use than 40,000 Web sites and has transcribed over 440 million words. -

The Uch Enmek Example(Altai Republic,Siberia)
Faculty of Environmental Sciences Institute for Cartography Master Thesis Concept and Implementation of a Contextualized Navigable 3D Landscape Model: The Uch Enmek Example(Altai Republic,Siberia). Mussab Mohamed Abuelhassan Abdalla Born on: 7th December 1983 in Khartoum Matriculation number: 4118733 Matriculation year: 2014 to achieve the academic degree Master of Science (M.Sc.) Supervisors Dr.Nikolas Prechtel Dr.Sander Münster Submitted on: 18th September 2017 Faculty of Environmental Sciences Institute for Cartography Task for the preparation of a Master Thesis Name: Mussab Mohamed Abuelhassan Abdalla Matriculation number: 4118733 Matriculation year: 2014 Title: Concept and Implementation of a Contextualized Navigable 3D Landscape Model: The Uch Enmek Example(Altai Republic,Siberia). Objectives of work Scope/Previous Results:Virtual Globes can attract and inform websites visitors on natural and cultural objects and sceneries.Geo-centered information transfer is suitable for majority of sites and artifacts. Virtual Globes have been tested with an involvement of TUD institutes: e.g. the GEPAM project (Weller,2013), and an archaeological excavation site in the Altai Mountains ("Uch enmek", c.f. Schmid 2012, Schubert 2014).Virtual Globes technology should be flexible in terms of the desired geo-data configuration. Research data should be controlled by the authors. Modes of linking geo-objects to different types of meta-information seems evenly important for a successful deployment. Motivation: For an archaeological conservation site ("Uch Enmek") effort has already been directed into data collection, model development and an initial web-based presentation.The present "Open Web Globe" technology is not developed any further, what calls for a migra- tion into a different web environment. -

Implementing OGC Web Map Service Client Applications Using JSP, JSTL and XMLC
Implementing OGC Web Map Service Client Applications Using JSP, JSTL and XMLC Hao Ding , Richard Pascoe & Neville Churcher Department of Computer Science University of Canterbury. Christchurch, New Zealand Phone: +64 3 364-2362 Fax: +64 3 364-2569 Email: [email protected] , {richard, neville}@cosc.canterbury.ac.nz Presented at SIRC 2002 – The 14th Annual Colloquium of the Spatial Information Research Centre University of Otago, Dunedin, New Zealand th December 3-5 2002 ABSTRACT Java technologies are widely used in web application development. In this paper are described three approaches to developing Java-based web applications and our experiences with applying each to the development of client that interact with servers implementing the OGC (Open GIS Consortium) Web Map Service (WMS) specification. Also described is the installation and configuration of open source software that implements the WMS specification. The paper is concluded with some preliminary insights into when one of the three approaches to WMS client implementation is more suited to another. Keywords and phrases: WMS, JSP, JSTL, XMLC, map layer, web map server 1.0 INTRODUCTION Of the many technologies, such as Common Gateway Interface (CGI), Active Server Pages (ASP), JavaServer Pages (JSP), that are used to develop web applications, three are of particular interest to the research presented here. These three technologies or approaches to developing clients that utilise web services are JavaServer Pages (JSP), JSP with the use of tags from the JSP Standard Tag Library (JSTL), and the eXtensible Markup Language Compiler (XMLC). JSP is a more convenient way to write Java servlets, and allows the insertion of Java code directly into static HTML (Hypertext Markup Language) pages. -

I Am Not a Robot: an Overview on Google's Captcha
I AM NOT A ROBOT: - AN OVERVIEW ON GOOGLE’S CAPTCHA A Thesis Presented to the Faculty of California State Polytechnic University, Pomona In Partial Fulfillment Of the Requirements for the Degree Master of Science In Computer Science By Uday Prabhala 2016 SIGNATURE PAGE THESIS: I AM NOT A ROBOT: - AN OVERVIEW ON GOOGLE’S CAPTCHA AUTHOR: Uday Prabhala DATE SUBMITTED: Summer 2016 Computer Science Department. Dr. Gilbert Young ___________________________________________ Thesis Committee Chair Computer Science Dr. Fang D. Tang ___________________________________________ Computer Science Dr. Yu Sun ___________________________________________ Computer Science ii ACKNOWLEDGEMENTS I would like to express my deepest gratitude to my family members, Yashoda, Lucky, and Diskey, as well as my girlfriend Siri, who helped make this endeavor possible. Their limitless support, assistance, and encouragement during the times when I was close to giving up were greatly helpful, and I wouldn’t have been able to overcome the obstacles without them. I would also like to send my appreciation and gratitude to the Professors who were part of my thesis committee. Most notably, I would like to thank Professor Gilbert Young, chair of the committee, for his support, patience, guidance, and sharing of knowledge throughout the program. I would also like to thank Professor Tang and Professor Yusun for reviewing my paper and attending my presentation. The above three Professors not only helped me to complete my program, but also served as an excellent example by exercising professionalism, versatility, and commitment to the developing engineering students at California State Polytechnic University, Pomona. iii ABSTRACT I am not a Robot Overview on Google’s Captcha Uday Kiran Prabhala Computers are one of the greatest inventions done by humans; these devices not only made our work easy, but could also be misused in various ways. -

