Implementing Host Services and Applications
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

List of TCP and UDP Port Numbers - Wikipedia, the Free Encyclopedia 6/12/11 3:20 PM
List of TCP and UDP port numbers - Wikipedia, the free encyclopedia 6/12/11 3:20 PM List of TCP and UDP port numbers From Wikipedia, the free encyclopedia (Redirected from TCP and UDP port numbers) This is a list of Internet socket port numbers used by protocols of the Transport Layer of the Internet Protocol Suite for the establishment of host-to-host communications. Originally, these port numbers were used by the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP), but are used also for the Stream Control Transmission Protocol (SCTP), and the Datagram Congestion Control Protocol (DCCP). SCTP and DCCP services usually use a port number that matches the service of the corresponding TCP or UDP implementation if they exist. The Internet Assigned Numbers Authority (IANA) is responsible for maintaining the official assignments of port numbers for specific uses.[1] However, many unofficial uses of both well-known and registered port numbers occur in practice. Contents 1 Table legend 2 Well-known ports: 0–1023 3 Registered ports: 1024–49151 4 Dynamic, private or ephemeral ports: 49152–65535 5 See also 6 References 7 External links Table legend Color coding of table entries Official Port/application combination is registered with IANA Unofficial Port/application combination is not registered with IANA Conflict Port is in use for multiple applications (may be official or unofficial) Well-known ports: 0–1023 The port numbers in the range from 0 to 1023 are the well-known ports. They are used by system processes that provide widely-used types of network services. -

Edition with Romkey, April 16, 1986 (PDF)
PC/IP User's Guide MASSACHUSETTS INSTITUTE OF TECHNOLOGY Laboratory For Computer Science Network programs based on the DoD Internet Protocol for the mM Personal Computer PC/~ release or March, 1986; document updated Aprill4, 1986 by: Jerome H. Saltzer John L. Romkey .• Copyright 1984, 1985, 1986 by the Massachusetts Institute or Technology Permission to use, copy, modlt'y, and distribute these programs and their documentation ror any purpose and without ree ls hereby granted, provided that this copyright and permission notice appear on all copies and supporting documentation, the name or M.I.T. not be used in advertising or publlclty pertalnlng to dlstrlbutlon or the programs without written prior permission, and notice be glven in supporting documentation that copying and distribution ls by permlsslon or M.I.T. M.I.T. makes no representations about the suitablllty or this software for any purpose. It is provided "as ls" without express or Implied warranty. - ii - CREDITS The PC/IP packages are bullt on the work of many people in the TCP/IP community, both at M.I.T. and elsewhere. Following are some of the people who directly helped in the creation of the packages. Network environment-John L. Romkey Terminal emulator and customizer-David A. Bridgham Inltlal TFTP-Kari D. Wright Inltlal telnet-Louls J. Konopelskl Teinet model-David D. Clark Tasking package-Larry W. Allen Development system-Christopher J. Terman Development environment-Wayne C. Gramlich Administrative Assistant-Muriel Webber October 3, 1985. This document is in cover .mss - iii- - iv Table of Contents 1. Overview of PC/IP network programs 1 1.1. -

List of TCP and UDP Port Numbers from Wikipedia, the Free Encyclopedia
List of TCP and UDP port numbers From Wikipedia, the free encyclopedia This is a list of Internet socket port numbers used by protocols of the transport layer of the Internet Protocol Suite for the establishment of host-to-host connectivity. Originally, port numbers were used by the Network Control Program (NCP) in the ARPANET for which two ports were required for half- duplex transmission. Later, the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP) needed only one port for full- duplex, bidirectional traffic. The even-numbered ports were not used, and this resulted in some even numbers in the well-known port number /etc/services, a service name range being unassigned. The Stream Control Transmission Protocol database file on Unix-like operating (SCTP) and the Datagram Congestion Control Protocol (DCCP) also systems.[1][2][3][4] use port numbers. They usually use port numbers that match the services of the corresponding TCP or UDP implementation, if they exist. The Internet Assigned Numbers Authority (IANA) is responsible for maintaining the official assignments of port numbers for specific uses.[5] However, many unofficial uses of both well-known and registered port numbers occur in practice. Contents 1 Table legend 2 Well-known ports 3 Registered ports 4 Dynamic, private or ephemeral ports 5 See also 6 References 7 External links Table legend Official: Port is registered with IANA for the application.[5] Unofficial: Port is not registered with IANA for the application. Multiple use: Multiple applications are known to use this port. Well-known ports The port numbers in the range from 0 to 1023 are the well-known ports or system ports.[6] They are used by system processes that provide widely used types of network services. -

