Inform Ation Gov Ernance
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Care Bill for Elderly £5 More in Borough
STAR BRIEFING 19 Limbering up for a monumental 10k run Shropshire Star Keen Shropshire runners are being en- Report by William Tomaney have decided to treat all mums to a compli- local area. Money raised from this year’s couraged to lace up their trainers for the [email protected] mentary glass of bubbly, so while the com- race will go to Lilleshall Cricket Club to return of a popular annual race. petitors are run off their feet they can be enable them to carry out work to improve Anti-Semitic Preparations are under way for the sixth said: “With six weeks to go to race day assured back at base their mothers will be its home. Lilleshall Monumental 10k race, near there is still plenty of time to dust off your looked after with their feet up.” The Lilleshall race had received funding Newport, which will take place on Sunday, trainers and get yourself prepared to join in She said prizes would be awarded for the from Shropshire Homes. March 15. this very popular event. first three men and women to cross the fin- The race is part of Newport Running incidents soar Hundreds of runners are expected to take “A fun run for children and those adults ishing line, category prizes in the 10k race Club’s ‘Fourmidables’ series – which sees a part in the race which is organised by New- who decide to play it safe will start the day and all 10k entrants would received an em- number of races held throughout the year Last year saw a record number of anti-Semitic inci- Thursday, February 5, 2015 port and District Running Club and starts at 10.45am, with the 10k participants set- broidered hand towel for taking part. -

Reach PLC Summary Response to the Digital Markets Taskforce Call for Evidence
Reach PLC summary response to the Digital Markets Taskforce call for evidence Introduction Reach PLC is the largest national and regional news publisher in the UK, with influential and iconic brands such as the Daily Mirror, Daily Express, Sunday People, Daily Record, Daily Star, OK! and market leading regional titles including the Manchester Evening News, Liverpool Echo, Birmingham Mail and Bristol Post. Our network of over 70 websites provides 24/7 coverage of news, sport and showbiz stories, with over one billion views every month. Last year we sold 620 million newspapers, and we over 41 million people every month visit our websites – more than any other newspaper publisher in the UK. Changes to the Reach business Earlier this month we announced changes to the structure of our organisation to protect our news titles. This included plans to reduce our workforce from its current level of 4,700 by around 550 roles, gearing our cost base to the new market conditions resulting from the pandemic. These plans are still in consultation but are likely to result in the loss of over 300 journalist roles within the Reach business across national, regional and local titles. Reach accepts that consumers will continue to shift to its digital products, and digital growth is central to our future strategy. However, our ability to monetise our leading audience is significantly impacted by the domination of the advertising market by the leading tech platforms. Moreover, as a publisher of scale with a presence across national, regional and local markets, we have an ability to adapt and achieve efficiencies in the new market conditions that smaller local publishers do not. -

