2DI70 - Statistical Learning Theory Lecture Notes
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Warm Start for Parameter Selection of Linear Classifiers
Warm Start for Parameter Selection of Linear Classifiers Bo-Yu Chu Chia-Hua Ho Cheng-Hao Tsai Dept. of Computer Science Dept. of Computer Science Dept. of Computer Science National Taiwan Univ., Taiwan National Taiwan Univ., Taiwan National Taiwan Univ., Taiwan [email protected] [email protected] [email protected] Chieh-Yen Lin Chih-Jen Lin Dept. of Computer Science Dept. of Computer Science National Taiwan Univ., Taiwan National Taiwan Univ., Taiwan [email protected] [email protected] ABSTRACT we may need to solve many optimization problems. Sec- In linear classification, a regularization term effectively reme- ondly, if we do not know the reasonable range of the pa- dies the overfitting problem, but selecting a good regulariza- rameters, we may need a long time to solve optimization tion parameter is usually time consuming. We consider cross problems under extreme parameter values. validation for the selection process, so several optimization In this paper, we consider using warm start to efficiently problems under different parameters must be solved. Our solve a sequence of optimization problems with different reg- aim is to devise effective warm-start strategies to efficiently ularization parameters. Warm start is a technique to reduce solve this sequence of optimization problems. We detailedly the running time of iterative methods by using the solution investigate the relationship between optimal solutions of lo- of a slightly different optimization problem as an initial point gistic regression/linear SVM and regularization parameters. for the current problem. If the initial point is close to the op- Based on the analysis, we develop an efficient tool to auto- timum, warm start is very useful. -

Neural Networks and Backpropagation
CS 179: LECTURE 14 NEURAL NETWORKS AND BACKPROPAGATION LAST TIME Intro to machine learning Linear regression https://en.wikipedia.org/wiki/Linear_regression Gradient descent https://en.wikipedia.org/wiki/Gradient_descent (Linear classification = minimize cross-entropy) https://en.wikipedia.org/wiki/Cross_entropy TODAY Derivation of gradient descent for linear classifier https://en.wikipedia.org/wiki/Linear_classifier Using linear classifiers to build up neural networks Gradient descent for neural networks (Back Propagation) https://en.wikipedia.org/wiki/Backpropagation REFRESHER ON THE TASK Note “Grandmother Cell” representation for {x,y} pairs. See https://en.wikipedia.org/wiki/Grandmother_cell REFRESHER ON THE TASK Find i for zi: “Best-index” -- estimated “Grandmother Cell” Neuron Can use parallel GPU reduction to find “i” for largest value. LINEAR CLASSIFIER GRADIENT We will be going through some extra steps to derive the gradient of the linear classifier -- We’ll be using the “Softmax function” https://en.wikipedia.org/wiki/Softmax_function Similarities will be seen when we start talking about neural networks LINEAR CLASSIFIER J & GRADIENT LINEAR CLASSIFIER GRADIENT LINEAR CLASSIFIER GRADIENT LINEAR CLASSIFIER GRADIENT GRADIENT DESCENT GRADIENT DESCENT, REVIEW GRADIENT DESCENT IN ND GRADIENT DESCENT STOCHASTIC GRADIENT DESCENT STOCHASTIC GRADIENT DESCENT STOCHASTIC GRADIENT DESCENT, FOR W LIMITATIONS OF LINEAR MODELS Most real-world data is not separable by a linear decision boundary Simplest example: XOR gate What if we could combine the results of multiple linear classifiers? Combine two OR gates with an AND gate to get a XOR gate ANOTHER VIEW OF LINEAR MODELS NEURAL NETWORKS NEURAL NETWORKS EXAMPLES OF ACTIVATION FNS Note that most derivatives of tanh function will be zero! Makes for much needless computation in gradient descent! MORE ACTIVATION FUNCTIONS https://medium.com/@shrutijadon10104776/survey-on- activation-functions-for-deep-learning-9689331ba092 Tanh and sigmoid used historically. -

