GDPR: 5 Lessons Learned Veeam Compliance Experience Shared a Step-By-Step Guide for IT Professionals
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Tintri and Veeam at a Glance
Tintri and Veeam Streamline Backup, Replication and Storage at the VM level Tintri VM-aware storage (VAS) is built for virtualized environments and the cloud. Enterprises and cloud service providers power their on-premises and hosted private cloud on Tintri, running a full range of mixed workloads – from VDI to business critical applications, to dev & test environments. You can create hundreds of high performance, zero-space VM clones speeding up VM provisioning for VDI, dev & test workloads. Backup and replication for critical workloads in multi-hypervisor environments such as VMware and Hyper-V is required to be seamless and simple to perform. Veeam Backup & Replication provides fast, flexible and reliable recovery of virtualized applications and data to support backup and replication of thousands of VMs for both VMware vSphere and Microsoft Hyper-V environments. Veeam supports Direct NFS Access for VMware, and Volume Shadow Copy Service (VSS) with Server Message Block (SMB) 3.0 file shares for Hyper-V hosted on Tintri VMstore. Together, Tintri and Veeam provide customers with simplified data protection of VMs, VM-level visibility and high performance backup and restore. Jointly, customers can reduce recovery point objectives (RPOs) to <15 minutes and achieve more economical disaster recovery (DR) solutions. Benefits of Tintri and Veeam Simplicity • Set-up in less than 30 minutes – connect, configure and deploy. • Manage and backup VMs and vDisks instead of LUNs and volumes—eliminate complex configuration and ongoing tuning. • Seamlessly scale and backup virtualized environments from hundreds to thousands of VMs without additional storage provisioning. Efficiency • Protect individual VMs with customizable policies using Tintri VM-level data protection including space efficient snapshots that don’t impact performance combined with Veeam Backup & Replication • Deploy affordable per-VM data protection and disaster recovery with Tintri VM-level replication reducing WAN bandwidth usage by as much as 95 percent with global deduplication and compression. -

1 Cloud Data Management
Product Overview Veeam Backup & Replication #1 Cloud Data Management Veeam® Backup & Replication™ delivers Availability for ALL your virtual, physical and cloud-based workloads. Through a single management console, you can “If you want worry-free Availability, manage fast, flexible and reliable backup, recovery and replication of all your choose Veeam. Of all the solutions applications and data to eliminate legacy backup solutions forever. available, Veeam is the Ferrari sitting on the showroom floor.” John Burks, Veeam Backup & Replication features Director of Information Technology, Backup BLR Veeam provides fast and reliable backup for ALL workloads — virtual, physical and cloud. “Veeam helps us deliver on our mission NEW • Veeam Cloud Tier: Provides unlimited capacity for long-term data retention with to create authentic experiences that native, cost effective object storage integrations which allow organizations to scale rock. Even during our busiest months, both on-premises and in the cloud. when we host several conventions and hundreds of thousands of people, • Veeam Plug-ins for SAP HANANEW and Oracle RMAN:NEW Improve scalability and Veeam gives us complete confidence operational efficiencies while managing enterprise environments. that our IT systems are able to support • Built-in management for Veeam Agent for Microsoft Windows and Veeam guest experiences 24.7.365.” Agent for Linux: Manage agent-based backup capabilities directly inside Kevin Ragsdale, the Veeam Backup & Replication console, including a single pane of glass for Director of IT Availability of virtual, physical and cloud workloads, centralized backup agent Hard Rock Hotel & Casino deployment and Windows Server Failover Cluster support. • Image-level VM backups: Create application-consistent backups with advanced “We had two options: we could spend application-aware processing. -

