Zero to Monero: First Edition a Technical Guide to a Private Digital Currency; for Beginners, Amateurs, and Experts Published June 26, 2018 (V1.0.0)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Auditing Wallets in Cryptonote
Auditing wallets in CryptoNote sowle <[email protected]> Zano project, https://zano.org Cryptocurrency wallet auditing is the ability for a third party (the "auditor") to watch the transactions and to be able to calculate the correct balance without an ability to spend a coin. This article explores several possible implementations of expansion cryptocurrency protocol CryptoNote 2.0 [1] with such ability. In the original CryptoNote protocol auditing is only partially possible with the help of the tracking key, namely, an auditor is able to distinguish incoming transactions in the blockchain, but the full set of secret keys is required to filter out outgoing transactions. This article is intended for readers familiar with the general blockchain technology and “classic” cryptocurrencies, as well as with the basics of cryptography on elliptic curves. 1. Introduction What is CryptoNote? Surprisingly, most people interested in blockchain technology have never heard anything about CryptoNote, in spite of the fact that the technology has more than 300 forks, including Monero as the most famous. Back in 2014 in the cryptocurrency community there were mentions [2] about a project, titled Bytecoin. That project did not originate as a Bitcoin or other known project fork, having its own original codebase. It was very unusual at the time. Bytecoin general conception was to be an implementation of a privacy-technology named CryptoNote. There were two main privacy mechanisms: stealth-addresses and inputs` mixing-in with the help of ring signatures (at the time it was called "blockchain mixer"). Since Zcash existed only on paper / in theory at that time, CryptoNote became a competitive technology and has provoked much controversy in the cryptocurrency community. -

Examining the Lightning Network on a Protocol Level
Examining the Lightning network on a protocol level Rene Pickhardt (Data Science Consultant) https://www.rene-pickhardt.de & https://twitter.com/renepickhardt München 19.7.2018 I've been told I should start any talk with something everybody in the audience should know A standard Bitcoin Transaction has 6 data fields ( The following is a brief summary of https://en.bitcoin.it/wiki/Transaction#Input ) ● Version number (4 Bytes) ● In-Counter (1-9 Bytes) ● List of inputs (depending on the Value of <In-Counter>) ● Out-Counter (1-9 Bytes) ● List of Outputs (depending on the Value of <Out-Counter>) ● Lock_time (4 Bytes) ( Bitcoin Transaction with 3 inputs and 2 outputs Data consists mainly of executable scripts! A chain of Bitcoin Transactions with 3 UTXO ● Outputs are references by the inputs ● The Script in the output defines how the transaction can be spent ● Owning Bitcoins means being able to spend the output of an unspent transaction ○ Provide an input script ○ Concatenate it with with some outputscript of an unspent transaction ○ The combined Script needs to evaluate to True Spending a Pay-to-PubkeyHash (standard TX) ● ScriptPubKey (aka the Output Script) ○ OP_DUP OP_HASH160 <pubKeyHash> OP_EQUALVERIFY OP_CHECKSIG ● ScriptSig: (aka the Input Script) ○ <sig> <pubKey> ● Explainations ○ OP_CODES are the instructions of the script language within Bitcoin ○ <data> is depicted like html tags with lesser than and greater than signs ○ The complete script is concatenated as Input || Output and then being executed on a Stack machine <sig> <pubKey> -

