Kubernetes and Virtualization
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Equity Research
EQUITY RESEARCH May 2021 7 Monthly Highlights FEATURED ARTICLES: DigitalOcean, Inc. 2 Sixth Street Specialty Lending 4 Coverage Universe (as of 4/30/21) 6 Outperform Rated Stocks 20-21 Perform Rated Stocks 22 Not Rated Stocks 23 Initiation of Coverage 24 Rating Changes 24 For analyst certification and important disclosures, see the Disclosure Appendix. Monthly Highlights Oppenheimer & Co Inc. 85 Broad Street, New York, NY 10004 Tel: 800-221-5588 Fax: 212-667-8229 Monthly Highlights May 3, 2021 CLOUD AND COMMUNICATIONS Stock Rating: DigitalOcean, Inc. Outperform 12-18 mo. Price Target $55.00 Pure-Play Public Cloud Platform for SMBs/Developers, DOCN-NASDAQ (4/30/21) $43.57 Initiated Outperform, $55 PT 11% 3-5 Yr. EPS Gr. Rate NA SUMMARY 52-week Range $45.49-$36.65 DigitalOcean is a very successful niche cloud provider, focused on ease of use for Shares Outstanding 127.0M developers and small businesses that need low-cost and easy-to-use cloud computing. The Float 40.0M Avg. Daily Trading Vol. NA cloud gives SMBs/developers flexibility to run applications and store data in a highly secure Market Capitalization $4,588.1M environment that can be accessed from anywhere. Every industry has scale providers and Dividend/Yield NA/NM niche ones. In cloud, AWS and MSFT are the scale providers with DigitalOcean and Fiscal Year Ends Dec Rackspace the niche providers. We believe that DOCN can grow revenues at 30%-plus per Book Value NM year for the next five years. It is turning FCF positive, and these margins should expand by 2021E ROE NA 100-200 basis points per year. -

View Annual Report
Dear Arista Networks Stockholders: I am pleased to report that Arista Networks demonstrated another year of strong execution in 2018, with continued momentum from our cloud customers and expanded business in the enterprise vertical. We are extremely proud of the strategic role that Arista is earning, with a broad set of customers deploying transformative cloud networking. 2018 Highlights: • Revenue for our fiscal year 2018 was $2.15 billion representing an increase of 30.7% from the prior year. We now serve over 5,600 customers, having shipped more than twenty million cloud networking ports worldwide, leveraging EOS our advanced network operating system. • Arista introduced Cognitive Cloud Networking for the campus encompassing a new network architecture designed to address transitional changes as the enterprise moves to an IoT ready campus. • Arista acquired WiFi pioneer Mojo Networks for cloud networking expansion, entering the wireless LAN market with a portfolio of WiFi edge products. • Arista introduced the next generation 400G version of our switch routing platforms with two new 400G fixed systems, delivering increased performance for the growth of applications such as AI (artificial intelligence), machine learning, and serverless computing. • Arista acquired Metamako, a leader in low-latency, FPGA-enabled network solutions. This acquisition plays a key role in the delivery of next generation platforms for low-latency applications. • The Forrester WaveTM Hardware Platforms for SDN, Q1 2018, recognized Arista as a leader in the current offering and strategy categories. • Arista maintained its leadership position in the Gartner July 2018 Magic Quadrant for Data Center Networking for the fourth consecutive year. Looking ahead, we see opportunities in delivering new technologies across our cloud networking and cognitive campus platforms in support of a broader customer base. -

D1.5 Final Business Models
ITEA 2 Project 10014 EASI-CLOUDS - Extended Architecture and Service Infrastructure for Cloud-Aware Software Deliverable D1.5 – Final Business Models for EASI-CLOUDS Task 1.3: Business model(s) for the EASI-CLOUDS eco-system Editor: Atos, Gearshift Security public Version 1.0 Melanie Jekal, Alexander Krebs, Markku Authors Nurmela, Juhana Peltonen, Florian Röhr, Jan-Frédéric Plogmeier, Jörn Altmann, (alphabetically) Maurice Gagnaire, Mario Lopez-Ramos Pages 95 Deliverable 1.5 – Final Business Models for EASI-CLOUDS v1.0 Abstract The purpose of the business working group within the EASI-CLOUDS project is to investigate the commercial potential of the EASI-CLOUDS platform, and the brokerage and federation- based business models that it would help to enable. Our described approach is both ‘top down’ and ‘bottom up’; we begin by summarizing existing studies on the cloud market, and review how the EASI-CLOUDS project partners are positioned on the cloud value chain. We review emerging trends, concepts, business models and value drivers in the cloud market, and present results from a survey targeted at top cloud bloggers and cloud professionals. We then review how the EASI-CLOUDS infrastructure components create value both directly and by facilitating brokerage and federation. We then examine how cloud market opportunities can be grasped through different business models. Specifically, we examine value creation and value capture in different generic business models that may benefit from the EASI-CLOUDS infrastructure. We conclude by providing recommendations on how the different EASI-CLOUDS demonstrators may be commercialized through different business models. © EASI-CLOUDS Consortium. 2 Deliverable 1.5 – Final Business Models for EASI-CLOUDS v1.0 Table of contents Table of contents ........................................................................................................................... -

