Print Cloud User’S Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Guidance for the Provision of ESI to Detainees
Guidance for the Provision of ESI to Detainees Joint Electronic Technology Working Group October 25, 2016 Contents Guidance ......................................................................................................................................... 1 I. An Approach to Providing e-Discovery to Federal Pretrial Detainees ................................... 1 II. Special Concerns in the Delivery of ESI to Detainees ........................................................... 2 A. Defense Concerns .............................................................................................................. 2 B. CJA and FDO Budgeting Concerns ................................................................................... 3 C. Court Concerns ................................................................................................................... 3 D. Facility Concerns ............................................................................................................... 3 E. U.S. Marshals Service Concerns ........................................................................................ 4 F. Government Concerns ........................................................................................................ 4 III. Practical Steps ....................................................................................................................... 4 A. Government, Defense, Facility and Judicial Points of Contact/Working Group ............... 4 B. Identify Facility e-Discovery Capabilities ........................................................................ -

Mac OS X: an Introduction for Support Providers
Mac OS X: An Introduction for Support Providers Course Information Purpose of Course Mac OS X is the next-generation Macintosh operating system, utilizing a highly robust UNIX core with a brand new simplified user experience. It is the first successful attempt to provide a fully-functional graphical user experience in such an implementation without requiring the user to know or understand UNIX. This course is designed to provide a theoretical foundation for support providers seeking to provide user support for Mac OS X. It assumes the student has performed this role for Mac OS 9, and seeks to ground the student in Mac OS X using Mac OS 9 terms and concepts. Author: Robert Dorsett, manager, AppleCare Product Training & Readiness. Module Length: 2 hours Audience: Phone support, Apple Solutions Experts, Service Providers. Prerequisites: Experience supporting Mac OS 9 Course map: Operating Systems 101 Mac OS 9 and Cooperative Multitasking Mac OS X: Pre-emptive Multitasking and Protected Memory. Mac OS X: Symmetric Multiprocessing Components of Mac OS X The Layered Approach Darwin Core Services Graphics Services Application Environments Aqua Useful Mac OS X Jargon Bundles Frameworks Umbrella Frameworks Mac OS X Installation Initialization Options Installation Options Version 1.0 Copyright © 2001 by Apple Computer, Inc. All Rights Reserved. 1 Startup Keys Mac OS X Setup Assistant Mac OS 9 and Classic Standard Directory Names Quick Answers: Where do my __________ go? More Directory Names A Word on Paths Security UNIX and security Multiple user implementation Root Old Stuff in New Terms INITs in Mac OS X Fonts FKEYs Printing from Mac OS X Disk First Aid and Drive Setup Startup Items Mac OS 9 Control Panels and Functionality mapped to Mac OS X New Stuff to Check Out Review Questions Review Answers Further Reading Change history: 3/19/01: Removed comment about UFS volumes not being selectable by Startup Disk. -
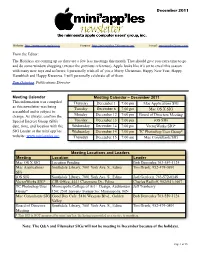
From the Editor: the Holidays Are Coming up So There Are a Few Less Meetings This Month
December 2011 Website: http://www.miniapples.org Forums: http://miniapples.7.forumer.com Email: [email protected] From the Editor: The Holidays are coming up so there are a few less meetings this month. That should give you extra time to go and do some window shopping (excuse the previous reference). Apple looks like it’s set to excel this season with many new toys and software. I personally wish all of you a Merry Christmas, Happy New Year, Happy Hanukkah and Happy Kwanzaa. I will personally celebrate all of them. Tom Ostertag, Publications Director Meeting Calendar Meeting Calendar – December 2011 This information was compiled Thursday December 1 7:00 pm Mac Applications SIG as this newsletter was being Tuesday December 6 7:00 pm Mac OS X SIG assembled and is subject to change. As always, confirm the Monday December 12 7:00 pm Board of Directors Meeting Special Interest Group (SIG) Tuesday December 13 7:00 pm iOS SIG date, time, and location with the Wednesday December 14 7:00 pm VectorWorks SIG* SIG Leader or the mini’app’les Wednesday December 14 7:00 pm TC Photoshop User Group* website: www.miniapples.org. Thursday December 15 7:00 am Mac Consultants SIG Meeting Locations and Leaders Meeting Location Leader Mac OS X SIG Location Pending Bob Demeules 763-559-1124 Mac Applications Southdale Library, 7001 York Ave. S., Edina Tim Drenk, 952-479-0891 SIG iOS SIG Southdale Library, 7001 York Ave. S., Edina Joel Gerdeen, 763-572-0148 VectorWorks SIG* CJR Office, 4441 Claremore Dr., Edina Charles Radloff, 952-941-1667 TC Photoshop User Minneapolis College of Art + Design, Auditorium Jeff Tranberry Group* 150; 2501 Stevens Avenue So; Minneapolis, MN Mac Consultants SIG Good Day Cafe, 5410 Wayzata Blvd., Golden Bob Demeules 763-559-1124 Valley Board of Directors Southdale Library, 7001 York Ave. -

