Elinux Status
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Internet of Things Meets Brain-Computer Interface: a Unified Deep Learning Framework for Enabling Human-Thing Cognitive Interactivity
JOURNAL OF LATEX CLASS FILES, VOL. 14, NO. 8, AUGUST 2015 1 Internet of Things Meets Brain-Computer Interface: A Unified Deep Learning Framework for Enabling Human-Thing Cognitive Interactivity Xiang Zhang, Student Member, IEEE, Lina Yao, Member, IEEE, Shuai Zhang, Student Member, IEEE, Salil Kanhere, Member, IEEE, Michael Sheng, Member, IEEE, and Yunhao Liu, Fellow, IEEE Abstract—A Brain-Computer Interface (BCI) acquires brain signals, analyzes and translates them into commands that are relayed to actuation devices for carrying out desired actions. With the widespread connectivity of everyday devices realized by the advent of the Internet of Things (IoT), BCI can empower individuals to directly control objects such as smart home appliances or assistive robots, directly via their thoughts. However, realization of this vision is faced with a number of challenges, most importantly being the issue of accurately interpreting the intent of the individual from the raw brain signals that are often of low fidelity and subject to noise. Moreover, pre-processing brain signals and the subsequent feature engineering are both time-consuming and highly reliant on human domain expertise. To address the aforementioned issues, in this paper, we propose a unified deep learning based framework that enables effective human-thing cognitive interactivity in order to bridge individuals and IoT objects. We design a reinforcement learning based Selective Attention Mechanism (SAM) to discover the distinctive features from the input brain signals. In addition, we propose a modified Long Short-Term Memory (LSTM) to distinguish the inter-dimensional information forwarded from the SAM. To evaluate the efficiency of the proposed framework, we conduct extensive real-world experiments and demonstrate that our model outperforms a number of competitive state-of-the-art baselines. -

Create an Email with Subject Title “Embedded Software Engineer”, Email a Copy of Your Resume to [email protected]
To Apply for This Position: Create an email with subject title “Embedded Software Engineer”, email a copy of your resume to [email protected] Location Address: ALLEN PARK, MI,48101 Position Description: TITLE: Embedded Software Engineer ‐ Hypervisor OS technologies This position is responsible to develop QNX and Android operating system images for Ford infotainment products. This includes creating and integrating code for: bootloader, kernel, drivers, type 1 hypervisor, and build environment. Skills Required: • Lead the design, bring‐up and support of QNX and Android operating system images • Create virt‐io drivers for QNX or Android guest operating systems • Participate in root cause analysis of hardware quality problems and software defects • Participate in system design, documentation, and testing to deliver a best‐in‐class infotainment system Experience Required: • 5+ years operating system experience involving Linux or QNX • 5+ years C/C++ software development experience on embedded, mobile, or consumer electronic platforms Experience Preferred: • Experience with Type 1 hypervisors • Experience creating virt‐io drivers • Mastery of C/C++ language, GNU tool chain, and Unix (QNX, Linux, or equivalent) • Experience with embedded build systems including QNX system builder, buildroot, yocto, or equivalent • Knowledge of in‐vehicle signaling and communication mechanisms such as CAN • Proficiency with revision control including Git, Subversion, or equivalent • Multi‐site software project team experience Education Required: • Bachelor's degree in Computer Engineering, Electrical Engineering, Computer Science, or related Education Preferred: • Master's degree in Computer Engineering, Electrical Engineering or Computer Science Additional Information: Web Based Assessment not required for this position. Visa Sponsorship and Domestic Relocation is available for this position. -

