Google Sync Integration Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Gmail for Devices.Docx
Gmail onto iPads Follow the steps below to setup Google Sync on your iPhone, iPad, or iPod Touch. Getting Started 1. Open the Settings application on your device's home screen. 2. Open Mail, Contacts, Calendars. 3. Press Add Account.... 4. Select Microsoft Exchange Enter Account Info 5. In the Email field, enter your full Google Account email address. Use your sedubois account: Example is [email protected], you may see an "Unable to verify certificate" warning when you proceed to the next step. 6. Leave the Domain field blank. 7. Enter your full Google Account email address as the Username. 8. Enter your Google Account password as the Password. 9. Tap Next at the top of your screen. 9a. Choose Cancel if the Unable to Verify Certificate dialog appears. 10. When the new Server field appears, enter m.google.com. ● To access m.google.com, set the language to English (US). 11. Press Next at the top of your screen again. Set up "Send Mail As" feature Enable "Send Mail As" feature Gmail and Google Apps users can send mail from a custom "From" address using the web browser on their iOS device or computer. 1. Sign in to Gmail using your web browser. 2. Click the gear in the top right. 3. Select Settings. 4. Select the Accounts tab. 5. Under Send mail as, click Add another email address you own. 6. In the Email address field, enter your name and alternate email address. If you want this address to be your default one, deselect Treat as an alias. -

Amicus Link Guide: Google Contacts & Calendar
Amicus Link Guide: Google Contacts & Calendar Applies to: Amicus Attorney Synchronize your Amicus and Google contacts and appointments. About the Link 2 What you need 2 Advantages of using the Link 3 Link overview 4 Synchronization direction 4 When synchronizations occur 4 Administering the Link at the firm level 5 Amicus Administrator checklist 5 Ensuring that Firm Members have access rights 5 Configuring the Link 6 Firm Member checklist 6 Special note if upgrading from an earlier version of Amicus Attorney 6 Using the Link Configuration wizard 7 Initializing the Link 14 Using the Link after initialization 16 Synchronizing information 16 Flagging individual Amicus Contacts & Appointments for synchronization 16 Preference settings for new items 17 Changing your Link configuration 18 Disabling the Link 18 Synchronization details 19 Match criteria 19 Contact synchronizations 20 Appointment synchronizations 21 Troubleshooting 23 Google Link Log 23 Resetting the Link 23 Other Important Information 24 Amicus Google Contacts & Calendar Link Guide © 2020 Abacus Data Systems Canada, Inc. 1 About the Link The Amicus Google Contacts & Calendar Link provides bi-directional synchronization that aligns your Amicus and Google Contacts and Appointments, and optionally Amicus Firm Members. And the sync is server-side. That means your Amicus workstation doesn’t have to be running when the sync takes place—a sync takes place automatically about every 15 minutes, regardless. And your assistant can do an immediate sync for you if necessary. You stay up to date when away from the office. Only Amicus Contacts and Appointments that are individually designated by you are synchronized. You select which of your Google Calendars to synchronize. -

Technology Tidbits Title
Volume 4, Issue 1 August 2017 C O L C H E S T E R I NFORMATION T E C H N O L O G Y D EPARTMENT T ECHNOLOGY TIDBITS INSIDE THIS ISSUE: Welcome Back! T ITLE Welcome Back 1 Welcome back to the Colchester School District for the 2017 – 2018 school year. We hope that Movie Creation 1 you had a fantastic summer. It is hard to believe Old Wireless 2 we are ready to start a new school year. This summer has been quite busy for IT, as we have Team Drive 3 been preparing technology for the start of the new school year. If you return to your building Android Apps 3 and/or classroom and something is not as you Windows 10 4 desire, please submit a helpdesk ticket, and we will help you as quickly as possible. Laptops for CHS Students! Interactive Projectors 5 Certain classrooms received new interactive Google Drive Sync 5 respond appropriately to your needs and projectors over the summer whereas others had to get the most out of our limited Technology Helpdesk 6 them installed towards the end of last year. If resources. I often hear when I am out in anyone needs a refresher course on how to use the buildings that technology is not the new technology, please review the article on working properly. When I inquire further, the subject later in this newsletter. If you need a it is not uncommon to learn that a more personal touch, please submit a helpdesk conversation was had with a technician in ticket. -