Macintosh Hypercard 1.2 Software Overview
Macintosh HyperCard 1.2 Software f:!l :: :·: Home Card Address Documents Calendar Clip Art Card Ideas Ideas Stack Ideas Quotations Button Overview HyperCard® softwarefor the on cards that appear on the language, HyperTalk'� built into Macintosh® familyof personal Macintosh screen. A group of HyperCard. HyperTalk lets you computers lets you organize in these cards is called a "stack." You write your own scripts to give formationmuch the way you can make notes, type, or draw on directions to buttons. Developers do in your mind-by association them just as you might on paper can extend HyperTalk to control and context. It lets you explore index cards. You can sort cards, external devices such as large amounts of information at browse among them, or quickly videodisc players, on-line infor exceptional speeds, or quickly findspecific inf ormation by point mation services, and CD-ROM zero in on exactly what you need. ing and clicking on "buttons." drives. HyperCard is also the ideal tool Buttons do specifictasks , such HyperCard is a powerfulnew formanaging and creating infor as connecting one card to another. medium forcreating and exchang mation using virtually any type of Buttons can also do many other ing information. It is an extension media, including video, animation, things, such as dialing a phone, of Macintosh technology that puts and sound. printing a report-evenlaunching new power into the hands of all HyperCard uses as a metaphor a other applications. You can sim Macintosh users. With this power, nearly universal method forstoring ply cut and paste the buttons that people without special training in information: the index card. -

Quicktime 4.1
QuickTime 4.1 Apple Technical Publications January 2000 Apple Computer, Inc. Apple, the Apple logo, FireWire, Mac, LIMITED WARRANTY ON MEDIA AND © 2000 Apple Computer, Inc. Macintosh, and QuickTime are REPLACEMENT All rights reserved. trademarks of Apple Computer, Inc., ALL IMPLIED WARRANTIES ON THIS No part of this publication or the registered in the United States and other MANUAL, INCLUDING IMPLIED software described in it may be countries. WARRANTIES OF MERCHANTABILITY reproduced, stored in a retrieval system, The QuickTime logo is a trademark of AND FITNESS FOR A PARTICULAR or transmitted, in any form or by any Apple Computer, Inc. PURPOSE, ARE LIMITED IN DURATION means, mechanical, electronic, Adobe, Acrobat, Photoshop, and TO NINETY (90) DAYS FROM THE DATE photocopying, recording, or otherwise, PostScript are trademarks of Adobe OF DISTRIBUTION OF THIS PRODUCT. without prior written permission of Systems Incorporated or its subsidiaries Even though Apple has reviewed this Apple Computer, Inc., except in the and may be registered in certain manual, APPLE MAKES NO WARRANTY normal use of the software or to make a jurisdictions. OR REPRESENTATION, EITHER EXPRESS backup copy of the software or Flash is a trademark of Macromedia OR IMPLIED, WITH RESPECT TO THIS documentation. The same proprietary Incorporated. MANUAL, ITS QUALITY, ACCURACY, and copyright notices must be affixed to MacPaint is a trademark of Apple MERCHANTABILITY, OR FITNESS FOR A any permitted copies as were affixed to Computer, Inc., registered in the U.S. PARTICULAR PURPOSE. AS A RESULT, the original. This exception does not and other countries. THIS MANUAL IS DISTRIBUTED “AS IS,” allow copies to be made for others, AND YOU ARE ASSUMING THE ENTIRE whether or not sold, but all of the Helvetica and Palatino are registered trademarks of Linotype-Hell AG and/or RISK AS TO ITS QUALITY AND material purchased (with all backup ACCURACY. -