TCP/IP Explained
TCP/IP Explained PHILIP MILLER DIGITAL PRESS Boston Oxford Johannesburg Melbourne New Delhi Singapore Table of Contents Preface xvii Chapter 1 - Introduction 1 1.1 What is TCP/IP? 1 1.1.1 A Brief History of TCP/IP 2 1.1.2 The Internet Protocol Suite 3 1.2 The Internet 5 1.2.1 The Growth of the Internet 6 1.3 Summary 9 Chapter 2 - Standardization 11 2.1 The Internet Architecture Board 11 2.1.1 The Internet Engineering Task Force 12 2.1.2 The Internet Research Task Force 13 2.2 Internet Protocol Standards 13 2.2.1 Protocol States 14 2.2.2 Protocol Status 16 2.2.3 The Request For Comments (RFC) 16 2.3 Internet Protocol Architecture 17 2.3.1 The Open Systems Interconnection (OSI) Model 18 2.3.2 The OSI Model and LANs 20 2.3.3 The Internet Protocol Suite Model 23 2.4 A Comparison of Major Architectures 25 2.5 Summary 26 Chapter 3 - An Overview of Network Technologies and Relay Systems 27 3.1 Ethernet and IEEE 802.3 27 3.1.1 802.3 Specifications 27 3.1.2 Ethernet/802.3 Frame Structure 30 3.1.3 Ethernet/802.3 Operation 32 3.2 Token Ring 33 3.2.1 802.5 Specifications 34 3.2.2 802.5 Frame Structure 36 3.2.3 802.5 Operation 38 3.3 Fibre Distributed Data Interface (FDDI) 39 3.3.1 FDDI Specifications 41 3.3.2 FDDI Frame Structure 42 3.3.3 FDDI Operation 43 3.4 Relay Systems 43 3.4.1 Repeaters 44 3.4.2 Bridges 45 3.5 WAN Links 50 3.6 Summary 51 Chapter 4 - Internet Addressing 53 4.1 The Need for an Addressing Scheme 53 4.2 Internet Addressing 54 4.2.1 Dotted Decimal Notation 55 4.2.2 Identifying IP Addresses and Rules 56 4.2.3 Choosing the Right Addressing -

Network Working Group J. Postel Request for Comments: 840 ISI April 1983
Network Working Group J. Postel Request for Comments: 840 ISI April 1983 Official Protocols This RFC identifies the documents specifying the official protocols used in the Internet. Annotations identify any revisions or changes planned. To first order, the official protocols are those in the Internet Protocol Transition Workbook (IPTW) dated March 1982. There are several protocols in use that are not in the IPTW. A few of the protocols in the IPTW have been revised these are noted here. In particular, the mail protocols have been revised and issued as a volume titled "Internet Mail Protocols" dated November 1982. There is a volume of protocol related information called the Internet Protocol Implementers Guide (IPIG) dated August 1982. A few of the protocols (in particular the Telnet Options) have not been revised for many years, these are found in the old ARPANET Protocol Handbook (APH) dated January 1978. This document is organized as a sketchy outline. The entries are protocols (e.g., Transmission Control Protocol). In each entry there are notes on status, specification, comments, other references, dependencies, and contact. The status is one of: required, recommended, elective, or experimental. The specification identifies the protocol defining documents. The comments describe any differences from the specification or problems with the protocol. The other references identify documents that comment on or expand on the protocol. The dependencies indicate what other protocols are called upon by this protocol. The contact indicates a person -