EN-Google Hacks.Pdf
Table of Contents Credits Foreword Preface Chapter 1. Searching Google 1. Setting Preferences 2. Language Tools 3. Anatomy of a Search Result 4. Specialized Vocabularies: Slang and Terminology 5. Getting Around the 10 Word Limit 6. Word Order Matters 7. Repetition Matters 8. Mixing Syntaxes 9. Hacking Google URLs 10. Hacking Google Search Forms 11. Date-Range Searching 12. Understanding and Using Julian Dates 13. Using Full-Word Wildcards 14. inurl: Versus site: 15. Checking Spelling 16. Consulting the Dictionary 17. Consulting the Phonebook 18. Tracking Stocks 19. Google Interface for Translators 20. Searching Article Archives 21. Finding Directories of Information 22. Finding Technical Definitions 23. Finding Weblog Commentary 24. The Google Toolbar 25. The Mozilla Google Toolbar 26. The Quick Search Toolbar 27. GAPIS 28. Googling with Bookmarklets Chapter 2. Google Special Services and Collections 29. Google Directory 30. Google Groups 31. Google Images 32. Google News 33. Google Catalogs 34. Froogle 35. Google Labs Chapter 3. Third-Party Google Services 36. XooMLe: The Google API in Plain Old XML 37. Google by Email 38. Simplifying Google Groups URLs 39. What Does Google Think Of... 40. GooglePeople Chapter 4. Non-API Google Applications 41. Don't Try This at Home 42. Building a Custom Date-Range Search Form 43. Building Google Directory URLs 44. Scraping Google Results 45. Scraping Google AdWords 46. Scraping Google Groups 47. Scraping Google News 48. Scraping Google Catalogs 49. Scraping the Google Phonebook Chapter 5. Introducing the Google Web API 50. Programming the Google Web API with Perl 51. Looping Around the 10-Result Limit 52. -

Awareness Watch™ Newsletter by Marcus P
Awareness Watch™ Newsletter By Marcus P. Zillman, M.S., A.M.H.A. http://www.AwarenessWatch.com/ V6N1 January 2008 Welcome to the V6N1 January 2008 issue of the Awareness Watch™ Newsletter. This newsletter is available as a complimentary subscription and will be issued monthly. Each newsletter will feature the following: Awareness Watch™ Featured Report Awareness Watch™ Spotters Awareness Watch™ Book/Paper/Article Review Subject Tracer™ Information Blogs I am always open to feedback from readers so please feel free to email with all suggestions, reviews and new resources that you feel would be appropriate for inclusion in an upcoming issue of Awareness Watch™. This is an ongoing work of creativity and you will be observing constant changes, constant updates knowing that “change” is the only thing that will remain constant!! Awareness Watch™ Featured Report This month’s featured report will be highlighting my Knowledge Discovery Resources 2008 Internet MiniGuide Annotated Link Compilation. These resources are constantly updated on the Knowledge Discovery Resources Subject Tracer™ Information Blog available at the following URL: http://www.KnowledgeDiscovery.info/ These resources and sites bring you the latest information and happenings in the area of Knowledge Discovery on the Internet and allow you to expand your knowledge both in discovery as well as connected and associated Internet links. 1 Awareness Watch V6N1 January 2008 Newsletter http://www.AwarenessWatch.com/ [email protected] © 2008 Marcus P. Zillman, M.S., A.M.H.A. Knowledge Discovery Resources 2008 An Internet MiniGuide Annotated Link Compilation By Marcus P. Zillman, M.S., A.M.H.A. Executive Director – Virtual Private Library [email protected] This Internet MiniGuide Annotated Link Compilation is dedicated to the latest and most competent resources for knowledge discovery available over the Internet. -

Better Alignment of Flash Storage to Mobile System Behavior
The SanDisk Brand § A global leader in storage technology § Most compelling value proposition § Unmatched innovation and IP § We are Data Champions 1 The Better Alignment of Managed Flash To System Behavior Alex Lemberg SW Manager 2 Agenda § Flash Storage in Mobile & Embedded § Real Performance Requirements § The Gap Between Synthetic and User Activities § Usage Case – Performance Peaks § How to Handle Performance Peaks in Flash Management Architecture § How it Affects the Endurance § Driver Support How to Get Better Performance? 3 Embedded Flash Memory is Everywhere IoT MOBILE WEARABLES COMPUTE HOME AUTO INDUSTRIAL 4 The “Real” Storage Performance Requirements § What is the Most Important Performance Metric? Sequential Write (MB/Sec) Sequential Read (MB/Sec) – Synthetic Benchmarks Random Write (IOPS) Random Read (IOPS) SQL Insert/Update/Delete IO Latency – System Analysis IO Flow IO Stack Level ? App Launch Time – User Experience Boot Time Multitasking Etc. 5 Getting IO Metrics – Is the Key 24-96 Hours of intensive “managed” user activity Statistics System Analysis & Research Wide platforms coverage Simulations \ Testing User Experience Various Android & Linux Versions 7 OEMs 16GB-64GB High End/Mid Range 1GB-4GB RAM EXT4/F2FS Regions 6 Enhanced Low Level Tracing Catch the Process and FS Info eMMC Device Driver Trace point eMMC Host Controller eMMC Device 7 Enhanced Low Level Tracing Allows to Gather Per-Process Stat. User Operation Context Gmail, W PS In stagram WifiDirect + Gmail 2.5K Night Suspend AppInstall + 4 K P layb ack (~16 Hours) -

