Research Collection
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

SOA Using Open ESB, BPEL, and Netbeans” > Focus Is to Explain How WSDL, BPEL, JBI, Open ESB, Java EE Work Together
SSOOAA uussiinngg OOppeenn EESSBB,, BBPPEELL,, aanndd NNeettBBeeaannss SSaanngg SShhiinn JJaavvaa TTeecchhnnoollooggyy EEvvaannggeelliisstt SSuunn MMiiccrroossyysstteemmss,, IInncc.. 1 Three Talks I Did on SOA Here • NetBeans Day: “Tools for Simplifying SOA” > Focus is to show how to use NetBeans for building a simple Composite application • GlassFish Day: “Open ESB and GlassFish” > Focus is to show more advanced features such as Intelligent Event Processing module for building a composite application • Sun Tech Day: “SOA using Open ESB, BPEL, and NetBeans” > Focus is to explain how WSDL, BPEL, JBI, Open ESB, Java EE work together 2 Agenda • Composite Applications • BPEL • Services • JBI • Java EE Service Engine • Open ESB • Open ESB runtime, tools, and sample apps • Demo 3 CCoommppoossiittee AApppplliiccaattiioonnss Traditional Application Development • Point technologies, products, and APIs > For example: EJB, Spring, Hibernate, JSF, Servlets, Struts, etc. • Lots of glue written by developers > Requires a great deal of expertise & time > Inflexible 5 Composite Applications • A way to compose applications from reusable parts • Composite applications employ SOA principles > Features exposed as Web services > Standards-based interaction between services > Are themselves composable 6 WWSSDDLL TTuuttoorriiaall ((OOppttiioonnaall PPrreesseennttaattiioonn)) Why WSDL? • Enables automation of communication details between communicating partners – Machines can read WSDL – Machines can invoke a service defined in WSDL • Discoverable through registry -

Refactoring of ESB-Based Systems on the Clouds
UNIVERSITYOFTARTU FACULTY OF MATHEMATICS AND COMPUTER SCIENCE Institute of Computer Science Mariana Kukhtyn Refactoring of ESB-based systems on the clouds Master's thesis (30 ECTS) Supervisor: Satish Srirama, Ph.D. Author: .......................................... \....." June 2011 Supervisor: .................................... \....." June 2011 Professor: ...................................... \....." June 2011 TARTU 2011 `The one thing that matters is the effort. It continues, whereas the end to be attained is but an illusion of the climber, as he fares on and on from crest to crest; and once the goal is reached it has no meaning." Antoine de Saint-Exupry, The Wisdom of the Sands UNIVERSITY OF TARTU Abstract Faculty of Mathematics and Computer Science Institute of Computer Science Master of Science Refactoring of ESB-based systems on the cloud by Mariana Kukhtyn Nowadays enterprises are facing new, unprecedented press for competitiveness: the speed of service providing, price of inaccuracy, possibility to use applications from desktops, notes and other mobile devices. These new conditions force business to search for addi- tional resources and configurations for providing better services. Thus, we are arguing to find general hints for uniting enterprises, cloud computing and distributed middleware software in one system in order to fulfill this goal. ESB-based systems and Service Oriented Architecture taken as one of its cases are as- sessed in concern to their possible aplication and profit-usage on the remote servers. In this work, for the first time different vision of distributed ESB-systems (Federated, In- ternet and proper Distributed) are described, prooving that idea is not new but different research groups focus on different features. Statistics data on cloud application is used to object widely-spread statements on cloud security and finance-efficiency. -