Credit Union Runs out of Disk Space, Replaces Dell EMC Data Domain with Exagrid
Credit Union Runs Out of Disk Space, Replaces Dell EMC Data Domain with ExaGrid CUSTOMER SUCCESS STORY Customer Overview As Maine’s first credit union, Infinity Federal Credit Union (FCU) has been serving its members since 1921, initially as the Telephone Workers Credit Union of Maine, then as Telco of New England FCU. Infinity FCU is now community-based, available to anyone who lives, works, worships, or attends school in Cumberland and York counties and the city of Bangor, Maine. “One of the things I like about Infinity FCU is a non-profit cooperative organization owned by its members. ExaGrid is that if I ever need to add more storage, I can just add another appliance to Aging System Leads to the system. My Data Domain New Solution systems were fully populated and starting to run out of disk Infinity FCU had been backing up its data to space at their end of life. I Dell EMC Data Domain systems with Quest was not able to expand them vRanger software. As the Data Domain anymore, or add any storage.” appliances reached their end of life, Sherry Dunkin, the organization’s IT manager, Sherry Dunkin researched new options for the backup IT Manager environment. Dunkin decided to replace vRanger with Veeam and looked for a new storage solution that Veeam would work well with. A reseller recommended ExaGrid for its The ExaGrid system is easy to install Key Benefits: integration with Veeam. and use, and works seamlessly with all Infinity FCU recovers data of the most frequently used backup ‘extremely quickly’ using Veeam Dunkin decided to compare products to find applications, so an organization can and ExaGrid the best option. -

Hyper-V Backup
SPECIAL PULLOUT SECTION PARTNER’S GUIDE TO Hyper-V Backup away at VMware’s position for a long time, though. The combined eff ort is starting to have an eff ect. As recently as 2008, VMware still owned 65.4 percent of the market, according to market research firm IDC. As of 2012, however, VMware’s lead was down to 56.8 percent. That may still be the lion’s share of the market, but it’s nowhere near the share VMware enjoyed a few years ago. The prime benefi ciary of VMware’s slide in market share has been Microsoft. IDC puts the Redmond-based software giant at a solid No. 2 in virtualization market share behind VMware. And Microsoft is gaining share almost as quickly as VMware is losing it. In 2008, IDC estimated Microsoft’s share of new virtualized servers at 20.3 percent. At the end of last year, IDC had Hyper-V at The current Windows Server 2012 and Windows Server 2012 R2 27.6 percent. release shipping this month give Microsoft partners plenty of reasons According to IDC analyst Al Gillen in a to consider recommending the technology to customers for their May interview with The Wall Street Journal, virtualization needs. By Scott Bekker Microsoft’s fastest areas of server virtualiza- tion growth are in the emerging markets icrosoft partners with deep of Asia and South America. Another area of growth for expertise in the Microsoft stack Microsoft Gillen pointed out is of particular interest to are looking harder than ever at the majority of Microsoft partners—smaller companies adding Microsoft Hyper-V to in developed markets. -

1 VM Backup for Vmware Vsphere and Microsoft Hyper-V
Product Overview Veeam Backup & Replication #1 VM Backup for VMware vSphere and Microsoft Hyper-V Veeam® Backup & Replication™ provides fast, flexible, and reliable “If you want worry-free recovery of virtualized applications and data. We bring backup and availability, choose Veeam. replication together in a single solution with award-winning support for Of all the solutions available, VMware vSphere and Microsoft Hyper-V virtual environments. Veeam is the Ferrari sitting on the showroom floor.” This powerful, easy-to-use and affordable backup and Availability John Burks solution leverages virtualization, storage, and cloud technologies to Director of Information meet SLAs for recovery time and point objectives (RTPO™) <15 minutes Technology BLR for ALL applications and data. “You’ve got to let Veeam do #1 VM Backup™ features what it does best — back up and restore data in a rapid Backup fashion.” Veeam provides fast and reliable backup for vSphere and Hyper-V virtual Ryan McClain environments — all without the use of agents. Systems Architect U.S. Legal Support, Inc. • Image-level VM backups: Create application-consistent backups with advanced application-aware processing “We had two options: we • ENHANCED Backup from Storage Snapshots for EMCNEW, HPE and NetApp: could spend more than half Generate ultra-fast backups with low RPOs the workweek managing and • NEW Scale-out Backup Repository™: Create a single virtual pool of backup worrying about VM backup storage to which backups can be assigned, offering the freedom to easily extend and replication, or we could backup storage capacity put Veeam in place and • Veeam Cloud Connect: Get backups off site without the cost and complexity of forget about it.” building and maintaining an off-site infrastructure; fast and secure cloud backup Brooks Barnes to a service provider Systems Administrator Great Southern Wood • SureBackup®: Automatically test and verify every backup and every virtual Preserving, Inc. -