Ringcentral for Google Chrome Extension User Guide Introduction 6
RingCentral for Google Chrome Extension User Guide RingCentral for Google Chrome Extension | User Guide | Contents | 2 C ontents Introduction ................................ ............................... 4 About RingCentral for Google Chrome Extension ................................ ................... 5 About this Guide ...................................................................... 5 Basics ............................................................................. 5 Installation ................................................................. 7 Verify Installation ............................................................ 8 Login ..................................................................... 9 Minimize and Close Button .................................................... 10 Options .................................................................. 11 Settings .................................................................. 12 Calling ................................................................... 13 Region .................................................................. 14 Status ................................................................... 15 Click to Dial/SMS ........................................................... 15 Authorize ................................................................. 16 Feedback ................................................................. 16 EULA and Version ........................................................... 16 Logout .................................................................. -

Or Directory?
01_599305_ffirs.qxd 7/15/05 6:50 PM Page iii Google™ Search & Rescue FOR DUMmIES‰ by Brad Hill 01_599305_ffirs.qxd 7/15/05 6:50 PM Page ii 01_599305_ffirs.qxd 7/15/05 6:50 PM Page i Google™ Search & Rescue FOR DUMmIES‰ 01_599305_ffirs.qxd 7/15/05 6:50 PM Page ii 01_599305_ffirs.qxd 7/15/05 6:50 PM Page iii Google™ Search & Rescue FOR DUMmIES‰ by Brad Hill 01_599305_ffirs.qxd 7/15/05 6:50 PM Page iv GoogleTM Search & Rescue For Dummies® Published by Wiley Publishing, Inc. 111 River Street Hoboken, NJ 07030-5774 www.wiley.com Copyright © 2005 by Wiley Publishing, Inc., Indianapolis, Indiana Published by Wiley Publishing, Inc., Indianapolis, Indiana Published simultaneously in Canada No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permit- ted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permission should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4355, or online at http://www.wiley.com/go/permissions. Trademarks: Wiley, the Wiley Publishing logo, For Dummies, the Dummies Man logo, A Reference for the Rest of Us!, The Dummies Way, Dummies Daily, The Fun and Easy Way, Dummies.com, and related trade dress are trademarks or registered trademarks of John Wiley & Sons, Inc. -