The Internet of Things (Iot): an Overview
Updated February 12, 2020 The Internet of Things (IoT): An Overview The Internet of Things (IoT) is a system of interrelated incorporation of IIoT and analytics is viewed by experts as devices connected to a network and/or to one another, the Fourth Industrial Revolution, or 4IR. exchanging data without necessarily requiring human-to- machine interaction. In other words, IoT is a collection of Internet of Medical Things (IoMT): The healthcare field electronic devices that can share information among has begun incorporating IoT, creating the Internet of themselves. Examples include smart factories, smart home Medical Things (IoMT). These devices, such as heart devices, medical monitoring devices, wearable fitness monitors and pace makers, collect and send patient health trackers, smart city infrastructures, and vehicular statistics over various networks to healthcare providers for telematics. Potential issues for Congress include regulation, monitoring, analysis, and remote configuration. At a digital privacy, and data security as discussed below. personal health level, wearable IoT devices, such as fitness trackers and smart watches, can track a user’s physical IoT Characteristics activities, basic vital data, and sleeping patterns. According IoT devices are often called “smart” devices because they to a 2019 survey by Pew Research, about one-in-five have sensors and can conduct complex data analytics. IoT Americans uses a smart watch or fitness tracker. devices collect data using sensors and offer services to the user based on the analyses of that data and according to Smart Cities: IoT devices and systems in the utilities, user-defined parameters. For example, a smart refrigerator transportation, and infrastructure sectors may be grouped uses sensors (e.g., cameras) to inventory stored items and under the category of “smart city.” Utilities can use IoT to can alert the user when items run low based on image create “smart” grids and meters for electricity, water, and recognition analyses. -

Fog Computing: a Platform for Internet of Things and Analytics
Fog Computing: A Platform for Internet of Things and Analytics Flavio Bonomi, Rodolfo Milito, Preethi Natarajan and Jiang Zhu Abstract Internet of Things (IoT) brings more than an explosive proliferation of endpoints. It is disruptive in several ways. In this chapter we examine those disrup- tions, and propose a hierarchical distributed architecture that extends from the edge of the network to the core nicknamed Fog Computing. In particular, we pay attention to a new dimension that IoT adds to Big Data and Analytics: a massively distributed number of sources at the edge. 1 Introduction The “pay-as-you-go” Cloud Computing model is an efficient alternative to owning and managing private data centers (DCs) for customers facing Web applications and batch processing. Several factors contribute to the economy of scale of mega DCs: higher predictability of massive aggregation, which allows higher utilization with- out degrading performance; convenient location that takes advantage of inexpensive power; and lower OPEX achieved through the deployment of homogeneous compute, storage, and networking components. Cloud computing frees the enterprise and the end user from the specification of many details. This bliss becomes a problem for latency-sensitive applications, which require nodes in the vicinity to meet their delay requirements. An emerging wave of Internet deployments, most notably the Internet of Things (IoTs), requires mobility support and geo-distribution in addition to location awareness and low latency. We argue that a new platform is needed to meet these requirements; a platform we call Fog Computing [1]. We also claim that rather than cannibalizing Cloud Computing, F. Bonomi R. -

The Internet of Things: Impact on Public Safety Communications
Cybersecurity and Infrastructure Security Agency The Internet of Things March 2019 The Internet of Things: Impact on Public Safety Communications The Internet of Things (IoT) is the network of physical devices and connectivity that enables objects to connect to one another, to the Internet, and exchange data amongst themselves.1, 2 IoT allows connected devices to be sensed or controlled remotely across network infrastructures, creating opportunities for more direct, cross-platform integration and improved efficiencies for the transfer of data between devices. IoT presents undeniable implications for public safety IoT goes beyond simply connecting communications. In turn, comprehensively addressing the objects to the Internet; it allows ever-growing IoT environment presents a unique challenge to physical objects to intelligently self- service providers, equipment manufacturers, and consumers. identify and communicate with other Harnessing network architecture changes and equipping devices, creating a new model of everyday objects to be IoT-enabled will allow public safety information sharing with a variety of stakeholders to maximize existing infrastructure investments potential applications. and provide near-real time decision support experiences that can change how they operate. IoT Benefits IoT-enabled devices can provide numerous benefits to public safety, as shown in Table 1. For example, a traffic accident response team could use the data collected from a variety of Internet-connected devices ― such as the involved vehicles (e.g., -

