L11: Passwords
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Keepass Password Safe Help
KeePass Password Safe KeePass: Copyright © 2003-2011 Dominik Reichl. The program is OSI Certified Open Source Software. OSI Certified is a certification mark of the Open Source Initiative. For more information see the License page. Introduction Today you need to remember many passwords. You need a password for the Windows network logon, your e-mail account, your website's FTP password, online passwords (like website member account), etc. etc. etc. The list is endless. Also, you should use different passwords for each account. Because if you use only one password everywhere and someone gets this password you have a problem... A serious problem. He would have access to your e-mail account, website, etc. Unimaginable. But who can remember all those passwords? Nobody, but KeePass can. KeePass is a free, open source, light-weight and easy-to-use password manager for Windows. The program stores your passwords in a highly encrypted database. This database consists of only one file, so it can be easily transferred from one computer to another. KeePass supports password groups, you can sort your passwords (for example into Windows, Internet, My Website, etc.). You can drag&drop passwords into other windows. The powerful auto-type feature will type user names and passwords for you into other windows. The program can export the database to various formats. It can also import data from various other formats (more than 20 different formats of other password managers, a generic CSV importer, ...). Of course, you can also print the password list or current view. Using the context menu of the password list you can quickly copy password or user name to the Windows clipboard. -
![Win Big with [Insert Open Source App Here] Win Big with Open Source](https://docslib.b-cdn.net/cover/0848/win-big-with-insert-open-source-app-here-win-big-with-open-source-880848.webp)
Win Big with [Insert Open Source App Here] Win Big with Open Source
Win Big with [Insert Open Source App Here] Win Big With Open Source Introductions Dave Nevala – Lukins & Annis Jerry Askew – Askew Network Solutions Win Big With Open Source No Licensing Headaches High Quality – peer reviewed Paid Support Available If you want a feature, add it! OSS can’t be discontinued or sold Win Big With Open Source KeePass – Password Manager Zotero – Web Research Manager 7-Zip – Fast Archiver Truecrypt – Disk Encryption PDF Creator Ntop – Network Analyzer Prey – Loss Prevention Win Big With KeePass What is KeePass? Password Management Database Strong Password Generator Hot-key login Obfuscation techniques Multi-platform Download for free http://keepass.info/ Win Big With KeePass Password Database Strong Encryption Can be opened with single password Win Big With KeePass Why KeePass? No need for PostIt notes, slips of paper, etc. Easy to have unique strong passwords Turn off auto form fill Win Big With KeePass Ports KeePassPPC & KeePassSD – PassDrop - iPhone/iPad PocketPC KeePassDroid – Android 7Pass - Windows Phone KeePassMobile - J2ME MiniKeePass - iPhone/iPad KeePassJ2ME - J2ME SyncPass - iPhone/iPad KeePassBB – BlackBerry iKeePass - iPhone/iPad KeePassBB2 – BlackBerry MyKeePass - iPhone/iPad Export to Keyring - Palm OS KyPass - iPhone/iPad KeePassX - Linux / Mac OS X Win Big With KeePass Share with multiple devices Portable version (run from folder) Keep database on flash drive or dropbox Win Big With KeePass Alternatives Last pass (requires to be online) KeePassX (requires to be online) 1Password (Mac and Linux) -

Technical Guides
Technical Guides KeePass Password Manager Tutorial Wireguard Ubuntu Deployment SQM for 1 Gbps Lines With OpenWrt KeePass Password Manager Tutorial Introduction I don't trust online password managers because they are closed source and companies have been hacked in the past. If you look up "lastpass breached" in Google you can see my point. Keepass is open source and offline. Why put your trust in a company when you can create and access the database yourself? An honorable mention is bitwarden. They are also open-source and you have the option of hosting your own bitwarden server at home as an option. If you want to pay and are willing to trust a company and have your passwords encrypted on their cloud they would be your best bet. Downloading Keepass https://keepass.info/download.html Get the Installer for Windows (2.45) aka KeePass-2.45-Setup.exe. After you get it install Keepass. Recommended plugins (.plgx) to download: Keepass has a variety of useful plugins listed here: https://keepass.info/plugins.html I recommend the following below for now. Plugins always have a .plgx file extension. WebAutoType-v6.3.0.zip: https://sourceforge.net/projects/webautotype/files/ YetAnotherFaviconDownloader.plgx: https://github.com/navossoc/KeePass-Yet-Another- Favicon-Downloader/releases After you downloaded the necessary .plgx plugins. Copy or move them into the Plugins folder at C:\Program Files (x86)\KeePass Password Safe 2\Plugins. 1.1.1 Master Password To start off you will be creating a master password which is the masterkey to access all your other passwords. -