Survey on the Run-Time Systems of Enterprise Application Integration Platforms Focusing on Performance
Received: 11 September 2018 Revised: 10 November 2018 Accepted: 14 November 2018 DOI: 10.1002/spe.2670 SURVEY PAPER Survey on the run-time systems of enterprise application integration platforms focusing on performance Daniela L. Freire Rafael Z. Frantz Fabricia Roos-Frantz Sandro Sawicki Department of Exact Sciences and Engineering, Unijuí University, Ijuí-RS, Summary Brazil Companies are taking advantage of cloud computing to upgrade their business Correspondence processes. Cloud computing requires interaction with many kinds of applica- Rafael Z. Frantz, Department of Exact tions, so it is necessary to improve the performance of software tools that allow Sciences and Engineering, Unijuí keeping information on all these applications consistent and synchronised. Inte- University, Ijuí-RS 98700-000, Brazil. Email: [email protected] gration platforms are specialised software tools that provide support to design, implement, run, and monitor integration solutions, which aim to orchestrate a Funding information Coordenação de Aperfeiçoamento de set of applications so as to promote compatibility among their data or to develop Pessoal de Nível Superior, Grant/Award new functionality on top of the current ones. The run-time system is the part Number: 73318345415 and of the integration platform responsible for running the integration solutions, 88881.119518/2016-01; Fundação de Amparo à Pesquisa do Estado do Rio which makes its performance the uttermost important issue. The contribution Grande do Sul, Grant/Award Number: of this article is two-fold: a framework and an evaluation of integration plat- 17/2551-0001206-2 forms. The former is a framework composed of ten properties grouped into two dimensions to evaluate the run-time systems focusing on performance. -

Focus on Apache Camel 23 3.1 Classification
Institute of Architecture of Application Systems University of Stuttgart Universitätsstraße 38 D–70569 Stuttgart Diploma Thesis No. 3480 Complete Enterprise Topologies with routing information of Enterprise Services Buses to enable Cloud-migration Andre Grund Course of Study: Software Engineering Examiner: Prof. Dr. Frank Leymann Supervisor: Dipl.-Inf. Tobias Binz Commenced: May 01, 2013 Completed: October 28, 2013 CR-Classification: E.1, K.6 Abstract The Enterprise Service Bus is an important part of todays enterprise IT landscape. It offers the integration of applications build on different platforms without adaptation. This is accomplished by offering message transformation and routing capabilities of client requests to the designated endpoint service. However, Enterprise Service Buses also introduce an additional indirection between the client and the called backend application. Enterprise Topology Graphs capture a snapshot of the whole enterprise IT and are used in various use cases for analysis, migration, adaptation, and optimization of IT. The focus of this work is to enhance the ETG model with structural and statistical information about an enterprise. However, due to the decoupled architecture the information is hidden inside the ESB and not directly accessible. Furthermore, the arrangement and semantics of the routing entities are unknown. The existing ETG Framework includes the automated discovery and maintenance of ETGs, but offers no solution for ESB components in the enterprise IT. This thesis provides an in depth analysis of the ESBs Apache Camel and Apache Synapse. It applies information gathering concepts and evaluate them with a prototypical implementation of an ETG Framework plugin. Using tailored information gathering and presentation methods to enhance ETGs with routing information. -