Scottsih Newspapers Have a Long Hisotry Fof Involvement With
68th IFLA Council and General Conference August 18-24, 2002 Code Number: 051-127-E Division Number: V Professional Group: Newspapers RT Joint Meeting with: - Meeting Number: 127 Simultaneous Interpretation: - Scottish Newspapers and Scottish National Identity in the Nineteenth and Twentieth Centuries I.G.C. Hutchison University of Stirling Stirling, UK Abstract: Scotland is distinctive within the United Kingdom newspaper industry both because more people read papers and also because Scots overwhelmingly prefer to read home-produced organs. The London ‘national’ press titles have never managed to penetrate and dominate in Scotland to the preponderant extent that they have achieved in provincial England and Wales. This is true both of the market for daily and for Sunday papers. There is also a flourishing Scottish local weekly sector, with proportionately more titles than in England and a very healthy circulation total. Some of the reasons for this difference may be ascribed to the higher levels of education obtaining in Scotland. But the more influential factor is that Scotland has retained distinctive institutions, despite being part of Great Britain for almost exactly three hundred years. The state church, the education system and the law have not been assimilated to any significant amount with their counterparts south of the border. In the nineteenth century in particular, religious disputes in Scotland generated a huge amount of interest. Sport in Scotlaand, too, is emphatically not the same as in England, whether in terms of organisation or in relative popularity. Additionally, the menu of major political issues in Scotland often has been and is quite divergent from England – for instance, the land question and self-government. -
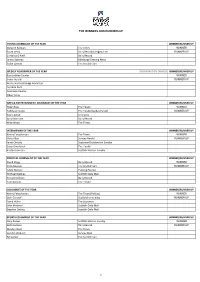
The Winners and Runners Up
THE WINNERS AND RUNNERS UP YOUNG JOURNALIST OF THE YEAR WINNER/RUNNER UP Gurpeet Narwan The Times WINNER Sarah Vesty Daily Record/Glasgow Live RUNNER UP Christina O'Neill Daily Record James Delaney Edinburgh Evening News Colan Lamont The Scottish Sun WEEKLY NEWSPAPER OF THE YEAR SPONSORED BY DIAGEO WINNER/RUNNER UP East Lothian Courier WINNER Irvine Herald RUNNER UP Aidrie and Coatrbidge Advertiser Ayrshire Post Inverness Courier Oban Times ARTS & ENTERTAINMENT JOURNALIST OF THE YEAR WINNER/RUNNER UP Peter Ross The Herald WINNER Teddy Jamieson The Herald/Sunday Herald RUNNER UP Paul English Freelance Anna Burnside Daily Record Mike Wade The Times INTERVIEWER OF THE YEAR WINNER/RUNNER UP Kenny Farquharson The Times WINNER Vicky Allan Sunday Herald RUNNER UP Janet Christie Scotsman/Scotland on Sunday Susan Swarbrick The Herald Kirsten Johnson Scottish Mail on Sunday POLITICAL JOURNALIST OF THE YEAR WINNER/RUNNER UP David Clegg Daily Record WINNER Chris Musson The Scottish Sun RUNNER UP Adele Merson Evening Express Michael Blackley Scottish Daily Mail Torcuil Crichton Daily Record Tom Gordon The Herald COLUMNIST OF THE YEAR WINNER/RUNNER UP Kenny Farquharson The Times (Politics) WINNER Dani Garavelli Scotland on Sunday RUNNER UP David Walsh The Scotsman John Macleod Scottish Daily Mail Stephen Daisley Scottish Daily Mail SPORTS COLUMNIST OF THE YEAR WINNER/RUNNER UP Gary Keown Scottish Mail on Sunday WINNER Keith Jackson Daily Record RUNNER UP Alasdair Reid The Times Gordon Waddell Sunday Mail Bill Leckie The Scottish Sun 1 THE WINNERS AND -

Sheet1 Page 1 Express & Star (West Midlands) 113,174 Manchester Evening News 90,973 Liverpool Echo 85,463 Aberdeen
Sheet1 Express & Star (West Midlands) 113,174 Manchester Evening News 90,973 Liverpool Echo 85,463 Aberdeen - Press & Journal 71,044 Dundee Courier & Advertiser 61,981 Norwich - Eastern Daily Press 59,490 Belfast Telegraph 59,319 Shropshire Star 55,606 Newcastle-Upon-Tyne Evening Chronicle 52,486 Glasgow - Evening Times 52,400 Leicester Mercury 51,150 The Sentinel 50,792 Aberdeen - Evening Express 47,849 Birmingham Mail 47,217 Irish News - Morning 43,647 Hull Daily Mail 43,523 Portsmouth - News & Sports Mail 41,442 Darlington - The Northern Echo 41,181 Teesside - Evening Gazette 40,546 South Wales Evening Post 40,149 Edinburgh - Evening News 39,947 Leeds - Yorkshire Post 39,698 Bristol Evening Post 38,344 Sheffield Star & Green 'Un 37,255 Leeds - Yorkshire Evening Post 36,512 Nottingham Post 35,361 Coventry Telegraph 34,359 Sunderland Echo & Football Echo 32,771 Cardiff - South Wales Echo - Evening 32,754 Derby Telegraph 32,356 Southampton - Southern Daily Echo 31,964 Daily Post (Wales) 31,802 Plymouth - Western Morning News 31,058 Southend - Basildon - Castle Point - Echo 30,108 Ipswich - East Anglian Daily Times 29,932 Plymouth - The Herald 29,709 Bristol - Western Daily Press 28,322 Wales - The Western Mail - Morning 26,931 Bournemouth - The Daily Echo 26,818 Bradford - Telegraph & Argus 26,766 Newcastle-Upon-Tyne Journal 26,280 York - The Press 25,989 Grimsby Telegraph 25,974 The Argus Brighton 24,949 Dundee Evening Telegraph 23,631 Ulster - News Letter 23,492 South Wales Argus - Evening 23,332 Lancashire Telegraph - Blackburn 23,260 -