Lecture 2: Linear Classifiers
Lecture 2: Linear Classifiers Andr´eMartins Deep Structured Learning Course, Fall 2018 Andr´eMartins (IST) Lecture 2 IST, Fall 2018 1 / 117 Course Information • Instructor: Andr´eMartins ([email protected]) • TAs/Guest Lecturers: Erick Fonseca & Vlad Niculae • Location: LT2 (North Tower, 4th floor) • Schedule: Wednesdays 14:30{18:00 • Communication: piazza.com/tecnico.ulisboa.pt/fall2018/pdeecdsl Andr´eMartins (IST) Lecture 2 IST, Fall 2018 2 / 117 Announcements Homework 1 is out! • Deadline: October 10 (two weeks from now) • Start early!!! List of potential projects will be sent out soon! • Deadline for project proposal: October 17 (three weeks from now) • Teams of 3 people Andr´eMartins (IST) Lecture 2 IST, Fall 2018 3 / 117 Today's Roadmap Before talking about deep learning, let us talk about shallow learning: • Supervised learning: binary and multi-class classification • Feature-based linear classifiers • Rosenblatt's perceptron algorithm • Linear separability and separation margin: perceptron's mistake bound • Other linear classifiers: naive Bayes, logistic regression, SVMs • Regularization and optimization • Limitations of linear classifiers: the XOR problem • Kernel trick. Gaussian and polynomial kernels. Andr´eMartins (IST) Lecture 2 IST, Fall 2018 4 / 117 Fake News Detection Task: tell if a news article / quote is fake or real. This is a binary classification problem. Andr´eMartins (IST) Lecture 2 IST, Fall 2018 5 / 117 Fake Or Real? Andr´eMartins (IST) Lecture 2 IST, Fall 2018 6 / 117 Fake Or Real? Andr´eMartins (IST) Lecture 2 IST, Fall 2018 7 / 117 Fake Or Real? Andr´eMartins (IST) Lecture 2 IST, Fall 2018 8 / 117 Fake Or Real? Andr´eMartins (IST) Lecture 2 IST, Fall 2018 9 / 117 Fake Or Real? Can a machine determine this automatically? Can be a very hard problem, since fact-checking is hard and requires combining several knowledge sources .. -

Hyperplane Based Classification: Perceptron and (Intro
Hyperplane based Classification: Perceptron and (Intro to) Support Vector Machines Piyush Rai CS5350/6350: Machine Learning September 8, 2011 (CS5350/6350) Hyperplane based Classification September8,2011 1/20 Hyperplane Separates a D-dimensional space into two half-spaces Defined by an outward pointing normal vector w RD ∈ (CS5350/6350) Hyperplane based Classification September8,2011 2/20 Hyperplane Separates a D-dimensional space into two half-spaces Defined by an outward pointing normal vector w RD ∈ w is orthogonal to any vector lying on the hyperplane (CS5350/6350) Hyperplane based Classification September8,2011 2/20 Hyperplane Separates a D-dimensional space into two half-spaces Defined by an outward pointing normal vector w RD ∈ w is orthogonal to any vector lying on the hyperplane Assumption: The hyperplane passes through origin. (CS5350/6350) Hyperplane based Classification September8,2011 2/20 Hyperplane Separates a D-dimensional space into two half-spaces Defined by an outward pointing normal vector w RD ∈ w is orthogonal to any vector lying on the hyperplane Assumption: The hyperplane passes through origin. If not, have a bias term b; we will then need both w and b to define it b > 0 means moving it parallely along w (b < 0 means in opposite direction) (CS5350/6350) Hyperplane based Classification September8,2011 2/20 Linear Classification via Hyperplanes Linear Classifiers: Represent the decision boundary by a hyperplane w For binary classification, w is assumed to point towards the positive class (CS5350/6350) Hyperplane based Classification -

Statistical Risk Estimation for Communication System Design: Results of the HETE-2 Test Case
IPN Progress Report 42-197 • May 15, 2014 Statistical Risk Estimation for Communication System Design: Results of the HETE-2 Test Case Alessandra Babuscia* and Kar-Ming Cheung* ABSTRACT. — The Statistical Risk Estimation (SRE) technique described in this article is a methodology to quantify the likelihood that the major design drivers of mass and power of a space system meet the spacecraft and mission requirements and constraints through the design and development lifecycle. The SRE approach addresses the long-standing challenges of small sample size and unclear evaluation path of a space system, and uses a combina- tion of historical data and expert opinions to estimate risk. Although the methodology is applicable to the entire spacecraft, this article is focused on a specific subsystem: the com- munication subsystem. Using this approach, the communication system designers will be able to evaluate and to compare different communication architectures in a risk trade-off perspective. SRE was introduced in two previous papers. This article aims to present addi- tional results of the methodology by adding a new test case from a university mission, the High-Energy Transient Experiment (HETE)-2. The results illustrate the application of SRE to estimate the risks of exceeding constraints in mass and power, hence providing crucial risk information to support a project’s decision on requirements rescope and/or system redesign. I. Introduction The Statistical Risk Estimation (SRE) technique described in this article is a methodology to quantify the likelihood that the major design drivers of mass and power of a space system meet the spacecraft and mission requirements and constraints through the design and development lifecycle. -

