Beating the Americans at Their Own Game an Offset Strategy with Chinese Characteristics
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Step Off the Road, and Let the Dead Pass By
191 Step Off the Road, and Let the Dead Pass By Le ceremony of paying homage to our honored need for a special memorial day, except as such an dead has been held annually on the Sunday closest to occasion is used to strengthen us in our resolves to September 29, the day that the lOOth Infantry Battalion live in a manner worthy of the dead, and as such an first entered combat in Italy in 1943 and suffered its first occasion serves to remind the world around us of the casualties. Through the years, we have been blessed with splendid achievements of the Americans of Japanese the eloquence of many distinguished speakers at these ancestry. annual memorial services, but rarely has the evocative All of us here present have reason to be thank power of speech so captured our souls as the address ful for what our dead have done. Because of such given by Israel Yost, our frontline chaplain, at the 1947 soldiers the war was kept away from America; service. That speech is reproduced below. because of these men our homes were not invaded, nor our loved ones endangered, nor our property Comrades and friends and parents: destroyed. We who were over there have seen what I regret that I am not able to address you war does to a country; because of the courage of our parents of our fallen comrades in the language with comrades, even unto death, we at home have been which you are most familiar. If I could I would glad spared such ravages of war. -

Chapter 7 Interact with History
The port of New Orleans, Louisiana, a major center for the cotton trade 1820 James Monroe is 1817 reelected president. 1824 John Construction 1819 U.S. Quincy Adams begins on the acquires Florida 1820 Congress agrees to is elected Erie Canal. from Spain. the Missouri Compromise. president. USA 1815 WORLD 1815 1820 1825 1815 Napoleon 1819 Simón 1822 Freed 1824 is defeated at Bolívar becomes U.S. slaves Mexico Waterloo. president of found Liberia on becomes Colombia. the west coast a republic. of Africa. 210 CHAPTER 7 INTERACT WITH HISTORY The year is 1828. You are a senator from a Southern state. Congress has just passed a high tax on imported cloth and iron in order to protect Northern industry. The tax will raise the cost of these goods in the South and will cause Britain to buy less cotton. Southern states hope to nullify, or cancel, such federal laws that they consider unfair. Would you support the federal or state government? Examine the Issues • What might happen if some states enforce laws and others don't? • How can Congress address the needs of different states? •What does it mean to be a nation? RESEARCH LINKS CLASSZONE.COM Visit the Chapter 7 links for more information about Balancing Nationalism and Sectionalism. 1838 1828 Removal of Andrew 1836 Martin the Cherokee 1840 William Jackson 1832 Andrew Van Buren along the Henry Harrison is elected Jackson is elected Trail of Tears is elected president. is reelected. president. begins. president. 1830 1835 1840 1830 France 1833 British 1837 Victoria 1839 Opium invades Algeria. -

Mtv and Transatlantic Cold War Music Videos
102 MTV AND TRANSATLANTIC COLD WAR MUSIC VIDEOS WILLIAM M. KNOBLAUCH INTRODUCTION In 1986 Music Television (MTV) premiered “Peace Sells”, the latest video from American metal band Megadeth. In many ways, “Peace Sells” was a standard pro- motional video, full of lip-synching and head-banging. Yet the “Peace Sells” video had political overtones. It featured footage of protestors and police in riot gear; at one point, the camera draws back to reveal a teenager watching “Peace Sells” on MTV. His father enters the room, grabs the remote and exclaims “What is this garbage you’re watching? I want to watch the news.” He changes the channel to footage of U.S. President Ronald Reagan at the 1986 nuclear arms control summit in Reykjavik, Iceland. The son, perturbed, turns to his father, replies “this is the news,” and lips the channel back. Megadeth’s song accelerates, and the video re- turns to riot footage. The song ends by repeatedly asking, “Peace sells, but who’s buying?” It was a prescient question during a 1980s in which Cold War militarism and the nuclear arms race escalated to dangerous new highs.1 In the 1980s, MTV elevated music videos to a new cultural prominence. Of course, most music videos were not political.2 Yet, as “Peace Sells” suggests, dur- ing the 1980s—the decade of Reagan’s “Star Wars” program, the Soviet war in Afghanistan, and a robust nuclear arms race—music videos had the potential to relect political concerns. MTV’s founders, however, were so culturally conserva- tive that many were initially wary of playing African American artists; addition- ally, record labels were hesitant to put their top artists onto this new, risky chan- 1 American President Ronald Reagan had increased peace-time deicit defense spending substantially. -