Top Three Reasons to Adopt Universal Licensing for All Your Workloads
Top three reasons to adopt universal licensing for all your workloads Chris Spencer Sr. Director Global Product Marketing Top three reasons to adopt universal licensing for all your workloads 2 Introduction IT is pervasive. Look at any industry, large or small, and you will see the importance of IT. More than ever, there are more choices for applications, hardware, virtualization, storage, networking and more. Businesses are bombarded with these choices and decisions on a regular basis. No matter if it’s a decision to stay small or expand globally, stay on-premises or move to the cloud, or perhaps not knowing what the next step will be, these business decisions are increasingly important. The most crucial part of these decisions concerns protecting customer data. Seriously! With data growing at upwards of 60% per year every year, flexible data protection that expands and scales is more critical than ever. Whether your data is virtualized, running on physical servers or in the cloud, businesses are held accountable for protecting that data, no matter what. Whether that data is for production or testing, on-premises only or hybrid cloud, it needs to be protected. That’s where Veeam® comes in. veeam.com Top three reasons to adopt universal licensing for all your workloads 3 On premises, cloud & hybrid: It’s all part of my IT strategy! Today, we rarely see customers who aren’t running a mixture of different workloads in different locations, with workloads and data residing both on premises and in the cloud. Data protection needs continue to transform in many ways: Physical, virtual, cloud, multi-cloud. -
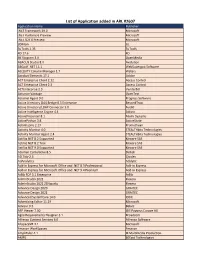
List of Application Added in ARL #2607
List of Application added in ARL #2607 Application Name Publisher .NET Framework 19.0 Microsoft .NET Runtime 6 Preview Microsoft .NET SDK 6 Preview Microsoft 3DMark UL 3uTools 2.35 3uTools 4D 17.6 4D 4K Stogram 3.0 OpenMedia ABACUS Studio 8.0 Avolution ABCpdf .NET 11.1 WebSupergoo Software ACQUITY Column Manager 1.7 Waters Acrobat Elements 17.1 Adobe ACT Enterprise Client 2.12 Access Control ACT Enterprise Client 2.3 Access Control ACTEnterprise 2.3 Vanderbilt Actiance Vantage OpenText Actional Agent 9.0 Progress Software Active Directory (AD) Bridge 8.5 Enterprise BeyondTrust Active Directory/LDAP Connector 5.0 Auth0 Active Intelligence Engine 4.4 Attivio ActivePresenter 8.1 Atomi Systems ActivePython 3.8 ActiveState ActivInspire 2.17 Promethean Activity Monitor 4.0 STEALTHbits Technologies Activity Monitor Agent 2.4 STEALTHbits Technologies ActiViz.NET 8.2 Supported Kitware SAS ActiViz.NET 8.2 Trial Kitware SAS ActiViz.NET 9.0 Supported Kitware SAS Acumen Cumulative 8.5 Deltek AD Tidy 2.6 Cjwdev AdAnalytics Adslytic Add-in Express for Microsoft Office and .NET 8.3 Professional Add-in Express Add-in Express for Microsoft Office and .NET 9.4 Premium Add-in Express Adlib PDF 5.1 Enterprise Adlib AdminStudio 2021 Flexera AdminStudio 2021 ZENworks Flexera Advance Design 2020 GRAITEC Advance Design 2021 GRAITEC Advanced SystemCare 14.0 IObit Advertising Editor 11.29 Microsoft Advisor 9.5 Belarc AFP Viewer 7.50 ISIS Papyrus Europe AG Agile Requirements Designer 3.1 Broadcom Alfresco Content Services 6.0 Alfresco Software AltspaceVR 4.1 Microsoft -

