Security and Privacy of QR Code Applications: a Comprehensive Study, General Guidelines and Solutions
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Readerware Cuecat Manual
Readerware CueCat Manual This manual will help you install your CueCat(R) barcode reader and get you started scanning your books, music and videos. Important: If you purchased your CueCat from another source, you may have received software with it, do not install this software. You do not need any additional software when using your CueCat with Readerware, and following the demise of Digital Convergence, the CueCat software will no longer work. Table of Contents Installing a PS/2 CueCat on a desktop machine (Windows and Linux)..............................2 Installing a PS/2 CueCat on a laptop (Windows and Linux)..............................................4 Installing a USB CueCat (Windows, Mac OS X and Linux)..............................................5 How to Swipe a Barcode..................................................................................................6 Troubleshooting................................................................................................................7 Readerware CueCat Manual v1.04 Page: 1 Installing a PS/2 CueCat on a desktop machine (Windows and Linux) Note: Before you begin, shut down all programs and turn off your computer. If you are installing the CueCat reader on a laptop computer, proceed to the next section. Disconnect the keyboard cable from your computer. The CueCat reader operates through the keyboard port. Make sure you do not use the mouse port. If the keyboard port on your computer doesn©t match the male connector on the CueCat reader, you can get adapters at any computer store or Radio Shack. Readerware CueCat Manual v1.04 Page: 2 Connect the male connector on the CueCat reader into the computer©s keyboard port. Match up the "notch key" for easy insertion. (Note: the male connector is the one with the protruding pins.) Connect the keyboard cable to the female connector on the CueCat reader. -
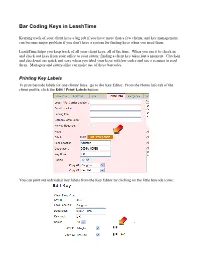
Bar Coding Keys in Leashtime
Bar Coding Keys in LeashTime Keeping track of your client keys a big job if you have more than a few clients, and key management can become major problem if you don't have a system for finding keys when you need them. LeashTime helps you keep track of all your client keys, all of the time. When you use it to check in and check out keys from your office to your sitters, finding a client key takes just a moment. Check-in and check-out are quick and easy when you label your keys with bar codes and use a scanner to read them. Managers and sitters alike can make use of these barcodes. Printing Key Labels To print barcode labels for one clients' keys, go to the Key Editor. From the Home Info tab of the client profile, click the Edit / Print Labels button: You can print out individual key labels from the Key Editor by clicking on the little barcode icons: You can save paper and time by printing out lots of key labels at once from the Key Location Report (KEYS > Key Location Report). Key Tags If you're going to print key labels, you will need key tags to slip the labels into. Search eBay for “key label tags” and you will find plenty of them. A tag that encases the label or protects the label from the elements with a window of plastic is a good idea. The largest size label tag that LeashTime currently prints labels for is sold under the Clik-It brand. -