Modern Password Security for System Designers What to Consider When Building a Password-Based Authentication System
Modern password security for system designers What to consider when building a password-based authentication system By Ian Maddox and Kyle Moschetto, Google Cloud Solutions Architects This whitepaper describes and models modern password guidance and recommendations for the designers and engineers who create secure online applications. A related whitepaper, Password security for users, offers guidance for end users. This whitepaper covers the wide range of options to consider when building a password-based authentication system. It also establishes a set of user-focused recommendations for password policies and storage, including the balance of password strength and usability. The technology world has been trying to improve on the password since the early days of computing. Shared-knowledge authentication is problematic because information can fall into the wrong hands or be forgotten. The problem is magnified by systems that don't support real-world secure use cases and by the frequent decision of users to take shortcuts. According to a 2019 Yubico/Ponemon study, 69 percent of respondents admit to sharing passwords with their colleagues to access accounts. More than half of respondents (51 percent) reuse an average of five passwords across their business and personal accounts. Furthermore, two-factor authentication is not widely used, even though it adds protection beyond a username and password. Of the respondents, 67 percent don’t use any form of two-factor authentication in their personal life, and 55 percent don’t use it at work. Password systems often allow, or even encourage, users to use insecure passwords. Systems that allow only single-factor credentials and that implement ineffective security policies add to the problem. -

Development of a Web Mapping Application Using Open Source
Centre National de l’énergie des sciences et techniques nucléaires (CNESTEN-Morocco) Implementation of information system to respond to a nuclear emergency affecting agriculture and food products - Case of Morocco Anis Zouagui1, A. Laissaoui1, M. Benmansour1, H. Hajji2, M. Zaryah1, H. Ghazlane1, F.Z. Cherkaoui3, M. Bounsir3, M.H. Lamarani3, T. El Khoukhi1, N. Amechmachi1, A. Benkdad1 1 Centre National de l’Énergie, des Sciences et des Techniques Nucléaires (CNESTEN), Morocco ; [email protected], 2 Institut Agronomique et Vétérinaire Hassan II (IAV), Morocco, 3 Office Régional de la Mise en Valeur Agricole du Gharb (ORMVAG), Morocco. INTERNATIONAL EXPERTS’ MEETING ON ASSESSMENT AND PROGNOSIS IN RESPONSE TO A NUCLEAR OR RADIOLOGICAL EMERGENCY (CN-256) IAEA Headquarters Vienna, Austria 20–24 April 2015 Context In nuclear disaster affecting agriculture, there is a need for rapid, reliable and practical tools and techniques to assess any release of radioactivity The research of hazards illustrates how geographic information is being integrated into solutions and the important role the Web now plays in communication and disseminating information to the public for mitigation, management, and recovery from a disaster. 2 Context Basically GIS is used to provide user with spatial information. In the case of the traditional GIS, these types of information are within the system or group of systems. Hence, this disadvantage of traditional GIS led to develop a solution of integrating GIS and Internet, which is called Web-GIS. 3 Project Goal CRP1.50.15: “ Response to Nuclear Emergency affecting Food and Agriculture” The specific objective of our contribution is to design a prototype of web based mapping application that should be able to: 1. -