ECHO Through EXEC
ECHO through EXEC • ECHO, page 3 • EDONKEY-STATIC, page 4 • EDONKEY, page 5 • EGP, page 6 • EIGRP, page 7 • ELCSD, page 8 • EMBL-NDT, page 9 • EMCON, page 10 • EMFIS-CNTL, page 11 • EMFIS-DATA, page 12 • ENCAP, page 13 • ENCRYPTED-BITTORRENT, page 14 • ENCRYPTED-EMULE, page 15 • ENTOMB, page 16 • ENTRUST-AAAS, page 17 • ENTRUST-AAMS, page 18 • ENTRUST-ASH, page 19 • ENTRUST-KMSH, page 20 • ENTRUST-SPS, page 21 • EPMAP, page 22 • ERPC, page 23 • ESCP-IP, page 24 • ESIGNAL, page 25 • ESPN-BROWSING, page 26 NBAR2 Protocol Pack 7.0.0 1 ECHO through EXEC • ESPN-VIDEO, page 27 • ESRO-EMSDP, page 28 • ESRO-GEN, page 29 • ETHERIP, page 30 • EUDORA-SET, page 31 • EXCHANGE, page 32 • EXEC, page 33 NBAR2 Protocol Pack 7.0.0 2 ECHO through EXEC ECHO ECHO Name/CLI Keyword echo Full Name Echo Protocol Description Echo is a protocol that is used for debugging and measurement. It works by sending back all the data that was received from the source. The protocol works on TCP and UDP, typically on port 7. Reference http://www.faqs.org/rfcs/rfc862.html Global ID L4:7 ID 101 Known Mappings UDP Port 7 TCP Port 7 IP Protocol - IP Version IPv4 Support Yes IPv6 Support Yes Application Group other Category net-admin Sub Category network-management P2P Technology No Encrypted No Tunnel No Underlying Protocols - NBAR2 Protocol Pack 7.0.0 3 ECHO through EXEC EDONKEY-STATIC EDONKEY-STATIC Name/CLI Keyword edonkey-static Full Name eDonkey Description eDonkey is peer-to-peer file sharing adopted to share large files. -