Talend Open Studio for Big Data Release Notes
Talend Open Studio for Big Data Release Notes 6.0.0 Talend Open Studio for Big Data Adapted for v6.0.0. Supersedes previous releases. Publication date July 2, 2015 Copyleft This documentation is provided under the terms of the Creative Commons Public License (CCPL). For more information about what you can and cannot do with this documentation in accordance with the CCPL, please read: http://creativecommons.org/licenses/by-nc-sa/2.0/ Notices Talend is a trademark of Talend, Inc. All brands, product names, company names, trademarks and service marks are the properties of their respective owners. License Agreement The software described in this documentation is licensed under the Apache License, Version 2.0 (the "License"); you may not use this software except in compliance with the License. You may obtain a copy of the License at http://www.apache.org/licenses/LICENSE-2.0.html. Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License. This product includes software developed at AOP Alliance (Java/J2EE AOP standards), ASM, Amazon, AntlR, Apache ActiveMQ, Apache Ant, Apache Avro, Apache Axiom, Apache Axis, Apache Axis 2, Apache Batik, Apache CXF, Apache Cassandra, Apache Chemistry, Apache Common Http Client, Apache Common Http Core, Apache Commons, Apache Commons Bcel, Apache Commons JxPath, Apache -
SOA and Open Source
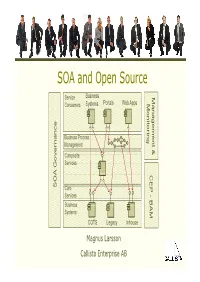
SOA and Open Source Service Business Ma Consumers Systems Portals Web Apps M nageme onitorin g ance Business Process n nn Management t & Composite Services Gover CEP -CEP B AA SO Core Services Business AM Systems COTS Legacy Inhouse Magnus Larsson Callista Enterprise AB Vendor support of Open Source SOA • Vendors provide services for training, consulting and support on selected Open Source SOA products • MuleSource – Over 1000 mission-critical production installations worldwide! – http:// www.mu lesou rce .co m/custo me rs/casestud ies .p hp •WSO2 – http://wso2.com/about/whitepapers/ • Progress FUSE – http://fusesource.com/resources/collateral/ SOA and Open Source Copyright 2009, Callista Enterprise AB Building a SOA Reference Model… Service Business Portals Web Apps Consumers Systems Business Systems COTS Legacy Inhouse SOA and Open Source Copyright 2009, Callista Enterprise AB Building a SOA Reference Model… • Connectivity Service Business - SOAP, Rest, Messaging, Database, FTP… Portals Web Apps Consumers Systems • Transformation - XML, CSV, Fixed Position… • Routing - Header and/or Content based • Enterprise Integration Patterns - Splitting, Aggregation, Resequencing… Core Services Business Systems COTS Legacy Inhouse SOA and Open Source Copyright 2009, Callista Enterprise AB Building a SOA Reference Model… Composite Services Service Business Portals Web Apps Consumers Systems ‐ Course Grained ‐ Internal Messaging High performance access to other services CitComposite Services Core Services Business Systems COTS Legacy Inhouse SOA -

Return of Organization Exempt from Income
OMB No. 1545-0047 Return of Organization Exempt From Income Tax Form 990 Under section 501(c), 527, or 4947(a)(1) of the Internal Revenue Code (except black lung benefit trust or private foundation) Open to Public Department of the Treasury Internal Revenue Service The organization may have to use a copy of this return to satisfy state reporting requirements. Inspection A For the 2011 calendar year, or tax year beginning 5/1/2011 , and ending 4/30/2012 B Check if applicable: C Name of organization The Apache Software Foundation D Employer identification number Address change Doing Business As 47-0825376 Name change Number and street (or P.O. box if mail is not delivered to street address) Room/suite E Telephone number Initial return 1901 Munsey Drive (909) 374-9776 Terminated City or town, state or country, and ZIP + 4 Amended return Forest Hill MD 21050-2747 G Gross receipts $ 554,439 Application pending F Name and address of principal officer: H(a) Is this a group return for affiliates? Yes X No Jim Jagielski 1901 Munsey Drive, Forest Hill, MD 21050-2747 H(b) Are all affiliates included? Yes No I Tax-exempt status: X 501(c)(3) 501(c) ( ) (insert no.) 4947(a)(1) or 527 If "No," attach a list. (see instructions) J Website: http://www.apache.org/ H(c) Group exemption number K Form of organization: X Corporation Trust Association Other L Year of formation: 1999 M State of legal domicile: MD Part I Summary 1 Briefly describe the organization's mission or most significant activities: to provide open source software to the public that we sponsor free of charge 2 Check this box if the organization discontinued its operations or disposed of more than 25% of its net assets. -