Check Point Threat Intelligence Bulletin
December 31, 2018 – January 6, 2019 VS. CISCO IRON PORT YOUR CHECK POINT THREAT INTELLIGENCE REPORT TOP ATTACKS AND BREACHES Highly-sensitive personal data of more than 100 German politicians, including German Chancellor Angela Merkel, has been leaked in a recent attack. While the identity of the attackers and the method used are still unknown, the leaked data appears to have been collected from their personal smartphones. The popular browser-based game ‘Town of Salem’ has suffered a major data breach, exposing account data of more than 7.6 million players. The breached database contained players’ email addresses, hashed passwords, IP addresses and some payment information. The Ryuk ransomware has hit the cloud hosting provider “Dataresolution.net”, after the attackers used a hacked login account. The Ryuk campaign was studied last August by Check Point’s research team, who associated it with the notorious North Korean APT Lazarus Group. Check Point SandBlast and Anti-Bot blades provide protection against this threat (Trojan-Ransom.Win32.Ryuk) A new campaign targeting Chromecast adapters has been launched in order to promote the popular YouTube channel “PewDiePie”. The hackers utilized the Universal Plug and Play (UPnP) feature in Chromecasts that allows routers to forward public Internet ports to internal adapters and used it to connect to the device and display YouTube content. A data leak has affected over 2.4 million users of Blur, the password manager application. The leak potentially exposed users’ email addresses, password hashes, IP addresses and, in some cases, full names and password hints. The official website of Dublin’s tram system, the Luas, has been hacked and defaced. -

Combating Attacks and Abuse in Large Online Communities
University of California Santa Barbara Combating Attacks and Abuse in Large Online Communities Adissertationsubmittedinpartialsatisfaction of the requirements for the degree Doctor of Philosophy in Computer Science by Gang Wang Committee in charge: Professor Ben Y. Zhao, Chair Professor Haitao Zheng Professor Christopher Kruegel September 2016 The Dissertation of Gang Wang is approved. Professor Christopher Kruegel Professor Haitao Zheng Professor Ben Y. Zhao, Committee Chair July 2016 Combating Attacks and Abuse in Large Online Communities Copyright c 2016 ⃝ by Gang Wang iii Acknowledgements I would like to thank my advisors Ben Y.Zhao and Haitao Zheng formentoringmethrough- out the PhD program. They were always there for me, giving me timely and helpful advice in almost all aspects of both research and life. I also want to thank my PhD committee member Christopher Kruegel for his guidance in my research projects and job hunting. Finally, I want to thank my mentors in previous internships: Jay Stokes, Cormac Herley, Weidong Cui and Helen Wang from Microsoft Research, and Vicente Silveira fromLinkedIn.Specialthanksto Janet Kayfetz, who has helped me greatly with my writing and presentation skills. Iamverymuchthankfultomycollaboratorsfortheirhardwork, without which none of this research would have been possible. First and foremost, to the members of SAND Lab at UC Santa Barbara: Christo Wilson, Bolun Wang, Tianyi Wang, Manish Mohanlal, Xiaohan Zhao, Zengbin Zhang, Xia Zhou, Ana Nika, Xinyi Zhang, Shiliang Tang, Alessandra Sala, Yibo Zhu, Lin Zhou, Weile Zhang, Konark Gill, Divya Sambasivan, Xiaoxiao Yu, Troy Stein- bauer, Tristan Konolige, Yu Su and Yuanyang Zhang. Second, totheemployeesatMicrosoft: Jack Stokes, Cormac Herley and David Felstead. Third, to Miriam Metzger from the Depart- ment of Communications at UC Santa Barbara, and Sarita Y. -

Creating Google Street Views with the Samsung Gear 360 Camera By
Creating Google Street Views with the Samsung Gear 360 Camera1 by Andy Lyons Last modified: November 2016 Google Street View Camera Loan Kit In October 2016, Google loaned a 360-camera kit to IGIS (a statewide technical support program in ANR), for the purposes of exploring how Google’s Street View technology can be useful for research and management at the Hopland Research and Extension Center (and ANR field stations more generally). Street View app and the Samsung Gear 360 2 The Street View app (for both Android and iOS) is what you use to create and upload Street Views. The Samsung Gear 360 is one of about four 360 cameras that the Google Street View app is setup to work with (meaning the app can control the camera pretty seamlessly). Most people use the Street View app only to view off-road street views. You can also view off-road street views in plain old Google Maps, but the Street View app makes it a little easier to find user generated content. If you have a VR device such as the Google Cardboard, you can view Street Views in 3 cardboard mode . In terms of content creation, the Street View app has three main functions: i) control the camera, ii) process images (which includes stitching them together, blurring faces and license plates, adding locations as needed, and linking nearby photos), and iii) upload the images to Google Street View (after which they’ll be available in Google Maps immediately). The Samsung Gear can also record 360 video. For that you need the Samsung Gear 360 Manager (or another app). -