(Linkable) Ring Signature from Hash-Then-One-Way Signature
(Linkable) Ring Signature from Hash-Then-One-Way Signature Xingye Lu Man Ho Au ∗ Zhenfei Zhang Department of Computing Department of Computing Algorand The Hong Kong Polytechnic University The Hong Kong Polytechnic University Boston, USA Hong Kong Hong Kong [email protected] [email protected] [email protected] Abstract—In this paper, we revisit the generic construction of (such as RSA) and three-move type (Type-T) signatures ring signatures from hash-then-one-way type (Type-H) signatures (discrete log (DL) based schemes such as Schnorr). While in proposed by Abe et al. (AOS) in 2004 from the following principle similar to the concrete instantiations, security proof aspects. First, we give a proof for the generic construction, in a strengthened security model. Previously, this was only done for for the AOS generic construction is not formally presented. concrete instantiations, in a weaker model. Second, we extend AOS’s framework to generically construct one-time linkable In 1994, Shor presented a quantum algorithm [4] which can ring signatures from Type-H signatures and one-time signatures. be used to break RSA and DL type digital signatures. Since Lastly, we instantiate the generic construction with an NTRU- then, significant effort has been made to develop practical based Type-H signature: FALCON and obtain a post-quantum quantum computers. Facing the potential threat from quantum linkable ring signature scheme. Our analysis shows that the computers, post-quantum cryptography has attracted more and resulting linkable signature is more efficient than any existing lattice based solutions for small to moderate number of users. -

Rev. Rul. 2019-24 ISSUES (1) Does a Taxpayer Have Gross Income Under
26 CFR 1.61-1: Gross income. (Also §§ 61, 451, 1011.) Rev. Rul. 2019-24 ISSUES (1) Does a taxpayer have gross income under § 61 of the Internal Revenue Code (Code) as a result of a hard fork of a cryptocurrency the taxpayer owns if the taxpayer does not receive units of a new cryptocurrency? (2) Does a taxpayer have gross income under § 61 as a result of an airdrop of a new cryptocurrency following a hard fork if the taxpayer receives units of new cryptocurrency? BACKGROUND Virtual currency is a digital representation of value that functions as a medium of exchange, a unit of account, and a store of value other than a representation of the United States dollar or a foreign currency. Foreign currency is the coin and paper money of a country other than the United States that is designated as legal tender, circulates, and is customarily used and accepted as a medium of exchange in the country of issuance. See 31 C.F.R. § 1010.100(m). - 2 - Cryptocurrency is a type of virtual currency that utilizes cryptography to secure transactions that are digitally recorded on a distributed ledger, such as a blockchain. Units of cryptocurrency are generally referred to as coins or tokens. Distributed ledger technology uses independent digital systems to record, share, and synchronize transactions, the details of which are recorded in multiple places at the same time with no central data store or administration functionality. A hard fork is unique to distributed ledger technology and occurs when a cryptocurrency on a distributed ledger undergoes a protocol change resulting in a permanent diversion from the legacy or existing distributed ledger. -

White Paper of Bitcoin Ultimatum Introduction
White Paper of Bitcoin Ultimatum Introduction 1. Problematic of the Blockchain 4. Bitcoin Ultimatum Architecture industry 4.1. Network working principle 1.1. Transactions Anonymity 4.1.1. Main Transaction Types 1.2. Insufficient Development of Key Aspects of the 4.1.1.1. Public transactions Technology 4.1.1.2. Private transactions 1.3. Centralization 4.1.2. Masternode Network 1.4. Mining pools and commission manipulation 4.2. How to become a validator or masternode in 1.5. Decrease in Transaction Speeds BTCU 4.3. Network Scaling Principle 2. BTCU main solutions and concepts 4.4. Masternodes and Validators Ranking System 4.5. Smart Contracts 2.1. Consensus algorithm basis 4.6. Anonymization principle 2.2. Leasing and Staking 4.7. Staking and Leasing 2.3. Projects tokenization and DeFi 4.7.1. Staking 2.4. Transactions Privacy 4.7.2. Leasing 2.5. Atomic Swaps 4.7.2 Multileasing 4.8. BTCU Technical Specifications 3. Executive Summary 4.8.1. Project Stack 4.8.2. Private key generation algorithm 5. Bitcoin Ultimatum Economy 5.1. Initial Supply and Airdrop 5.2. Leasing Economy 5.3. Masternodes and Validators Commission 5.4. Transactions Fee 6. Project Roadmap 7. Legal Introduction The cryptocurrency market is inextricably tied to the blockchain – its fundamental and underlying technology. The modern market is brimming with an abundance of blockchain protocols, algorithms, and concepts, all of which have fostered the development of a wide variety of services and applications. The modern blockchain market offers users an alternative to both established financial systems and ecosystems/infrastructures of applications and services. -