Architecture of Mule and Servicemix 42 3 ■ Setting up the Mule and Servicemix Environments 72 4 ■ the Foundation of an Integration Solution 111
Open Source ESBs in Action Open Source ESBs in Action EXAMPLE IMPLEMENTATIONS IN MULE AND SERVICEMIX TIJS RADEMAKERS JOS DIRKSEN MANNING Greenwich (74° w. long.) For online information and ordering of this and other Manning books, please visit www.manning.com. The publisher offers discounts on this book when ordered in quantity. For more information, please contact: Special Sales Department Manning Publications Co. Sound View Court 3B Fax: (609) 877-8256 Greenwich, CT 06830 Email: [email protected] ©2009 by Manning Publications Co. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by means electronic, mechanical, photocopying, or otherwise, without prior written permission of the publisher. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in the book, and Manning Publications was aware of a trademark claim, the designations have been printed in initial caps or all caps. Recognizing the importance of preserving what has been written, it is Manning’s policy to have the books we publish printed on acid-free paper, and we exert our best efforts to that end. Recognizing also our responsibility to conserve the resources of our planet, Manning books are printed on paper that is at least 15% recycled and processed elemental chlorine-free Development Editor: Jeff Bleil Manning Publications Co. Copyeditors: Liz Welch, Tiffany Taylor Sound View Court 3B Typesetter: Denis -

Proof of Concept Implementation of an Enterprise Service Bus for Health Information Exchanges
PHILIPPINE ENGINEERING JOURNAL PC Zuñiga, et al 49 PEJ 2020; Vol. 41, No. 1: 49-66 Proof of Concept Implementation of an Enterprise Service Bus for Health Information Exchanges Philip Christian Zuniga, Joseph Benjamin Del Mundo, Edgardo Felizmenio, Marie Jo-anne Mendoza and Rose Ann Zuniga Computer Security Group, Department of Computer Science, University of the Philippines - Diliman Abstract – Integration of health systems is one of the biggest problem in eHealth today. There are a lot of systems, yet they were developed using different platforms and technologies, making them virtually impossible to connect. In this paper, we discussed how to implement an ESB as the integration platform for health data. We identified use cases and functional requirements. Logical and deployment architecture were developed, and an actual proof of concept of an ESB is developed. Experiments were also done to determine the overhead caused by the ESB. Some of the functionalities of the ESB were examined to determine their individual overheads. Keywords: Enterprise Service Bus, Interoperability, Health Information Exchange, OpenHIE. I. INTRODUCTION During the past few years, the healthcare industry has witnessed a growth in the development of Health Information Systems. Hospitals, both public and private, rural health clinics, and even individual clinics of medical practitioners have been developing or acquiring their own Electronic Medical Records (EMRs), and Hospital Information Systems (HIS). The goal of these systems is to ensure a secure, organized and effective way of collecting and storing patient data [1]. The increase in the number of edge applications leads to the increase of patient data that are stored separately and independently, depending on the application that collected the data. -

Kuali Student Advanced Camp
Kuali Student Advanced CAMP June 19-20, 2008 Jens Haeusser Director, Strategy Information Technology Objectives . At the end of this session you will have seen . The Kuali Student technical architecture vision . The results of our efforts to date . The working relationships in place to support our efforts Kuali Student – Advanced CAMP June 19-20 2 Agenda . Kuali Student’s Vision . Our vision for Phase I and Phase II (July 2007 – May 2008) . Our execution of the vision . Kuali Student Architecture . Web Services Stack . Development Infrastructure . Our Current Challenges . Relationships with vendors, open source, and Kuali . On the Leading Edge While Remaining Flexible . Getting Validation of Our Work Kuali Student – Advanced CAMP June 19-20 3 Background . Modular, standards-based next generation student system . Community Source project with a 5 year timeline . UBC, Berkeley, Florida, Maryland, San Joaquin Delta, Southern California . MIT, Cambridge . Person centric system . Service Oriented Architecture . Enables integration at diverse institutions . Allows schools to implement their practices Kuali Student – Advanced CAMP June 19-20 4 Functional Vision . Support end users by anticipating their needs . Wide range of learners and learning activities. Wide range of business processes . Easier to change business processes. Reduce time staff spend on routine task Kuali Student – Advanced CAMP June 19-20 5 Technical Vision . SOA and Web Services . SOA Design Methodology . SOA Governance . Web Services: SOAP, WSDL, XML Schema . Web Services -

