Design of a WBEM-Based Management System for Ubiquitous Computing Servers
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Megaraid 6Gb/S SAS RAID Controllers Users Guide
USER’S GUIDE MegaRAID® 6Gb/s SAS RAID Controllers November 2009 41450-02 Rev. B This document contains proprietary information of LSI Corporation. The information contained herein is not to be used by or disclosed to third parties without the express written permission of an officer of LSI Corporation. LSI products are not intended for use in life-support appliances, devices, or systems. Use of any LSI product in such applications without written consent of the appropriate LSI officer is prohibited. Purchase of I2C components of LSI Corporation, or one of its sublicensed Associated Companies, conveys a license under the Philips I2C Patent Rights to use these components in an I2C system, provided that the system conforms to the I2C standard Specification as defined by Philips. Document 41450-02 Rev. B, November 2009. This document describes the current versions of the LSI Corporation MegaRAID® SAS RAID controllers and will remain the official reference source for all revisions/releases of these products until rescinded by an update. LSI Corporation reserves the right to make changes to any products herein at any time without notice. LSI does not assume any responsibility or liability arising out of the application or use of any product described herein, except as expressly agreed to in writing by LSI; nor does the purchase or use of a product from LSI convey a license under any patent rights, copyrights, trademark rights, or any other of the intellectual property rights of LSI or third parties. Copyright © 2009 by LSI Corporation. All rights reserved. TRADEMARK ACKNOWLEDGMENT LSI, the LSI logo design, Fusion-MPT, and MegaRAID are trademarks or registered trademarks of LSI Corporation. -

An Adaptive Policy Based Framework for Network Management
Department of Computing Imperial College London University of London An Adaptive Policy Based Framework for Network Management Leonidas A. Lymberopoulos A thesis submitted in partial fulfilment of the requirements for the degree of Doctor of Philosophy in the Faculty of Engineering of the University of London, and for the Diploma of the Imperial College London London, October 2004 Στους γονείς µου, Αντρέα και Γεωργία To my parents, Andreas and Georgia Abstract Policy-based management has emerged as a promising solution for the management of large-scale and heterogeneous networks. This approach has been adopted in several network management areas, such as in the areas of Quality of Service (QoS) and security management. However, although policy-based management has been the subject of considerable research, proposed solutions are often restricted to static condition-action rules where conditions determine when actions should be performed on the managed entities. The static policy configurations require manual intervention to cater for configuration changes and to enable policy deployment. However, changes in the system such as QoS violations, network failures or denial of service attacks in a secured network may require adaptation of existing policies to new circumstances. Thus, policies themselves need to be managed and adapted. Policies define management strategies for network devices, access control systems or internet services. However, little work has been done on validating whether the policies will lead to a feasible implementation for the specific environment to which they apply. Validation requires checking that the policy is consistent with the functional or resource constraints within the target environment. For example, one can check whether the policies assume functionality or specific operations, which do not exist in target devices, or bandwidth in excess of the capacity of data links. -

Architecture of Network Management Tools for Heterogeneous System
(IJCSIS) International Journal of Computer Science and Information Security, Vol. 6, No. 3, 2009 Architecture of Network Management Tools for Heterogeneous System Rosilah Hassan, Rozilawati Razali, Shima Mohseni, Ola Mohamad and Zahian Ismail Department of Computer Science, Faculty of Information Science and Technology Universiti Kebangsaan Malaysia, Bangi, Selangor, Malaysia . Human: where human manager defines the policy and organization approaches. Abstract— Managing heterogeneous network systems is Methodology: defines the architectural a difficult task because each of these networks has its own curious management system. These networks framework and the functions to be usually are constructed on independent management performed. protocols which are not compatible with each other. Instrumentation: the actual operational This results in the coexistence of many management aspects that establish the procedures, systems with different managing functions and services methods and algorithms for data collection, across enterprises. Incompatibility of different processing and reporting, and analysis of management systems makes management of whole problems, their repair, prediction or system a very complex and often complicated job. forecasting of service levels and probable Ideally, it is necessary to implement centralized meta- level management across distributed heterogeneous improvements to enhance performance. systems and their underlying supporting network systems where the information flow and guidance is S&NM aims to provide network -