War of 1812 Booklist Be Informed • Be Entertained 2013
War of 1812 Booklist Be Informed • Be Entertained 2013 The War of 1812 was fought between the United States and Great Britain from June 18, 1812 through February 18, 1815, in Virginia, Maryland, along the Canadian border, the western frontier, the Gulf Coast, and through naval engagements in the Great Lakes and the Atlantic and Pacific Oceans. In the United States frustrations mounted over British maritime policies, the impressments of Americans into British naval service, the failure of the British to withdraw from American territory along the Great Lakes, their backing of Indians on the frontiers, and their unwillingness to sign commercial agreements favorable to the United States. Thus the United States declared war with Great Britain on June 18, 1812. It ended with the signing of the Treaty of Ghent on December 24, 1814, although word of the treaty did not reach America until after the January 8, 1815 Battle of New Orleans. An estimated 70,000 Virginians served during the war. There were some 73 armed encounters with the British that took place in Virginia during the war, and Virginians actively fought in Maryland, Virginia, and Ohio and in naval engagements. The nation’s capitol, strategically located off the Chesapeake Bay, was a prime target for the British, and the coast of Virginia figured prominently in the Atlantic theatre of operations. The War of 1812 helped forge a national identity among the American states and laid the groundwork for a national system of homeland defense and a professional military. For Canadians it also forged a national identity, but as proud British subjects defending their homes against southern invaders. -

The Aesthetics of Stealth Towards an Activist Philosophy of Becoming-Imperceptible in Contemporary Media Pape, T
UvA-DARE (Digital Academic Repository) The aesthetics of stealth Towards an activist philosophy of becoming-imperceptible in contemporary media Pape, T. DOI 10.1080/14680777.2017.1326564 Publication date 2017 Document Version Final published version Published in Feminist Media Studies License CC BY Link to publication Citation for published version (APA): Pape, T. (2017). The aesthetics of stealth: Towards an activist philosophy of becoming- imperceptible in contemporary media. Feminist Media Studies, 17(4), 630-645. https://doi.org/10.1080/14680777.2017.1326564 General rights It is not permitted to download or to forward/distribute the text or part of it without the consent of the author(s) and/or copyright holder(s), other than for strictly personal, individual use, unless the work is under an open content license (like Creative Commons). Disclaimer/Complaints regulations If you believe that digital publication of certain material infringes any of your rights or (privacy) interests, please let the Library know, stating your reasons. In case of a legitimate complaint, the Library will make the material inaccessible and/or remove it from the website. Please Ask the Library: https://uba.uva.nl/en/contact, or a letter to: Library of the University of Amsterdam, Secretariat, Singel 425, 1012 WP Amsterdam, The Netherlands. You will be contacted as soon as possible. UvA-DARE is a service provided by the library of the University of Amsterdam (https://dare.uva.nl) Download date:02 Oct 2021 Feminist Media Studies ISSN: 1468-0777 (Print) 1471-5902 (Online) Journal homepage: http://www.tandfonline.com/loi/rfms20 The aesthetics of stealth: towards an activist philosophy of becoming-imperceptible in contemporary media Toni Pape To cite this article: Toni Pape (2017) The aesthetics of stealth: towards an activist philosophy of becoming-imperceptible in contemporary media, Feminist Media Studies, 17:4, 630-645, DOI: 10.1080/14680777.2017.1326564 To link to this article: https://doi.org/10.1080/14680777.2017.1326564 © 2017 The Author(s). -