Chapter 4 How Do We Measure Risk?
1 CHAPTER 4 HOW DO WE MEASURE RISK? If you accept the argument that risk matters and that it affects how managers and investors make decisions, it follows logically that measuring risk is a critical first step towards managing it. In this chapter, we look at how risk measures have evolved over time, from a fatalistic acceptance of bad outcomes to probabilistic measures that allow us to begin getting a handle on risk, and the logical extension of these measures into insurance. We then consider how the advent and growth of markets for financial assets has influenced the development of risk measures. Finally, we build on modern portfolio theory to derive unique measures of risk and explain why they might be not in accordance with probabilistic risk measures. Fate and Divine Providence Risk and uncertainty have been part and parcel of human activity since its beginnings, but they have not always been labeled as such. For much of recorded time, events with negative consequences were attributed to divine providence or to the supernatural. The responses to risk under these circumstances were prayer, sacrifice (often of innocents) and an acceptance of whatever fate meted out. If the Gods intervened on our behalf, we got positive outcomes and if they did not, we suffered; sacrifice, on the other hand, appeased the spirits that caused bad outcomes. No measure of risk was therefore considered necessary because everything that happened was pre-destined and driven by forces outside our control. This is not to suggest that the ancient civilizations, be they Greek, Roman or Chinese, were completely unaware of probabilities and the quantification of risk. -
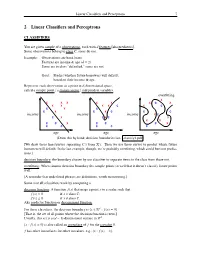
2 Linear Classifiers and Perceptrons
Linear Classifiers and Perceptrons 7 2 Linear Classifiers and Perceptrons CLASSIFIERS You are given sample of n observations, each with d features [aka predictors]. Some observations belong to class C; some do not. Example: Observations are bank loans Features are income & age (d = 2) Some are in class “defaulted,” some are not Goal: Predict whether future borrowers will default, based on their income & age. Represent each observation as a point in d-dimensional space, called a sample point / a feature vector / independent variables. overfitting X X X X X X X C X X X X X C X C C X C C X C X C C C income income income X C C X C X C X X X C C X C C C X C C C C C age age age [Draw this by hand; decision boundaries last. classify3.pdf ] [We draw these lines/curves separating C’s from X’s. Then we use these curves to predict which future borrowers will default. In the last example, though, we’re probably overfitting, which could hurt our predic- tions.] decision boundary: the boundary chosen by our classifier to separate items in the class from those not. overfitting: When sinuous decision boundary fits sample points so well that it doesn’t classify future points well. [A reminder that underlined phrases are definitions, worth memorizing.] Some (not all) classifiers work by computing a decision function: A function f (x) that maps a point x to a scalar such that f (x) > 0 if x class C; 2 f (x) 0 if x < class C. -

Machine Learning Empirical Risk Minimization
Machine Learning Empirical Risk Minimization Dmitrij Schlesinger WS2014/2015, 08.12.2014 Recap – tasks considered before n For a training dataset L = (xl, yl) ... with xl ∈ R (data) and yl ∈ {+1, −1} (classes) fing a separating hyperplane yl · [hw, xli + b] ≥ 0 ∀l → Perceptron algorithm The goal is to fing a "corridor" (stripe) of the maximal width that separates the data → Large Margin learning, linear SVM 1 kwk2 → min 2 w s.t. yl[hw, xli + b] ≥ 1 In both cases the data is assumed to be separable. What if not? ML: Empirical Risk Minimization 08.12.2014 2 Empirical Risk Minimization Let a loss function C(y, y0) be given that penalizes deviations between the true class and the estimated one (like the loss in the Bayesian Decision theory). The Empirical Risk of a decision strategy is the total loss over the training set: X R(e) = C yl, e(xl) → min e l It should bi minimized with respect to the decision strategy e. Special case (today): – the set of decisions is {+1, −1} – the loss is the delta-function C(y, y0) = δ(y 6= y0) – the decision strategy can be expressed in the form e(x) = sign f(x) with an evaluation function f : X → R Example: f(x) = hw, xi − b is a linear classifier. ML: Empirical Risk Minimization 08.12.2014 3 Hinge Loss The problem: the subject is not convex The way out: replace the real loss by its convex upper bound ← example for y = 1 (for y = −1 it should be flipped) δ y 6= sign f(x) ≤ max 0, 1 − y · f(x) It is called Hinge Loss ML: Empirical Risk Minimization 08.12.2014 4 Sub-gradient algorithm Let the evaluation function be parameterized, i.e. -

