Antivirus Security: Naked During Updates
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
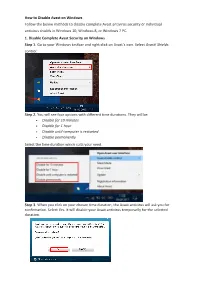
How to Disable to Antivirus
How to Disable Avast on Windows Follow the below methods to disable complete Avast antivirus security or individual antivirus shields in Windows 10, Windows 8, or Windows 7 PC. 1. Disable Complete Avast Security on Windows Step 1. Go to your Windows taskbar and right click on Avast’s icon. Select Avast! Shields control. Step 2. You will see four options with different time durations. They will be: • Disable for 10 minutes • Disable for 1 hour • Disable until computer is restarted • Disable permanently Select the time duration which suits your need. Step 3. When you click on your chosen time duration, the Avast antivirus will ask you for confirmation. Select Yes. It will disable your Avast antivirus temporarily for the selected duration. @CK How to disable or turn off AVG antivirus. 1. For AVG antivirus software: 1. Right-click the AVG icon in the system tray next to the clock. 2. Click "Temporarily disable AVG protection". 3. Choose how long you want the protection to be disabled and whether to disable the firewall as well, and then click "OK". 2. You can also disable AVG from the "Advanced settings": 1. Open the AVG Program. @CK 2. On the "Options" menu, click "Advanced settings". 3. Select "Temporarily disable AVG protection" in the menu on the left side. 4. Click the "Temporarily disable AVG protection" button. 5. Choose how long you want the protection to be disabled and whether to disable the Firewall as well, and then click "OK". @CK HOW TO DEACTIVATE / ACTIVATE AVIRA PROTECTION 1. Open the Avira Control Center 2. -

Hostscan 4.8.01064 Antimalware and Firewall Support Charts
HostScan 4.8.01064 Antimalware and Firewall Support Charts 10/1/19 © 2019 Cisco and/or its affiliates. All rights reserved. This document is Cisco public. Page 1 of 76 Contents HostScan Version 4.8.01064 Antimalware and Firewall Support Charts ............................................................................... 3 Antimalware and Firewall Attributes Supported by HostScan .................................................................................................. 3 OPSWAT Version Information ................................................................................................................................................. 5 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.890.0 for Windows .................................................. 5 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.890.0 for Windows ........................................................ 44 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.824.0 for macos .................................................... 65 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.824.0 for macOS ........................................................... 71 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.730.0 for Linux ...................................................... 73 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.730.0 for Linux .............................................................. 76 ©201 9 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. -

Malware List.Numbers
CLASS A - Tested once a month (and as significant updates and samples are available) (95% or higher detection rate) CLASS B - Tested every two months (and if many new samples or significant updates are available) (95 - 85% detection rate) CLASS C - Tested every three months (85-75% detection rate) CLASS D - Tested every six months (75% or lower detection rates) For Comparison, not an actual Antivirus CLASS F - Excluded from future testing (read notes) Notes, comments, remarks, FAQ and everything else. McAfee Endpoint Protection for Malware Family (by year) # Malware Sample Type MD5 Hash Avast 9.0 Intego VirusBarrier X8 10.8 Norman 3.0.7664 ESET 6.0 Sophos 9 F-Secure 1.0 Kaspersky Security 14 G Data AntiVirus for Mac Dr Web 9.0.0 Avira ClamXav 2.6.4 (web version) Norton 12.6 (26) Comodo Webroot 8 Thirtyseven4 Total Security eScan 5.5-7 iAntivirus 1.1.4 (282) ProtectMac 1.3.2 - 1.4 BitDefender 2.30 - 3.0.6681 McAfee Internet Security for Mac* AVG AntiVirus for Mac Dr Web Light 6.0.6 (201207050) Max Secure Antivirus MacBooster X-Protect Gatekeeper Intego VirusBarrier 2013 10.7 Intego VirusBarrier X6 VirusBarrier Express 1.1.6 (79) Panda Antivirus 1.6 Bitdefender (App Store) 2.21 MacKeeper 2.5.1 - 2.8 (476) Panda Antivirus 10.7.6 Trend Micro Titanium 3.0 McAfee Security 1.2.0 (1549) Norton 11.1.1 (2) Trend Micro Smart Sur. 1.6.1101 McAfee VirusScan for Mac 8.6.1 FortiClient 5.0.6.131 Quick Heal Total Sec 1.0 MacScan 2.9.4 McAfee Virex 7.7 (163) Magician 1.4.3 Vipre 1.0.51 Mac Malware Remover 1.1.6 MD5 Hash Mac 1 Price -> Free $39.99 (Internet -