The Oxford Dictionary of New Words: a Popular Guide to Words in the News
The Oxford Dictionary of New Words: A popular guide to words in the news PREFACE Preface This is the first dictionary entirely devoted to new words and meanings to have been published by the Oxford University Press. It follows in the tradition of the Supplement to the Oxford English Dictionary in attempting to record the history of some recent additions to the language, but, unlike the Supplement, it is necessarily very selective in the words, phrases, and meanings whose stories it sets out to tell and it stands as an independent work, unrelated (except in the resources it draws upon) to the Oxford English Dictionary. The aim of the Oxford Dictionary of New Words is to provide an informative and readable guide to about two thousand high-profile words and phrases which have been in the news during the past decade; rather than simply defining these words (as dictionaries of new words have tended to do in the past), it also explains their derivation and the events which brought them to prominence, illustrated by examples of their use in journalism and fiction. In order to do this, it draws on the published and unpublished resources of the Oxford English Dictionary, the research that is routinely carried out in preparing new entries for that work, and the word-files and databases of the Oxford Dictionary Department. What is a new word? This, of course, is a question which can never be answered satisfactorily, any more than one can answer the question "How long is a piece of string?" It is a commonplace to point out that the language is a constantly changing resource, growing in some areas and shrinking in others from day to day. -
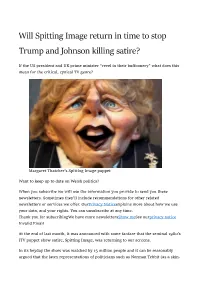
Will Spitting Image Return in Time to Stop Trump and Johnson Killing Satire?
Will Spitting Image return in time to stop Trump and Johnson killing satire? If the US president and UK prime minister “revel in their buffoonery” what does this mean for the critical, cynical TV genre? Margaret Thatcher's Spitting Image puppet Want to keep up to date on Welsh politics? When you subscribe we will use the information you provide to send you these newsletters. Sometimes they’ll include recommendations for other related newsletters or services we offer. OurPrivacy Noticeexplains more about how we use your data, and your rights. You can unsubscribe at any time. Thank you for subscribingWe have more newslettersShow meSee ourprivacy notice Invalid Email At the end of last month, it was announced with some fanfare that the seminal 1980’s ITV puppet show satire, Spitting Image, was returning to our screens. In its heyday the show was watched by 15 million people and it can be reasonably argued that the latex representations of politicians such as Norman Tebbit (as a skin- head bovver boy), Kenneth Baker (half human, half slug) and Michael Heseltine (a wide-eyed and feral Tarzan) filtered down into popular consciousness rendering the fictional far more memorable than the actual. Apparently, the proposed new series’ first episode has already been filmed and Roger Law, one of the show’s original creators, confirmed to the Guardian that producers were in talks with US TV networks about bringing the programme to a global audi- ence. This is significant because the primary target of the newest incarnation of Spitting Image is going to be, unsurprisingly, the so-called leader of the free world, Donald Trump. -

The First Americans the 1941 US Codebreaking Mission to Bletchley Park
United States Cryptologic History The First Americans The 1941 US Codebreaking Mission to Bletchley Park Special series | Volume 12 | 2016 Center for Cryptologic History David J. Sherman is Associate Director for Policy and Records at the National Security Agency. A graduate of Duke University, he holds a doctorate in Slavic Studies from Cornell University, where he taught for three years. He also is a graduate of the CAPSTONE General/Flag Officer Course at the National Defense University, the Intelligence Community Senior Leadership Program, and the Alexander S. Pushkin Institute of the Russian Language in Moscow. He has served as Associate Dean for Academic Programs at the National War College and while there taught courses on strategy, inter- national relations, and intelligence. Among his other government assignments include ones as NSA’s representative to the Office of the Secretary of Defense, as Director for Intelligence Programs at the National Security Council, and on the staff of the National Economic Council. This publication presents a historical perspective for informational and educational purposes, is the result of independent research, and does not necessarily reflect a position of NSA/CSS or any other US government entity. This publication is distributed free by the National Security Agency. If you would like additional copies, please email [email protected] or write to: Center for Cryptologic History National Security Agency 9800 Savage Road, Suite 6886 Fort George G. Meade, MD 20755 Cover: (Top) Navy Department building, with Washington Monument in center distance, 1918 or 1919; (bottom) Bletchley Park mansion, headquarters of UK codebreaking, 1939 UNITED STATES CRYPTOLOGIC HISTORY The First Americans The 1941 US Codebreaking Mission to Bletchley Park David Sherman National Security Agency Center for Cryptologic History 2016 Second Printing Contents Foreword ................................................................................ -