Using Macwrite and Macpaint 1984.Pdf
.. Tim Field ""'--·-·.·.··---~-- . '-- ~ ... -.~ ·-:·....... ---.. ...... ;,..~-- ' I USING MACWRITETM AND I MAC PAINT™ Tim Field Osborne McGraw-Hill Berkeley, California Published by Osborne McGraw-Hill 2600 Tenth Street Berkeley, California 94710 U.S.A. For information on translations and book distributors outside of the U.S.A., please write to Osborne McGraw-Hill at the above address. MacWrite, MacPaint, Macintosh, and The Finder are trademarks of Apple Computer, Inc. Using MacWriteTM and MacPaint™ is not sponsored or approved by or connected with Apple Computer, Inc. All references to MacWrite, MacPaint, Macintosh, and the Finder in the text of this book are to the trademarks of Apple Computer, Inc. Apple is a registered trademark of Apple Computer, Inc. IBM is a registered trademark of International Business Machines, Inc. USING MACWRITE'u AND MACPAINT™ Copyright @ 1984 by McGraw-Hill, Inc. All rights reserved. Printed in the United States of America. Except as permitted under the Copyright Act of 1976, no part of this publication may be reproduced or distributed in any form or by any means, or stored in a data base or retrieval system, without the prior written permission of the publisher, with the excep tion that the program listings may be entered, stored, and executed in a computer system, but they may not be reproduced for publication. 234567890 DODO 8987654 ISBN 0-88134-137-1 Judy Ziajka, Acquisitions Editor Dave Ushijima, Technical Editor Fran Haselsteiner, Copy Editor Jan Benes, Text Design Yashi Okita, Cover Design TABLE -

Download the Manual in PDF Format
-$ The Graphicrn Exchange The Graphics Conversion Utility for the AppleQP JIGS by John MacLean © Copyright 1987-1990 Techflow Pty, Ltd. Manual by Shann Kellaway, John MacLean, & Jeff Smith Produced by: Roger Wagner Publishing, Inc. 1050 Pioneer Way, Suite "P" E1 Cajon, California 92020 Customer Service & Technical Support: 619/442-0522 ISBN 0-927796-01-5 1M90 A -$ I -$- I -$ B -$1 Customer Licensing Agreement The Roger Wagner Publishing, Inc. software product that you have just received from Roger Wagner Publishing, Inc., or one of its authorized dealers, is provided to you subject to the Terms and Conditions of the Software Customer Licensing Agreement. Should you decide that you cannot accept these Tenns and Conditions, then you must return your product with all documentation and this License marked "REFUSED" within the 30 day examination period following the receipt of the product. 1. License. Roger Wagner Publishing, Inc. hereby grants you upon your receipt of this product, a nonexclusive license to use the enclosed Roger Wagner Publishing, Inc. product subject to the tenns and restrictions set forth in this License Agreement 2. Copyright. This software product, and its documentation, is copyrighted by Roger Wagner Publishing, Inc., with all rights reserved. You may not copy or otherwise reproduce the product or any part of it except as ex pressly permitted in this License. 3. Restrictions on Use and Transfer. The original and any backup copies of this product are intended for your own personal use in connection with no more than two computers (for example, one at home and one at work). You may not sell or transfer copies of, or any part of, this product, nor rent or lease to others without the express written pennission of Roger Wagner Publishing, Inc. -