Lowering AWS Costs with Digitalocean
Lowering AWS Costs with DigitalOcean WHITE PAPER Introduction Since the introduction of cloud computing, businesses have been leveraging dynamic infrastructure to quickly scale without the burden of significant capital expense. According to the Rightscale State of the Cloud 2018 Report, 92% of SMBs leverage cloud solutions and 50% spend more than $10,000 a month. Of these SMBs, 76% plan to spend more in 2018 and 72% say that managing costs is a top challenge with cloud adoption. While many of these businesses use AWS for cloud infrastructure, with 1300 new choices introduced this year according to Datamation, AWS can be difficult to navigate. According to Concurrency Labs the price variations of AWS regions can result in costs that are much higher than expected. These complexities can drive up business costs and lower developer productivity. Rightscale estimates that up to 35% of cloud spend is wasted due to under-utilized or un-optimized cloud resources. DigitalOcean aims to provide an easier cloud platform to deploy, manage, and scale applications of any size, often resulting in savings of up to 67% compared to AWS (see figure 2). DigitalOcean keeps pricing simple by including commonly used resources like storage and bandwidth, and by setting consistent pricing across data center regions. Since 2012 DigitalOcean has been focused on providing the best price-to-performance cloud with a focus on simplicity. By offering cloud compute, storage, and networking products with leading pricing and performance, DigitalOcean helps your business scale while lowering your cloud costs. Typical Cloud Cost Drivers Total Cost of Ownership (TCO) can be difficult to calculate because of AWS’s regional price variations and thousands of product choices. -
Sebastian Witowski
I made a website! Now what? Sebastian Witowski 1 Disclaimer There are many great tools at CERN (OpenShift). This presentation is not about those tools. 2 This presentation is about external tools 3 Free to use Open source Good value/money Good service Supports FOSS/education 4 Hosting 5 Cloud hosting Physical server vs VPS: Billed for real usage (per second on AWS) Easy to scale 6 Hosting providers AWS (EC2 and Amazon Lightsail) Free tier for 1 year (2x t2.micro, 1 DB, 5GB storage, etc.) Complex pricing model DigitalOcean From $5/month (512MB RAM, 20GB storage, 1TB transfer) Additional storage from $0.10/GB/month Linode From $5/month (1GB RAM, 20GB storage, 1TB transfer) Additional storage from $0.10/GB/month Heroku PaaS: more expensive, but easier to use (less congurable) 1 dyno free forever (512 MB RAM, 10k PostgreSQL rows) 7 Server parameters Storage - 20GB is plenty (use AWS S3 for more) Transfer - 1TB is usually more than enough CPU - 1 CPU is ne for simple website RAM - the more the better (caching, DB, etc.) 8 Cloud computing 9 When a VPS is not enough AWS Free tier for 1 year (VPS, DB, S3, Lambda and more) More features than competition Longest time on market == more 3rd party libraries Google Cloud $300 free credits to spend during rst 12 months "Always free" tier with VPS (1 f1-micro, 30GB storage), DB (1GB NoSQL), storage (5 GB), messaging, logging, serverless functions, but also NLP, speech and vision API Azure 30 days free trial with $200 free credits, some services free for 12 months and some free forever Good support for Windows applications 10 Static websites 11 When a VPS is too much GitLab pages Supports any static site generator Free Continuous Integration Slightly more complicated setup GitHub pages Supports only Jekyll (to use other static site generators, you need to precompile les locally) Easy, out-of-the-box setup Both are free and offer separate websites for projects and organizations. -

Digitalocean-Currents-Remote Work Edition
CURRENTS Remote work edition Key findings: Introduction Remote work is the new normal for developers. It's not only something they prefer, but something they increasingly demand from employers. Trends in the developer community move quickly. As a developer-focused Eighty-six percent of respondents currently work remotely in some capacity, company, it's vital to keep up with the technologies and tools developers with nearly 1/3 working from home full time. Forty-three percent say the are interested in so we can help them achieve their goals. ability to work remotely is a must-have when considering an offer with a company. Currents is DigitalOcean’s seasonal report on developer trends that we created to share knowledge with the community. For the sixth edition, we Remote workers are connected. The traditional narrative of remote workers surveyed more than 4,500 developers around the world about remote work as isolated and disengaged from their companies is proving false for many. — including how they work, their experiences working remotely, how they Seventy-one percent of developers who work remotely said they feel connect with the larger community, and how they maintain work-life connected to their company’s community. balance. But the issue hasn’t disappeared entirely. The twenty-nine percent who don’t feel connected say they feel excluded from offline team conversations or don’t feel integrated into their company’s culture when working remotely. The burnout problem is real. Two-thirds of all respondents said their stress levels have caused them to feel burnt out or work fatigued, regardless of whether or not they work remotely. -