Chapter 30.Pdf
p0934-935aspe-0830co 10/17/02 9:22 AM Page 934 U.S. troops on patrol with helicopter support in Vietnam, 1965. 1960 John 1963 Kennedy is 1964 Lyndon F. Kennedy assassinated; B. Johnson 1965 First major is elected Lyndon B. Johnson is elected U.S. combat units president. becomes president. president. arrive in Vietnam. USA 1960 WORLD 1960 19651965 1960 The National 1962 The 1966 Mao Liberation Front forms African nation of Zedong begins 1967 Israel in South Vietnam. Uganda becomes the Cultural captures Gaza independent. Revolution Strip and in China. West Bank in Six-Day War. 934 CHAPTER 30 p0934-935aspe-0830co 10/17/02 9:22 AM Page 935 INTERACTINTERACT WITH HISTORY In 1965, America’s fight against com- munism has spread to Southeast Asia, where the United States is becoming increasingly involved in another country’s civil war. Unable to claim victory, U.S. generals call for an increase in the number of combat troops. Facing a shortage of volunteers, the president implements a draft. Who should be exempt from the draft? Examine the Issues • Should people who believe the war is wrong be forced to fight? • Should people with special skills be exempt? • How can a draft be made fair? RESEARCH LINKS CLASSZONE.COM Visit the Chapter 30 links for more information about The Vietnam War Years. 1968 Martin Luther King, Jr., and Robert Kennedy are 1970 Ohio 1973 United assassinated. National 1969 States signs Guard kills 1968 Richard U.S. troops 1972 cease-fire four students M. Nixon is begin their Richard M. with North 1974 Gerald R. -

Television and the Cold War in the German Democratic Republic
0/-*/&4637&: *ODPMMBCPSBUJPOXJUI6OHMVFJU XFIBWFTFUVQBTVSWFZ POMZUFORVFTUJPOT UP MFBSONPSFBCPVUIPXPQFOBDDFTTFCPPLTBSFEJTDPWFSFEBOEVTFE 8FSFBMMZWBMVFZPVSQBSUJDJQBUJPOQMFBTFUBLFQBSU $-*$,)&3& "OFMFDUSPOJDWFSTJPOPGUIJTCPPLJTGSFFMZBWBJMBCMF UIBOLTUP UIFTVQQPSUPGMJCSBSJFTXPSLJOHXJUI,OPXMFEHF6OMBUDIFE ,6JTBDPMMBCPSBUJWFJOJUJBUJWFEFTJHOFEUPNBLFIJHIRVBMJUZ CPPLT0QFO"DDFTTGPSUIFQVCMJDHPPE Revised Pages Envisioning Socialism Revised Pages Revised Pages Envisioning Socialism Television and the Cold War in the German Democratic Republic Heather L. Gumbert The University of Michigan Press Ann Arbor Revised Pages Copyright © by Heather L. Gumbert 2014 All rights reserved This book may not be reproduced, in whole or in part, including illustrations, in any form (be- yond that copying permitted by Sections 107 and 108 of the U.S. Copyright Law and except by reviewers for the public press), without written permission from the publisher. Published in the United States of America by The University of Michigan Press Manufactured in the United States of America c Printed on acid- free paper 2017 2016 2015 2014 5 4 3 2 A CIP catalog record for this book is available from the British Library. ISBN 978– 0- 472– 11919– 6 (cloth : alk. paper) ISBN 978– 0- 472– 12002– 4 (e- book) Revised Pages For my parents Revised Pages Revised Pages Contents Acknowledgments ix Abbreviations xi Introduction 1 1 Cold War Signals: Television Technology in the GDR 14 2 Inventing Television Programming in the GDR 36 3 The Revolution Wasn’t Televised: Political Discipline Confronts Live Television in 1956 60 4 Mediating the Berlin Wall: Television in August 1961 81 5 Coercion and Consent in Television Broadcasting: The Consequences of August 1961 105 6 Reaching Consensus on Television 135 Conclusion 158 Notes 165 Bibliography 217 Index 231 Revised Pages Revised Pages Acknowledgments This work is the product of more years than I would like to admit. -

