Printer and Scanner Forensics
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

END USER COMPUTING - NETWORK ATTACHED PRINTER SUPPORT Effective JULY 1, 2020
END USER COMPUTING - NETWORK ATTACHED PRINTER SUPPORT Effective JULY 1, 2020 SUPPORT OVERVIEW The OTS approach for providing services and support for all State technology is to utilize Lines of Service as a mechanism to adequately and appropriately recover the cost of operations related to each of the services. In order to further standardize EUC support operations as a line of service, network attached printers must be counted as a supported and managed device included in the Enterprise Device Support line of service. The EUC Enterprise Device Support rate of $60 per device per month is being applied to all purchased or legacy out of warranty network attached printers to cover the cost of the initial setup and ongoing operational management and support requirements. The EUC Network Copier and Warrantied Printer Support rate of $30 per device per month is being applied to all network based copiers and printers that are either rented through the Office of State Procurement copier contract or have an active service agreement or warranty with a third party provider. This service is applied to cover the EUC related support costs at a reduced rate to account for services already provided directly through the copier rental vendor or printer warranty vendor. WHAT IS INCLUDED Every network attached printer and copier requires EUC support throughout the lifecycle of the device. The line of service rate provides for the following services: · Initial device setup on the network · Initial device setup on the OTS print server · Installation -

HP Engage One Serial USB Thermal Printer
QuickSpecs HP Engage One Serial USB Thermal Printer Overview HP Engage One Serial USB Thermal Printer Model HP Engage One Serial USB Thermal Printer (Black) 1RL96AA HP Engage One Serial USB Thermal Printer (White) 3GS19AA Introduction Redefine your perception of retail printing with the HP Engage One Serial USB Thermal Printer, an eye-catching, compact, cubist printer designed to dazzle alongside your HP Engage One AiO System at the point of sale. Key Features and Benefits • Print quickly with 114 mm per second print speed and 8 MB of integrated memory. Add your logo, special offers or coupons to receipts with 203 DPI and fonts that include Unicode, Arabic, and Asian. • Connect to your retail system with an optional USB, PUSB or Serial cable kit (sold separately), and drive up to two optional cash drawers through connections on the printer. • Place the ultra-compact printer where you need it with the assurance that the internal steel frame can withstand the everyday wear and tear of retail environments. Compatibility The HP Engage One Serial USB Thermal Printer is compatible with the HP Engage One AiO Systems. NOTE: Not all Point of Sale system models are available in all regions. Not all HP Cash Drawer models are available in all regions. This printer does not comply with fiscalization requirements that may be required in certain countries. Service and Support Three (3) year limited warranty with advance exchange when purchased from HP. c05573122 —16010 Worldwide — Version 6 — October 2, 2019 Page 1 QuickSpecs HP Engage One Serial USB -

Mobile Print/Scan Guide for Brother Iprint&Scan
Mobile Print/Scan Guide for Brother iPrint&Scan Version D ENG Definitions of notes We use the following icon throughout this user’s guide: Notes tell you how you should respond to a situation that may arise or give Note tips about how the operation works with other features. Trademarks The Brother logo is a registered trademark of Brother Industries, Ltd. Android is a trademark of Google Inc. Apple, Macintosh, Mac OS, iCloud, iPhone, iPod touch, iPad and Safari are trademarks of Apple Inc., registered in the U.S. and other countries. Microsoft and Windows are registered trademarks of Microsoft Corporation in the United States and/or other countries. Each company whose software title is mentioned in this manual has a Software License Agreement specific to its proprietary programs. Any trade names and product names of companies appearing on Brother products, related documents and any other materials are all trademarks or registered trademarks of those respective companies. ©2011 Brother Industries, Ltd. All rights reserved. i Table of Contents Section I For Android™ Devices 1 Introduction 2 Overview....................................................................................................................................................2 Hardware requirement...............................................................................................................................3 Supported operating systems..............................................................................................................3 Network settings..................................................................................................................................3 -
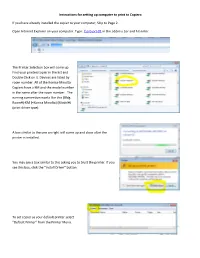
Instructions for Setting up Computer to Print to Copiers
Instructions for setting up computer to print to Copiers: If you have already installed the copier to your computer, Skip to Page 2. Open Internet Explorer on your computer. Type: \\csb-prt-01 in the address bar and hit enter. The Printer Selection box will come up. Find your printer/copier in the list and Double Click on it. Devices are listed by room number. All of the Konica-Minolta Copiers have a KM and the model number in the name after the room number. The naming convention works like this (Bldg. Room#)-KM (=Konica Minolta) (Model#) (print driver type). A box similar to the one on right will come up and close after the printer is installed. You may see a box similar to this asking you to trust the printer. If you see this box, click the “Install Driver” button. To set copier as your default printer select “Default Printer” from the Printer Menu. Changing Copier to Use Account Code From the Printer control panel right click your printer and choose Printing Preferences. You can find this in the Control Panel>Printers. Or you can open Word >Print> Printer Properties. You should see the box to the right. Click on “Basic” Tab In the “Printing Preferences” Click on the “Authentication/Account Track” button. Type your Employee ID in the Password box. Put Your Name in the Department Name box. (If this box is grayed out, the copier is not configured to use “Account Track”) Click the “Verify” button this will check to see if your account number works Click OK. -