Equity Research 388 Companies Under Coverage
Equity Research 388 Companies Under Coverage Financial Services Commercial Finance Consumer Finance & Financial Technology Insurance Investment Banks, Brokers & Alternative Asset Managers Devin Ryan David Scharf Matthew Carletti Devin Ryan (212) 906-3578 (415) 835-8942 (312) 768-1784 (212) 906-3578 Ares Capital Corp. (ARCC) Alliance Data Systems Corp. (ADS) Alleghany Corp. (Y) James River Group Holdings (JRVR) Apollo Global Management (APO) BlackRock TCP Capital Corp. (TCPC) Credit Acceptance Corp. (CACC) The Allstate Corp. (ALL) Kemper Corp. (KMPR) The Blackstone Group (BX) Capital Southwest Corp. (CSWC) Elevate Credit (ELVT) AMERISAFE (AMSF) Kinsale Capital Group (KNSL) The Charles Schwab Corp. (SCHW) Hercules Capital (HTGC) Encore Capital Group (ECPG) Arch Capital Group (ACGL) Lemonade (LMND) Cowen Group (COWN) Oaktree Specialty Lending Corp. (OCSL) Enova International (ENVA) Argo Group International Holdings (ARGO) Midwest Holding (MDWT) Envestnet (ENV) Owl Rock Capital Corp. (ORCC) FirstCash (FCFS) AXIS Capital Holdings (AXS) Old Republic International Corp. (ORI) Evercore (EVR) PennantPark Floating Rate Capital (PFLT) International Money Express (IMXI) Chubb (CB) Palomar Holdings (PLMR) Fortress Transportation and Infrastructure Investors (FTAI) PennantPark Investment Corp. (PNNT) MoneyGram International (MGI) Doma Holdings (DOMA) ProAssurance Corp. (PRA) The Goldman Sachs Group (GS) Sixth Street Specialty Lending (TSLX) OneMain Holdings (OMF) Employers Holdings (EIG) RenaissanceRe Holdings (RNR) Greenhill & Co. (GHL) SuRo Capital -

ITEA 2 Project 10014 EASI-CLOUDS
ITEA 2 Project 10014 EASI-CLOUDS - Extended Architecture and Service Infrastructure for Cloud-Aware Software Deliverable D1.5 –Final Business Models for the EASI-CLOUDS Use Cases Task 1.3: Business model(s) for the EASI-CLOUDS eco-system Editors: Atos, Gearshift Group Security public Version 1.0 Main authors Markku Nurmela, Juhana Peltonen, and Florian Röhr (alphabetically) Contributors Jörn Altmann, Maurice Gagnaire, Melanie Jekal, Alexander Krebs, Jan-Frédéric (alphabetically) Plogmeier Pages 99 Deliverable 1.5 – Business Impact v1.0 Abstract The purpose of the business impact work group (WGH) and task 1.5 is to investigate the commercial potential of the EASI-CLOUDS infrastructure, and the federation-based business models that it would help to enable. Our approach described is both ‘top down’ and ‘bottom up’; we begin by summarizing existing studies on the cloud market, and review how the EASI- CLOUDS project partners are positioned on the cloud value chain. We review emerging trends, concepts, business models and value drivers in the cloud market, and present results from a survey targeted at top cloud bloggers and cloud professionals. We then review how the EASI- CLOUDS infrastructure components create value both directly and by facilitating brokerage and federation. We then examine how cloud market opportunities can be grasped through different business models. Specifically, we examine value creation and value capture in different generic business models that may benefit from the EASI-CLOUDS infrastructure. We conclude by providing recommendations on how the different EASI-CLOUDS demonstrators may be commercialized through different business models. © EASI-CLOUDS Consortium. 2 Deliverable 1.5 – Business Impact v1.0 Table of contents Table of contents ........................................................................................................................... -