Virusscan Enterprise 7.1.0 Installation Guide
Installation Guide Revision 1.0 VirusScan® Enterprise version 7.1.0 COPYRIGHT © 2003 Networks Associates Technology, Inc. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated into any language in any form or by any means without the written permission of Networks Associates Technology, Inc., or its suppliers or affiliate companies. To obtain this permission, write to the attention of the Network Associates legal department at: 5000 Headquarters Drive, Plano, Texas 75024, or call +1-972-963-8000. TRADEMARK ATTRIBUTIONS Active Firewall, Active Security, Active Security (in Katakana), ActiveHelp, ActiveShield, AntiVirus Anyware and design, Appera, AVERT, Bomb Shelter, Certified Network Expert, Clean-Up, CleanUp Wizard, ClickNet, CNX, CNX Certification Certified Network Expert and design, Covert, Design (stylized N), Disk Minder, Distributed Sniffer System, Distributed Sniffer System (in Katakana), Dr Solomon’s, Dr Solomon’s label, E and Design, Entercept, Enterprise SecureCast, Enterprise SecureCast (in Katakana), ePolicy Orchestrator, Event Orchestrator (in Katakana), EZ SetUp, First Aid, ForceField, GMT, GroupShield, GroupShield (in Katakana), Guard Dog, HelpDesk, HelpDesk IQ, HomeGuard, Hunter, Impermia, InfiniStream, Intrusion Prevention Through Innovation, IntruShield, IntruVert Networks, LANGuru, LANGuru (in Katakana), M and design, Magic Solutions, Magic Solutions (in Katakana), Magic University, MagicSpy, MagicTree, McAfee, McAfee (in Katakana), -

Q3 Consumer Endpoint Protection Jul-Sep 2020
HOME ANTI- MALWARE PROTECTION JUL - SEP 2020 selabs.uk [email protected] @SELabsUK www.facebook.com/selabsuk blog.selabs.uk SE Labs tested a variety of anti-malware (aka ‘anti-virus’; aka ‘endpoint security’) products from a range of well-known vendors in an effort to judge which were the most effective. Each product was exposed to the same threats, which were a mixture of targeted attacks using well-established techniques and public email and web-based threats that were found to be live on the internet at the time of the test. The results indicate how effectively the products were at detecting and/or protecting against those threats in real time. 2 Home Anti-Malware Protection July - September 2020 MANAGEMENT Chief Executive Officer Simon Edwards CONTENTS Chief Operations Officer Marc Briggs Chief Human Resources Officer Magdalena Jurenko Chief Technical Officer Stefan Dumitrascu Introduction 04 TEstING TEAM Executive Summary 05 Nikki Albesa Zaynab Bawa 1. Total Accuracy Ratings 06 Thomas Bean Solandra Brewster Home Anti-Malware Protection Awards 07 Liam Fisher Gia Gorbold Joseph Pike 2. Threat Responses 08 Dave Togneri Jake Warren 3. Protection Ratings 10 Stephen Withey 4. Protection Scores 12 IT SUPPORT Danny King-Smith 5. Protection Details 13 Chris Short 6. Legitimate Software Ratings 14 PUBLICatION Sara Claridge 6.1 Interaction Ratings 15 Colin Mackleworth 6.2 Prevalence Ratings 16 Website selabs.uk Twitter @SELabsUK 6.3 Accuracy Ratings 16 Email [email protected] Facebook www.facebook.com/selabsuk 6.4 Distribution of Impact Categories 17 Blog blog.selabs.uk Phone +44 (0)203 875 5000 7. -

