Spirent Testcenter™
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mist Teleworker ME
MIST TELEWORKER GUIDE Experience the corporate network @ home DOCUMENT OWNERS: Robert Young – [email protected] Slava Dementyev – [email protected] Jan Van de Laer – [email protected] 1 Table of Contents Solution Overview 3 How it works 5 Configuration Steps 6 Setup Mist Edge 6 Configure and prepare the SSID 15 Enable Wired client connection via ETH1 / Module port of the AP 16 Enable Split Tunneling for the Corp SSID 17 Create a Site for Remote Office Workers 18 Claim an AP and ship it to Employee’s location 18 Troubleshooting 20 Packet Captures on the Mist Edge 23 2 Solution Overview Mist Teleworker solution leverages Mist Edge for extending a corporate network to remote office workers using an IPSEC secured L2TPv3 tunnel from a remote Mist AP. In addition, MistEdge provides an additional RadSec service to securely proxy authentication requests from remote APs to provide the same user experience as inside the office. WIth Mist Teleworker solution customers can extend their corporate WLAN to employee homes whenever they need to work remotely, providing the same level of security and access to corporate resources, while extending visibility into user network experience and streamlining IT operations even when employees are not in the office. What are the benefits of the Mist Teleworker solution with Mist Edge compared to all the other alternatives? Agility: ● Zero Touch Provisioning - no AP pre-staging required, support for flexible all home coverage with secure Mesh ● Exceptional support with minimal support - leverage Mist SLEs and Marvis Actions Security: ● Traffic Isolation - same level of traffic control as in the office. -

Brocade Vyatta Network OS Data Sheet
DATA SHEET Brocade Vyatta Network OS HIGHLIGHTS A Network Operating System for the Way Forward • Offers a proven, modern network The Brocade® Vyatta® Network OS lays the foundation for a flexible, easy- operating system that accelerates the adoption of next-generation to-use, and high-performance network services architecture capable of architectures meeting current and future network demands. The operating system was • Creates an open, programmable built from the ground up to deliver robust network functionality that can environment to enhance be deployed virtually or as an appliance, and in concert with solutions differentiation, service quality, and from a large ecosystem of vendors, to address various Software-Defined competitiveness Networking (SDN) and Network Functions Virtualization (NFV) use cases. • Supports a broad ecosystem for With the Brocade Vyatta Network OS, organizations can bridge the gap optimal customization and service between traditional and new architectures, as well as leverage existing monetization investments and maximize operational efficiencies. Moreover, they can • Simplifies and automates network compose and deploy unique, new services that will drive differentiation functions to improve time to service, increase operational efficiency, and and strengthen competitiveness. reduce costs • Delivers breakthrough performance flexibility, performance, and operational and scale to meet the needs of any A Proven, Modern Operating efficiency, helping organizations create deployment System The Brocade Vyatta Network OS new service offerings and value. Since • Provides flexible deployment options separates the control and data planes in 2012, the benefits of this operating to support a wide variety of use cases software to fit seamlessly within modern system have been proven by the Brocade SDN and NFV environments. -

Brocade Vyatta Network OS LAN Interfaces Configuration Guide, 5.2R1
CONFIGURATION GUIDE Brocade Vyatta Network OS LAN Interfaces Configuration Guide, 5.2R1 Supporting Brocade 5600 vRouter, VNF Platform, and Distributed Services Platform 53-1004724-01 24 October 2016 © 2016, Brocade Communications Systems, Inc. All Rights Reserved. Brocade, the B-wing symbol, and MyBrocade are registered trademarks of Brocade Communications Systems, Inc., in the United States and in other countries. Other brands, product names, or service names mentioned of Brocade Communications Systems, Inc. are listed at www.brocade.com/en/legal/ brocade-Legal-intellectual-property/brocade-legal-trademarks.html. Other marks may belong to third parties. Notice: This document is for informational purposes only and does not set forth any warranty, expressed or implied, concerning any equipment, equipment feature, or service offered or to be offered by Brocade. Brocade reserves the right to make changes to this document at any time, without notice, and assumes no responsibility for its use. This informational document describes features that may not be currently available. Contact a Brocade sales office for information on feature and product availability. Export of technical data contained in this document may require an export license from the United States government. The authors and Brocade Communications Systems, Inc. assume no liability or responsibility to any person or entity with respect to the accuracy of this document or any loss, cost, liability, or damages arising from the information contained herein or the computer programs that accompany it. The product described by this document may contain open source software covered by the GNU General Public License or other open source license agreements. To find out which open source software is included in Brocade products, view the licensing terms applicable to the open source software, and obtain a copy of the programming source code, please visit http://www.brocade.com/support/oscd. -