Towards Distributed Information Access Possibilities and Implementation
Towards Distributed Information Access Possibilities and Implementation Victor de Graaff i ii Towards Distributed Information Access Alternatives and Implementation Master thesis Author: Victor de Graaff University: University of Twente Master: Computer Science Track: Software Engineering Internal Supervisors: Dr. Luís Ferreira Pires Dr. ir. Marten van Sinderen External Supervisors: ing. Gerke Stam, TSi Solutions iii iv Preface This thesis describes the results of a Master of Science assignment at the Software Engineering group at the University of Twente. This assignment has been carried out from February to November 2009 at TSi Solutions in Enschede, The Netherlands. I would like to thank all the people who gave me support while writing this thesis. In the first place these people are my girlfriend Susanne Jeschke and my daughter Melissa. They have supported me through the last piece of my Bachelor and my entire Master course by taking my mind off work every night and weekend, as far as my deadlines allowed them to. They have given me the chance to spend countless hours on my work, my classes, and later my thesis, while they went to all the activities and appointments a young child has. I can truly say that I could never have finished my studies without their support, understanding and patience. Another great influence has been the supervision of Luís Ferreira Pires, Marten van Sinderen and Gerke Stam. Luís managed to keep the balance in my work between quality and steady progress. On top of that, Luís taught me a lot on writing objective texts by rephrasing or pointing out sentences which were subjective or too popular. -

Avaliando a Dívida Técnica Em Produtos De Código Aberto Por Meio De Estudos Experimentais
UNIVERSIDADE FEDERAL DE GOIÁS INSTITUTO DE INFORMÁTICA IGOR RODRIGUES VIEIRA Avaliando a dívida técnica em produtos de código aberto por meio de estudos experimentais Goiânia 2014 IGOR RODRIGUES VIEIRA Avaliando a dívida técnica em produtos de código aberto por meio de estudos experimentais Dissertação apresentada ao Programa de Pós–Graduação do Instituto de Informática da Universidade Federal de Goiás, como requisito parcial para obtenção do título de Mestre em Ciência da Computação. Área de concentração: Ciência da Computação. Orientador: Prof. Dr. Auri Marcelo Rizzo Vincenzi Goiânia 2014 Ficha catalográfica elaborada automaticamente com os dados fornecidos pelo(a) autor(a), sob orientação do Sibi/UFG. Vieira, Igor Rodrigues Avaliando a dívida técnica em produtos de código aberto por meio de estudos experimentais [manuscrito] / Igor Rodrigues Vieira. - 2014. 100 f.: il. Orientador: Prof. Dr. Auri Marcelo Rizzo Vincenzi. Dissertação (Mestrado) - Universidade Federal de Goiás, Instituto de Informática (INF) , Programa de Pós-Graduação em Ciência da Computação, Goiânia, 2014. Bibliografia. Apêndice. Inclui algoritmos, lista de figuras, lista de tabelas. 1. Dívida técnica. 2. Qualidade de software. 3. Análise estática. 4. Produto de código aberto. 5. Estudo experimental. I. Vincenzi, Auri Marcelo Rizzo, orient. II. Título. Todos os direitos reservados. É proibida a reprodução total ou parcial do trabalho sem autorização da universidade, do autor e do orientador(a). Igor Rodrigues Vieira Graduado em Sistemas de Informação, pela Universidade Estadual de Goiás – UEG, com pós-graduação lato sensu em Desenvolvimento de Aplicações Web com Interfaces Ricas, pela Universidade Federal de Goiás – UFG. Foi Coordenador da Ouvidoria da UFG e, atualmente, é Analista de Tecnologia da Informação do Centro de Recursos Computacionais – CERCOMP/UFG.