RECOMMENDED MERGER of AVAST PLC with NORTONLIFELOCK INC
NOT FOR RELEASE, PUBLICATION OR DISTRIBUTION, IN WHOLE OR IN PART, DIRECTLY OR INDIRECTLY, IN, INTO OR FROM ANY JURISDICTION WHERE TO DO SO WOULD CONSTITUTE A VIOLATION OF THE RELEVANT LAWS OR REGULATIONS OF SUCH JURISDICTION FOR IMMEDIATE RELEASE THIS ANNOUNCEMENT CONTAINS INSIDE INFORMATION 10 August 2021 RECOMMENDED MERGER of AVAST PLC with NORTONLIFELOCK INC. to be effected by means of a Scheme of Arrangement under Part 26 of the Companies Act 2006 Summary Further to the announcements made by NortonLifeLock Inc. (“NortonLifeLock”) and Avast plc (“Avast” or the “Company”) on 14 July 2021, the boards of NortonLifeLock and Avast are pleased to announce that they have reached agreement on the terms of a recommended merger of Avast with NortonLifeLock, in the form of a recommended offer by Nitro Bidco Limited (“Bidco”), a wholly- owned subsidiary of NortonLifeLock, for the entire issued and to be issued ordinary share capital of the Company (the “Merger”). It is intended that the Merger will be effected by means of a Court- sanctioned scheme of arrangement under Part 26 of the Companies Act (the “Scheme”). The boards of NortonLifeLock and Avast believe the Merger has compelling strategic logic and represents an attractive opportunity to create a new, industry leading consumer Cyber Safety business, leveraging the established brands, technical expertise and innovation of both groups to deliver substantial benefits to consumers, shareholders and other stakeholders. Under the terms of the Merger, Avast Shareholders will be entitled to receive: for each Avast Share held: USD 7.61 in cash and 0.0302 of a New NortonLifeLock Share in respect of their entire holding of Avast Shares (the “Majority Cash Option”). -

Aluria Security Center Avira Antivir Personaledition Classic 7
Aluria Security Center Avira AntiVir PersonalEdition Classic 7 - 8 Avira AntiVir Personal Free Antivirus ArcaVir Antivir/Internet Security 09.03.3201.9 x64 Ashampoo FireWall Ashampoo FireWall PRO 1.14 ALWIL Software Avast 4.0 Grisoft AVG 7.x Grisoft AVG 6.x Grisoft AVG 8.x Grisoft AVG 8.x x64 Avira Premium Security Suite 2006 Avira WebProtector 2.02 Avira AntiVir Personal - Free Antivirus 8.02 Avira AntiVir PersonalEdition Premium 7.06 AntiVir Windows Workstation 7.06.00.507 Kaspersky AntiViral Toolkit Pro BitDefender Free Edition BitDefender Internet Security BullGuard BullGuard AntiVirus BullGuard AntiVirus x64 CA eTrust AntiVirus 7 CA eTrust AntiVirus 7.1.0192 eTrust AntiVirus 7.1.194 CA eTrust AntiVirus 7.1 CA eTrust Suite Personal 2008 CA Licensing 1.57.1 CA Personal Firewall 9.1.0.26 CA Personal Firewall 2008 CA eTrust InoculateIT 6.0 ClamWin Antivirus ClamWin Antivirus x64 Comodo AntiSpam 2.6 Comodo AntiSpam 2.6 x64 COMODO AntiVirus 1.1 Comodo BOClean 4.25 COMODO Firewall Pro 1.0 - 3.x Comodo Internet Security 3.8.64739.471 Comodo Internet Security 3.8.64739.471 x64 Comodo Safe Surf 1.0.0.7 Comodo Safe Surf 1.0.0.7 x64 DrVirus 3.0 DrWeb for Windows 4.30 DrWeb Antivirus for Windows 4.30 Dr.Web AntiVirus 5 Dr.Web AntiVirus 5.0.0 EarthLink Protection Center PeoplePC Internet Security 1.5 PeoplePC Internet Security Pack / EarthLink Protection Center ESET NOD32 file on-access scanner ESET Smart Security 3.0 eTrust EZ Firewall 6.1.7.0 eTrust Personal Firewall 5.5.114 CA eTrust PestPatrol Anti-Spyware Corporate Edition CA eTrust PestPatrol -