An Open-Source Web Platform to Share Multisource, Multisensor Geospatial Data and Measurements of Ground Deformation in Mountain Areas
International Journal of Geo-Information Article An Open-Source Web Platform to Share Multisource, Multisensor Geospatial Data and Measurements of Ground Deformation in Mountain Areas Martina Cignetti 1,2, Diego Guenzi 1,* , Francesca Ardizzone 3 , Paolo Allasia 1 and Daniele Giordan 1 1 National Research Council of Italy, Research Institute of Geo-Hydrological Protection (CNR IRPI), Strada delle Cacce 73, 10135 Turin, Italy; [email protected] (M.C.); [email protected] (P.A.); [email protected] (D.G.) 2 Department of Earth Sciences, University of Pavia, 27100 Pavia, Italy 3 National Research Council of Italy, Research Institute of Geo-Hydrological Protection (CNR IRPI), Via della Madonna Alta 126, 06128 Perugia, Italy; [email protected] * Correspondence: [email protected] Received: 20 November 2019; Accepted: 16 December 2019; Published: 18 December 2019 Abstract: Nowadays, the increasing demand to collect, manage and share archives of data supporting geo-hydrological processes investigations requires the development of spatial data infrastructure able to store geospatial data and ground deformation measurements, also considering multisource and heterogeneous data. We exploited the GeoNetwork open-source software to simultaneously organize in-situ measurements and radar sensor observations, collected in the framework of the HAMMER project study areas, all located in high mountain regions distributed in the Alpines, Apennines, Pyrenees and Andes mountain chains, mainly focusing on active landslides. Taking advantage of this free and internationally recognized platform based on standard protocols, we present a valuable instrument to manage data and metadata, both in-situ surface measurements, typically acquired at local scale for short periods (e.g., during emergency), and satellite observations, usually exploited for regional scale analysis of surface displacement. -
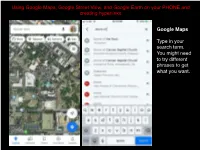
Using Google MAPS Street View on Your PHONE and Creating Hyperlinks
Using Google Maps, Google Street View, and Google Earth on your PHONE and creating hyperlinks Google Maps Type in your search term. You might need to try different phrases to get what you want. Pull the bottom screen up to see the Overview and click on Photos Switch to “Street View & 360” and search through the images listed, opening them by clicking on them. Once in the 360 degree view you can move your view around by swiping on the screen (you can also do this to the smaller preview images in the list). Once you have found the view that “explains the ways in which it augments understanding of the monument/place/site/object itself, beyond your readings or what has been discussed in class” save the view as the choice for your Spatial Exploration Project entry. To do this click on the “share” icon (a square with an arrow projecting from it) that I’ve outlined in red at the top of the page. At this point you can text or email yourself the link or copy it to paste into a document. To create a hyperlink in your document, highlight the text you want to be connected to your view, paste the copied url you made from the previous share screen, hit ”go” or “enter,” and that text will now have the link embedded in it. Google Street View While less well known than Google Maps, Street View allows you to walk the streets of the location you choose. Once again, you type in your search term. -

An Object Detection Based Solver for Google's Image Recaptcha V2
An Object Detection based Solver for Google’s Image reCAPTCHA v2 Md Imran Hossen∗ Yazhou Tu∗ Md Fazle Rabby∗ Md Nazmul Islam∗ Hui Cao† Xiali Hei∗ ∗University of Louisiana at Lafayette †Xi’an Jiaotong University Abstract have emerged as a superior alternative to text ones as they are considered more robust to automated attacks. Previous work showed that reCAPTCHA v2’s image chal- lenges could be solved by automated programs armed with reCAPTCHA v2, a dominant image CAPTCHA service Deep Neural Network (DNN) image classifiers and vision released by Google in 2014, asks users to perform an im- APIs provided by off-the-shelf image recognition services. age recognition task to verify that they are humans and not In response to emerging threats, Google has made signifi- bots. However, in recent years, deep learning (DL) algorithms cant updates to its image reCAPTCHA v2 challenges that have achieved impressive successes in several complex image can render the prior approaches ineffective to a great extent. recognition tasks, often matching or even outperforming the In this paper, we investigate the robustness of the latest ver- cognitive ability of humans [30]. Consequently, successful sion of reCAPTCHA v2 against advanced object detection attacks against reCAPTCHA v2 that leverage Deep Neural based solvers. We propose a fully automated object detection Network (DNN) image classifier and off-the-shelf (OTS) im- based system that breaks the most advanced challenges of age recognition services have been proposed [44, 50]. reCAPTCHA v2 with an online success rate of 83.25%, the The prior work advanced our understanding of the security highest success rate to date, and it takes only 19.93 seconds issues of image CAPTCHAs and led to better CAPTCHA (including network delays) on average to crack a challenge.