Class -IV Super Computer Year- 2020-21
s Class -IV Super Computer Year- 2020-21 1 1. Input and Output devices • Focus of the Chapter 1. Input devices 2. Output devices • Introduction The computer will be of no use unless it is able to communicate with the outside world. Input/output devices are required for users to communicate with the computer. An input device sends information to a computer system for processing. An input device tor a computer allows you to enter information. An output device can receive data from another device, but it cannot send data to another device. There are different devices of the computer that help it to do work. Input Devices The devices which are used to input the data and the program in the computer are known as "Input Devices". For the text input, keyboard are used, microphone is used for audio or sound input. 2 Keyboard The keyboard is the most common input device. A 'keyboard' is a human interface device which is "-presented as a layout of buttons. It is a text-based input device that allows the user to interact with the computer through a set of keys mounted on a board. Mouse After the keyboard, the mouse is the most common type of input device. A mouse makes the process of navigating the screen much easier than trying to use just a keyboard. A mouse usually uses a ball, light or a laser to track movement. Joystick A joystick is an input device consisting of a large pointed stick and input buttons on it. We can use this for playing games on the computer. -

Peripheral Guidance and How to Connect a Home Printer
Peripheral Guidance and How to Connect a Home Printer In the current COVID-19 telework environment, you may have the need to use your personal printer, monitor or mouse, or even use a headset for a meeting from a NASA computer. In accordance with NASA Policy Directive NPD 2540.1I Acceptable Use of Government Office Property Including Information Technology section 5, clause (6), “Users shall not connect unauthorized non-NASA devices to GFP (Government Furnished Property) via Universal Serial Bus (USB), Bluetooth, or other connection methods.” This policy is currently being updated, and the following guidelines should be adhered to: • Allowed non-NASA device categories for wired and wireless connectivity to a GFP computer include a personally owned: monitor, keyboard, mouse, scanner, printer, home network router, headset and headphone. • Disallowed non-NASA device categories for connection to a GFP computer: USB or “thumb drive” external storage device, external hard drive, smart phone/tablet and any device that provides/offers data storage. • No software shall be installed, or peripheral equipment connected by wired or wireless (including Bluetooth) or device/system used to process NASA data from the following companies or any subsidiary or affiliate of such entities: . Kaspersky Lab . Hikvision Digital Technology Company . Huawei Technologies . Dahua Technology Company . ZTE Corp. Hytera Communications Corp. To Install a New Printer Follow the instructions below to install a new printer. Detailed instructions with screen shots are available in Knowledge Article KB0018594. Due to a recent policy change, elevated privilege (EP) is not needed for printer installation. Important: If the printer is a networked printer at your home location, you will need to disconnect from NASA's VPN before performing the steps below. -