Its Only a Movie: Reel Life Adventures of a Film Obsessive Free
FREE ITS ONLY A MOVIE: REEL LIFE ADVENTURES OF A FILM OBSESSIVE PDF Mark Kermode | 352 pages | 01 Jan 2011 | Cornerstone | 9780099543480 | English | London, United Kingdom It's Only a Movie by Mark Kermode | Waterstones Goodreads helps you keep track of books you want to read. Want to Read saving…. Want to Read Currently Reading Read. Other editions. Enlarge cover. Error rating book. Refresh and try again. Open Preview See a Problem? Details if other :. Thanks for telling us about the problem. Return to Book Page. It's Only a Movie by Mark Kermode. Film critic and broadcaster, Mark Kermode, has written a forthright account of a life lived in film. From his favourite movies to rants against Pirates of the Caribbeanand the current resurgence of 3D, there are spirited defences of Hannah Montana and Mamma Mia. Get A Copy. Paperbackpages. More Details Original Title. Other Editions 6. Friend Reviews. To see what your friends thought of this book, please sign up. To ask other readers questions about It's Only a Movieplease sign up. Lists with This Book. Community Reviews. Showing Average rating 3. Rating details. More filters. Sort order. Start your review of It's Only a Movie. Especially for a book I bought two years ago to find info that wasn't even in it, this was a lot of fun. The first couple of chapters I liked so much I thought I'd be giving it 5 stars. The nostalgia was perfectly pitched - childhood 70s cinema, 80s leftwing student politics and journalism. That was being a "proper student", because of course, being a kid at the time, that's when my idea of how students were was formed. -

Before Its Time: Public Perception of Disability Rights, the Americans with Disabilities Act, and the Future of Access and Accommodation
Washington University Journal of Law & Policy Volume 23 Disabilities January 2007 Before Its Time: Public Perception of Disability Rights, the Americans with Disabilities Act, and the Future of Access and Accommodation Mary Johnson The Disability Rag Follow this and additional works at: https://openscholarship.wustl.edu/law_journal_law_policy Part of the Disability Law Commons Recommended Citation Mary Johnson, Before Its Time: Public Perception of Disability Rights, the Americans with Disabilities Act, and the Future of Access and Accommodation, 23 WASH. U. J. L. & POL’Y 121 (2007), https://openscholarship.wustl.edu/law_journal_law_policy/vol23/iss1/5 This Essay is brought to you for free and open access by the Law School at Washington University Open Scholarship. It has been accepted for inclusion in Washington University Journal of Law & Policy by an authorized administrator of Washington University Open Scholarship. For more information, please contact [email protected]. Before Its Time: Public Perception of Disability Rights, the Americans with Disabilities Act, and the Future of Access and Accommodation Mary Johnson* The 1990 Americans with Disabilities Act (ADA)1 passed Congress as a result of the work of a small group of disability rights lobbyists. Unlike those who worked on the 1964 Civil Rights Act when it was in Congress, these lobbyists did not mount an effort to explain to the public the need for the law. They did not try to get reporters to write about the problem of disability discrimination and the need for civil rights protections for people with disabilities. They believed that reporters held too many stereotypes about people with disabilities to be trusted to write accurately about the need for the law.2 Because of this group’s strategy of avoiding the media, the ADA passed without any broad societal understanding about what “disability discrimination” means, and it seems that, because of this, it has taken a beating in both the court of law and the court of public opinion.