On the Relationship of Cryptocurrency Price with US Stock and Gold Price Using Copula Models
mathematics Article On the Relationship of Cryptocurrency Price with US Stock and Gold Price Using Copula Models Jong-Min Kim 1 , Seong-Tae Kim 2 and Sangjin Kim 3,* 1 Statistics Discipline, University of Minnesota at Morris, Morris, MN 56267, USA; [email protected] 2 Department of Mathematics, North Carolina A&T State University, Greensboro, NC 27411, USA; [email protected] 3 Department of Management and Information Systems, Dong-A University, Busan 49236, Korea * Correspondence: [email protected] Received: 15 September 2020; Accepted: 20 October 2020; Published: 23 October 2020 Abstract: This paper examines the relationship of the leading financial assets, Bitcoin, Gold, and S&P 500 with GARCH-Dynamic Conditional Correlation (DCC), Nonlinear Asymmetric GARCH DCC (NA-DCC), Gaussian copula-based GARCH-DCC (GC-DCC), and Gaussian copula-based Nonlinear Asymmetric-DCC (GCNA-DCC). Under the high volatility financial situation such as the COVID-19 pandemic occurrence, there exist a computation difficulty to use the traditional DCC method to the selected cryptocurrencies. To solve this limitation, GC-DCC and GCNA-DCC are applied to investigate the time-varying relationship among Bitcoin, Gold, and S&P 500. In terms of log-likelihood, we show that GC-DCC and GCNA-DCC are better models than DCC and NA-DCC to show relationship of Bitcoin with Gold and S&P 500. We also consider the relationships among time-varying conditional correlation with Bitcoin volatility, and S&P 500 volatility by a Gaussian Copula Marginal Regression (GCMR) model. The empirical findings show that S&P 500 and Gold price are statistically significant to Bitcoin in terms of log-return and volatility. -

Deviant Decentralized Exchange
DDEEVVXX Deviant Decentralized Exchange A hybrid exchange leveraging Smartcoins on the Bitshares (BTS) blockchain. CONTENTS 03 What is the current landscape for trading crypto assets? 05 Centralized Exchanges 08 Decentralized Exchanges 11 Hybrid Exchanges 13 DEVX Platform 14 Platform Overview 16 DEVX Smart Coin 17 DEVX off-chain engine - The DEVX Transient Protocol (DEVTP) 19 Trading Process 25 What is the status of development / roadmap for these innovations? 26 DEVX Team 03 Crypto assets are here to stay. According to Apple co-founder Steve Wozniak, Bitcoin and WHAT IS THE blockchain will be the next major IT revolution, and will achieve full CURRENT potential in a decade. According to LANDSCAPE FOR Paypal co-founder Peter Thiel, Bitcoin is the next Digital Gold. TRADING CRYPTO Since Bitcoin’s release in 2009, 1,622 altcoin variants have been issued. ASSETS? 2018 has already broken all records with 345 Initial Coin Offerings, and over US$ 7.7 billion of capital raised. DEVX the next revolution 04 Growth in the number of crypto assets has also driven an increase in crypto asset trading, in order to satisfy the requirements of the increasingly numerous universe of holders, investors, arbitrageurs, market makers, speculators and hedgers. There are presently more than 500 crypto asset exchanges to bring together buyers and sellers, where crypto assets are traded for either different digital currencies, or for other assets such as conventional fiat money. These exchanges operate mostly outside Western countries, and range from fully-online platforms to bricks-and-mortar businesses. Currently, almost two thirds of all daily global crypto asset trading volume results from activity on just ten of these exchanges. -