Computer Basics Study Guide Monitor CPU Mouse Keyboard Scanner Printer
Computer Basics Study Guide CPU (Central Processing Unit) – This is the brain of the computer. The central processing unit, motherboard, hard drive, memory, etc. are all contained in the computer case…everything that makes the computer work. Monitor – A device that displays the signals of the computer. Today, monitors are typically thin or slimline LCD displays. Keyboard – A panel of keys used to operate a computer. It is the primary way we enter data into a computer. Mouse – a hand-operated electronic device that controls the coordinates of a cursor or pointer on your computer screen as you move it around on a pad. An optical mouse has an optical light on the bottom to control the cursor or pointer. A mechanical mouse has a ball on the bottom that rolls to control the cursor or pointer. Printer – A machine connected to a computer used to print text or pictures onto paper. Scanner – a device that captures images from photographic prints, posters, magazine pages, and similar sources for computer editing and display. CPU Monitor Keyboard Mouse Scanner Printer Computer: An electronic device that can store, retrieve, and process data. Kinds of Computers: Desktop, laptop, tablets, smartphones, and even some gaming consoles and TVs 2 Styles of Computers: PC and MAC 2 Parts to Computers: Hardware and Software Hardware – The physical components of a computer that you can see and touch. Examples: Monitor, CPU, Keyboard, Mouse, Printer, and Scanner Input Devices – Any peripheral (piece of computer hardware equipment) used to provide data and control signals to an information processing system such as a computer. -

Lobbyguard® Assist Installation Guide
LobbyGuard® Assist Installation Guide Installation Instructions ..................................................................................... 3 Step 1: Installation Checklist ............................................................................ 4 Step 2: Install the LobbyGuard Assist Software ............................................... 5 Step 3: Install your Hardware ........................................................................... 6 LobbyGuard Assist Station ............................................................................ 7 Printer ............................................................................................................ 9 Webcam ...................................................................................................... 11 Driver License Scanner ............................................................................... 18 Bar Code Scanner ....................................................................................... 26 Step 4: Test your LobbyGuard Assist Installation ........................................... 27 Step 5: Get Training ....................................................................................... 29 Additional Resources ....................................................................................... 30 Appendices ....................................................................................................... 31 Appendix A: Customer Registration Email ..................................................... 32 Appendix -

User Guide: RS-232C/RS-422 Serial Interface Option for OKI® B6100 Printer
User Guide: RS-232C/RS-422 Serial Interface Option for OKI® B6100 Printer 59345001 i RS-232C/RS-422 Serial Interface Option Trademarks The following are trademarks or registered trademarks of their respective owners. Other product names mentioned in this manual may also be trademarks or registered trademarks of their respective owners. Registered trademarks are registered in the United States Patent and Trademark Office; some trademarks may also be registered in other countries. PostScript is a trademark of Adobe Systems Incorporated for a page description language and may be registered in certain jurisdictions. OKI, OkiLPR, and OkiLAN are registered trademaks of Oki Electric Industry Company, Ltd. Adobe, Adobe PhotoShop, Adobe PageMaker/Adobe Systems Incorporated OpenVMS, Compaq/Compaq Computer Corporation Microsoft, MS-DOS, Windows/Microsoft Corporation The ENERGY STAR logo/United States Environmental Protection Agency. The ENERGY STAR emblem does not represent EPA endorsement of any product or service. Proprietary Statement The digitally encoded software included with your printer is copyrighted. All Rights Reserved. This software may not be reproduced, modified, displayed, transferred, or copied in any form or in any manner or on any media, in whole or in part, without the express written permission of the manufacturer. Copyright Notice This manual is copyrighted. All Rights Reserved. This manual may not be copied in whole or in part, nor transferred to any other media or language, without the express written permission of the manufacturer. The specifications of your printer and the content of this publication are subject to change without prior notice. Every attempt has been made to verify the accuracy of the content herein RS-232C/RS-422 Serial Interface Option ii How This Guide is Organized Chapter 1 - Installing the Serial Interface This chapter explains the procedure for installing the RS-232C/RS-422 Serial Interface option in OKI B6100 Laser Printers. -