AP-DATA Supported File Formats and Size Limits V8.2
TRITON AP-DATA Supported File Formats and Size Limits Supported File Formats and Size Limits | TRITON AP-DATA| Version 8.2.x This article provides a list of all the Supported File Formats that can be analyzed by Forcepoint™ TRITON® AP-DATA, as well as the File Size Limits for network, endpoint, and discovery functions. Use the arrows to proceed. Supported File Formats Supported File Formats and Size Limits | TRITON AP-DATA | Version 8.2.x This article provides a list of all the file formats that TRITON AP-DATA supports. The file formats supported are constantly being updated and added to. File Type Description 7-Zip 7-Zip format Ability Comm Communication Ability Ability DB Database Ability Ability Image Raster Image Ability Ability SS Spreadsheet Ability Ability WP Word Processor Ability AC3 Audio File Format AC3 Audio File Format ACE ACE Archive ACT ACT AD1 AD1 evidence file Adobe FrameMaker Adobe FrameMaker Adobe FrameMaker Book Adobe FrameMaker Book Adobe Maker Interchange Adobe Maker Interchange format Adobe PDF Portable Document Format Advanced Streaming Microsoft Advanced Streaming file TRITON AP-DATA - Supported Files Types and Size Limits 1 TRITON AP-DATA Supported File Formats and Size Limits File Type Description Advanced Systems Format Advanced Systems Format (ASF) Advanced Systems Format Advanced Systems Format (WMA) Advanced Systems Format Advanced Systems Format (WMV) AES Multiplus Comm Multiplus (AES) Aldus Freehand Mac Aldus Freehand Mac Aldus PageMaker (DOS) Aldus PageMaker for Windows Aldus PageMaker (Mac) Aldus PageMaker -

Graphicconverter V4.5 a Converter for the Classic Macos® and Macos X®
GraphicConverter V4.5 A converter for the Classic MacOS® and MacOS X® User’s manual ©1992-2002 Lemke Software GmbH Thorsten Lemke Date: 2002-10-28 1 Table of contents 1 INTRODUCTION 7 1.1 Features 7 1.2 Requirements 7 1.3 Registration 7 1.4 Payment 7 1.5 Restrictions 8 1.6 Errors 8 1.7 For me 8 1.8 Thanks 8 1.9 Legal Statements 8 1.10 About this Documentation 8 1.11 Copyright Notice 8 2 PREFACE 9 2.1 Words and Terms 9 2.2 Installation 9 3 MENUS 10 3.1 Apple Menu (Classic MacOS) 10 3.1.1 About GraphicConverter… 10 3.1.2 About Plug-ins/Add-ons 10 3.2 GraphicConverter Menu (MacOS X) 10 3.2.1 About GraphicConverter… 10 3.2.2 About Plug-ins/Add-ons 10 3.3 File Menu 11 3.3.1 New 11 3.3.2 Open 15 3.3.3 Browse Folder 16 3.3.4 Close 18 3.3.5 Close All 18 2 3.3.6 Save 18 3.3.7 Save All 18 3.3.8 Save as 19 3.3.9 Save a Copy as 36 3.3.10 Revert 36 3.3.11 Aquire 36 3.3.12 Export 37 3.3.13 Edit File Info (IPTC) 37 3.3.14 Edit Color Profile 37 3.3.15 Slide Show 38 3.3.16 Slideshow with Find 39 3.3.17 Continue Slide Show 39 3.3.18 Convert… 39 3.3.19 Page Setup 51 3.3.20 Print 51 3.3.21 Print Catalog 52 3.3.22 Print Folder 54 3.3.23 Quit 54 3.4 Edit Menu 55 3.4.1 Undo 55 3.4.2 Cut 55 3.4.3 Copy 55 3.4.4 Paste 57 3.4.5 Clear 57 3.4.6 Find and Replace 58 3.4.7 Select all 58 3.4.8 Select Picture Content 58 3.4.9 Invert Selection 58 3.4.10 Unselect 58 3.4.11 Fill Selection with Foreground Color 58 3.4.12 Trim 58 3.4.13 Trim Options 59 3.4.14 Compare 59 3.4.15 Next Page 59 3.4.16 Previous Page 60 3.4.17 Goto Page 60 3.4.18 Enable/Disable Grid 60 3.4.19 Grid -
Mac Os 9 Emulator for Mac
1 / 4 Mac Os 9 Emulator For Mac By contrast, the 68k emulator accesses the very lowest levels of the OS by being at the same level as, and tightly connected to, the Mac OS nanokernel on PPC Macs, which means that the nanokernel is able to intercept PowerPC interrupts, translate them to 68k interrupts (then doing a mixed mode switch, if necessary), and then execute 68k code to handle the interrupts.. It gives developers and consumers a transition period in which to update their application software to run on newer hardware.. Macintosh OS or popularly known as Mac OS used by Apple on its Mac PC’s and Macbook’s is an awesome OS, with its awesome user-interface, and great features, wouldn’t it be more awesome if we are able to run Android on Mac os.. Even if you own the original hardware and software, you may find yourself technically on the wrong side of infringement legislation unless you extract the ROMs yourself.. 5 (Leopard) Mac OSX 10 4 (Tiger) Windows 8 1; Windows 8; Windows 7; Windows Vista; Windows XP; Networking; Guides. The machines creator, Steve Wozniak, wanted the Apple II to play a decent game of Breakout, in order to impress his computer club chums.. The Internet Archive and Scullin Steel both have Apple II emulators that enable you to load apps and games in a browser.. [2]Rosetta[edit]Mac transition to Intel processorsApple released the first version of Rosetta in 2006 when it changed the instruction set architecture of the Macintoshplatform from the PowerPC to the Intel processor. -

