Interposition Agents: Transparently Interposing User Code at the System Interface
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

DLCC Software Catalog
Daniel's Legacy Computer Collections Software Catalog Category Platform Software Category Title Author Year Media Commercial Apple II Integrated Suite Claris AppleWorks 2.0 Claris Corporation and Apple Computer, Inc. 1987 800K Commercial Apple II Operating System Apple IIGS System 1.0.2 --> 1.1.1 Update Apple Computer, Inc. 1984 400K Commercial Apple II Operating System Apple IIGS System 1.1 Apple Computer, Inc. 1986 800K Commercial Apple II Operating System Apple IIGS System 2.0 Apple Computer, Inc. 1987 800K Commercial Apple II Operating System Apple IIGS System 3.1 Apple Computer, Inc. 1987 800K Commercial Apple II Operating System Apple IIGS System 3.2 Apple Computer, Inc. 1988 800K Commercial Apple II Operating System Apple IIGS System 4.0 Apple Computer, Inc. 1988 800K Commercial Apple II Operating System Apple IIGS System 5.0 Apple Computer, Inc. 1989 800K Commercial Apple II Operating System Apple IIGS System 5.0.2 Apple Computer, Inc. 1989 800K Commercial Apple II Reference: Programming ProDOS Basic Programming Examples Apple Computer, Inc. 1983 800K Commercial Apple II Utility: Printer ImageWriter Toolkit 1.5 Apple Computer, Inc. 1984 400K Commercial Apple II Utility: User ProDOS User's Disk Apple Computer, Inc. 1983 800K Total Apple II Titles: 12 Commercial Apple Lisa Emulator MacWorks 1.00 Apple Computer, Inc. 1984 400K Commercial Apple Lisa Office Suite Lisa 7/7 3.0 Apple Computer, Inc. 1984 400K Total Apple Lisa Titles: 2 Commercial Apple Mac OS 0-9 Audio Audioshop 1.03 Opcode Systems, Inc. 1992 800K Commercial Apple Mac OS 0-9 Audio Audioshop 2.0 Opcode Systems, Inc. -

Full Journal, PDF, 19.8 Megabytes
$2.95 • was The Journal of W ashington Apple Pi, Ltd. Volume 14, Number 11 November 1992 Apple Expo East '---------- -------' 21 ~-A_r_tis_t_s_o_n_E_x_h _ib_it_ __.l 22 Looking Good in "9 ._____P_r_in_t_R_e_v_i_e_w___ ___. L .____M_a_c_E_K_G_ R_e_vi_e_w_ ____, 32 PowerBundle: A 34 ~-G_o_o_d_Va_l_u_e_? __~ A~ple II Screen 52 ~_S_o_ts_:_B_e_l _ie_v_e_lt_! _ __. Washington Apple Pi General Meeting 4th Saturday • 9:00 a.m. • Community & Cultural Center Northern VA Community College • 8333 Little River Turnpike Annadale, Virginia Oct. 24 Mac: Major presentation Nov. 21 by Claris on FileMaker Mac: Major presentation December 12 Pro, MacWrite Pro, etc. by Hewlett-Packard Apple II: GEnie & (and maybe a surprise). telecommunications. Apple II: wonders of Plus the usual gossip System 6. and enthusiastic Plus the usual gossip Q & A sessions. and enthusiastic Q & A sessions. location to be announced. From the Belf\vay (1 -495) rake Exit 6 west on VA 236 approx. 1 mile. Turn left into the camp us of Northern Virginia Comm. College. DC Loop around ro rhe rear ..A.. parking lots, and \Valk to lliJl the Community & Culrural Cenrer Building. Northern Virginia Community College There is abundant free parking adjacent to the Community & Cultural Center. Give your Chooser better choices HP LaserJet PostScript® printers for the Macin tosh® combine superior print qualtiy with ''plug and-play" simplicity. Now there is a family of reliable HP LaserJet PostScript printers offering the choices that will help you make a better impres sion at the office. With five models available, you can choose from simple affordability, personal or workgroup, duplexing or sheer speed All have true Adobe®PostScript with 35 typefaces. -