What Is a Virtual Private Network?
C H A P T E R 1 What Is a Virtual Private Network? A virtual private network (VPN) allows the provisioning of private network services for an organization or organizations over a public or shared infrastructure such as the Internet or service provider backbone network. The shared service provider backbone network is known as the VPN backbone and is used to transport traffic for multiple VPNs, as well as possibly non-VPN traffic. VPNs provisioned using technologies such as Frame Relay and Asynchronous Transfer Mode (ATM) virtual circuits (VC) have been available for a long time, but over the past few years IP and IP/Multiprotocol Label Switching (MPLS)-based VPNs have become more and more popular. This book focuses on describing the deployment of IP- and IP/MPLS-based VPNs. The large number of terms used to categorize and describe the functionality of VPNs has led to a great deal of confusion about what exactly VPNs are and what they can do. The sections that follow cover VPN devices, protocols, technologies, as well as VPN categories and models. VPN Devices Before describing the various VPN technologies and models, it is useful to first describe the various customer and provider network devices that are relevant to the discussion. Devices in the customer network fall into one of two categories: • Customer (C) devices—C devices are simply devices such as routers and switches located within the customer network. These devices do not have direct connectivity to the service provider network. C devices are not aware of the VPN. • Customer Edge (CE) devices—CE devices, as the name suggests, are located at the edge of the customer network and connect to the provider network (via Provider Edge [PE] devices). -

Time-Sensitive Networks Over 5G
Time-sensitive networks over 5G Bachelor’s thesis Häme University of Applied Sciences Information and Communications Technology Spring 2020 Kaarlo Skogberg TIIVISTELMÄ Tieto- ja viestintätekniikka Hämeen Ammattikorkeakoulu Tekijä Kaarlo Skogberg Vuosi 2020 Työn nimi Aikakriittiset verkot 5G:n yli Työn ohjaaja /t Marko Grönfors (HAMK), Toni Huusko, Juhani Kerovuori TIIVISTELMÄ Opinnäytetyön tarkoitus oli tuottaa vertailu reaaliaikaisista kommunikaa- tiokeinoista nosturin ja etäohjausaseman välille 5G-mobiiliverkon yli. Kent- täväyliä tarvitaan nosturin kanssa kommunikointiin, mutta koska nämä ovat pääosin tason 2 protokollia ja eivät reitity luontaisesti 5G-verkossa täytyy kenttäväylän verkkoliikenne tunneloida. Työssä tutkittiin erilaisia Ethernet-pohjaisia kenttäväyliä sekä tunnelointiteknologioita, jotka kyke- nevät tunneloimaan tason 2 verkkoliikennettä. Tason 2 tunnelointi mah- dollistaa suoran kommunikaation kahden paikallisverkon välillä. Kaikkien työssä tutkittujen Ethernet-pohjaisten kenttäväylien sekä tunnelointipro- tokollien täytyi olla sopivia käytettäväksi teollisessa ympäristössä valituilla verkkolaitteistolla. Työtä varten tutkitun tiedon perusteella esitetään, että käytettävä kenttä- väylä sekä tunnelointiprotokolla tulisi valita saatavilla olevan verkkolait- teiston sekä muun infrastruktuurin perusteella. Kenttäväylää valittaessa reaaliaikaiset vaatimukset olivat käyttötarkoitukseen nähden kevyet, joka avaa enemmän vaihtoehtoja kenttäväylää valittaessa. Yrityksessä käyte- tään jo Profinetia, joka soveltuu mainiosti käyttötarkoitukseen. -

