Enterprise Security with Mobilecho Enterprise Security from the Ground Up
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mobile First: Securing Information Sprawl
Mobile First: Securing Information Sprawl January 2014 Contents: Introduction: Addressing Information Sprawl – The Next Mobile First Challenge 2 1. Mobile First Platform: About Enterprise Mobility Management 4 2. Getting Down to Business: Managing Applications and Content 6 3. Identifying the Right Mobile Content Management Partner 7 4. Securing Information Sprawl Efficiently, Without Compromise 10 5. Designing your solution 11 415 East Middlefield Road Mountain View, CA 94043 USA Tel. +1.650.919.8100 References 15 Fax +1.650.919.8006 [email protected] 1 COPYRIGHT © 2014 MOBILEIRON. ALL RIGHTS RESERVED. Introduction: Addressing Information Sprawl – The Next Mobile First Challenge In a recent survey, “The Mobile Trust Gap,” MobileIron reported that of the 3000 respondents, 80% claimed they are using personal smartphones and tablets for work. In November 2013, 451 Research reported that 41% of enterprises increased spending on Mobile Device Management (MDM) in 2013, with 46% planning to do so in 2014. It’s clear; the question is no longer if but rather when and how businesses will bring mobile devices under management. (For a detailed discussion of how to support a multi-OS mobile device environment, please see our whitepaper: Simplifying the move from BlackBerry to Multi-OS.) So you’ve secured the device. What about the content? Once you have implemented mobile device management (MDM), the next mobile problem to address is information sprawl. Because they increasingly want access to more than just email, business users are taking advantage of the sharing and access capabilities of consumer mobile devices, including app-based cloud services. Workers now use smartphones and tablets as their primary computing endpoints and have high expectations for mobile collaboration capabilities. -

Apps Para Empresas Guía De Primeros Pasos Descubre Apps | Compra Apps | Distribuye Apps | Apps En Acción | Recursos Adicionales
Apps para empresas Guía de primeros pasos Descubre apps | Compra apps | Distribuye apps | Apps en acción | Recursos adicionales Contenido Miles de apps para el iPad y el iPhone ya están ofreciendo prestaciones revolucionarias que transforman la manera de trabajar de los empleados. El propósito de esta guía es ayudarte a descubrir y seleccionar las apps que pueden aumentar la productividad en tu empresa. También incluye información sobre las opciones para comprar y distribuir apps. Descubre apps 3 Apps en acción 21 Identifica apps para el iPad y Averigua cómo usan las apps otras el iPhone que se adaptan a las empresas para cambiar su forma de necesidades de tu empresa. trabajar. Compra apps 15 Recursos 24 Infórmate sobre las opciones Obtén más información mediante para comprar apps para tu empresa. recursos online. Distribución de aplicaciones 19 Encuentra la mejor forma de distribuir las apps entre tus empleados. Apps para empresas Guía de primeros pasos 2 Descubre apps | Compra apps | Distribuye apps | Apps en acción | Recursos adicionales Descubre apps Explora las siguientes categorías para conocer algunas de las mejores apps para empresas y descubrir las más adecuadas para tus necesidades. Acceso a archivos Gestión de clientes Edición de documentos Análisis de informes Creación de formularios Lluvias de ideas Colaboración Presentaciones Toma de notas Gestión de viajes y gastos Seguimiento, facturación y ventas Consejo rápido Diseñada para el iPad y el iPhone iPad l iPhone Versiones distintas para el iPad y el iPhone Descubre apps | Compra apps | Distribuye apps | Apps en acción | Recursos adicionales Acceso a archivos Cuando estés fuera de la oficina, usa apps para descargar archivos desde un equipo de mesa, un servicio alojado online o un sistema de gestión de contenido corporativo. -
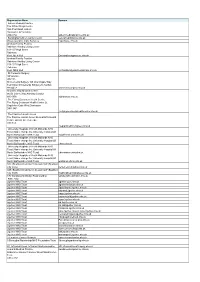
Organisation Name
Organisation Name Domain Askern Medical Practice The White Wings Centre Spa Pool Road, Askern Doncaster, S-Yorkshire DN6 0HZ askernmedicalpractice.nhs.uk Buckinghamshire County Council sexualhealthbucks.nhs.uk Gloucestershire Care Services hopehouse.nhs.uk Orchard Family Practice Rainham Healthy Living Centre 103-107 High Street Rainham Kent, ME8 8AA Orchardfamilypractice.nhs.uk Orchard Family Practice Rainham Healthy Living Centre 103-107 High Street Rainham Kent, ME8 8AA orchardfamilypracticerainham.nhs.uk St Clements Surgery GP practice D82105 St Clements Surgery 105 Churchgate Way Terrington St Clements Kings Lynn Norfolk PE344LZ stclementssurgery.nhs.uk St Johns Way Medical Centre 96 St. John's Way Archway London N19 3RN stjohnsway.nhs.uk. The Flying Scotsman Health Centre The Flying Scotsman Health Centre St. Sepulchre Gate West Doncaster DN1 3AP heflyingscotsmanhealthcentre nhs.uk The Practice Lincoln Green The Practice Lincoln Green Burmantofts Health Centre Lincoln Green Leeds LS9 7TA hepracticelincolngreen.nhs.uk University Hospitals of North Midlands NHS Trust (Name change fro: University Hospital Of North Staffordshire NHS Trust) myipfcheck.uhns.nhs.uk University Hospitals of North Midlands NHS Trust (Name change fro: University Hospital Of North Staffordshire NHS Trust) uhnm.nhs.uk University Hospitals of North Midlands NHS Trust (Name change fro: University Hospital Of North Staffordshire NHS Trust) uhnmdawn.uhns.nhs.uk University Hospitals of North Midlands NHS Trust (Name change fro: University Hospital Of North Staffordshire -