Newsletter 11 *»
May, 1993 a£ l i t • / / Vol. 16 No. 5 Newsletterapples 11 *» the Minnesota Apple Computer Users' Group, Inc. Inside: May Events Compression Wars Hard Drive Answers Sun Mon Tue Wed Thr Fri Sat The Complete History of the Apple II (part 1) And... 7:00 1:00 10 11 Y2 13 14 15 10:00 ©700 <&oo Swap »meet 16 17 18 19 20 21 22 7:00 oo Hi] 7:00 7:00 b:00 23 24 25 26 27 28 29 m, 00 ]7:00 6 7:00 Board of Directors- Mini'app'les W^ HyperCard SIG - Scripting Q&A - E. Members Welcome - Lexington Lib., Lake Ub., 2727 East Lake St., Mpls - University & Lexington, St. Paul - Peter Fleck, 370-0017 David Laden, 488-6774 c UJ Apple II Novice SIG - Open Forum - Programmer's Workshop - Think-C Murray Jr. High, 2200 Buford, St. Paul Program Coding - Brookdale-Henn Lib., TomGates, 789-1713 6125 Shingle Creek Pkwy, Brooklyn Center - Keven Kasulker, 535-2968 a FileMaker Pro SIG - Open Discussion - Highland Park Ub., 1974 Ford Pkwy., & Apple ll/GS Main - Data Recovery - St. Paul - Steve Wilmes, 458-1513 Murray Jr. High, 2200 Buford, St.Paul - Tom Ostertag, 488-9979 Macintosh DTP SIG - St. Anthony Ub., d3 2245 Como Ave., St. Paul - Bob Grant, Something New Macintosh Main - Marty Probst of Pro 827-6294 Active Marketing - Penn Lake Lib., 8800 to do After Dark Penn Ave. S., Bloomington - wMacintosh Novice SIG - Open Forum - Mike Carlson, 377-6553 Highland Park Ub., 1974 Ford Pkwy., St. Paul - Tom Lufkin, 698-6523 Swap Meet! - Apache Plaza, Mac Programmers SJG - Apple OCE - 3800 Silver Lake Rd., NE Mpls Murray Jr. -
Archive Utility Download Mac Free Best Zip Program for Mac: 4 Options to Know
archive utility download mac free Best Zip Program for Mac: 4 Options to Know. Files you may use on your computer will be of different formats and no matter which operating system your computer runs on, you would certainly have come across .zip files. Zipped files or compressed files, as they’re called, are used when you wish to save space on your computer and also when they need to be sent via the internet. Zip files have been in existence for many years now and is helpful when you have to deal with a large number of files that you may need to send to someone via email or reduce the actual size of the files when sharing. Like on Windows, you can also open .zip files on your Mac and create .zip files by compressing other files. In this post, we’ll list the programs you may use to open and compress .ZIP files on a Mac. Mac’s Archive Utility The Unarchiver RAR Extractor Keka. Mac’s Archive Utility. Mac offers a native compressing and decompressing solution in the form of the Archive Utility that’s built right into the macOS system. Not only can you summon the app from the Launchpad or through Spotlight, but the ability to compress a file into archive format is also built right into the Mac’s Finder app. This way, you are not required to open a separate app or preset values for compression. By default, the Archive Utility inside Finder compresses files in ZIP format and leaves the files and archive alone when decompressing or compressing. -