The Future of the Internet and How to Stop It the Harvard Community Has
The Future of the Internet and How to Stop It The Harvard community has made this article openly available. Please share how this access benefits you. Your story matters. Citation Jonathan L. Zittrain, The Future of the Internet -- And How to Stop It (Yale University Press & Penguin UK 2008). Published Version http://futureoftheinternet.org/ Accessed February 18, 2015 9:54:33 PM EST Citable Link http://nrs.harvard.edu/urn-3:HUL.InstRepos:4455262 Terms of Use This article was downloaded from Harvard University's DASH repository, and is made available under the terms and conditions applicable to Other Posted Material, as set forth at http://nrs.harvard.edu/urn-3:HUL.InstRepos:dash.current.terms- of-use#LAA (Article begins on next page) YD8852.i-x 1/20/09 1:59 PM Page i The Future of the Internet— And How to Stop It YD8852.i-x 1/20/09 1:59 PM Page ii YD8852.i-x 1/20/09 1:59 PM Page iii The Future of the Internet And How to Stop It Jonathan Zittrain With a New Foreword by Lawrence Lessig and a New Preface by the Author Yale University Press New Haven & London YD8852.i-x 1/20/09 1:59 PM Page iv A Caravan book. For more information, visit www.caravanbooks.org. The cover was designed by Ivo van der Ent, based on his winning entry of an open competition at www.worth1000.com. Copyright © 2008 by Jonathan Zittrain. All rights reserved. Preface to the Paperback Edition copyright © Jonathan Zittrain 2008. Subject to the exception immediately following, this book may not be reproduced, in whole or in part, including illustrations, in any form (beyond that copying permitted by Sections 107 and 108 of the U.S. -
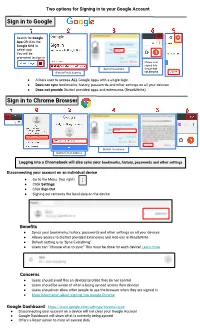
Signing in to Your Google Account File
Two options for Signing in to your Google Account Sign in to Google Search for Google App OR click the Google Grid to select app. You will be prompted to sign in Shows user signed into District Username Google but District Email Address not Chrome ● Allows user to access ALL Google Apps with a single login ● Does not sync bookmarks, history, passwords and other settings on all your devices ● Does not provide District provided apps and extensions (Read&Write) Sign in to Chrome Browser District Username District Email Address Logging into a Chromebook will also sync your bookmarks, history, passwords and other settings Disconnecting your account on an individual device ● Go to the Menu (top right) ● Click Settings ● Click Sign Out ● Signing out removes the local data on the device Benefits ● Syncs your bookmarks, history, passwords and other settings on all your devices ● Allows access to District provided Extensions and Add-ons ie Read&Write ● Default setting is to “Sync Everything” ● Users can “Choose what to sync” This must be done for each device! Learn more Concerns ● Users should avoid this on devices/profiles they do not control ● Users should be aware of what is being synced across their devices ● Users should not allow other people to use the browser when they are signed in ● More information about signing into Google Chrome Google Dashboard: https://www.google.com/settings/chrome/sync ● Disconnecting your account on a device will not clear your Google Account ● Google Dashboard will show what is currently being synced ● Offers a Reset option to clear all synced data. -

Noor Kharrat
Google and your Privacy By: Noor Kharrat Many take Google.com for granted. The number one most used website to search and the number two most visited site has recently been under criticism by many individuals and groups about its privacy. Google is based in Mountain View, California and is regulated according to US laws. This means that Google has to follow the USA Patriot Act, which is a controversial Act of Congress that U.S. President George Bush signed into law on October 26, 2001. All Google's applications and services that it opens to the public are bound under that act. Google.ca, Google.co.uk, Google.cn all fall under google.com. The servers that hold international sites for Google are still located in US grounds. The rights group "Privacy International" rated the search giant as "hostile" to privacy in a report ranking web firms by how they handle personal data. The group said Google was leading a "race to the bottom" among Internet firms many of whom had policies that did little to substantially protect users. (BBC news channel) Here are some of the reasons why Google was declared "hostile to privacy":1 • IP addresses are not considered personal information. They do not believe that they collect sensitive information. (privacyinternational.org, 2007) • Google maintains records of all search strings and the associated IP-addresses and time stamps for at least 18 to 24 months and does not provide users with an option. (privacyinternational.org, 2007) • Google has access to additional personal information, including hobbies, employment, address, and phone number, contained within user profiles in Orkut, which is a social network similar to the much popular Facebook. -

(IV) : January – March 2018
UGC University Grants Commission Journal No.: 48996 (Conference Special) Volume 6, Issue 1 (IV) January - March 2018 National Level Conference On MARKETING IN DIGITAL INDIA: TRENDS, OPPORTUNITIES & CHALLENGES 19th & 20th February, 2018 In Association with Indian Academicians and Researchers Association (IARA) website: www.iaraedu.com Best College Award in South India AICTE Approved SAQS accredited Postgraduate programs AIU equivalence for MBA programs NBA accredited Postgraduate programs ABOUT IPE The Institute of Public Enterprise (IPE) was established in 1964 for the study of issues and policies relating to public enterprises (PEs). Shri.S.S Khera, ICS, the then Cabinet Secretary, Government of India, had conceived the idea of a research institution that would undertake a systematic and sustained study of issues relevant to the formulation of policies towards public enterprises. In the early sixties, when PEs were designed as the principal instrument to serve the social and economic objectives of development, Shri. Khera felt that there was need for an institute which would collect relevant information and documents on PEs, study specific issues and undertake consultancy and training exclusively for PEs. Dr.V.V. Ramanadham, the then Professor and Head of the Department of Commerce, Osmania University, translated Shri Khera’s concept into a reality that is IPE, with the active support and guidance provided by the late Dr. D. S Reddy, then Vice-Chancellor, Osmania University as an autonomous, non-profit society at the initiative of the then Cabinet Secretary to the Government of India, Shri S.S.Khera, ICS, and late Dr.D.S.Reddy, Vice-Chancellor of Osmania University.