Mobilecho® Overview
OVERVIEW mobilEcho® Overview Secure Mobile File Management for Enterprise Mobility Users mobilEcho® enables enterprise IT to provide mobile users with secure access mobilEcho Benefits to enterprise file servers and SharePoint files, eliminating the headaches of employees using unsafe and non-compliant alternatives such as consumer-based services and applications. Key features: • Simple for the end-user; no mobilEcho ensures that all corporate files and assets can be securely accessed training required by the right people. mobilEcho drives business value in several ways, including: • Centralized Management • Enterprise Security • Mitigated Risk: mobilEcho ensures mobile file access adheres to your • Secure PDF Annotation corporate security policies and files are properly protected. • Two-way sync and offline file • Regulatory Compliance: mobilEcho helps organizations meet compliance access regulations regarding data and file access. This eliminates costly fines and embarrassing PR exposure. Empower Your Mobile Employees: • Reduced IT Management Cost: mobilEcho provides simple yet comprehensive • Senior Executives on-the-go tools for your IT team to ensure they meet their security, compliance and enabled to make quick management objectives in a cost-effective manner. decisions with anytime, anywhere access • Improved Employee Productivity: Mobile devices allow greater access • Sales Executives in front of to information which can improve decision-making, increase customer customers are speeding up satisfaction, and improve profitability. mobilEcho allows enterprises to the sales process with instant support both corporate-owned and employee-owned devices. access to collaterals • Field Service Workers have • Competitive Differentiation: Meet security needs and arm your employees secure access to critical docs, with the devices they want and need to better complete their tasks and meet improving productivity and SLA operational objectives that set you apart from competitors. -