Unique Ring Signatures: a Practical Construction
Unique Ring Signatures: A Practical Construction Matthew Franklin and Haibin Zhang Dept. of Computer Science, University of California, Davis, California 95616, USA {franklin,hbzhang}@cs.ucdavis.edu Abstract. We propose unique ring signatures that simplify and capture the spirit of linkable ring signatures. We use new techniques to provide an instantiation which can be tightly related to the DDH problem in the random oracle model, leading to the most efficient linkable/unique ring signature. Keywords: anonymity, authentication, e-voting system, provable secu- rity, ring signature, tight reduction, unique signature, verifiable random function. 1 Introduction Ring signatures [23] are very useful tools for many privacy-preserving applica- tions. However, they are not adequate in settings where some degree of priva- cy for users must be balanced against limited access. For example, a service provider might have the list of public keys that correspond to all users that have purchased a single access to some confidential service for that day (re- quiring anonymous authentication). For this kind of application, a number of restricted-use ring signatures are proposed. Notable examples include linkable ring signatures [1, 7, 19, 20, 25, 26] and traceable ring signatures [13, 14]. Linkable ring signature asks that if a user signs any two messages (same or different) with respect to the same ring, then an efficient public procedure can verify that the signer was the same (although the user's identity is not revealed). Traceable ring signature is a ring signature scheme where each message is signed not only with respect to a list of ring members, but also with respect to an issue (e.g., identifying label of a specific election or survey). -

Vulnerability of Blockchain Technologies to Quantum Attacks
Vulnerability of Blockchain Technologies to Quantum Attacks Joseph J. Kearneya, Carlos A. Perez-Delgado a,∗ aSchool of Computing, University of Kent, Canterbury, Kent CT2 7NF United Kingdom Abstract Quantum computation represents a threat to many cryptographic protocols in operation today. It has been estimated that by 2035, there will exist a quantum computer capable of breaking the vital cryptographic scheme RSA2048. Blockchain technologies rely on cryptographic protocols for many of their essential sub- routines. Some of these protocols, but not all, are open to quantum attacks. Here we analyze the major blockchain-based cryptocurrencies deployed today—including Bitcoin, Ethereum, Litecoin and ZCash, and determine their risk exposure to quantum attacks. We finish with a comparative analysis of the studied cryptocurrencies and their underlying blockchain technologies and their relative levels of vulnerability to quantum attacks. Introduction exist to allow the legitimate owner to recover this account. Blockchain systems are unlike other cryptosys- tems in that they are not just meant to protect an By contrast, in a blockchain system, there is no information asset. A blockchain is a ledger, and as central authority to manage users’ access keys. The such it is the asset. owner of a resource is by definition the one hold- A blockchain is secured through the use of cryp- ing the private encryption keys. There are no of- tographic techniques. Notably, asymmetric encryp- fline backups. The blockchain, an always online tion schemes such as RSA or Elliptic Curve (EC) cryptographic system, is considered the resource— cryptography are used to generate private/public or at least the authoritative description of it. -
Proof of 'X' and Hash Functions Used
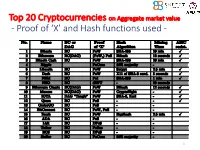
Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 1 ISI Kolkata BlockChain Workshop, Nov 30th, 2017 CRYPTOGRAPHY with BlockChain - Hash Functions, Signatures and Anonymization - Hiroaki ANADA*1, Kouichi SAKURAI*2 *1: University of Nagasaki, *2: Kyushu University Acknowledgements: This work is supported by: Grants-in-Aid for Scientific Research of Japan Society for the Promotion of Science; Research Project Number: JP15H02711 Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 3 Table of Contents 1. Cryptographic Primitives in Blockchains 2. Hash Functions a. Roles b. Various Hash functions used for Proof of ‘X’ 3. Signatures a. Standard Signatures (ECDSA) b. Ring Signatures c. One-Time Signatures (Winternitz) 4. Anonymization Techniques a. Mixing (CoinJoin) b. Zero-Knowledge proofs (zk-SNARK) 5. Conclusion 4 Brief History of Proof of ‘X’ 1992: “Pricing via Processing or Combatting Junk Mail” Dwork, C. and Naor, M., CRYPTO ’92 Pricing Functions 2003: “Moderately Hard Functions: From Complexity to Spam Fighting” Naor, M., Foundations of Soft. Tech. and Theoretical Comp. Sci. 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 5 Brief History of Proof of ‘X’ 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 2012: “Peercoin” Proof of Stake (& Proof of Work) ~ : Delegated Proof of Stake, Proof of Storage, Proof of Importance, Proof of Reserves, Proof of Consensus, ... 6 Proofs of ‘X’ 1. Proof of Work 2. Proof of Stake Hash-based Proof of ‘X’ 3. Delegated Proof of Stake 4. Proof of Importance 5. -