VPN Ipsec Tunnels with Cisco ASA/Asav VTI on Oracle Cloud Infrastructure
Deploying VPN IPSec Tunnels with Cisco ASA/ASAv VTI on Oracle Cloud Infrastructure O R A C L E SOLUTION GUIDE | M A R C H 2 0 1 8 | VERSION 1.1 Table of Contents Overview 4 Scope and Assumptions 4 VPN IPSec Tunnel Concepts 5 CPE Configuration 5 General Requirements for Connecting to the Oracle Cloud Infrastructure DRG via IPSec 6 Establish the IKE Security Association Using Pre-Shared Keys 6 Establish the IPSec Security Association 6 Use AES 256-Bit Encryption 6 Use the SHA-1 or SHA-256 Hashing Function 6 Use Diffie-Hellman with Perfect Forward Secrecy 7 IPSec Dead Peer Detection 7 Bind Tunnel to Logical Interface (Route-Based VPN) 7 Fragment IP Packets Before Encryption 8 Recommendations for TCP Maximum Segment Size and DF Flags 8 Data Lifetime Rekey Interval 9 VPN IPSec Tunnels on Oracle Cloud Infrastructure 9 Key Components of VPN IPSec Tunnels on OCI 10 Access Requirements for VPN IPSec Tunnels Configuration 13 Configure the VPN IPSec 14 Step 1: Create a VCN 15 Step 2: Create the DRG 16 Step 3: Attach the DRG to the VCN 17 Step 4: Modify the Default Route Table for the VCN 17 Step 6: Edit the Default Security List for the Subnet 18 2 | DEPLOYING VPN IPSEC TUNNELS WITH CISCO ASA/ASAV VTI ON ORACLE CLOUD INFRASTRUCTURE Step 7: Create a Subnet 19 Step 8: Create a CPE Object 21 Step 9: Create an IPSec Tunnel Between the DRG and CPE 22 Step 10: Verify the IPSec Tunnels 23 Summary 24 Configure the ASA/ASAv On-Premises Device 25 Step 1: Note All the Values Used in the ASA/ASAv Configuration 25 Step 2: Configure the IKE and IPSec Policy and IPSec Profile 26 Step 3: Set Up Some IPSec and Tunnel Friendly Parameters 27 Step 4: Configure the Tunnel Group 28 Step 5: Configure the VTI 28 Step 6: Configure the Static Routes 29 Step 7: Verify That the Tunnels Are Up on Oracle Cloud Infrastructure 31 Sample ASA/ASAv Configuration File from this Document 31 Conclusion 33 3 | DEPLOYING VPN IPSEC TUNNELS WITH CISCO ASA/ASAV VTI ON ORACLE CLOUD INFRASTRUCTURE Overview This guide provides step-by-step instructions for configuring VPN IPSec tunnels on Oracle Cloud Infrastructure. -
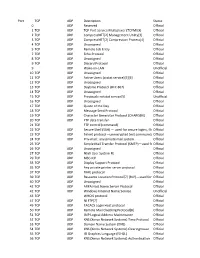
Official 2 TCP UDP Compr
Port TCP UDP Description Status 0 UDP Reserved Official 1 TCP UDP TCP Port Service Multiplexer (TCPMUX) Official 2 TCP UDP CompressNET[2] Management Utility[3] Official 3 TCP UDP CompressNET[2] Compression Process[4] Official 4 TCP UDP Unassigned Official 5 TCP UDP Remote Job Entry Official 7 TCP UDP Echo Protocol Official 8 TCP UDP Unassigned Official 9 TCP UDP Discard Protocol Official 9 UDP Wake-on-LAN Unofficial 10 TCP UDP Unassigned Official 11 TCP UDP Active Users (systat service)[5][6] Official 12 TCP UDP Unassigned Official 13 TCP UDP Daytime Protocol (RFC 867) Official 14 TCP UDP Unassigned Official 15 TCP UDP Previously netstat service[5] Unofficial 16 TCP UDP Unassigned Official 17 TCP UDP Quote of the Day Official 18 TCP UDP Message Send Protocol Official 19 TCP UDP Character Generator Protocol (CHARGEN) Official 20 TCP UDP FTP data transfer Official 21 TCP FTP control (command) Official 22 TCP UDP Secure Shell (SSH) — used for secure logins, file Officialtransfers (scp, sftp) and port forwarding 23 TCP UDP Telnet protocol—unencrypted text communicationsOfficial 24 TCP UDP Priv-mail : any private mail system. Official 25 TCP Simple Mail Transfer Protocol (SMTP)—used forOfficial e-mail routing between mail servers 26 TCP UDP Unassigned Official 27 TCP UDP NSW User System FE Official 29 TCP UDP MSG ICP Official 33 TCP UDP Display Support Protocol Official 35 TCP UDP Any private printer server protocol Official 37 TCP UDP TIME protocol Official 39 TCP UDP Resource Location Protocol*7+ (RLP)—used for determiningOfficial the location -

The Definitive Guide to HTML5 Websocket // Example Websocket Server
For your convenience Apress has placed some of the front matter material after the index. Please use the Bookmarks and Contents at a Glance links to access them. Contents at a Glance Foreword ���������������������������������������������������������������������������������������� xiii About the Authors ���������������������������������������������������������������������������� xv About the Technical Reviewer ������������������������������������������������������� xvii Acknowledgments �������������������������������������������������������������������������� xix ■ Chapter 1: Introduction to HTML5 WebSocket �������������������������������� 1 ■ Chapter 2: The WebSocket API ����������������������������������������������������� 13 ■ Chapter 3: The WebSocket Protocol ��������������������������������������������� 33 ■ Chapter 4: Building Instant Messaging and Chat over WebSocket with XMPP ��������������������������������������������������������� 61 ■ Chapter 5: Using Messaging over WebSocket with STOMP ���������� 85 ■ Chapter 6: VNC with the Remote Framebuffer Protocol ������������� 109 ■ Chapter 7: WebSocket Security �������������������������������������������������� 129 ■ Chapter 8: Deployment Considerations �������������������������������������� 149 ■ Appendix A: Inspecting WebSocket Traffic ��������������������������������� 163 ■ Appendix B: WebSocket Resources �������������������������������������������� 177 Index ���������������������������������������������������������������������������������������������� 183 v CHAPTER 1 Introduction -