Leading Green Institution Employs Mobilecho® to Reduce Waste and Streamline Productivity for Senior Staff
SUCCESS STORY Leading Green Institution Employs mobilEcho® to Reduce Waste and Streamline Productivity for Senior Staff “mobilEcho is revolutionary in the way that it enables the iPad, which was originally designed as a non-corporate product, to be used in a corporate landscape” Iain Reeman, ICT Systems Director at University of East Anglia Challenge: Key Challenges: Empower Staff to Leverage the iPad for File Access and Enable employees to leverage the iPad’s mobile More Efficient Workflow capabilities with easy access to corporate files on the university’s servers—without interfering with the In the spring of 2012, the University of East Anglia, a top-ranked university’s existing infrastructure or security standards. university in Norwich, U.K., purchazed iPads for members of some of the university’s senior management teams, in an effort to provide a Key Benefits: more efficient workflow and significantly reduce the amount of paper generated by department meetings. While the iPads made remote • mobilEcho gives employees the ability to easily email access and other browser-based tools easy enough, without on- access their files on the university server using device storage options, the university couldn’t offer employees a way their iPads without compromising university security and privacy protocols. to access files from the iPads® safely and securely. • No extra log-ins, passwords or applications are With a secure file service in place that did not support file access via required. mobile devices, the IT department simply needed to find a solution • Use of paper for the university’s senior staff has that would work within their existing infrastructure. -

Grouplogic Introduces Mobilecho 4.0, Giving Access to Sharepoint Servers
prMac: Publish Once, Broadcast the World :: http://prmac.com GroupLogic Introduces mobilEcho 4.0, Giving Access to SharePoint Servers Published on 07/31/12 GroupLogic, announces the latest version of its Mobile File Management solution, mobilEcho. mobilEcho client management improvements offer users more flexibility to edit and access files from the device of their choice. With mobilEcho 4.0, users now have access to corporate content via enterprise file servers, Network Attached Storage, and SharePoint. In addition to SharePoint integration, mobilEcho 4.0 also contains updates to client management and an administration console enhancement. Arlington, Virginia - GroupLogic(R), the industry's leading provider of software products that unlock the power of new enterprise platforms, announced today the latest version of its Mobile File Management (MFM) solution, mobilEcho. With mobilEcho 4.0, users now have access to corporate content via enterprise file servers, Network Attached Storage (NAS), and SharePoint. In addition to SharePoint integration, mobilEcho 4.0 also contains updates to client management and an administration console enhancement. "Enterprise investment in content and document management is continuing to grow, which means the use of corporate files and documents on smartphones and tablets is also increasing," said Chris Hazelton, research director, mobile & wireless, at 451 Research. "At the same time, it is necessary to keep these devices secure, especially when accessing and editing documents. Organizations need to marry the user's need for easy and convenient access to documents with the IT department's need to exhibit a level of control that ensures policies remain intact." "mobilEcho has enabled us to access documents from wherever our employees happen to be, changing how we do business and enabling us to work more efficiently," said Brandon Covert, director of information technology for the Cleveland Browns. -

451 Group 1 Context
GroupLogic extends mobile sync support with new activEcho product Analyst: Chris Hazelton Kathleen Reidy 27 Mar, 2012 GroupLogic has released activEcho, which is aimed at the mobile file-sharing and -synchronization market (aka 'Dropbox for the enterprise'). The company intends to sell activEcho directly to IT departments and position it as an alternative to consumer- and SMB-oriented file-sharing and -sync services delivered from the public cloud. ActivEcho is a companion to the mobilEcho product that GroupLogic released in May 2011. MobilEcho enables file sharing and sync for tablets and other mobile devices, while activeEcho brings in support for desktops. Both products help IT gain control of data movement in the age of 'bring your own device' (BYOD). GroupLogic faces a number of potential competitors in this market, although none is yet well established with enterprise IT departments, which are now just beginning to find alternatives to the rampant use of consumer services by employees. The 451 Take Controlling the movement of data across devices in the enterprise has always been of paramount importance, but it has become increasingly difficult to deal with in the age of BYOD. As employees demand access to corporate data on any type and number of devices, at any time, mobile file sharing and synchronization becomes a key tool for tracking and managing the movement of a company's key data. GroupLogic is building on its history of supporting Apple devices in the enterprise to deliver its own enterprise-grade synchronization service. With enterprise computing going through significant changes in the types of devices and the manner in which data is stored, GroupLogic is well positioned. -