File Conversion L Technical Information
L Technical Information File Conversion PostScript™ imagesetting has long been dominated by Apple’s Macintosh® computers. But times are changing. The number of IBM and IBM compatible PC (personal computer) users using PostScript will continue to increase for a number of reasons: • The large installed base of PC users and the wide range of PostScript applications available to them. • The appealing price/performance aspect of the PC platform. • The introduction of Windows™ versions of many Macintosh software applications including Adobe Photoshop™ and QuarkXPress®. The result is that an increasing number of PostScript files will be exchanged between Macintoshes and PCs. DOS PC-DOS™ (Personal Computer - Disk Operating System) and MS-DOS® (Microsoft - Disk Operating System) are operating systems which control the functioning of a computer. PC-DOS and MS-DOS are used extensively in the PC world. In DOS, commands are entered on a keyboard. Graphical User Interfaces (GUIs) operate through DOS and give users a way of expressing commands via a mouse or similar tool. Many people prefer this type of 1 interface since they don’t have to memorize commands and since it tends to Macintoshes have had a built-in 1 GUI since their introduction. be more intuitive. In the DOS environment, both Windows and GEM™ (Graphics Environment Manager) provide GUIs. OS/2® (an IBM-developed operating system) also provides a GUI called Presentation Manager®. File transfer and conversion There are two primary issues in moving a PC file to a Macintosh (or a Macintosh file to a PC), file transfer (getting the file to where you can work with it) and file conversion2 (getting it into a form you can use): File transfer – Unless you are receiving a file via a network, modem or directly via a cable, your first concern is being able to read the diskette at all. -

6 X 16 = 32-Bi Multiply
SILICON COMPOSERS INC FAST Forth Native-Language Embedded Computers DUP >R R> Harris RTX 2000tml&bit Forth Chip SC32tm32-bit Forth Microprocessor -8 or 10 MHz operation and 15 MIPS speed. *8 or 10 MHz operation and 15 MIPS speed. 1-cycle 16 x 16 = 32-bi multiply. 1-clock cycle instruction execution. 1-cycle 1Cprioritiied interrupts. *Contiguous 16 GB data and 2 GB code space. *two 2Sword stack memories. *Stack depths limited only by available memory. *&channel I/O bus 81 3 timer/counters. -Bus request/bus grant lines with on-chip tristate. SC/FOX PCS (Parallel Coprocessor System) SC/FOX SBC32 (Single Board Computer32) *RTX 2000 industrial PGA CPU; 8 & 10 MHz. -32-biSC32 industrial grade Forth PGA CPU. -System speed options: 8 or 10 MHz. *System speed options: 8 or 10 MHz. 032 KB to 1 MB 0-wait-state static RAM. -32 KB to 512 KB 0-wait-state static RAM. Full-length PC/XT/AT plug-in (6-layer) board. elOOmm x 160mm Eurocard size (4-layer) board. SC/FOX VME SBC (Single Board Computer) SC/FOX PCS32 (Parallel Coprocessor Sys) *RTX 2000 industrial PGA CPU; 8, 10, 12 MHz. 032-bi SC32 industrial grade Forth PGA CPU. *Bus Master, System Controller, or Bus Slave. *System speed options: 8 or 10 MHz. -Up to 640 KB 0-wait-state static RAM. 064 KB to 1 MB @wait-state static RAM. *233mm x 160mm 6U size (Slayer) board. *FulClength PC/XT/AT plug-in (Slayer) board. SC/FOX CUB (Single Board Computer) SC/FOX SBC (Single Board Computer) RTX 2000 PLCC or 2001A PLCC chip. -