Scalable Remote Measurement of Application-Layer Censorship
Quack: Scalable Remote Measurement of Application-Layer Censorship Benjamin VanderSloot, Allison McDonald, Will Scott, J. Alex Halderman, and Roya Ensafi University of Michigan {benvds, amcdon, willscott, jhalderm, ensafi}@umich.edu Abstract under repressive or secretive government controls, coop- erating with security researchers has substantial risks. Remote censorship measurement tools can now detect An emerging body of work addresses these problems DNS- and IP-based blocking at global scale. However, by using existing protocols and infrastructure to remotely a major unmonitored form of interference is blocking measure network interference. Such approaches have triggered by deep packet inspection of application-layer been effective in measuring DNS poisoning [35,41] and data. We close this gap by introducing Quack, a scalable, for detecting interference in TCP/IP-connectivity between remote measurement system that can efficiently detect remote machines [17,34]. There has not yet been a global, application-layer interference. remote method for detecting another broadly deployed We show that Quack can effectively detect application- censorship technique: application-layer censorship. layer blocking triggered on HTTP and TLS headers, and Application-layer censorship has become increasingly it is flexible enough to support many other diverse pro- important with the rise of content delivery networks tocols. In experiments, we test for blocking across 4458 (CDNs). CDNs use a small number of network entry- autonomous systems, an order of magnitude larger than points for a large number of customers, resulting in siz- provided by country probes used by OONI over a one able collateral damage to IP-based blocking techniques. week span. We also test a corpus of 100,000 keywords When an adversary wishes to block some, but not all, of from vantage points in 40 countries to produce detailed these sites, they must look into the content of requests national blocklists. -

Configuring IP Slas UDP Echo Operations
Configuring IP SLAs UDP Echo Operations This module describes how to configure an IP Service Level Agreements (SLAs) User Datagram Protocol (UDP) Echo operation to monitor end-to-end response time between a Cisco device and devices using IPv4 or IPv6. UDP echo accuracy is enhanced by using the Cisco IP SLAs Responder at the destination Cisco device. This module also demonstrates how the results of the UDP echo operation can be displayed and analyzed to determine how a UDP application is performing. • Finding Feature Information, page 1 • Restrictions for IP SLAs UDP Echo Operations, page 1 • Information About IP SLAs UDP Echo Operations, page 2 • How to Configure IP SLAs UDP Echo Operations, page 3 • Configuration Examples for IP SLAs UDP Echo Operations, page 12 • Additional References, page 12 • Feature Information for the IP SLAs UDP Echo Operation, page 13 Finding Feature Information Your software release may not support all the features documented in this module. For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the feature information table. Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required. Restrictions for IP SLAs UDP Echo Operations We recommend using a Cisco networking device as the destination device, although any networking device that supports RFC 862, Echo Protocol , can be used. -

Etc/Services
# /etc/services: # $Id: services,v 1.48 2009/11/11 14:32:31 ovasik Exp $ # # Network services, Internet style # IANA services version: last updated 2009-11-10 # # Note that it is presently the policy of IANA to assign a single well-known # port number for both TCP and UDP; hence, most entries here have two entries # even if the protocol doesn't support UDP operations. # Updated from RFC 1700, ``Assigned Numbers'' (October 1994). Not all ports # are included, only the more common ones. # # The latest IANA port assignments can be gotten from # http://www.iana.org/assignments/port-numbers # The Well Known Ports are those from 0 through 1023. # The Registered Ports are those from 1024 through 49151 # The Dynamic and/or Private Ports are those from 49152 through 65535 # # Each line describes one service, and is of the form: # # service-name port/protocol [aliases ...] [# comment] tcpmux 1/tcp # TCP port service multiplexer tcpmux 1/udp # TCP port service multiplexer rje 5/tcp # Remote Job Entry rje 5/udp # Remote Job Entry echo 7/tcp echo 7/udp discard 9/tcp sink null discard 9/udp sink null systat 11/tcp users systat 11/udp users daytime 13/tcp daytime 13/udp qotd 17/tcp quote qotd 17/udp quote msp 18/tcp # message send protocol msp 18/udp # message send protocol chargen 19/tcp ttytst source chargen 19/udp ttytst source ftp-data 20/tcp ftp-data 20/udp # 21 is registered to ftp, but also used by fsp ftp 21/tcp ftp 21/udp fsp fspd ssh 22/tcp # The Secure Shell (SSH) Protocol ssh 22/udp # The Secure Shell (SSH) Protocol telnet 23/tcp telnet 23/udp