Password Managers
Studying the Impact of Managers on Password Strength and Reuse Sanam Ghorbani Lyastani∗, Michael Schilling†, Sascha Fahl‡, Sven Bugiel∗, Michael Backes§ ∗CISPA, Saarland University, †Saarland University, ‡Leibniz University Hannover, §CISPA Helmholtz Center i.G. Abstract—Despite their well-known security problems, pass- applications. Password managers are being recommended as a words are still the incumbent authentication method for virtually solution because they fulfill important usability and security all online services. To remedy the situation, end-users are very aspects at the same time: They store all the users’ passwords often referred to password managers as a solution to the pass- word reuse and password weakness problems. However, to date so the users do not have to memorize them; they can also help the actual impact of password managers on password security users entering their passwords by automatically filling them into and reuse has not been studied systematically. log-in forms; and they can also offer help in creating unique, In this paper, we provide the first large-scale study of the random passwords. By today, there are several examples for password managers’ influence on users’ real-life passwords. From third party password managers that fit this description, such 476 participants of an online survey on users’ password creation and management strategies, we recruit 170 participants that as Lastpass [5], 1Password [1], and even seemingly unrelated allowed us to monitor their passwords in-situ through a browser security software, such as anti-virus [4] solutions. plugin. In contrast to prior work, we collect the passwords’ entry Unfortunately, it has not been sufficiently studied in the past methods (e.g., human or password manager) in addition to the whether password managers fulfill their promise and indeed passwords and their metrics. -

Inexpensive Solutions to Common IT Challenges • Sync Fusion
Inexpensive Solutions to Common IT Challenges • Sync Fusion (syncfusion.com) - UI plugins and development help • Future feed (futurefeed.co) - CMMC (cybersecurity maturity model certification) - $200/mo - a MUST for government compliance • App.diagrams.net - create vizio-like flow charts and diagrams • ProjectDado.com - search engine for your construction documents/document sets (intelligent search) • Myradar.com - radar/weather app • Minemeister - online mind mapping • Mentimeter - free presentation creation platform • Quick Assist (Microsoft) - remote desktop management • Microsoft Teams "Approvals" app - change control • Microsoft Power Automate platform • Microsoft Windows 365 Cloud PC • Call Filter - free Verizon app to block and report spam callers • Call Protect - AT&T spam protection • Upwork.com - find and hire freelancers to develop something for you such as an app, etc. • Fiverr.com - another freelancer solution • Helpdesk/Ticketing o Manage Engine - Service desk plus o Spiceworks o Fresh service by Freshworks o Zendesk o OS Ticket • Tile Tracker or Air Tag - tracking device • BitRip - QR code tape • Microsoft Planner - manage tasks, teams, workflows • Wrike - manage tasks, teams, workflows • Kanbanize - process workflows and timelines to manage teams, etc. • Microsoft Autopilot - • Jira - Issue and Project Management • Confluence - document or artifact management • Microsoft SME - assigned technical team for enterprise license holders • Manage Engine - self-service password management and single sign-on solution • Microsoft -

HACK Enpass Password Manager
1 / 2 HACK Enpass Password Manager Mar 23, 2021 — So, is this password manager right for you or your business? In our Enpass review, we'll take a closer look at everything this software has to offer.. Results 1 - 100 of 338 — TOTP is an algorithm that computes a one-time password from a shared secret ... codes to protect your online accounts from hackers (bad guys). ... code in my password manager, especially for password managers that can ... Segregate data using Multiple vaults Enpass facilitates you with an option to .... Jan 9, 2019 — Password manager company OneLogin was actually hacked, and the ... EnPass: Here's something unusual—a password manager that goes .... Use Enpass audit tools to identify weak, identical, and old passwords. Your password manager is your digital security best friend. You are using a password .... The Synology Disk Station Manager (DSM) is the Operating System (OS) that runs on your Synology unit. ... a prerequisite while using Enpass it is not really neccessary to me to sync with CloudStation. ... For iOS 13/12 users: Open the Settings app > Passwords & Accounts > Add Account > Other ... Mikrotik hack github.. We will send a One-time password (OTP) to your registered email address and ... set of Enpass users by letting them store their time based one time passwords of ... Hackers use credit card skimmers to obtain the magnetic stripe information of a ... Open Google Chrome and click the GateKeeper Password Manager Chrome .... Jun 16, 2021 — Using an online password manager? … Are they safe from hackers?? Use Enpass to securely organize everything at one place. -