Vyos Documentation Release Current
VyOS Documentation Release current VyOS maintainers and contributors Jun 04, 2019 Contents: 1 Installation 3 1.1 Verify digital signatures.........................................5 2 Command-Line Interface 7 3 Quick Start Guide 9 3.1 Basic QoS................................................ 11 4 Configuration Overview 13 5 Network Interfaces 17 5.1 Interface Addresses........................................... 18 5.2 Dummy Interfaces............................................ 20 5.3 Ethernet Interfaces............................................ 20 5.4 L2TPv3 Interfaces............................................ 21 5.5 PPPoE.................................................. 23 5.6 Wireless Interfaces............................................ 25 5.7 Bridging................................................. 26 5.8 Bonding................................................. 27 5.9 Tunnel Interfaces............................................. 28 5.10 VLAN Sub-Interfaces (802.1Q)..................................... 31 5.11 QinQ................................................... 32 5.12 VXLAN................................................. 33 5.13 WireGuard VPN Interface........................................ 37 6 Routing 41 6.1 Static................................................... 41 6.2 RIP.................................................... 41 6.3 OSPF................................................... 42 6.4 BGP................................................... 43 6.5 ARP................................................... 45 7 -

Preview - Click Here to Buy the Full Publication
This is a preview - click here to buy the full publication IEC TR 62357-200 ® Edition 1.0 2015-07 TECHNICAL REPORT colour inside Power systems management and associated information exchange – Part 200: Guidelines for migration from Internet Protocol version 4 (IPv4) to Internet Protocol version 6 (IPv6) INTERNATIONAL ELECTROTECHNICAL COMMISSION ICS 33.200 ISBN 978-2-8322-2795-4 Warning! Make sure that you obtained this publication from an authorized distributor. ® Registered trademark of the International Electrotechnical Commission This is a preview - click here to buy the full publication – 2 – IEC TR 62357-200:2015 © IEC 2015 CONTENTS FOREWORD ........................................................................................................................... 6 INTRODUCTION ..................................................................................................................... 8 1 Scope .............................................................................................................................. 9 2 Normative references ...................................................................................................... 9 3 Terms, definitions, abbreviated terms, acronyms and conventions ................................. 13 3.1 Terms and definitions ............................................................................................ 13 3.2 Abbreviations ........................................................................................................ 14 3.3 Conventions ......................................................................................................... -