Monitoring Windows with Powershell
Monitoring Windows Systems with PowerShell SL1 version 8.14.0 Table of Contents Introduction 4 Monitoring Windows Devices in the ScienceLogic Platform 5 What is SNMP? 5 What is PowerShell? 5 PowerPacks 6 Configuring Windows Systems for Monitoring with SNMP 7 Configuring SNMP for Windows Server 2016 and Windows Server 2012 8 Configuring Ping Responses 8 Installing the SNMP Service 9 Configuring the SNMP Service 14 Configuring the Firewall to Allow SNMP Requests 19 Configuring Device Classes for Windows Server 2016 and Windows 10 19 Manually Align the Device Class 20 Edit the Registry Key 20 Configuring SNMP for Windows Server 2008 21 Configuring Ping Responses 21 Installing the SNMP Service 22 Configuring the SNMP Service 25 Configuring the Firewall to Allow SNMP Requests 30 Configuring Windows Servers for Monitoring with PowerShell 31 Prerequisites 32 Configuring PowerShell 32 Step 1: Configuring the User Account for the ScienceLogic Platform 33 Option 1: Creating an Active Directory Account with Administrator Access 33 Option 2: Creating a Local User Account with Administrator Access 34 Option 3: Creating a Non-Administrator User Account 34 Optional: Configuring the User Account for Remote PowerShell Access to Microsoft Exchange Server 36 Optional: Configuring the User Account for Remote PowerShell Access to Hyper-V Servers 36 Creating a User Group and Adding a User in Active Directory 36 Setting the Session Configuration Parameters and Group Permissions 37 Creating a PowerShell Credential 38 Optional: Configuring the User Account for -

Network Management
Chapter 12: Network Management Jian Ren and Tongtong Li, Michigan State University Introduction 2 Network Scanners . 25 OSI Network Management Model . .3 Packet Filters . 26 Network Management Layers . .4 Wireless Network Management 26 ISO Network Management Functions 6 Cellular Networks . 27 Configuration Management . .6 Location Management for Cellular Fault Management . .6 Networks . 28 Security Management . .7 Accounting Management . .7 Policy-based Network Management 29 What Is a Policy? . 30 Performance Management . .7 Benefits of PBNM . 31 Network Management Protocols 7 Architecture of a PBNM System . 31 SNMP/SNMPv1 . .8 Conclusion 32 SNMPv2 . 13 SNMPv3 . 15 Glossary 33 Remote Network Monitoring (RMON) 23 Acknowledgements 34 Network Management Tools 24 Network Monitors . 25 Acronyms 37 Abstract: The continuous growth in scale and diversity of computer networks and network components has made network management one of the most challenging issues facing network administrators. It has become impossible to carry out network management functions without the support of automated tools and applications. In this chapter, the major network management issues, including network management requirements, functions, techniques, security, some well- known network management protocols and tools, will be discussed. Location management for the wireless cellular networks will also be briefly described. Finally, policy-based network management, which is a promising direction for the next generation of network management, will be briefly described. Keywords: -

Govt Linux Appreciation Day 09/18/01
John Terpstra Vice President, Technology Caldera International, Inc. The Maturation of Linux Are we there yet? Slide 2 The Road to Maturity . Self-Discipline . Acceptance of Responsibility . Accountability for Actions Slide 3 MarketMarket Share 1999 Worldwide Market for Server Operating Environments N = 5.475 Million Shipments Other NOS Netware 2.6% 19.4% NT Server 38.1% Unix & Linux 39.9% Source: IDC Slide 4 Linux Server Applications Primary Function of Linux Servers Installed at U.S. Sites, 1999 Web Server 42.1% Overwhelming File/Print Server 26.0% appeal as a Web Email Server 23.2% DNS 15.3% server – over 50% Firewall/Proxy/Cache 14.7% of all Internet Internet/Intranet Server 12.6% Web Servers run Database 10.5% on Apache and Application Development 8.4% Application server 6.3% 60% of all Apache Experimental/Testing 6.3% Servers run on Router/Gateway 5.8% Linux Networking 2.6% Systems Mgmt. 2.1% Backup 2.1% VPN 1.6% Technical Apps 1.1% Other 1.1% 0% 10% 20% 30% 40% 50% Source: IDC N=195 Slide 5 Where Are We? 1. File and Print – 10 Million servers - Major application - Samba 2. Web Serving – 18 Million servers - Major application - Apache 3. Proxy Serving - - Major application – Squid Linux plays a major role hosting each application Slide 6 A Competitive View – Then http://www.microsoft.com/windows/serverappliance/kempin.asp Date: Nov 9, 2000 But it is true that Linux are actually rapidly increasing their market share in the US also. Doesn't this pose a threat? "Linux is simply a fad that has been generated by the media and is destined to fall by the wayside in time. -