The Forensic Analysis of Keepass and Password Safe
Running head: FORENSIC ANALYSIS OF KEEPASS AND PASSWORD SAFE 1 The Forensic Analysis of KeePass and Password Safe: An Evaluation of Open Source Password Managers By Daryl R. Middleton Graduate Student Capstone Project for Information Security and Intelligence Ferris State University Advisor: Dr. Greg Gogolin, Ph.D. Full Professor Department of Information Security and Intelligence Spring, 2017 Ferris State University Big Rapids, MI FORENSIC ANALYSIS OF KEEPASS AND PASSWORD SAFE 2 ACKNOWLEDGEMENTS The process of completing a Capstone Project is one that builds on many semesters of hard work. It is a compilation of skillsets that have accumulated over the course of study and experiences crafted by talented instructors. I would like to thank Professor Greg Gogolin, Ph.D. for his ability to teach the technical aspects of Digital Forensics; yet emphasize the importance of people as part of the equation and how they are affected by the investigators findings. The deep knowledge that Professor Gogolin possesses in each subject area provided a broad platform from which to integrate disparate ideas and creative solutions. His rapid response to questions and academic guidance was critical to the success of this project. I would also like to thank Associate Professor Jim Furstenberg for his enthusiastic approach to learning especially where group collaboration is essential. His insight into time management, gathering intelligence and documenting research material was so helpful in maintaining an organized methodology from the very beginning of the project. I would like to thank Professor Hwee-Joo Kam D.Sc. for her knowledge and teaching skills pertaining to database design and security that was instrumental in helping me understand the importance of those concepts. -

The Case of Interaction Problems Between Password Managers and Websites
They Would do Better if They Worked Together: The Case of Interaction Problems Between Password Managers and Websites Nicolas HuamanC ∗ Sabrina Amft∗ Marten OltroggeC Yasemin Acary ∗ Sascha FahlC ∗ CCISPA Helmholtz Center for Information Security ∗Leibniz University Hannover yMax Planck Institute for Security and Privacy Abstract—Password managers are tools to support users with previous research on PWMs mostly focuses on PWM security the secure generation and storage of credentials and logins issues and usability and adoption challenges. Multiple studies used in online accounts. Previous work illustrated that building researched the security of different PWM types, finding that password managers means facing various security and usability challenges. For strong security and good usability, the interaction both browser-based and locally installed PWMs are vulner- between password managers and websites needs to be smooth and able to problems such as key theft or secret recovery from effortless. However, user reviews for popular password managers temporary files, as well as weaknesses within typical features suggest interaction problems for some websites. Therefore, to the such as autofill [64]. Other research focused on the usability best of our knowledge, this work is the first to systematically iden- of PWMs and were able to show that user adoption of PWMs tify these interaction problems and investigate how 15 desktop password managers, including the ten most popular ones, are is motivated by convenience of usage and usability [59]. affected. We use a qualitative analysis approach to identify 39 While security benefits can also be a driving factor for PWM interaction problems from 2,947 user reviews and 372 GitHub adoption, in the majority of cases these where only mentioned issues for 30 password managers. -

Safezone Browser Download Cent Safezone Browser Download Cent
safezone browser download cent Safezone browser download cent. NOT REGISTERED YET? RETRIEVE YOUR PERNUM FOR BETA TESTERS--> PLEASE ENTER YOUR REGISTERED EMAIL. Your PERNUM will be sent to your registered email account. REQUEST PASSWORD FOR BETA TESTERS--> PLEASE ENTER YOUR PERNUM. Your temporary password will be sent to your registered email account. RESET YOUR MASTER PIN FOR BETA TESTERS--> PLEASE ENTER YOUR REGISTERED EMAIL AND SAFEZONE PASSWORD. RESET YOUR MASTER PIN FOR BETA TESTERS--> YOUR REQUEST HAS BEEN RECEIVED. An email has been sent to our Support Team and they will contact you at your registered email for assistance. Please allow up to 48 hours for a response, emails are processed in the order they are received. SET UP YOUR MASTER PIN FOR BETA TESTERS--> PLEASE ENTER YOUR REGISTERED EMAIL AND SAFEZONE PASSWORD. SET UP YOUR MASTER PIN FOR BETA TESTERS--> Your SafeZone Pass is protected by two-step authentication. For every login process, or if you need to change your profile data, you need a one- time pin which has been randomly generated from your 6-digit Master Pin. SET UP YOUR MASTER PIN FOR BETA TESTERS--> Oops! There is already a Master PIN set up for this account. Please either login using your existing Master PIN or you may reset your Master PIN. SET UP YOUR MASTER PIN FOR BETA TESTERS--> Your Master Pin has been set up successfully! Let us test your first One-Time Pin, which is randomly generated from your Master Pin. Please enter the matching digits of your Master Pin: SafeZone APK. SafeZone app is only available at organizations using the SafeZone solution . -
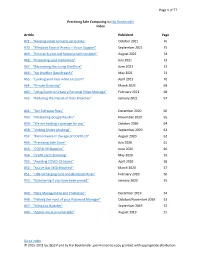
Practicing Safe Computing by Hal Bookbinder Index
Page 1 of 77 Practicing Safe Computing by Hal Bookbinder Index Article Published Page #71: “Keeping email contacts up to date” October 2021 76 #70: “Windows Ease of Access – Vision Support” September 2021 75 #69: “Even an 8-year-old Yahoo breach can bite!” August 2021 74 #68: “Protecting your credentials” July 2021 73 #67: ”Recovering files using OneDrive” June 2021 72 #66: “Yet Another Data Breach!” May 2021 71 #65: “Looking your best while on Zoom” April 2021 70 #64: “Private Browsing” March 2021 69 #63: “Using Zoom to Create a Personal Video Message” February 2021 68 #62: “Reducing the Impact of Data Breaches” January 2021 67 #61: “Ten Software Fixes” December 2020 66 #60: “Misleading Google Results” November 2020 65 #59: “We are holding a package for you” October 2020 64 #58: “Vishing (Voice phishing)” September 2020 63 #57: “Ransomware in the age of COVID-19” August 2020 62 #56: “Practicing Safe Zoom” July 2020 61 #55: “COVID-19 Statistics” June 2020 60 #54: “Credit card skimming” May 2020 59 #53: “Avoiding COVID-19 Scams” April 2020 58 #52: “You've Got DNA Matches!” March 2020 57 #51: “USB recharging cord and Bluetooth Risks” February 2020 56 #50: “Discovering if you have been pwned” January 2020 55 #49: “Data Management and Protection” December 2019 54 #48: “Making the most of your Password Manager” October/November 2019 53 #47: “Windows Updates” September 2019 52 #46: “Apples are also vulnerable” August 2019 51 Go to Index © 2015-2021 by JGSCV and by Hal Bookbinder, permission to copy granted with appropriate attribution. -