Optimizing Vmware Protection with HP and Veeam
Optimizing VMware protection with HP and Veeam Technical white paper Table of contents Executive summary ............................................................................................................................... 2 Key points ....................................................................................................................................... 2 Introduction ......................................................................................................................................... 2 Technology overview ........................................................................................................................... 2 VMware vStorage APIs and Change Block Tracking ............................................................................. 3 Veeam Backup source-side deduplication ............................................................................................ 3 HP StoreOnce D2D appliance target-side deduplication ....................................................................... 3 Combining Veeam Backup inline and HP D2D target-based deduplication ................................................ 3 HP StoreOnce D2D appliances and Veeam Backup ................................................................................. 4 An appliance vs. general purpose disk for data protection .................................................................... 4 Important considerations when sizing your HP StoreOnce D2D appliance ................................................. -

Veeam Disaster Recovery in Microsoft Azure Maintain Business Continuity with Next-Generation On-Demand DR in the Cloud
Solution Overview Veeam Disaster Recovery in Microsoft Azure Maintain business continuity with next-generation on-demand DR in the cloud When a disaster strikes, businesses of all sizes need a fast and reliable solution for on-demand disaster recovery (DR) in the cloud. However, even though the cloud has made DR affordable, many businesses still struggle with the complexities of establishing a solution. Today’s modern business is faced with protecting a variety of virtualized VMs, physical servers and endpoints located in multiple locations and a constantly growing amount of data making it increasingly difficult to scale and manage the protection of an organization’s most critical workloads. Further, many organizations are also unable to properly manage the complicated network setup and configuration tasks associated with establishing a cloud-based DR solution or lack the budget to maintain a staff of networking engineers to manage connectivity. Veeam Disaster Recovery in Microsoft Azure Veeam® Disaster Recovery in Microsoft Azure helps businesses of all sizes maintain business continuity and Availability for their most critical workloads with the next generation of “on- demand DR” in the cloud. It delivers cloud restore for Veeam backups to optimize resource allocation and gain new DR options, coupled with an easy to use, light-weight software defined networking solution to simplify setup and connectivity, regardless of location. © 2017 Veeam Software. Confidential information. All rights reserved. All trademarks are the property of their respective owners. 06272017 Solution Overview Direct Restore to Microsoft Azure Restore ANYTHING to Azure Restore Windows- and Linux-based VMs, physical servers or endpoints. Direct Restore to Microsoft Azure, included in Veeam Availability Suite, delivers cloud restore for Veeam backups to optimize resource allocation and gain new DR options. -

Setting up the Dell DR Series System on Veeam
Setting Up the Dell™ DR Series System on Veeam Dell Engineering April 2016 A Dell Technical White Paper Revisions Date Description January 2014 Initial release May 2014 Updated to add note to explain purpose of enabling dedupe on Veeam side. July 2014 Updated to add workflow specific best practices. April 2015 Updated with Veeam 8.0 screenshots. June 2015 Updated cleaner recommendations. November 2015 Updated with information about Instant Recovery with DR Series. April 2016 Updated with Veeam 9.0 screenshots and features. THIS WHITE PAPER IS FOR INFORMATIONAL PURPOSES ONLY, AND MAY CONTAIN TYPOGRAPHICAL ERRORS AND TECHNICAL INACCURACIES. THE CONTENT IS PROVIDED AS IS, WITHOUT EXPRESS OR IMPLIED WARRANTIES OF ANY KIND. © 2016 Dell Inc. All rights reserved. Reproduction of this material in any manner whatsoever without the express written permission of Dell Inc. is strictly forbidden. For more information, contact Dell. PRODUCT WARRANTIES APPLICABLE TO THE DELL PRODUCTS DESCRIBED IN THIS DOCUMENT MAY BE FOUND AT: http://www.dell.com/learn/us/en/19/terms-of-sale-commercial-and-public-sector Performance of network reference architectures discussed in this document may vary with differing deployment conditions, network loads, and the like. Third party products may be included in reference architectures for the convenience of the reader. Inclusion of such third party products does not necessarily constitute Dell’s recommendation of those products. Please consult your Dell representative for additional information. Trademarks used in this text: Dell™, the Dell logo, PowerVault™, EqualLogic™ are trademarks of Dell Inc. Other Dell trademarks may be used in this document. Microsoft®, Windows®, Windows Server®, Internet Explorer®, MS-DOS®, Windows Vista® and Active Directory® are either trademarks or registered trademarks of Microsoft Corporation in the United States and/or other countries. -