Quicktime 7.3 User’S Guide Includes Instructions for Using Quicktime Pro for Mac OS X Version 10.3.9 Or Later, and Windows
QuickTime 7.3 User’s Guide Includes instructions for using QuickTime Pro For Mac OS X version 10.3.9 or later, and Windows K Apple Inc. Apple, the Apple logo, AppleScript, Final Cut Pro, © 2007 Apple Inc. All rights reserved. FireWire, iMovie, iPod, iTunes, Mac, Mac OS, Macintosh, QuickDraw, and QuickTime are trademarks of Apple Inc., Under the copyright laws, this manual may not be registered in the U.S. and other countries. Finder, copied, in whole or in part, without the written consent iPhone, and Tiger are trademarks of Apple Inc. Apple of Apple. Your rights to the software are governed by Store is a service mark of Apple Inc., registered in the the accompanying software license agreement. U.S. and other countries. .Mac is a service mark of Apple The Apple logo is a trademark of Apple Inc., registered Inc. in the U.S. and other countries. Use of the “keyboard” Intel, Intel Core, and Xeon are trademarks of Intel Corp. Apple logo (Option-Shift-K) for commercial purposes in the U.S. and other countries. without the prior written consent of Apple may constitute trademark infringement and unfair PowerPC™ is a trademark of International Business competition in violation of federal and state laws. Machines Corporation, used under license therefrom. Every effort has been made to ensure that the Other company and product names mentioned herein information in this manual is accurate. Apple is not are trademarks of their respective companies. Mention responsible for printing or clerical errors. of third-party products is for informational purposes only and constitutes neither an endorsement nor a Apple recommendation. -

The Macintosh
I s.~.s.T.E.M'I-. R.E;V.'~.E.WI The Macintosh ?;. ?;. , 7% The ew computers-indeed, few consumer figure 1) the system costs $2990. The pro- many items of any kind-have generated cessor is a Motorola 68000, running a name- F such a wide range of opinions as the less operating system (see the text box. 'A $ facets of a Macintosh. Criticized as an expensive gimmick Second Opinion" on page 248 for a full slightly and hailed as the liberator of the masses, the description). It has absolutely no IBM PUMS Mac is a potentially great system. Whether it DOS compatibility, and it would appear Ap- flawed gem lives up to that potential remains to be seen. ple plans none. Personally, I think the Macintosh is a won- 1- - 1- derful machine. I use one daily at work, and lNE then at night I play with the one I have at The display is small (9-inch diagonal). but it BY BRUCE ' home. Or, at least, I try to play with it. You see, has very high resolution (512 by 342 pixels). my wife-who for years resisted all my at- Every pixel is crisp. Several things make the tempts to introduce her to computers-has display unusual. First, the Macintosh has no fallen in love with the Mac (her words, not "text mode:' Instead, the display is always bit- mine). She uses it to type up medical reports, mapped graphics. Second, the display is black- notes on her clients, and personal letters. In on-white rather than amber-, green-, or color- fact, she's suggested that we get a second on-black, giving it an ink-on-paper effect.