Kiosk Barcode Reader
KBR2D Kiosk Barcode Reader KBR2D is the family of barcode scanners designed for self-service kiosks, ATMs, price checkers, healthcare and for any OEM application, also available in a plastic case version (KBR2D-C). KBR2D is a high-performance, high-volume omnidirectional scanner, capable of quickly and accurately reading any 1D and 2D barcodes, whether printed on paper (badges, receipts, health bracelets) or displayed on the screen of a smartphone or of a tablet. KBR2D scanners are based on CMOS technology for optimal image sensitivity and dynamic range. KBR2D integration is quick and easy thanks to several mounting options. www.custom.biz - [email protected] Follow us CHARACTERISTICS Easily integrated with various OEM applications 1D and 2D barcode scanning Omnidirectional scanning: no need to align barcode and scanner, ensuring user comfort and protecting productivity Long distance reading from 3 to 28 cm without problems even in direct sunlight (100,000 lux) Reading barcodes on screens of smartphones or tablets even with brightness reduced to 25/30% Red colored pointer for precise aiming and optimal barcode acquisition Flexibility: various external mounting options or internal screw holes Integrated decoder Custom ScannerSet configuration software DIMENSION: www.custom.biz - [email protected] Follow us www.custom.biz - [email protected] Follow us TECHNICAL SHEET KBR2D-C KBR2D GENERAL Interface USB-HID(or Virtual COM port) RS232/USB-HID(or Virtual COM port) UPC-A, UPC-E, EAN-8/JAN-8, EAN-13/JAN-13, Code 39, Code 128, Interleaved 25, Industrial -
Barcode Reader
BARCODE READER USER MANUAL V 2.1 EN INSTALLATION OF YOUR DEVICE PS-2 Connection RS-232 Connection (need 5Volts power supply) 1 INSTALLATION OF YOUR DEVICE USB Connection 2 USING THIS MANUAL TO SETUP YOUR DEVICE To set up all the necessary functions you can use the following barcode menus. Using these barcodes, you should enter in program mode, scan the required command symbol then exit from program mode. The general procedure is the following: -1) Scan the command symbol “PROGRAM” -2) Scan one or more parameters -3) Scan the command symbol “END” (note) Code 2/5 symbologies have an unchecked reading mode, so that, you could set a fixed code length to avoid any reading errors. Following is the correct procedure: -1) Scan the command symbol “PROGRAM” -2) Scan the command symbol “FIXED LENGTH” -3) Scan the command symbol “END” The first two scanned barcodes 2/5 will be stored as fixed length values. The following procedure will reset the above selection: -1) Scan the command symbol “PROGRAM” -2) Scan the command symbol “FIXED LENGTH OFF” -3) Scan the command symbol “END” 3 COMPLEX DEVICE SETTINGS Set MIN/MAX barcode lengt: -1) Scan the command symbol “PROGRAM” -2) Scan the symbol “SET MAX&MIN” -3) Scan barcode symbology (i2/5, 39,… etc…) -4) Scan the symbol “MM” or “NN” (max or min) -5) Scan 2 digits from the ASCII table -6) Scan the symbol “SET MAX&MIN” -7) Scan the command symbol “END” Set PREAMBLE/POSTAMBLE -1) Scan the command symbol “PROGRAM” -2) Scan the symbol “PREAMBLE/POSTAMBLE” -3) Scan up to 16 characters from the ASCII table -4) -

Harrison 2011
FloorPlay: Design and evaluation of a system to motivate physical activity in office workers Daniel Bryan Peter Harrison "Project report submitted in part fulfilment of the requirements for the degree of Master of Science (Human-Computer Interaction with Ergonomics) in the Faculty of Brain Sciences, University College London, 2012." NOTE BY THE UNIVERSITY This project report is submitted as an examination paper. No responsibility can be held by London University for the accuracy or completeness of the material therein. Acknowledgements This was a very ambitious MSc project, and as such there are a lot of people I’d like to thank. I’d first like to thank Jon Bird and Paul Marshall, for all of their support and assistance in producing and installing the system, and ultimately getting this report written. They offered great help throughout the project; the project wouldn’t have came together without them. I’d also like to thank all of the other academic and support staff that have taught and helped me over the past twelve months on the Masters’ degree. The Technical Support Group staff, especially Dave Twinsleton, were also a great help with installing various parts of the system, including the wiring for the interactive surface and the wireless network in the stairwell. My friend, Greg Booth, also very kindly took a long day away from home to come to UCL and help me install parts of the system. Fran Allfrey and James Owers kindly allowed me to stay at their home when it was either too late or when I was too exhausted to take the train home. -

User Manual North America: English
USER MANUAL NORTH AMERICA: ENGLISH CR6000 MANUAL VERSION 02 RELEASE DATE: JUNE 2014 www.codecorp.com Configuration Guide YouTube.com/codecorporation Statement of Agency Compliance The Code Reader™ 6000 (Model #: CR6022_01) has been tested for compliance with FCC regulations and was found to be compliant with all applicable FCC Rules and Regulations. IMPORTANT NOTE: To comply with FCC RF exposure compliance requirements, this device must not be co-located or operate in conjunction with any other antenna or transmitter CAUTION: Changes or modifications not expressly approved by the party responsible for compliance could void the user’s authority to operate the CR6022_01 equipment. The Code Reader 6000 has been tested for compliance to CE standards and guidelines and was found to conform to applicable CE standards, specifically the EMC requirements EN 55024, ESD EN 61000-4-2, Radiated RF Immunity EN 61000-4-3, PFMF EN 6100-4-8, EFT EN 61000-4-4, Conducted RF Immunity EN 61000-4-6, and EN 55022 Class B Radiated Emissions and Class B Conducted Emissions. Code voids product warranty if the hard case has been opened or tampered with in any way. External Power Supply: MFG: Group West. Model: 6UA-05-1200. Rating: 5VDC, 1.2A. Code Reader™ 6000 User Manual Copyright © 2014 Code Corporation. All Rights Reserved. The software described in this manual may only be used in accordance with the terms of its license agreement. No part of this publication may be reproduced in any form or by any means without written permission from Code Corporation. This includes electronic or mechanical means such as photocopying or recording in information storage and retrieval systems. -