Using Linear Classifier Probes
Under review as a conference paper at ICLR 2017 UNDERSTANDING INTERMEDIATE LAYERS USING LINEAR CLASSIFIER PROBES Guillaume Alain & Yoshua Bengio Department of Computer Science and Operations Research Universite´ de Montreal´ Montreal, QC. H3C 3J7 [email protected] ABSTRACT Neural network models have a reputation for being black boxes. We propose a new method to better understand the roles and dynamics of the intermediate layers. This has direct consequences on the design of such models and it enables the expert to be able to justify certain heuristics (such as adding auxiliary losses in middle layers). Our method uses linear classifiers, referred to as “probes”, where a probe can only use the hidden units of a given intermediate layer as discriminating features. Moreover, these probes cannot affect the training phase of a model, and they are generally added after training. They allow the user to visualize the state of the model at multiple steps of training. We demonstrate how this can be used to develop a better intuition about models and to diagnose potential problems. 1 INTRODUCTION The recent history of deep neural networks features an impressive number of new methods and technological improvements to allow the training of deeper and more powerful networks. Despite this, models still have a reputation for being black boxes. Neural networks are criticized for their lack of interpretability, which is a tradeoff that we accept because of their amazing performance on many tasks. Efforts have been made to identify the role played by each layer, but it can be hard to find a meaning to individual layers. -

Statistical Machine Learning: Introduction
Statistical Machine Learning: Introduction Dino Sejdinovic Department of Statistics University of Oxford 22-24 June 2015, Novi Sad slides available at: http://www.stats.ox.ac.uk/~sejdinov/talks.html Tom Mitchell, 1997 Any computer program that improves its performance at some task through experience. Kevin Murphy, 2012 To develop methods that can automatically detect patterns in data, and then to use the uncovered patterns to predict future data or other outcomes of interest. Introduction Introduction What is Machine Learning? Arthur Samuel, 1959 Field of study that gives computers the ability to learn without being explicitly programmed. Kevin Murphy, 2012 To develop methods that can automatically detect patterns in data, and then to use the uncovered patterns to predict future data or other outcomes of interest. Introduction Introduction What is Machine Learning? Arthur Samuel, 1959 Field of study that gives computers the ability to learn without being explicitly programmed. Tom Mitchell, 1997 Any computer program that improves its performance at some task through experience. Introduction Introduction What is Machine Learning? Arthur Samuel, 1959 Field of study that gives computers the ability to learn without being explicitly programmed. Tom Mitchell, 1997 Any computer program that improves its performance at some task through experience. Kevin Murphy, 2012 To develop methods that can automatically detect patterns in data, and then to use the uncovered patterns to predict future data or other outcomes of interest. Introduction Introduction -

Loss-Based Risk Measures Rama Cont, Romain Deguest, Xuedong He
Loss-Based Risk Measures Rama Cont, Romain Deguest, Xuedong He To cite this version: Rama Cont, Romain Deguest, Xuedong He. Loss-Based Risk Measures. 2011. hal-00629929 HAL Id: hal-00629929 https://hal.archives-ouvertes.fr/hal-00629929 Submitted on 7 Oct 2011 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Loss-based risk measures Rama CONT1,3, Romain DEGUEST 2 and Xue Dong HE3 1) Laboratoire de Probabilit´es et Mod`eles Al´eatoires CNRS- Universit´ePierre et Marie Curie, France. 2) EDHEC Risk Institute, Nice (France). 3) IEOR Dept, Columbia University, New York. 2011 Abstract Starting from the requirement that risk measures of financial portfolios should be based on their losses, not their gains, we define the notion of loss-based risk measure and study the properties of this class of risk measures. We charac- terize loss-based risk measures by a representation theorem and give examples of such risk measures. We then discuss the statistical robustness of estimators of loss-based risk measures: we provide a general criterion for qualitative ro- bustness of risk estimators and compare this criterion with sensitivity analysis of estimators based on influence functions. -

Statistical Regularization and Learning Theory 1 Three Elements
ECE901 Spring 2004 Statistical Regularization and Learning Theory Lecture: 1 Statistical Regularization and Learning Theory Lecturer: Rob Nowak Scribe: Rob Nowak 1 Three Elements of Statistical Data Analysis 1. Probabilistic Formulation of learning from data and prediction problems. 2. Performance Characterization: concentration inequalities uniform deviation bounds approximation theory rates of convergence 3. Practical Algorithms that run in polynomial time (e.g., decision trees, wavelet methods, support vector machines). 2 Learning from Data To formulate the basic learning from data problem, we must specify several basic elements: data spaces, probability measures, loss functions, and statistical risk. 2.1 Data Spaces Learning from data begins with a specification of two spaces: X ≡ Input Space Y ≡ Output Space The input space is also sometimes called the “feature space” or “signal domain.” The output space is also called the “class label space,” “outcome space,” “response space,” or “signal range.” Example 1 X = Rd d-dimensional Euclidean space of “feature vectors” Y = {0, 1} two classes or “class labels” Example 2 X = R one-dimensional signal domain (e.g., time-domain) Y = R real-valued signal A classic example is estimating a signal f in noise: Y = f(X) + W where X is a random sample point on the real line and W is a noise independent of X. 1 Statistical Regularization and Learning Theory 2 2.2 Probability Measure and Expectation Define a joint probability distribution on X × Y denoted PX,Y . Let (X, Y ) denote a pair of random variables distributed according to PX,Y . We will also have use for marginal and conditional distributions.