Page VLAC Technology and Internet Equipment Internet
VLAC TECHNOLOGY AND INTERNET EQUIPMENT AND ACCEPTABLE USE AGREEMENT VLAC Technology and Internet Equipment Internet Access and Technology Equipment Oakland Schools shall provide each student with the option of receiving Internet access at the student’s home, a computer, printer, and a webcam (if not already built into the computer) to access the Virtual Learning Academy Consortium (“VLAC”) program curriculum and complete the student’s coursework under the VLAC program. Oakland Schools is the legal title owner of all technology equipment issued to a student participating in VLAC unless purchased by the parent/legal guardian. Parents/legal guardians may opt to have their student use their personal computer, printer, webcam, or Internet service (provided that such computer or printer meets certain technological requirements as determined by Oakland Schools). For purposes of this VLAC Technology and Internet Acceptable Use Agreement that will be referred to as Agreement throughout this document, computer means an electronic device, including but not limited to, a desktop, laptop, notebook, or tablet computer, issued to a student in connection with the VLAC program. The computer, printer, webcam and Internet service provided shall be determined at the sole discretion of Oakland Schools. After a student has completed one full year of the VLAC program, the computer and/or printer may be purchased. The sale price of VLAC computers and printers shall be calculated using a Straight Line Depreciation Method with a 10% of purchase price salvage value and a four year depreciation/useful life (Purchase Price – Salvage Value/Years of Estimated Life = Depreciation Value or Sale Price). Lost, Stolen or Damaged Computer, Printer or Webcam Students are responsible for the safeguarding of technology equipment issued by Oakland Schools. -

Title: Concept of Hardware Versus Software . Such As: Webcam/Printer
Title: Concept of hardware versus software . Such as: Webcam/Printer versus their controlling software Date June, 2007 REF No 3.30 Contributor Semeena Kader Std 3 Reviewer Usha Viswanathan Brief Description: This topic introduces concepts of Hardware and Software. Goal: To become familiar with hardwares and their supporting softwares. Pre-requisites: Familiar with computer . Should know about computer peripherals and basic applications. Learning Outcome: Able to know about hardware and their controlling software . Duration: 1Session References: http://www.webopedia.com/TERM/S/software.html http://www.computerhope.com/issues/ch000039.htm http://www.liv.ac.uk/HPC/HTMLF90Course/HTMLF90CourseSlidesnod e3.html Detailed Description Computer hardware is the physical part of a computer . The Monitor , Keyboard , Mouse , Printer , Web cam etc are examples for hardwares. These are items that you can actually touch or move from one desk or room to another. Computer software can be defined as a set of instructions that tells the computer how to behave. These are the program or procedure are used to operate computer hardware. Computer instructions or data, anything that can be stored electronically is software. The storage devices and display devices are the hardware. The distinction between software and hardware is sometimes confusing because they are so integrally linked. For example, when you purchase a program, you are buying a software, but to buy the software, you need to buy the disk (hardware) on which the software is recorded. Software is code or instructions that tell a computer and other related hardware how to operate. This code can be viewed and executed using a computer or other hardware device. -

Mobile Print/Scan Guide for Brother Iprint&Scan
Mobile Print/Scan Guide for Brother iPrint&Scan Version I ENG Definitions of notes We use the following icon throughout this user’s guide: Notes tell you how you should respond to a situation that may arise or give NOTE tips about how the operation works with other features. Trademarks The Brother logo is a registered trademark of Brother Industries, Ltd. Brother is a trademark of Brother Industries, Ltd. Google, Android, Android Market and Gmail are trademarks of Google Inc. Use of these trademarks is subject to Google Permissions. Apple, OS X, iCloud, iPhone, iPod touch, iPad, iTunes and Safari are trademarks of Apple Inc., registered in the U.S. and other countries. Microsoft, Windows, Excel and PowerPoint are registered trademarks of Microsoft Corporation in the United States and/or other countries. Wi-Fi is a registered trademarks of the Wi-Fi Alliance. Wi-Fi Direct is a trademark of the Wi-Fi Alliance. The Bluetooth word mark and logos are owned by the Bluetooth SIG, Inc. and any use of such marks by Brother Industries, Ltd. is under license. Each company whose software title is mentioned in this manual has a Software License Agreement specific to its proprietary programs. Any trade names and product names of companies appearing on Brother products, related documents and any other materials are all trademarks or registered trademarks of those respective companies. ©2011-2012 Brother Industries, Ltd. All rights reserved. i Table of Contents Section I For Android™ Devices 1 Introduction 2 Overview....................................................................................................................................................2