Sécurité Et Antivirus Sur Mac
Sécurité et antivirus sur Mac Sécurité et antivirus sur Mac ............................................................................................................. 1 Sécurité : le discours officiel et les faits ......................................................................................... 3 Sécurité : les types de menace en activité ..................................................................................... 4 Les failles de sécurité ......................................................................................................................................... 4 Trojans ................................................................................................................................................................. 4 Phishing, vol d'identité ..................................................................................................................................... 5 Les mécanismes de défense standard ............................................................................................ 6 Quelles défenses contre des logiciels malveillants ? ................................................................. 7 Le chiffrement de données sous Mac OS X .................................................................................... 8 Antivirus sur Mac : est-ce bien nécessaire ? ................................................................................. 9 Les suites de sécurité sur Mac ....................................................................................................... -

Antivirus Downloads Free the Best Antivirus Software 2021: Free and Paid Options Compared
antivirus downloads free The best antivirus software 2021: free and paid options compared. Having one of the best antivirus software packages in your device is as important as it has ever been. Yup, it's an incredibly boring and dry thing to think about - particularly as many of us won't have been affected by a virus for years and years, if ever - but that's not meant to say you shouldn't have one of the best antivirus packs anyway. It's definitely still a case of 'rather have it and not need than need it and not have it', for sure. We can guarantee that there are baddies still out there and want to get your personal details, even if it might not be in the traditional sense of a virus anymore. So, whether you have a premium machine like one of the best gaming PCs or one of the best gaming laptops, or just a cheap one for work, having one of the best antivirus will protect you while you work or play. If you're looking to beef up security on an Apple Mac or MacBook though, you might want to consider checking out our antivirus for Macs guide. However, in the year 2021, it is a very saturated market. There are free versions that we remember from years ago still around - though now refined - and also some newer or much-revamped paid-for programs that are more comprehensive than ever. As a result, it can be a confusing market to work your way through. But fear not, we’ve looked at a range of options available, from premium to free, from some of the biggest players in online security, to help you make a safe and informed decision on the best antivirus software for you. -

Jotti Report
Online malware scan Page 1 of 2 Jotti's malware scan 2.99-TRANSITION_TO_3.00-R1 File to upload & scan: Browse... Submit Service Service load: 0% 100% File: iehv.zip Status: OK MD5: 7e1297c4bc4fc8d972b65396f27e3216 Packers detected: PE_PATCH.UPX, UPX Virus and Trojan Remover Download Free Trojan & Virus Scan Recommended and Used By The Experts www.pctools.com Scanner results Scan taken on 28 Feb 2009 16:48:40 (GMT) A-Squared Found nothing AntiVir Found nothing ArcaVir Found nothing Avast Found nothing AVG Antivirus Found nothing BitDefender Found nothing ClamAV Found nothing CPsecure Found nothing Dr.Web Found nothing F-Prot Antivirus Found nothing F-Secure Anti-Virus Found nothing Ikarus Found nothing Kaspersky Anti-Virus Found nothing NOD32 Found nothing Norman Virus Control Found nothing Panda Antivirus Found nothing Sophos Antivirus Found nothing VirusBuster Found nothing VBA32 Found nothing Powered by Disclaimer This service is by no means 100% safe. If this scanner says 'OK', it does not necessarily mean the file is clean. There could be a whole new virus on the loose. NEVER rely on one single product only, not even this service, even though it utilizes several products. Therefore, We cannot and will not be held responsible for any damage caused by results presented by this non-profit online service. Scanning can take a while, since several scanners are being used, plus the fact some scanners use very high levels of (time consuming) heuristics. Scanners used are Linux versions, differences with Windows scanners may or may not occur. Some scanners will only report one virus when scanning archives with multiple pieces of malware. -