Pressreader Newspaper Titles
PRESSREADER: UK & Irish newspaper titles www.edinburgh.gov.uk/pressreader NATIONAL NEWSPAPERS SCOTTISH NEWSPAPERS ENGLISH NEWSPAPERS inc… Daily Express (& Sunday Express) Airdrie & Coatbridge Advertiser Accrington Observer Daily Mail (& Mail on Sunday) Argyllshire Advertiser Aldershot News and Mail Daily Mirror (& Sunday Mirror) Ayrshire Post Birmingham Mail Daily Star (& Daily Star on Sunday) Blairgowrie Advertiser Bath Chronicles Daily Telegraph (& Sunday Telegraph) Campbelltown Courier Blackpool Gazette First News Dumfries & Galloway Standard Bristol Post iNewspaper East Kilbride News Crewe Chronicle Jewish Chronicle Edinburgh Evening News Evening Express Mann Jitt Weekly Galloway News Evening Telegraph Sunday Mail Hamilton Advertiser Evening Times Online Sunday People Paisley Daily Express Gloucestershire Echo Sunday Sun Perthshire Advertiser Halifax Courier The Guardian Rutherglen Reformer Huddersfield Daily Examiner The Independent (& Ind. on Sunday) Scotland on Sunday Kent Messenger Maidstone The Metro Scottish Daily Mail Kentish Express Ashford & District The Observer Scottish Daily Record Kentish Gazette Canterbury & Dist. IRISH & WELSH NEWSPAPERS inc.. Scottish Mail on Sunday Lancashire Evening Post London Bangor Mail Stirling Observer Liverpool Echo Belfast Telegraph Strathearn Herald Evening Standard Caernarfon Herald The Arran Banner Macclesfield Express Drogheda Independent The Courier & Advertiser (Angus & Mearns; Dundee; Northants Evening Telegraph Enniscorthy Guardian Perthshire; Fife editions) Ormskirk Advertiser Fingal -

Scottish Newspapers and the Crisis of the Print Press: Journalistic Autonomy and Digital Transition in a Liberal Media System
Scottish newspapers and the crisis of the print press: journalistic autonomy and digital transition in a liberal media system Article (Accepted Version) Dekavalla, Marina (2018) Scottish newspapers and the crisis of the print press: journalistic autonomy and digital transition in a liberal media system. Recherches en Communication, 44. pp. 103-119. ISSN 2033-3331 This version is available from Sussex Research Online: http://sro.sussex.ac.uk/id/eprint/74343/ This document is made available in accordance with publisher policies and may differ from the published version or from the version of record. If you wish to cite this item you are advised to consult the publisher’s version. Please see the URL above for details on accessing the published version. Copyright and reuse: Sussex Research Online is a digital repository of the research output of the University. Copyright and all moral rights to the version of the paper presented here belong to the individual author(s) and/or other copyright owners. To the extent reasonable and practicable, the material made available in SRO has been checked for eligibility before being made available. Copies of full text items generally can be reproduced, displayed or performed and given to third parties in any format or medium for personal research or study, educational, or not-for-profit purposes without prior permission or charge, provided that the authors, title and full bibliographic details are credited, a hyperlink and/or URL is given for the original metadata page and the content is not changed in any way. http://sro.sussex.ac.uk Scottish newspapers and the crisis of the print press: journalistic autonomy and digital transition in a liberal media system Marina Dekavalla, University of Sussex Abstract: This article examines how members of the Scottish newspaper industry view the current crisis of the print press and the future of their titles. -