Frequently Asked Questions
Frequently Asked Questions What is mobilEcho? mobilEcho is the industry’s first Mobile File Management (MFM) software for enterprise IT and mobile device users. mobilEcho enables enterprises to provide mobile device users with secure access to enterprise file servers, SharePoint servers, and NAS storage, eliminating the need for workarounds and third-party mobile applications that compromise the security of enterprise files and assets. Configurable and deployable across the enterprise within minutes, mobilEcho promotes efficient IT Management while ensuring corporate security and compliance standards are met. Enterprise end-users of mobilEcho can access, browse, search and interact with corporate files as well as sync files for offline access, improving overall mobile worker productivity regardless of job function. Who uses mobilEcho? Any enterprise that needs to provide secure file access from mobile devices -- from the small and medium size businesses to Fortune 1000 companies. Who benefits from mobilEcho being deployed in the Enterprise? • Employees with mobile devices will prefer mobilEcho for its speedy browsing and lightning--fast search of file names and content, all of which can be remotely administered, making their out of the box experience instantly gratifying. • IT System Administrators will prefer mobilEcho for its centralized management and easy integration into existing Windows-based tools and processes. • Businesses will benefit from mobilEcho enabling greater productivity and satisfaction from their employees while ensuring the security and compliance policies of the corporation are met. What are the key features? • Access, Browse, Preview, Sync & Search Files on corporate file servers, SharePoint servers, and NAS Devices Same, seamless and secure file access as on a PC and from your iOS or Android mobile devices. -

Smart Card Authentication
SMART CARD AUTHENTICATION Smart Card Authentication Secure CAC/PIV Mobile File Management Acronis mobilEcho® for iOS meets the needs of US DoD, Federal, State and Local governments and corporate iPhone and iPad users for simple and straightforward two-factor authenticated CAC, PIV, PIV-I and CIV smart card access to files. mobilEcho empowers employees who choose iPhones & iPads with secure, managed access to documents stored on enterprise storage including file servers, NAS such as NetApp, EMC or Isilon and SharePoint sites with built in editing for Microsoft Office files including Microsoft Word, Excel and PowerPoint. mobilEcho supports the common use of searching for a document on a server, opening and editing that document and saving the edited version back to the server, all from an iPhone or iPad. Authenticate to access files on: • Windows and any file servers accessible by SMB/CIFS • Microsoft SharePoint sites, including Office 365 hosted sites • Network Attached Storage (NAS) such as NetApp, Isilon, EMC and Western Digital Thursby Inside The Secure CAC/PIV technology is licensed from Thursby Software, Inc. The smart card technology is the same code used by the Pentagon, Army, Navy, White House, NIH and SEC across tens of thousands of Mac users since the mid 2000s. Smart Card Reader Support mobilEcho supports a variety of smart card readers including: • Thursby • Indentive iAuthenticate • Precise Biometrics Reader hardware and card are not included. Protecting the App When mobilEcho’s primary authentication is configured to use Smart Cards, the mobilEcho app will require that the user’s Smart Card is inserted into the reader before the user can use the app. -