Netiq® Cloudaccess and Mobileaccess Installation and Configuration Guide
NetIQ® CloudAccess and MobileAccess Installation and Configuration Guide September 2014 www.netiq.com/documentation Legal Notice THIS DOCUMENT AND THE SOFTWARE DESCRIBED IN THIS DOCUMENT ARE FURNISHED UNDER AND ARE SUBJECT TO THE TERMS OF A LICENSE AGREEMENT OR A NON-DISCLOSURE AGREEMENT. EXCEPT AS EXPRESSLY SET FORTH IN SUCH LICENSE AGREEMENT OR NON-DISCLOSURE AGREEMENT, NETIQ CORPORATION PROVIDES THIS DOCUMENT AND THE SOFTWARE DESCRIBED IN THIS DOCUMENT "AS IS" WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESS OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. SOME STATES DO NOT ALLOW DISCLAIMERS OF EXPRESS OR IMPLIED WARRANTIES IN CERTAIN TRANSACTIONS; THEREFORE, THIS STATEMENT MAY NOT APPLY TO YOU. For purposes of clarity, any module, adapter or other similar material ("Module") is licensed under the terms and conditions of the End User License Agreement for the applicable version of the NetIQ product or software to which it relates or interoperates with, and by accessing, copying or using a Module you agree to be bound by such terms. If you do not agree to the terms of the End User License Agreement you are not authorized to use, access or copy a Module and you must destroy all copies of the Module and contact NetIQ for further instructions. This document and the software described in this document may not be lent, sold, or given away without the prior written permission of NetIQ Corporation, except as otherwise permitted by law. Except as expressly set forth in such license agreement or non-disclosure agreement, no part of this document or the software described in this document may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, or otherwise, without the prior written consent of NetIQ Corporation. -

SCO Office MAIL SERVER
SCO_office_DS2.qxd 1/8/03 9:21 AM Page 1 SCOoffice MAIL SERVER SCOoffice Mail Server combines the Microsoft Outlook® compatibility users need with the built-in reliability and ease of use customers expect, and is priced at a fraction of the cost of Microsoft Exchange™. The result is a rock solid, affordable, and complete mail and collaboration solution. COMPATIBLE SCOoffice MAIL SERVER 2.0 FEATURES SCOoffice Mail Server is specifically designed to COMPATIBLE be compatible with Microsoft Outlook and other popular • Advanced, scalable, full-featured Internet mail server mail clients. It comes pre-configured to support mail, enhanced address book, and busy-free calendar features of • Supports Internet standard email protocols including popular messaging readers. As a result, businesses can deliver SMTP, POP3, and IMAP4 complete messaging and time management without any user • Supports popular mail clients, including Microsoft Outlook retraining or desktop software updates. 2000, Outlook XP, Outlook 98, Outlook Express, Eudora, When used with Microsoft Outlook, SCOoffice Mail Server Netscape Communicator 4.7, Kmail and others adds essential collaboration with shared calendar, folders, and • Internet Messaging Program (IMP) web-based email client global address book features. Further, the simple Outlook for complete web-based mail interface enables users to quickly set up shared resources • Free/Busy calendaring services for Microsoft Outlook and without technical assistance. Ximian Evolution • Integrates with popular third-party virus filtering tools RELIABLE • Supports well known and trusted commercial solutions for Known worldwide for providing key infrastructure for the backup, FAX messaging, and virus protection day-to-day business operations of internationally recognized • Support remote, sometimes connected clients via IMAP4 organizations, such as McDonald’s and NASDAQ, SCO has and Web-based Mail Client built its reputation around the reliability of its software. -

Z/OS Common Information Model User's Guide for Version 2 Release 4 (V2R4)
z/OS 2.4 Common Information Model User's Guide IBM SC34-2671-40 Note Before using this information and the product it supports, read the information in “Notices” on page 335. This edition applies to Version 2 Release 4 of z/OS (5650-ZOS) and to all subsequent releases and modifications until otherwise indicated in new editions. Last updated: 2021-04-26 © Copyright International Business Machines Corporation 2005, 2021. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Figures................................................................................................................. xi Tables................................................................................................................ xiii Abstract.............................................................................................................. xv How to send your comments to IBM.................................................................... xvii If you have a technical problem............................................................................................................... xvii z/OS information................................................................................................ xix Summary of changes...........................................................................................xxi Summary of changes for z/OS Common Information Model User's Guide for Version 2 Release 4 (V2R4)...................................................................................................................................................xxi -

Open Virtualization Format Specification
1 2 Document Number: DSP0243 3 Date: 2013-12-12 4 Version: 2.1.0 5 Open Virtualization Format Specification 6 Document Type: Specification 7 Document Status: DMTF Standard 8 Document Language: en-US Open Virtualization Format Specification DSP0243 9 Copyright notice 10 Copyright © 2010-2013 Distributed Management Task Force, Inc. (DMTF). All rights reserved. 11 DMTF is a not-for-profit association of industry members dedicated to promoting enterprise and systems 12 management and interoperability. Members and non-members may reproduce DMTF specifications and 13 documents, provided that correct attribution is given. As DMTF specifications may be revised from time to 14 time, the particular version and release date should always be noted. 15 Implementation of certain elements of this standard or proposed standard may be subject to third party 16 patent rights, including provisional patent rights (herein "patent rights"). DMTF makes no representations 17 to users of the standard as to the existence of such rights, and is not responsible to recognize, disclose, 18 or identify any or all such third party patent right, owners or claimants, nor for any incomplete or 19 inaccurate identification or disclosure of such rights, owners or claimants. DMTF shall have no liability to 20 any party, in any manner or circumstance, under any legal theory whatsoever, for failure to recognize, 21 disclose, or identify any such third party patent rights, or for such party’s reliance on the standard or 22 incorporation thereof in its product, protocols or testing procedures. DMTF shall have no liability to any 23 party implementing such standard, whether such implementation is foreseeable or not, nor to any patent 24 owner or claimant, and shall have no liability or responsibility for costs or losses incurred if a standard is 25 withdrawn or modified after publication, and shall be indemnified and held harmless by any party 26 implementing the standard from any and all claims of infringement by a patent owner for such 27 implementations. -