Demand-Side Sentencing for Online Sexual Exploitation of Children
FALLING SHORT: DEMAND-SIDE SENTENCING FOR ONLINE SEXUAL EXPLOITATION OF CHILDREN Composite Case Review, Analysis, and Recommendations for the United Kingdom October 2020 A product of Center to End Online Sexual Exploitation of Children [email protected] Contact Information For more information, please contact: John Tanagho Director, IJM’s Center to End Online Sexual Exploitation of Children [email protected] Brandon Kaopuiki Technical Advisor, IJM Global Hub Against Online Sexual Exploitation of Children [email protected] IJM is available for and interested in providing further consultation to demand and source- side governments about online sexual exploitation of children and recommendations to combat it. Such consultation can be provided confidentially, if necessary, and without cost. Acknowledgements: IJM would like to thank and acknowledge the following for providing input and feedback to the paper: Iain Drennan, Executive Director, WePROTECT Global Alliance; Sara Carnegie, Legal Projects Director, International Bar Association; Donald Findlater, Director, The Lucy Faithfull Foundation; Ollie Simpson, Policy Advisor, The Office of The Sentencing Council; Raveena Jawanda, Policy Officer, Bail, Sentencing and Release Policy Unit, Ministry of Justice; Louise Gleich, Human Trafficking Senior Policy Officer, Care; Dylan Moses, Rosie Naylor and Annabel Goulding, K&L Gates UK; International Justice Mission UK. Special thanks to Julienne Daly (IJM Legal Fellow) for leading the research and writing for this project. FALLING SHORT: DEMAND-SIDE -

Vol53no3 with Accts
Vol 53 No 3 ISSN 1479-0882 May / June 2019 The Wareham (Dorset) which is celebrating ten years of being run by a Trust – see Newsreel p28; photo taken May 2006 The Hucknall (Notts). A new owner is planning to convert it into a four-screen cinema – see Newsreel p24; photo taken May 2008 I owe all members and also Michael Armstrong and his colleagues at the Wymondham a big apology. For the first two issues this year Company limited by guarantee. Reg. No. 04428776. I erroneously printed last year’s programme in the ‘Other Registered address: 59 Harrowdene Gardens, Teddington, TW11 0DJ. Events’ section of the Bulletin. I must have misfiled the current Registered Charity No. 1100702. Directors are marked in list below. programme card and used the old one instead. I have done a suitable penance. The listing on p3 is correct! Thank you all for continuing to send in items for publication. I have been able to use much of the backlog this time. On p32 I have printed Full Membership (UK)..................................................................................£29 some holiday snaps from Ned Williams. I have had these in stock Full Membership (UK under 25s)...............................................................£15 since July 2017, just waiting for a suitable space. I say this simply to Overseas (Europe Standard & World Economy)........................................£37 prove I throw nothing away deliberately – although, as noted above, I Overseas (World Standard).........................................................................£49 Associate Membership (UK & Worldwide).................................................£10 can sometimes do so by accident. Life Membership (UK only).................................£450; aged 65 & over £350 I still have held over a major article from Gavin McGrath on Cinemas Life Membership for Overseas members will be more than this; please contact the membership secretary for details. -
News Hartlepool MP Mike Hill Resigns to Trigger By- Election
Jobs Classieds Login More Menu News All News Hartlepool MP Mike Hill resigns to trigger by- election UK News | Published: Mar 16, 2021 | Last Updated: Mar 16, 2021 The poll will mark the rst test of Sir Keir Starmer’s leadership of the Labour Party. Subscribe to our daily newsletter! Email Address Sign Up Mike Hill has resigned as MP for Hartlepool, triggering a by-election Mike Hill has quit as an MP, Labour has conrmed, triggering a by-election. The sudden announcement sets up a fresh electoral contest in Hartlepool, a seat long-held by Labour, marking the rst test of Sir Keir Starmer’s leadership since taking over from Jeremy Corbyn last year. “Mike Hill has resigned as Member of Parliament for Hartlepool with immediate effect,” a party spokeswoman said. On Tuesday, Mr Hill appeared to have deleted his Twitter account. The 57-year-old had represented the North East of England town since 2017. Sir Keir Starmer (Leon Neal/PA) You May Like Sponsored Links by Taboola Seniors Born 1941 - 1971 Could Claim This Benet British Seniors Invest in Amazon and you could earn an extra income from home 101 Investing He held off a Conservative and Brexit Party challenge at the last election but saw his majority slashed by more than half to just under 3,600. His resignation follows reports that he used taxpayers’ money to ght a staff member’s claim of unfair dismissal, sexual assault and harassment. Mr Hill was suspended by Labour in September 2019 over allegations he sexually harassed a woman, but had the whip restored to contest the general election two months later. -