Tech Tip of the Week QR Codes
Tech Tip of the Week QR Codes The above QR Code is a URL Link to www.theholler.org Overview: Have you noticed the above types of codes appearing every type of item from the supermarket to the newspapers. QR Codes are becoming tools that are being used throughout our nation to help provide quick links to information in a modern way, through the use of handheld technology. This technology has already been making its way into the classrooms and many teachers are starting to use it to engage their students in new ways. In this technology tip, I will try to provide you with some basics of what a QR Code is, some history, how to create QR codes, where to find QR code readers and creators, some classroom uses, and links to help you with your implementation of the technology into your class, Basics: A QR (Quick Response) code is a 2D barcode that is on steroids that can store more information using tiny squares. Barcodes have been used for a long time to store information on a horizontal line using vertical line segments to represent information and are scanned horizontally to obtain the information. With the QR codes information can be scanned in both directions and you don’t need a special tool to read them. All you need is a QR Code Reader, which you can download from any APP store and most are free. Historical Note: Denso-Wave is credited for the creation of the QR Code. To learn more about it Scan the below QR Code: How to Create a QR Code: 1. -

Wasp WWS650 2D Handheld Wireless Barcode Reader
Wasp WWS650 2D Handheld Wireless Barcode Reader Product Reference Guide Wasp Barcode Technologies 1400 10th Street Plano, Texas USA 75074 Telephone: (214) 547-4100 ©2013-2018 Wasp Barcode Technologies An Unpublished Work - All rights reserved. No part of the contents of this documentation or the procedures described therein may be reproduced or transmitted in any form or by any means without prior written permission of Wasp Barcode Technologies or its subsidiaries or affiliates ("Wasp Technologies" Technologies Wasp Technologies). Owners of WaspTechnol- ogies products are hereby granted a non-exclusive, revocable license to reproduce and transmit this documentation for the purchaser's own internal business purposes. Pur- chaser shall not remove or alter any proprietary notices, including copyright notices, con- tained in this documentation and shall ensure that all notices appear on any reproductions of the documentation. Should future revisions of this manual be published, you can acquire printed versions by contacting your Wasp Technologies representative. Electronic versions may either be downloadable from the Wasp Technologies website (www.waspbarcode.com) or provided on appropriate media. If you visit our website and would like to make comments or sugges- tions about this or other Wasp Technologies publications, please let us know via the "Con- tact WaspTechnologies" page. Disclaimer Wasp Technologies has taken reasonable measures to provide informantion in this manual that is complete and accurate, however, Wasp Technologies reserves the right to change any specification at any time without prior notice. Wasp Technologies and the Wasp Tech- nologies logo are registered trademarks of Wasp Technologies Barcode Technologies in many countries, including the U.S.A. -

Breaking Down the Barcode Amanda Nelson, Product Manager – Barcode Readers January 2021
Breaking Down the Barcode Amanda Nelson, Product Manager – Barcode Readers January 2021 Breaking Down the Barcode Barcode Reading Basics and How to Choose the Right Barcode Reader A barcode is a visual expression of data designed specifically to be read by machines. They store information such as model number, serial number, or product history. The first barcodes expressed this data in the width and spacing of parallel black bars and white spaces. These are called 1D (one-dimensional) barcodes and are still incredibly ubiquitous today. However, more recently, barcodes that are composed of boxes, or cells, were created in order to store vast quantities of data. These barcodes, because they are rows and columns in a grid, are called 2D barcodes (although they are not comprised of bars, as such). From their humble beginning as an unloved patent back in 1952 to today, when virtually every industry uses barcoding, understanding barcodes, how they work, and how to best integrate them into your application is vital. 1D (Linear) Barcodes There are two main types of barcodes. The “traditional” barcode, 1D or linear, is made up of parallel black lines and white spaces of various widths. A barcode reader, scanner, or a computer calculates the width of the bars as well as the widths of the spaces between them to “read” the barcode. 1D barcodes are the most common type of barcode, used in industries spanning clothing retail to the United States Military. Within the category of 1D barcodes, there are many different kinds developed for various industries, with particular qualities that make them well-suited to the type and quantity of data needed. -