Home Automation System Using Google Assistant
© 2021 JETIR June 2021, Volume 8, Issue 6 www.jetir.org (ISSN-2349-5162) HOME AUTOMATION SYSTEM USING GOOGLE ASSISTANT MUDASIR M, NEHA V, NIHAAL THATHIR K, PAVAN YADAV M, POLLARPU SREERAMULU, SMITHA PATIL B.Tech. Student, Department of Computer Science and Engineering, Presidency University, Bangalore, India B.Tech. Student, Department of Computer Science and Engineering, Presidency University, Bangalore, India B.Tech. Student, Department of Computer Science and Engineering, Presidency University, Bangalore, India B.Tech. Student, Department of Computer Science and Engineering, Presidency University, Bangalore, India B.Tech. Student, Department of Computer Science and Engineering, Presidency University, Bangalore, India Assistant Professor, Department of Computer Science and Engineering, Presidency University, Bangalore, India Abstract: Nowadays Technology keeps on upgrading. The idea behind Google assistant-controlled Home automation is to control home devices with voice. On the market there are many devices available to do that, but making our own is awesome. In this project, the Google assistant requires voice commands. Adafruit account which is a cloud based free IoT web server used to create virtual switches, is linking to IFTTT website abbreviated as “If This Than That” which is used to create if else conditional statements. The voice commands for Google assistant have been added through IFTTT website. In this home automation, as the user gives commands to the Google assistant, Home appliances like Bulb, Fan and Motor etc., can be controlled accordingly. The commands given through the Google assistant are decoded and then sent to the microcontroller, the microcontroller in turn control the relays connected to it. The device connected to the respective relay can be turned ON or OFF as per the users request to the Google Assistant. -

Predictive Analysis of 3D Reram-Based PUF for Securing the Internet of Things
Predictive Analysis of 3D ReRAM-based PUF for Securing the Internet of Things Jeeson Kim Hussein Nili School of Engineering Electrical and Computer Engineering RMIT University University of California Santa Barbara Melbourne, Australia Santa Barbara, USA [email protected] [email protected] Gina C. Adam Nhan Duy Truong Electrical and Computer Engineering School of Engineering University of California Santa Barbara RMIT University Santa Barbara, USA Melbourne, Australia gina [email protected] [email protected] Dmitri B. Strukov Omid Kavehei Electrical and Computer Engineering Electrical and Information Engineering University of California Santa Barbara The University of Sydney Santa Barbara, USA Sydney, Australia [email protected] [email protected] Abstract—In recent years, an explosion of IoT devices challenge [2, 3]. Widely used traditional cryptographic and its use leads threats to the privacy and security solutions, for example, advanced encryption standard concerns of individual users and merchandises. As one (AES) and elliptic curve cryptography (ECC), can be of promising solutions, physical unclonable function (PUF) has been extensively studied. This paper investigates quality used for both the integrity and the authentication of of randomness in the first generation of 3D analog ReRAM exchanging data and messages. PUF primitives using measured and gathered data from IoT hardware anti-counterfeiting, integrated circuit fabricated ReRAM crossbars. This study is significant as (IC) trust and physical tampering are also critical the randomness quality of a PUF directly relates to its tasks [4]. In 2014, defense advanced research projects resilience against various model-building attacks, includ- ing machine learning attack. -

Paving the Way for Self-Driving Vehicles”
June 13, 2017 The Honorable John Thune, Chairman The Honorable Bill Nelson, Ranking Member U.S. Senate Committee on Commerce, Science & Transportation 512 Dirksen Senate Office Building Washington, DC 20510 RE: Hearing on “Paving the Way for Self-Driving Vehicles” Dear Chairman Thune and Ranking Member Nelson: We write to your regarding the upcoming hearing “Paving the Way for Self-Driving Vehicles,”1 on the privacy and safety risks of connected and autonomous vehicles. For more than a decade, the Electronic Privacy Information Center (“EPIC”) has warned federal agencies and Congress about the growing risks to privacy resulting from the increasing collection and use of personal data concerning the operation of motor vehicles.2 EPIC was established in 1994 to focus public attention on emerging privacy and civil liberties issues. EPIC engages in a wide range of public policy and litigation activities. EPIC testified before the House of Representatives in 2015 on “the Internet of Cars.”3 Recently, EPIC 1 Paving the Way for Self-Driving Vehicles, 115th Cong. (2017), S. Comm. on Commerce, Science, and Transportation, https://www.commerce.senate.gov/public/index.cfm/pressreleases?ID=B7164253-4A43- 4B70-8A73-68BFFE9EAD1A (June 14, 2017). 2 See generally EPIC, “Automobile Event Data Recorders (Black Boxes) and Privacy,” https://epic.org/privacy/edrs/. See also EPIC, Comments, Docket No. NHTSA-2002-13546 (Feb. 28, 2003), available at https://epic.org/privacy/drivers/edr_comments.pdf (“There need to be clear guidelines for how the data can be accessed and processed by third parties following the use limitation and openness or transparency principles.”); EPIC, Comments on Federal Motor Vehicle Safety Standards; V2V Communications, Docket No. -