Creator Codes
APPLICATION NAME CREATOR 1st Aid HFS 1AID 3rd Dimension TESC 4-Matter 4-Ma 4D Client 4D+1 4D Runtime 4D05 4th Dimension 4D03 Acrobat Distiller DSTL Adobe/Acrobat Reader CARO ACT! ACT! Acta ACTA Address Book AdBk Address Book Plus puAB Adobe After Effects FXTC Adobe Dimensions AD3D Adobe Photoshop 8BIM Adobe Premiere PrMr Adobe Separator ASEP Aldus Fetch FtCH Aldus Persuasion PLP3 Alias Director pLaL All Midi 2Mid Alpha ALFA AMAPI AMAP America Online AOqc Analog MAG^ Anarchie Arch AOL Web Browser TCPa Apple Backup OBBa Apple DocViewer HLX2 Apple File Exchange PSPT Apple HD SC Setup scsi Apple IR File Exchange beam Apple Media Conference mtsm Apple Media Tool K__A Apple Phone tele Apple Photo CD kpcd Apple Printer Utility apu Apple Remote Access lx Apple System Profiler prfc Apple Video Player mtv2 AppleCD Audio Player aucd AppleLink GEOL AppleMail lap2 AppleScript compiled applet aplt AppleScript compiled droplet dplt AppleSearch Client MRLW AppleShare File Server hgfd AppleVision Setup smav AppleWorks or ClarisWorks BOBO Archie CjM@ ArcMac arc* Ares FontChameleon aArC Arnold's Midi Player MIDp Attributes jAt® Audiodeck Audk Audiophile SDSP Audioshop AUDI Auspice AUS* Authorware APM3 Auto UnStuffIt AUSt AVI to QT Utility AVIC Avid Cinema Mndy BalloonWriter bubl Band-In-A-Box BB40 Battery Recondition recn BatteryAmnesia JBKd BBEdit R*ch Binary Pump BINP BinHex 4.0 BNHQ BinHex 5.0 BnHq BitMapsToEPS RMF? BrushStrokes HUPA Bryce2 Bry2 Burn-It MwBu CADintosh FCAD CalConvert h«»d Calculator CALC Calculator II calc Calibrator Agcb CanOpener eIC7 -

Apple Collection.Pdf
0 archive of apple ad’s & commercials movies of apple II, IIgs, macs, neXt, newton, tours, software 0 archive of apple ad’s & commercials apple service case with tools & software to check apple computers 0 archive of apple & mac systems & software dos-prodos-sos-lisa os-newton -macos 0>X & software II, III ... 0 archive of computers & hardware info of each item i own, manuals, tutorials, guides, pictures 0 archive of other apple & macintosh items info other apple & mac, introduction apple & mac ... 0 original apple Historical DVD set volume 1 DVD 0 original apple Historical DVD set volume 2 DVD 0 original apple Historical DVD set volume 3 DVD 0 original apple Historical DVD set volume 4 DVD 0 original apple Historical DVD set volume 5 DVD 0 original apple Historical DVD set volume 6 DVD 0 original apple Historical DVD set volume 7 DVD 0 original apple Historical DVD set volume 8 DVD 0 original apple II Balloon software apple IIgs 0 original apple II Easy Writer software Apple II Easy Writer - mailer - complete 0 original apple II manual red book apple II manual “the must have” 1978 0 original apple II manuals apple II IIe IIgs ..... 0 original apple II shrinkit II works with osX classic to (de)compress apple II shrinkIt archives 0 original apple II’s Flight Simulator II original packed flight simulator II for apple II 0 original apple II’s & III apple II III IIe IIc IIgs ..... 0 original apple III access software 0 original apple III basic vol1 & 2 software 0 original apple III DVD set 2 DVD’s The Apple /// In Ten EZ Lessons 0 original apple III E-Z pieces software Database - word processing - spreadsheet 0 original apple III script software 0 original apple III Visicalc software original packed Visicalc for apple III 0 original apple III Visicalc software advanced original packed Visicalc for apple III advanced version 0 original apple service guides service source CD’s service guide books mactest diskettes 0 original CD set techservice manuals (3CD) 1200 manuals 0 original macintosh bag 128k 3 the computer which came out of that bag was a.. -
Filename Extensions
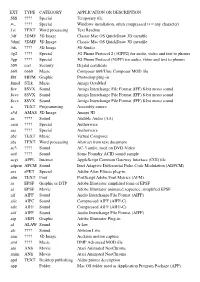
EXT TYPE CATEGORY APPLICATION OR DESCRIPTION .$$$ ???? Special Temporary file .••_ ???? Special Windows installation, often compressed (• = any character) .1st TEXT Word processing Text Readme .3df 3DMF 3D Image Classic Mac OS QuickDraw 3D metafile .3dmf 3DMF 3D Image Classic Mac OS QuickDraw 3D metafile .3ds ???? 3D Image 3D Studio .3g2 ???? Special 3G Phone Protocol 2 (3GPP2) for audio, video and text to phones .3gp ???? Special 3G Phone Protocol (3GPP) for audio, video and text to phones .509 cert Security Digital certificate .669 6669 Music Composer 669/Unis Composer MOD file .8bf 8BFM Graphic Photoshop plug-in .8med STrk Music Amiga OctaMed .8sv 8SVX Sound Amiga Interchange File Format (IFF) 8-bit mono sound .8svc 8SVX Sound Amiga Interchange File Format (IFF) 8-bit mono sound .8svx 8SVX Sound Amiga Interchange File Format (IFF) 8-bit mono sound .a TEXT Programming Assembly source .a3d AMAS 3D Image Amapi 3D .aa ???? Sound Audible Audio (AA) .aam ???? Special Authorware .aas ???? Special Authorware .abc TEXT Music Virtual Composer .abs TEXT Word processing Abstract from text document .ac3 ???? Sound AC-3 audio, used on DVD-Video .acd ???? Sound Sonic Foundry ACID sound sample .acgi APPL Internet AppleScript Common Gateway Interface (CGI) file .adpcm APCM Sound Intel Adaptive Differential Pulse Code Modulation (ADPCM) .aex eFKT Special Adobe After Effects plug-in .afm TEXT Font PostScript Adobe Font Metrics (AFM) .ai EPSF Graphic or DTP Adobe Illustrator simplified form of EPSF .ai EPSF Movie Adobe Illustrator animated sequence, simplified -