Mechanics of Mobilecoin: First Edition
Mechanics of MobileCoin: First Edition exploring the foundations of a private digital currency April 6, 2021, Preview (10/11) v0.0.39 koe1,2 DRAFT INFORMATION: This is just a draft, and may not always be available wher- ever it is currently hosted. The final version will be available at https://github.com/ mobilecoinfoundation. License: `Mechanics of MobileCoin: First Edition' is released into the public domain. 1 [email protected] 2 Author `koe' worked on this document as part of a private contract with, then as an employee of, MobileCoin, Inc. Abstract Cryptography. It may seem like only mathematicians and computer scientists have access to this obscure, esoteric, powerful, elegant topic. In fact, many kinds of cryptography are simple enough that anyone can learn their fundamental concepts. It is common knowledge that cryptography is used to secure communications, whether they be coded letters or private digital interactions. Another application is in so-called cryptocurrencies. These digital moneys use cryptography to assign and transfer ownership of funds. To ensure that no piece of money can be duplicated or created at will, cryptocurrencies usually rely on `blockchains', which are public, distributed ledgers containing records of currency transactions that can be verified by third parties [115]. It might seem at first glance that transactions need to be sent and stored in plain text format to make them publicly verifiable. In truth, it is possible to conceal a transaction's participants, as well as the amounts involved, using cryptographic tools that nevertheless allow transactions to be verified and agreed upon by observers [151]. This is exemplified in the cryptocurrency MobileCoin. -

Blocksci: Design and Applications of a Blockchain Analysis Platform
BlockSci: Design and applications of a blockchain analysis platform Harry Kalodner Steven Goldfeder Alishah Chator [email protected] [email protected] [email protected] Princeton University Princeton University Johns Hopkins University Malte Möser Arvind Narayanan [email protected] [email protected] Princeton University Princeton University ABSTRACT to partition eectively. In fact, we conjecture that the use of a tra- Analysis of blockchain data is useful for both scientic research ditional, distributed transactional database for blockchain analysis and commercial applications. We present BlockSci, an open-source has innite COST [5], in the sense that no level of parallelism can software platform for blockchain analysis. BlockSci is versatile in outperform an optimized single-threaded implementation. its support for dierent blockchains and analysis tasks. It incorpo- BlockSci comes with batteries included. First, it is not limited rates an in-memory, analytical (rather than transactional) database, to Bitcoin: a parsing step converts a variety of blockchains into making it several hundred times faster than existing tools. We a common, compact format. Currently supported blockchains in- describe BlockSci’s design and present four analyses that illustrate clude Bitcoin, Litecoin, Namecoin, and Zcash (Section 2.1). Smart its capabilities. contract platforms such as Ethereum are outside our scope. Second, This is a working paper that accompanies the rst public release BlockSci includes a library of useful analytic and visualization tools, of BlockSci, available at github.com/citp/BlockSci. We seek input such as identifying special transactions (e.g., CoinJoin) and linking from the community to further develop the software and explore addresses to each other based on well-known heuristics (Section other potential applications.