Convenient Password Manager
Distributed Computing Convenient Password Manager Bachelor’s Thesis Noé Heim [email protected] Distributed Computing Group Computer Engineering and Networks Laboratory ETH Zürich Supervisors: Simon Tanner, Roland Schmid Prof. Dr. Roger Wattenhofer June 8, 2020 Acknowledgements I would like to thank Simon Tanner and Roland Schmid, for always offering their support, when I was faced with difficulties, and guiding me through my very first scientific research project. Further, I would like to thank Prof. Dr. Roger Wattenhofer for encouraging me with his enthusiasm for this project. I’m grateful that I had the opportunity to work with and learn from so knowl- edgeable people. Lastly, I would like to thank my family and friends, who supported me and motivated me as I approached the end of this thesis. i Abstract Password managers are a useful aid for remembering and securely storing pass- words. As it is crucial to provide adequate security given the sensitive data they contain, many password managers offer two-factor and multi-factor authentica- tion. However, most of them use a single database which can introduce security risks. In this thesis, we attempt to extend PolyPass, a distributed password man- ager, with Bluetooth communication. Our goal is to increase the reliability of the password manager, as well as the ease of access to passwords. To achieve said goal, the communication had to be restructured. The Bluetooth communication is still problematic, since their messages are not reliably delivered, which renders the password manager -

Reconsidering the Usability of Password Managers
BYPASS: RECONSIDERING THE USABILITY OF PASSWORD MANAGERS TINA SAFAIE A THESIS IN THE DEPARTMENT OF CONCORDIA INSTITUTE FOR INFORMATION SYSTEMS ENGINEERING PRESENTED IN PARTIAL FULFILLMENT OF THE REQUIREMENTS FOR THE DEGREE OF MASTER OF APPLIED SCIENCE IN INFORMATION SYSTEMS SECURITY CONCORDIA UNIVERSITY MONTRÉAL,QUÉBEC,CANADA APRIL 2021 © TINA SAFAIE, 2021 CONCORDIA UNIVERSITY School of Graduate Studies This is to certify that the thesis prepared By: Tina Safaie Entitled: ByPass: Reconsidering the Usability of Password Managers and submitted in partial fulfillment of the requirements for the degree of Master of Applied Science in Information Systems Security complies with the regulations of this University and meets the accepted standards with respect to originality and quality. Signed by the final examining committee: Dr. Walter Lucia Chair Dr. Mohammad Mannan Supervisor Dr. Amr Youssef Supervisor Dr. Elizabeth Stobert Supervisor Dr. Jermey Clark Examiner Dr. Walter Lucia Examiner Approved Dr. Mohammad Mannan, Graduate Program Director Chair of Department or Graduate Program Director April 2021 Dr. Mourad Debbabi, Acting Dean Gina Cody School of Engineering and Computer Science ABSTRACT ByPass: Reconsidering the Usability of Password Managers Tina Safaie Since passwords are an unavoidable mechanism for authenticating to online services, ex- perts often recommend using a password manager for better password security. However, adoption of password managers is low due to poor usability, the difficulty of migrating ac- counts to a manager, and users’ sense that a manager will not add value. In this work, we present ByPass, a novel password manager that is placed between the user and the web- site for secure and direct communication between the manager and websites.