OS Selection for Dummies
OS SELECTION HOW TO CHOOSE HOW TO CHOOSE Choosing your OS is the first step, so take the time to consider your choice fully. There are many parameters to take into account: l Is this a new project or the evolution of an existing product? l Using the same SW stack? Re-using existing code? l Is your team familiar with a particular OS? Ø Using an OS you are already comfortable with can help l What are the HW constraints of your system? Ø Some operating systems require more memory/processing power than others l Have no SW team? Not sure about the above? Ø Contact us so we can help you decide! Ø We can also introduce you to one of our many partners! 1 OS SELECTION OPEN SOURCE VS. COMMERCIAL OS Embedded OS BSP Provider $ Cost Open-Source OS Boundary Devices • Embedded Linux / Android Embedded Linux $0, included • Large pool of developers available with Board Purchase • Strong community • Royalty-free And / or partners 3rd Party - Commercial OS Partners • QNX / Win10 IoT / Green Hills $>0, depends on • Professional support requirements • Unique set of development tools 2 OS SELECTION OPEN SOURCE SELECTION OS SELECTION PROS CONS Embedded Linux Most powerful / optimized Complexity for newcomers solution, maintained by NXP • Build systems Ø Yocto / Buildroot Simpler solution, makefile- Not as flexible as Yocto Ø Everything built from scratch based, maintained by BD Desktop-like approach, Harder to customize, non- Package-based distribution easy-to-use atomic updates, no cross- • Ubuntu / Debian compilation SDK Apt install / update, millions • Packages installed from server of prebuilt packages available Android Millions of apps available, same number of developers, Resource-hungry, complex • AOSP-based (no GMS) development environment, BSP modifications (HAL) • APK applications IDE + debugging tools 3 SOFTWARE PARTNERS Boundary Devices has an industry-leading group of software partners. -