Malware Analysis (CS6038) Week 08.1 Static Analyzers
Malware Analysis (CS6038) Week 08.1 Static Analyzers Scott Nusbaum [email protected] March 5, 2019 Overview • Homework • Static Analyzers – Overview – Pros / Cons – Free Tools (vscan, ClamAV, Yara) – Current Trends and Alternatives Homework • Homework 3: – Due Feb 28, 2019 – Graded and uploaded to Blackboard • Homework 4: – Assigned: Feb 28, 2019 – Due March 14, 2019 – Covers RE and Network Analysis Static Analyzers Signature-based Anti-Virus Systems • By far, the most popular weapon against cyber attacks is signature-based antivirus software. • When you are relying upon Symantec’s Norton Antivirus, Intel/McAfee’s VirusScan, and similar products, you are using a signature-based antivirus solution. • This may not be the exclusive function of the tools, but it is a significant component. Pros and Cons to Signatures • Pros • Cons – Signatures can be easily – Easily avoided or bypassed – Proprietary databases written. – Not all vendors detect the same way • Based on hashes – Vendors label or categorize • Strings or ”Unique” byte differently the same malware sample arrays – Scans can be time intensive – Open source repo’s exists – Always need to be updated to catch to cultivate and maintain the most resent version of malware signatures. Free Static Analyzers • vscan – Build around Google’s re2 library • ClamAV – Uses binary pattern language for efficiency vs versatility balance • Yara – Contains a more versatile pattern matching engine * https://zeltser.com/custom-signatures-for-malware-scan/ vscan • The tool vscan is a malware scanner that’s predominantly focused on searching for the presence of text-based evidence of malware, given a set of files. • The list of information to search for is managed in a data set named sensors in the config.lua file. -

Endpoint Integrity Check\221\316\211\236\210\352\227\227.Xlsx
エンドポイントインテグリティチェック - アンチウイルス対応メーカ一覧 360safe.com AEC, spol. s r.o. ALWIL Software AT & T AVG Technologies Agnitum Ltd AhnLab, Inc. Aliant America Online, Inc. Antiy Labs Authentium, Inc. Avanquest Publishing USA, Inc. Avira GmbH Beijing Rising Technology Corp. Ltd. Bell Bell Aliant BellSouth Bitdefender BullGuard Ltd. CJSC Returnil Software CMC Information Security Cat Computer Services Pvt. Ltd. Central Command , Inc. Check Point, Inc Cisco Systems, Inc. ClamAV ClamWin Comodo Group Computer Associates International, Inc Coranti, Inc Crawler LLC Cyber Defender Corp. Defender Pro LLC ESTsoft Corp. EathLink, Inc Emsi Software GmbH Eset Software F-Secure Corp. FairPoint Faronics Corporation Fortinet, Inc Frisk Software International GData Software AG GFI Software Grisoft, Inc. H+BEDV Datentechnik GmbH HAURI, Inc IKARUS Software GmbH Internet Security Systems, Inc. Jiangmin, Inc K7 Computing Pvt. Ltd. kaspersky Labs Kingsoft Corp. LANDesk Software, Ltd. Lavasoft, Inc. Lumension Security McAfee, Inc. MicroWorld Microsoft Corp. N-able Technologies Inc Nano Security New Technology Wave Inc. Norman ASA ONO Omniquad PC Tools Software PCSecurityShield Panda Software Parallels, Inc. Preventon Technologies Ltd. Prevx Ltd. Quick Heal Technologies (P) Ltd. Radialpoint Inc. Rogers SOFTWIN SalD Ltd. Security Coverage Inc. Sereniti, Inc. Shavlik Technologies Sophos, Plc Sunbelt Software Symantec Corp. TELUS Thirtyseven4, LLC. Tobit.Software Trend Micro, Inc. Troppus Software Corporation TrustPort, a.s. VCOM VMware, Inc. Verizon Videotron Virgin Broadband Virgin Media Virus BlokAda Ltd. Virus Buster Ltd. Webroot Software, Inc Yahoo!, Inc Zone Labs LLC e frontier, Inc. eEye Digital Security iolo technologies, LLC.