Case COMP/C-3/37.792 Microsoft)
EN EN EN COMMISSION OF THE EUROPEAN COMMUNITIES Brussels, 21.4.2004 C(2004)900 final COMMISSION DECISION of 24.03.2004 relating to a proceeding under Article 82 of the EC Treaty (Case COMP/C-3/37.792 Microsoft) (ONLY THE ENGLISH TEXT IS AUTHENTIC) (Text with EEA relevance) EN EN COMMISSION DECISION of 24.03.2004 relating to a proceeding under Article 82 of the EC Treaty (Case COMP/C-3/37.792 Microsoft) (ONLY THE ENGLISH TEXT IS AUTHENTIC) (Text with EEA relevance) THE COMMISSION OF THE EUROPEAN COMMUNITIES, Having regard to the Treaty establishing the European Community, Having regard to Council Regulation No 17 of 6 February 1962, First Regulation implementing Articles 85 and 86 of the Treaty1, and in particular Article 3 and Article 15(2) thereof, Having regard to the complaint lodged by Sun Microsystems, Inc. on 10 December 1998, alleging infringements of Article 82 of the Treaty by Microsoft and requesting the Commission to put an end to those infringements, Having regard to the Commission decision of 1 August 2000 to initiate proceedings in Case IV/C-3/37.345, Having regard to the Commission decision of 29 August 2001 to initiate proceedings in this case, and to join the findings in Case IV/C-3/37.345 to the procedure followed under this case, Having given the undertaking concerned the opportunity to make known their views on the objections raised by the Commission pursuant to Article 19(1) of Regulation No 17 and Commission Regulation (EC) No 2842/98 of 22 December 1998 on the hearing of parties in certain proceedings under Articles 85 and 86 of the EC Treaty2, Having regard to the final report of the hearing officer in this case, After consulting the Advisory Committee on Restrictive Practices and Dominant Positions, 1 OJ 13, 21.2.1962, p. -
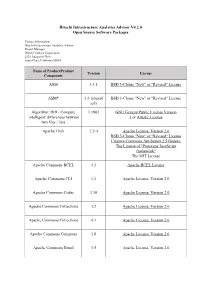
Hitachi Infrastructure Analytics Advisor V4.2.0 Open Source Software Packages
Hitachi Infrastructure Analytics Advisor V4.2.0 Open Source Software Packages Contact Information: Hitachi Infrastructure Analytics Advisor Project Manager Hitachi Vantara Corporation 2535 Augustine Drive Santa Clara, California 95054 Name of Product/Product Version License Component ASM 3.3.1 BSD 3-Clause "New" or "Revised" License ASM* 3.3.1(modif BSD 3-Clause "New" or "Revised" License ied) Algorithm::Diff - Compute 1.1903 GNU General Public License Version `intelligent' differences between 1 or Artistic License two files / lists Apache Click 2.3.0 Apache License, Version 2.0 BSD 3-Clause "New" or "Revised" License Creative Commons Attribution 2.5 Generic The License of "Prototype JavaScript framework" The MIT License Apache Commons BCEL 5.1 Apache BCEL License Apache Commons CLI 1.1 Apache License, Version 2.0 Apache Commons Codec 1.10 Apache License, Version 2.0 Apache Commons Collections 3.2 Apache License, Version 2.0 Apache Commons Collections 4.1 Apache License, Version 2.0 Apache Commons Compress 1.0 Apache License, Version 2.0 Apache Commons Email 1.5 Apache License, Version 2.0 Name of Product/Product Version License Component Apache HTTP Server 2.4.34 Apache License, Version 2.0 BSD 3-Clause "New" or "Revised" License GNU General Public License, Version 3 with Autoconf exception Public Domain or Free License without conditions The License by "Bell Communications Research, Inc. (Bellcore)" The License by "Carnegie Mellon University" The License by "RSA Data Security, Inc." The License of "RSA Data Security, Inc. MD4 Message-Digest Algorithm" The License of "RSA Data Security, Inc.