Internet of Things
INTERNET OF THINGS Internet of Things (IoT) or smart devices refers to any object or device that is connected to the Internet. This rapidly expanding set of “things,” which can send and receive data, includes cars, appliances, smart watches, lighting, home assistants, home security, and more. #BeCyberSmart to connect with confidence and protect your interconnected world. WHY SHOULD WE CARE? • Cars, appliances, wearables, lighting, healthcare, and home security all contain sensing devices that can talk to another machine and trigger other actions. Examples include devices that direct your car to an open spot in a parking lot; mechanisms that control energy use in your home; and tools that track eating, sleeping, and exercise habits. • New Internet-connected devices provide a level of convenience in our lives, but they require that we share more information than ever. • The security of this information, and the security of these devices, is not always guaranteed. Once your device connects to the Internet, you and your device could potentially be vulnerable to all sorts of risks. • With more connected “things” entering our homes and our workplaces each day, it is important that everyone knows how to secure their digital lives. SIMPLE TIPS TO OWN IT. • Shake up your password protocol. Change your device’s factory security settings from the default password. This is one of the most important steps to take in the protection of IoT devices. According to NIST guidance, you should consider using the longest password or passphrase permissible. Get creative and create a unique password for your IoT devices. Read the Creating a Password Tip Sheet for more information. -
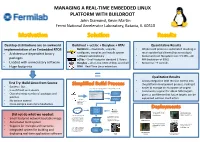
MANAGING a REAL-TIME EMBEDDED LINUX PLATFORM with BUILDROOT John Diamond, Kevin Martin Fermi National Accelerator Laboratory, Batavia, IL 60510
MANAGING A REAL-TIME EMBEDDED LINUX PLATFORM WITH BUILDROOT John Diamond, Kevin Martin Fermi National Accelerator Laboratory, Batavia, IL 60510 Desktop distributions are an awkward Buildroot + ucLibc + Busybox + RTAI Quantitative Results implementation of an Embedded RTOS Buildroot – downloads, unpacks, • Whole build process is automated resulting in • Architecture-dependent binary configures, compiles and installs system much quicker build times (hours not days) software automatically • Kernel and root filesystem size: 3.5 MB – 20 packages uClibc – Small-footprint standard C library MB (reduction of 99%) • Loaded with unnecessary software Busybox – all-in-one UNIX utilities and shell • Boot-time: ~9 seconds • Huge footprints RTAI – Real-Time Linux extensions = Qualitative Results • Allows integration with revision control into First Try: Build Linux from Source the platform development process, making it • Success! But.. 2. Buildroot’s menuconfig generates a package configuration file easier to manage an ecosystem of targets • Is as difficult as it sounds and kernel configuration file • Community support for x86 & ARM targets Linux Kernel • Overwhelming number of packages and Configuration gives us confidence that future targets can be patches Package supported without much effort 1. Developer Configuration • No version control configures build via Buildroot’s • Cross-compile even more headaches menuconfig Internet Build Process Power Supply Control Quench Protection Git / CVS / SVN and Regulation for the System for Tevatron Did not do what we needed: Fermilab Linac Electron Lens (TEL II) 3. The build process pulls 4. The output from the software packages from build process is a kernel • Small-footprint network bootable image the internet and custom bzImage bzImage file with an softare packages from a integrated root filesystem ARM Cortex A-9 source code repository file PC/104 AMD • Automated build system Geode SBC Beam Position Monitor Power Supply Control prototype for Fermilab and Regulation for • Support for multiple architectures 5. -

Linux Based Mobile Operating Systems
INSTITUTO SUPERIOR DE ENGENHARIA DE LISBOA Área Departamental de Engenharia de Electrónica e Telecomunicações e de Computadores Linux Based Mobile Operating Systems DIOGO SÉRGIO ESTEVES CARDOSO Licenciado Trabalho de projecto para obtenção do Grau de Mestre em Engenharia Informática e de Computadores Orientadores : Doutor Manuel Martins Barata Mestre Pedro Miguel Fernandes Sampaio Júri: Presidente: Doutor Fernando Manuel Gomes de Sousa Vogais: Doutor José Manuel Matos Ribeiro Fonseca Doutor Manuel Martins Barata Julho, 2015 INSTITUTO SUPERIOR DE ENGENHARIA DE LISBOA Área Departamental de Engenharia de Electrónica e Telecomunicações e de Computadores Linux Based Mobile Operating Systems DIOGO SÉRGIO ESTEVES CARDOSO Licenciado Trabalho de projecto para obtenção do Grau de Mestre em Engenharia Informática e de Computadores Orientadores : Doutor Manuel Martins Barata Mestre Pedro Miguel Fernandes Sampaio Júri: Presidente: Doutor Fernando Manuel Gomes de Sousa Vogais: Doutor José Manuel Matos Ribeiro Fonseca Doutor Manuel Martins Barata Julho, 2015 For Helena and Sérgio, Tomás and Sofia Acknowledgements I would like to thank: My parents and brother for the continuous support and being the drive force to my live. Sofia for the patience and understanding throughout this challenging period. Manuel Barata for all the guidance and patience. Edmundo Azevedo, Miguel Azevedo and Ana Correia for reviewing this document. Pedro Sampaio, for being my counselor and college, helping me on each step of the way. vii Abstract In the last fifteen years the mobile industry evolved from the Nokia 3310 that could store a hopping twenty-four phone records to an iPhone that literately can save a lifetime phone history. The mobile industry grew and thrown way most of the proprietary operating systems to converge their efforts in a selected few, such as Android, iOS and Windows Phone.