Implementing SES Network Duplication a Best Practices Guide
Implementing SES Network Duplication A Best Practices Guide. SIP Enablement Services 5.1 Avaya ABSTRACT This application note is a tutorial on Avaya SIP Enablement Services Network Duplication from a implementation focus. SES Network Duplication basics, protocol examples and rationale are discussed as a Best Practice. The customer is always free to implement SES Network Duplication in any other method they choose for any reasons. The intent of this document is to provide guidelines on implementing Avaya’s SES Network Duplication from a best practices data network view. External posting: www.avaya.com. Application Note June 2008 COMPAS ID 136114 All information in this document is subject to change without notice. Although the information is believed to be accurate, it is provided without guarantee of complete accuracy and without warranty of any kind. It is the user’s responsibility to verify and test all information in this document. Avaya shall not be liable for any adverse outcomes resulting from the application of this document; the user accepts full responsibility. © 2008 Avaya Inc. All Rights Reserved. Avaya and the Avaya Logo are trademarks of Avaya Inc. or Avaya ECS Ltd., a wholly owned subsidiary of Avaya Inc. and may be registered in the US and other jurisdictions. All trademarks identified by ® and ™ are registered trademarks or trademarks, respectively, of Avaya Inc. All other registered trademarks or trademarks are property of their respective owners. Table of Contents 1) Introduction-------------------------------------------------------------------------------------------------------------------------------3 -
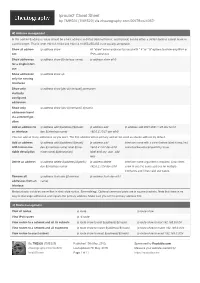
Iproute2 Cheat Sheet by TME520 (TME520) Via Cheatography.Com/20978/Cs/4067
iproute2 Cheat Sheet by TME520 (TME520) via cheatography.com/20978/cs/4067/ Address management In this section ${address} value should be a host address in dotted decimal format, and ${mask} can be either a dotted decimal subnet mask or a prefix length. That is, both 192.0.2.10/24 and 192.0.2.10 /25 5.25 5.255.0 are equally accepta ble. Show all addres‐ ip address show All "s how " commands can be used with "- 4" or "- 6" options to show only IPv4 or ses IPv6 addresses. Show addresses ip address show ${inter face name} ip address show eth0 for a single interf‐ ace Show addresses ip address show up only for running interfa ces Show only ip address show [dev ${inter face}] permanent statically configured address es Show only ip address show [dev ${inter face}] dynamic addresses learnt via autocon fig ur‐ ation Add an address to ip address add ${addre ss} /${ mask} ip address add ip address add 2001:db 8:1 ::/48 dev tun10 an interfa ce dev ${inter face name} 192.0.2.10/27 dev eth0 You can add as many addresses as you want. The first address will be primary and will be used as source address by default. Add an address ip address add ${addre ss} /${ mask} ip address add Interface name with a colon before label is required, with human-r ea‐ dev ${inter face name} label ${inte‐ 192.0.2.1/24 dev eth0 some backwards compati bility issue. dable descrip tion rface name}:$ {de scr ipt ion} label eth0:my _wa n_a dd‐ ress Delete an address ip address delete ${addre ss} /${ pre fix} ip address delete Interface name argument is required. -

C1921-3G-V-SEC/K9 Datasheet
C1921-3G-V-SEC/K9 Datasheet Get a Quote Overview The Cisco 1921 builds on the best-in-class. All Cisco 1900 Series Integrated Services Routers offer embedded hardware encryption acceleration, and advanced security services. In addition, the platforms support the industry's widest range of wired and wireless connectivity options such as Serial, T1/E1, xDSL, Gigabit Ethernet, and third-generation (3G) wireless. The Cisco 1921 is architected to meet the application demands of today's branch offices with design flexibility for future applications. PRODUCT DETAILS Device Type Router Enclosure Type Desktop, rack-mountable - modular - 1U Data Link Protocol Ethernet, Fast Ethernet, Gigabit Ethernet Network / Transport IPSec, L2TPv3 Protocol OSPF, IS-IS, BGP, EIGRP, DVMRP, PIM-SM, static IP routing, IGMPv3, GRE, PIM-SSM, static IPv4 routing, static IPv6 Routing Protocol routing, policy-based routing (PBR), MPLS Remote Management SNMP, RMON Protocol Compliant Standards IEEE 802.1Q, IEEE 802.3ah, IEEE 802.1ah, IEEE 802.1ag Power AC 120/230 V ( 50/60 Hz ) Dimensions (WxDxH) 34.3 cm x 29.2 cm x 4.4 cm Weight 5.4 kg Manufacturer 1 year warranty Warranty Get more information Do you have any question about the C1921-3G-V-SEC-K9? Contact us now via Live Chat or [email protected]. Specification General Device Type: Router Service Provider: Verizon Wireless Enclosure Type: Desktop, rack-mountable, modular, 1U Connectivity Wired Technology: Data Link Ethernet, Fast Ethernet, Gigabit Ethernet Protocol: Network / Transport IPSec, L2TPv3 Protocol: OSPF, -