Appendix E Software Compatibility
Appendix E Software Compatibility Note that in addition to IBM-compatible and Macintosh computers the WHPO also has a MicroVAX 3800 with VMS operating system and a Sun Sparc10 with a Unix operating system. The Sun has limited software at present but can handle most standard network functions for Unix. We continue to add software and hardware capabilities in an attempt to keep up with the changing technology and the WOCE community, so if your software package does not appear on this list please contact us as it may have been acquired, or a translation program added, since this list was compiled. TABLE E.1: List of IBM PC (DOS and Windows) and Macintosh software and graphics that can be read by the WHPO. Software Name IBM PC Macintosh Comments Ami Professional 1.2, 2.0, 3.0 Yes Yes Appleworks 3.0 No Yes Appleworks GS No Yes CGM Yes No ClarisWorks No Yes DBASE III, III+, IV, 1.0 Yes No DCA/RFT Yes Yes DCA/RFT with Display Write 5 Yes No DIB Yes No Display Write 2, 3, 4, 5 Yes No DXF Yes No Excel 2.1, 2.2 Yes Yes Excel 3.0 Yes Yes Framemaker 2, 3, 4 Yes Yes HPGL Yes No IGES Yes No IslandWrite No No a L T EX Yes Yes Legacy Yes No Note that we can read either IBM PC or Macintosh 3.5 or 5.25 double sided high density (HD) or double density (DD) floppies. Also, Sun 3.5 high density floppies can be read. -

Catalog 05/07.Indd
Software Library Listing July 2005 1 INTRODUCTION This is a catalog of all of the files maintained in the Keystone MacCentral Software Library. The Library can be obtained on CD by request. The library requires two CDs. Normally we will provide one full CD with the latest files. These will be programs that require OS X or in some cases Classic. Please specify if you require the complete library. DOMs Disks Of the Month are arbitrary collections of files. They have been downloaded from the Net. The web sites are included in the documentation so that you may download directly from the source. ROMs In September of 1998, we featured MacMAME as our Disk Of the Month (DOM 98/09.) In a nutshell, MacMAME attempts to emulate as closely as possible the original hardware of the early eighties arcade games. It does this by fooling the original program code, contained in ROM chips, into thinking they are running inside the real machine when in reality they are running on your Mac. MAME, which stands for Multi-Arcade Machine Emulator, is the product of a group of people who have teamed up to emulate as many of these games as possible. This is a list of the games that we have in our library in the DOM 98/09 folder. SOUND BYTES This portion of our catalog lists the names of the various sound bytes, that we have in our library. The five folders are arranged by type of sound. About .seas and .sits Many of the files are .sea files.