Acronis Access (Ios)
! Using Acronis Access with MobileIron March 6, 2014 Proprietary and Confidential Do Not Distribute Overview Bundle ID: com.grouplogic.mobilecho The Access Mobile Client provides iPad and iPhone devices with secure access to files located on Windows file servers, SharePoint servers, Access Sync & Share volumes, as well as 'network reshare' access to SMB/CIFS compatible file servers (i.e., NAS devices, remote Windows Servers, Linux file servers). Acronis Access servers can optionally control the mobile application's features and security settings by configuring user and/or group policies. The Access Mobile Client application can access files on one or many Acronis Access Gateway Servers. Files can be copied or synced from servers to on- device encrypted storage within the Access Mobile Client app. These files can then be accessed even if the mobile client does not have a Wi-Fi or 3G net- work connection. The mobile app has SmartOffice integrated, which allows files to be opened and edited within the Access Mobile Client. Files can also be opened in other mobile applications, moved, copied, printed, emailed, renamed or deleted. In addition, the Acronis Access iOS client application allows PDFs to be annotat- !ed directly within the app. App availability The Acronis Access mobile app is available in the Apple App Store: https:// itunes.apple.com/app/acronis-access/id429704844 Device compatibility Access Mobile Client Application Supported devices: ▪ Apple iPad 2nd, 3rd, 4th generation Company Confiden,al .1 ▪ Apple iPad Mini 1st, 2nd generation ▪ Apple iPad Air ▪ Apple iPhone 3GS, 4, 4S, 5, 5s, 5c ▪ Apple iPod Touch 4th, 5th generation Access Mobile Client Application Supported OS's: ▪ iOS 6 or later ! ! App-specific configuration The following keys can be used with the Acronis Access app: Key Description enrollmentServerNa The value of this key should be set to the DNS me address of the Acronis Access Gateway Server that the user will enroll with. -

How to Wipe Company Data on Employees’
How to Wipe Company Data on Employees’ Mobile Devices while Leaving Personal Data Alone; Interview with GroupLogic, Part V In this final installment of our interview series with GroupLogic we look at how mobilEcho enables organizations to wipe only company data off employees’ mobile devices, leaving the employee’s personal data untouched. We also hear how GroupLogic is helping telecommunications firms increase revenue by adding value to their customers’ telecommunications experience, and we gain insight into the DNA of the company as a software provider for over 20 years. Joshua: Why is additional mobile device management needed in file-sync-and-share management, e.g can’t a customer wipe a device using Microsoft Activesync? Anders: A lot of the time it boils down to who bought the device. So if I bought the device and I bring it to work, I’m probably not going to be all that thrilled with the idea that work could wipe everything off of it. So what we do is we focus on providing secure access to content that belongs to the organization. And therefore the organization has the right to wipe that information off of the device regardless if the organization purchased it on behalf of the employee, or the employee purchased it themselves. That’s the idea. Joshua: IT leadership at your customers may eliminate corporate data without disrupting employee personal devices? Anders: Yeah. So that whole BYOD [bring your own device] trend_or consumerization trend or whatever buzzword you want to put in there_this actually really helps that. Because we just wipe the data that’s associated with mobilEcho. -

Cloud Platform Solutions
Mobile Device Management Solutions Buyer’s Guide Includes a Category Overview The Top 10 Questions to Ask Plus a Capabilities Reference of the Leading 20 Providers for Mobile Device Management Solutions Mobile Device Management Management 2015 Buyer’s Guide In this Buyers Guide, Solutions Review has chosen to highlight Mobile Device Management INTRODUCTION: (MDM) because the recent explosion of mobile devices has caused a seismic shift in how IT executives need to think about their networks. The end user – whether they are employees or students – is demanding access to networks via mobile devices and the amount of applications and data they expect to access is growing at an alarming rate. In addition, the scope of mobility management solutions is growing as well. In the past, the broadly accepted category name has been Mobile Device Management (MDM), an extension of additional functionality has resulted in a redefinition of the technology category as Enterprise Mobility Management. In your search for an MDM provider you will come to realize that many of the leading solutions now offer multiple and bundled mobility components including: 1. Mobile Device Management (MDM) 2. Mobile Application Management (MAM) 3. Mobile Content/Email Management 4. Mobile Collaboration 5. Policy and Configuration Management With all these changes in the technology and business practices one thing remains constant: The importance and necessity for IT managers to monitor track and secure business critical information being accessed through mobile devices. A task made even more daunting by the wide variety of mobile applications and operating systems that need to be considered. It is that complexity coupled with the necessity to manage and secure the range of devices that has led to a growing MDM solution sophistication.