Packetix VPN ?????
??????? ?? Web ????? PacketiX VPN 4.0 ????????????????????? PacketiX VPN ????? ?????????? VPN ?????? • 4,096 ????? ?????????? HUB ? • 4,096 ? ????????????? VPN • ??? 2 (Ethernet ????) • ??? 3 (IP ??????) ?????????? VPN • ??? 2 (Ethernet ????) • ??? 3 (IP ??????) ???????? • VoIP / QoS ???? • ?????????????????? ?? HUB ????????????????? • ????: 10,000 • ????: 10,000 • ??????????: 32,768 • MAC ???????????: 65,536 • IP ???????????: 65,536 • ???????: 128 SecureNAT ?? • ?? NAT ??: ?? HUB ????? 4,096 NAT ???? • ??????? NAT • ??????? NAT • ?? DHCP ?????? ????(HA)???????? • ???????????: 64 • ????????? • ?????????????????????????? • ??????????????????????????????? HUB ????? • ???????????????????? ???????? • ????????: RADIUS ?? / NT ???? ?? / Active Directory • ????????????????????????????? • ?? HUB ??????????? • ?????????????????????? • ????????????????????????????????? • DoS ??(SYN Flood ??)????????? ???? • Windows ? GUI ?? VPN ??????????? • CUI ??????????????????(vpncmd) • syslog ????????? • VPN ??????????????? PacketiX VPN Server????????VPN?????? • SoftEther VPN ????? (Ethernet over HTTPS) • OpenVPN (L3 ???? L2 ???) • L2TP/IPsec • MS-SSTP (Microsoft Secure Socket Tunneling Protocol) • L2TPv3/IPsec • EtherIP/IPsec PacketiX VPN ???????? • ???????????: ?????? • VPN ??????????(??): SSL (Secure Socket Layer) 3.0 / TLS (Transport Layer Security) 1.0 • VPN ??????????(??): TCP/IP ? UDP/IP ??? (IPv4 ??? IPv6 ?) • ????: RC4-MD5, RC4-SHA, AES128-SHA, AES256-SHA, DES-CBC-SHA and DES- CBC3-SHA • ?????: zlib • ??????: 128bit • ??????: ?????HTTP over SSL Protocol -

Advanced Networking Laboratory
Advanced Networking Laboratory Virtual Private Networking: Enhancing Security for E-Business TR-ANL-2002-04-01 Jingdi Zeng and Nirwan Ansari April 2002 Electrical and Computer Engineering New Jersey Institute of Technology University Heights Newark, NJ 07029 U.S.A 1 Virtual Private Networking: Enhancing Security for E-business1 Abstract With the Internet penetrating every corner of the world, e-business has found an excellent carrier which is able to fulfill the information transfer among diverse areas. Virtual private networking, a booming value-added service over the Internet, offers a low-cost, high-security, and easy-to- manage solution for e-business applications and services. The article introduces the implementation of Virtual Private Networks (VPNs), by portraying a generic deployment process following with certain details. The comparison and discussion in the article shall benefit service providers seeking for new avenues, and enterprises longing for supreme e-business services as well. Key words: E-business, virtual private networks, deployment framework, implementation, security. Authors: Jingdi Zeng [email protected] Prof. Nirwan Ansari ECE department New Jersey Institute of Technology 323 M. L. K. Blvd. University Height Newark, New Jersey 07102 USA (Tel) 973-596-3670 [email protected] 1 This work is resulted from the effort on incorporating IP VPN services into a 10G Ethernet product for OpenCon Communication Systems. 2 1. INTRODUCTION With the Internet reaching more and more homes and offices, the electronic commerce has been spreading out to every corner of the world. On one hand, e-business providers desire diverse technologies, from database management to Intranet security, to support everyday activities.