Cab Programming Manual
Product Marking 1 1 A+ series Mach 4 PX Print Module XD4 Programming Manual J-Script and abc for cab printers Edition 7.0 cab Produkttechnik GmbH & Co KG 1 2 2 JScript - the programming language for cab printers. The usage of all described functions in this manual requires firmware version 3.17 or higher. This is a generic manual which describes the commands for different printer models,which means that it may contain descriptions or explanations of features which are not available on every printer model. cab Produkttechnik GmbH & Co KG 2 3 3 cab Programming Manual valid for following printer types: A+ -Series TM XD4 -Series TM Mach 4 TM PX -Print Module TM and all printing systems based on the cab „X2“ board copyright © cab Produkttechnik GmbH & Co KG all rights reserved No parts of this manual may be copied, rewritten or used for anything else than for original cab printers. This interdicts the usage of the manual for OEM products unless you have a written permission. The cab printers command language is owned and copyrighted by cab Produkttechnik GmbH & Co KG cab Produkttechnik GmbH & Co KG Wilhelm Schickard Str. 14 76131 Karlsruhe / Germany Tel: +49 - 721-6626-0 Fax:+49 - 721-6626-239 Email: [email protected] http://www.cabgmbh.com All registered trademarks or product names are trademarks of their respectives companies SwissTM is registered Trademark of Bitstream Inc. cab Produkttechnik GmbH & Co KG 3 4 4 Table of contents copyright © cab Produkttechnik GmbH & Co KG.................................................................................. -

Barcode Reader System
Barcode Reader System The ability to read and decode barcodes is a key requirement for many tire test and measurement processes. Barcode readers and interpretation functions are available as an option for the Micro‐Poise ASTEC® PLUS tire uniformity and AkroDYNE® tire dynamic balancer machinery. The Barcode Reader System is designed to be used with the Tire Handler/Lube Station. When integrated with Micro‐Poise test and measurement systems, the Barcode Reader System reads the tires individual barcode as it is rotated for bead lube, prior to entering the test station. From the barcode number, testing parameters are determined such as tire characteristics enabling the machine to adjust for individual tire characteristics and test the tire to established standards. Key Functions: The barcode is scanned at tire handler & lube station. Tire type is associated with the barcode number through a customer managed database. The information is then sent to the tire testing system. Testing Machine automatically adjusts. The Micro‐Poise machine automatically performs its tests on the tire according to parameters established by tire type. Measurement results transmitted with barcode value in output string of data. Results can be written to an ODBC compliant database. Measurement results are aligned relative to barcode label. The label becomes a zero‐point reference angle on the tire allowing measurement to be related to Barcode Reader specific areas of tire construction. installed on a tire handler & lube station Micro‐Poise Measurement Systems, LLC For more than 90 years, Micro‐Poise has been supplying innovative solutions that put us on the leading edge of final finish tire testing technology. -

Let's Talk Symbology
Let’s talk symbology A guide to decoding barcodes Symbology in barcodes Barcode technologies provide fast reliable data collection to ensure part or product traceability, error-proof assembly processes, and enhance customer service. Barcodes are machine readable symbols that store identifying data about the part or product with which they are associated. These symbols, when read by a barcode scanner, are decoded, recorded, and processed to extract the data for a variety of uses (e.g., pricing, order fulfillment, traceability through production, sortation, shipping, etc.) Over the years, different forms of barcodes have been developed to help businesses around the world. These include: 1-D linear 2-D matrix barcodes codes A 1-D (one-dimensional) barcode is the typical style with In the 2-D (two-dimensional) matrix code type, the data is which we are most familiar. All the information in the code encoded as black and white ‘cells’ (small squares) is organized horizontally in bar and space widths and read arranged in either a square or rectangular pattern. As well left to right by a scanner. Several versions of 1-D codes store as being able to encode huge amounts of data, the matrix only numerical data while others can encode additional code improves readability and resistance to poor printing. characters. The height of the code varies based on the space They also include redundant data so even if one or more available on a product and the ability of a barcode reader to cells are damaged, the code is still readable. read a small or large sized barcode.