Optimice Veeam Backup & Replication Con Quest® Qorestor
Optimice Veeam Backup & Replication con Quest® QoreStor™ Acelere los backups y reduzca considerablemente los requisitos y los costes de almacenamiento Ahora cuenta con Veeam Backup & Con QoreStor, no solo agilizará los Replication a diario como solución de backups con los exclusivos aceleradores Con Quest QoreStor, puede protección de datos, pero el crecimiento de protocolos, sino que también reducirá acelerar significativamente exponencial de estos puede estar aún más el almacenamiento gracias a sus backups de Veeam ralentizando el proceso, afectando a la deduplicación y la compresión de sus objetivos de punto de recuperación bloques variables con reconocimiento mientras reduce el (RPO) y añadiendo riesgos innecesarios. de contenido. Asimismo, acelerará almacenamiento de backups Además, como tiene que seguir la replicación y se olvidará de las en más de un 95 %. invirtiendo en aumentar el volumen de conexiones WAN con altibajos al tiempo almacenamiento para no quedarse atrás que aprovecha la cloud para el archivado y guardar sus backups in situ o incluso en y la recuperación ante desastres por su VENTAJAS: la cloud, está consumiendo su limitado resistente tecnología de replicación. presupuesto de tecnología informática. • Reduzca los costes de QoreStor complementa su entorno de almacenamiento en las instalaciones y Con Quest® QoreStor™, puede Veeam y le ayuda a finalizar los backups en la cloud con potentes capacidades de deduplicación y compresión. acelerar significativamente sus más rápido, a reducir los costes de backups de Veeam® mientras reduce almacenamiento y a replicar en la cloud • Acelere la realización de backups el almacenamiento de backups en de una manera más ágil y segura. mediante aceleradores de protocolos más de un 95 %. -

Veeam Unternehmensportrait
Veeam Software – Unternehmensportrait Management-Software für virtualisierte IT-Umgebungen Veeam Software entwickelt Systemmanagement- und Backup-Lösungen für virtualisierte IT-Umgebungen auf Basis von VMware. Veeams Produkte sind auf die täglichen Aufgaben von Administratoren abgestimmt und decken den kompletten Management-Zyklus von der Datensicherung über Monitoring und Verwaltung bis hin zum Reporting ab. In diesem Dokument finden Sie die wichtigsten Informationen über Veeam Software im Überblick. Wenn Sie Veeam näher kennenlernen und mit einem Vertreter des Unternehmens sprechen möchten, wenden Sie sich bitte an unsere Agentur: Oseon Conversations Hr. Tapio Liller T: +49-69-25 73 80 22-1 M: +49-177-749 23 22 E: [email protected] Tw: @tapioliller 1 1. Kurzprofil Veeam Software (Veeam) entwickelt Systemmanagement-Lösungen für virtualisierte IT-Umgebungen. Wichtigste Plattform ist seit Gründung des Unternehmens im Jahr 2006 die des Marktführers VMware, deren „Pre- mier-Level Technology Alliance Partner“ Veeam ist. Die Schlüsselprodukte sind die Datensicherungslösung Veeam Backup and Replication, die Monitoring- und Berichtswerkzeuge Veeam Monitor und Reporter Enterprise, sowie das kostenlose Tool Veeam Business View, mit dessen Hilfe VMware-Umgebungen nach organisatorischen Kriterien statt nach rein technischen Gegebenheiten verwaltet werden können. Das eben- falls von Veeam stammende kostenlose Tool FastSCP wird von mehr als 100.000 VMware-Profis weltweit verwendet. Seit der Akquisition von nworks im Jahr 2008 gehören zu Veeams Pro- duktpalette auch Erweiterungen für die Systemmanagementumgebungen von Microsoft und HP. Mit ihrer Hilfe können Administratoren die Betriebs- und Leistungsdaten ihrer virtualisierten IT direkt im gewohnten Steuerung- sprogramm anzeigen. Das Unternehmen verfolgt einen schnellen Expansionskurs, der vor allem durch ein hohes Innovationstempo bei den Produkten und ein wachsendes Netz von Vertriebspartnern (derzeit mehr als 3.000 weltweit) gekennzeich- net ist.