Sources for LONGDON on TERN
Sources for LONGDON ON TERN This guide gives a brief introduction to the variety of sources available for the parish of Longdon on Tern at Shropshire Archives. Printed books: General works - These may also be available at Wellington library Eyton, Antiquities of Shropshire Transactions of the Shropshire Archaeological Society Shropshire Magazine Trade Directories which give a history of the town, main occupants and businesses, 1828-1941 Victoria County History of Shropshire – Volume X Parish Packs Monumental Inscriptions List of more specific books available - (search http://search.shropshirehistory.org.uk for a more comprehensive list) C64 Reading Room Antiquities of Shropshire, vol VIII – Robert Eyton C66 My Shropshire Days on Common Ways – John Beard K22.3 An account of the improvements on the estates of the Marquess of Stafford in the counties of Staffordshire and Salop and on the estate of Sutherland with remarks Parts 1 & 11 – James Loch 1820 St Bartholomew’s church, Longdon Upon Tern from www.secretshropshire.org.uk website 6009/128 Sources on microfiche or film: Parish and non-conformist church registers Baptisms Marriages / Banns Burials St Bartholomew’s church 1692-1955 1692-1969 / 1828-1960 1692-1955 Census returns 1841, 1851(indexed), 1861, 1871, 1881, 1891, 1901 Census returns for the whole country to 1911 can be looked at on the Ancestry website Maps Ordnance Survey maps 25” to the mile and 6 “to the mile, c1880, c1901 (OS reference: old series XXXV.4 new series SJ 6115) Tithe map and apportionment, 1839 Newspapers Shrewsbury Chronicle, 1772 onwards (NB from 1950 as originals only – Reader’s Ticket required) Shropshire Star, 1964 onwards Wellington Journal, 1901 onwards as originals (from 1854 on film at Telford Library) Archives: To see these sources you need a Shropshire Archives Reader's Ticket. -

News Consumption Survey 2019
News Consumption Survey 2019 Wales PROMOTING CHOICE • SECURING STANDARDS • PREVENTING HARM About the News Consumption report 2019 The aim of the News Consumption report is to inform understanding of news consumption across the UK and within each UK nation. This includes sources and platforms used, the perceived importance of different outlets for news, attitudes towards individual news sources, international and local news use. The primary source* is Ofcom’s News Consumption Survey. The survey is conducted using face-to- face and online interviews. In total, 2,156 face-to-face and 2,535 online interviews across the UK were carried out during 2018/19. The interviews were conducted over two waves (November & December and March) in order to achieve a robust and representative view of UK adults. The sample size for all adults over the age of 16 in Wales is 475. The full UK report and details of its methodology can be read here. *The News Consumption 2019 report also contains information from a range of industry currencies including BARB for television viewing, TouchPoints for newspaper readership, ABC for newspaper circulation and Comscore for online consumption. PROMOTING CHOICE • SECURING STANDARDS • PREVENTING HARM 2 Key findings from the 2019 report • TV remains the most-used platform for news nowadays by adults in Wales at 75%, compared to 80% last year. • Social media is the second most used platform for news in Wales (45%) and is used more frequently than any other type of internet news source. • More than half of adults (57%) in Wales use BBC One for news, but this is down from 68% last year.