Digital Ocean the Shopify of Cloud Computing
DigitalOcean (DOCN) – The Shopify of Cloud Computing $200 Price Target Citron – Learning from Our Mistakes One of the greatest blunders we have made over the past 20 years of publishing Citron Research, is not realizing the power of Shopify when the stock was $100. At the time it seemed like another overpriced software company that allowed people to perform the simplest of tasks… making websites. What we failed to recognize and attribute enough value to was that: 1. Customers LOVED the product 2. The Small and Medium Sized Business (SMB) market was a lot larger than we anticipated and could work through its own churn 3. The power of a passionate and dedicated developer network 4. The ease of cross selling once a large customer base was established Congratulations to everyone who owned Shopify through the years. Citron has been waiting patiently for another company to come along with the same profile, hoping with fingers crossed that valuation would be investible… and it has finally come to market. Enter DigitalOcean – The Shopify of Cloud Computing DigitalOcean (DOCN) is a cloud computing platform purpose-built for SMBs (i.e., the Shopify of cloud computing or AWS for SMBs) at a fraction of the cost of large cloud providers. The transformation to the cloud for large enterprises is obviously already on its way. Just look at Amazon with Wall Street analysts estimating the value of AWS at $700-800 billion. The next wave is the SMB transformation to the cloud and multi cloud. We’ve seen this movie before and just like how Shopify and Square saw that SMBs were not far behind large enterprises in adopting ecommerce and digital payments, DigitalOcean is in the leading position to capitalize on this mega trend. -
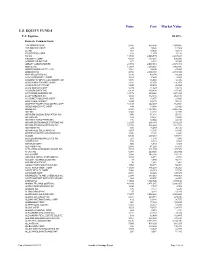
Usef-I Q2 2021
Units Cost Market Value U.S. EQUITY FUND-I U.S. Equities 88.35% Domestic Common Stocks 10X GENOMICS INC 5,585 868,056 1,093,655 1ST SOURCE CORP 249 9,322 11,569 2U INC 301 10,632 12,543 3D SYSTEMS CORP 128 1,079 5,116 3M CO 11,516 2,040,779 2,287,423 A O SMITH CORP 6,897 407,294 496,998 AARON'S CO INC/THE 472 8,022 15,099 ABBOTT LABORATORIES 24,799 2,007,619 2,874,948 ABBVIE INC 17,604 1,588,697 1,982,915 ABERCROMBIE & FITCH CO 1,021 19,690 47,405 ABIOMED INC 9,158 2,800,138 2,858,303 ABM INDUSTRIES INC 1,126 40,076 49,938 ACACIA RESEARCH CORP 1,223 7,498 8,267 ACADEMY SPORTS & OUTDOORS INC 1,036 35,982 42,725 ACADIA HEALTHCARE CO INC 2,181 67,154 136,858 ACADIA REALTY TRUST 1,390 24,572 30,524 ACCO BRANDS CORP 1,709 11,329 14,749 ACI WORLDWIDE INC 6,138 169,838 227,965 ACTIVISION BLIZZARD INC 13,175 839,968 1,257,422 ACUITY BRANDS INC 1,404 132,535 262,590 ACUSHNET HOLDINGS CORP 466 15,677 23,020 ADAPTHEALTH CORP 1,320 39,475 36,181 ADAPTIVE BIOTECHNOLOGIES CORP 18,687 644,897 763,551 ADDUS HOMECARE CORP 148 13,034 12,912 ADOBE INC 5,047 1,447,216 2,955,725 ADT INC 3,049 22,268 32,899 ADTALEM GLOBAL EDUCATION INC 846 31,161 30,151 ADTRAN INC 892 10,257 18,420 ADVANCE AUTO PARTS INC 216 34,544 44,310 ADVANCED DRAINAGE SYSTEMS INC 12,295 298,154 1,433,228 ADVANCED MICRO DEVICES INC 14,280 895,664 1,341,320 ADVANSIX INC 674 15,459 20,126 ADVANTAGE SOLUTIONS INC 1,279 14,497 13,800 ADVERUM BIOTECHNOLOGIES INC 1,840 7,030 6,440 AECOM 5,145 227,453 325,781 AEGLEA BIOTHERAPEUTICS INC 287 1,770 1,998 AEMETIS INC 498 6,023 5,563 AERSALE CORP -

Navigate to Success Via the Continuous Customer™
NAVIGATE TO SUCCESS VIA THE CONTINUOUS CUSTOMER™ A GUIDE TO ACCELERATE THE JOURNEY TO RECURRING REVENUE TABLE OF CONTENTS INTRODUCTION . 3 REAPING THE REWARDS: BENEFITS OF CULTIVATING CONTINUOUS CUSTOMERS™ . 4 ORGANIZATIONAL SYMPTOMS OF A BROKEN RECURRING REVENUE BUSINESS . 5 Customer Churn . 5 Billing Inquiries and Disputes . 5 Definition Confusion . 5 Internal Conflict . 5 Inflexible Operations . 5 Manual Process Overload . 6 Mushrooming Headcount . 6 SKU Proliferation . 6 Unattainable Customer Self-Service . 6 System Customization . 6 Reporting Inaccuracies . 6 STRATEGIC ACCELERATORS TO THE CONTINUOUS CUSTOMER™ . 7 Develop a ‘Services’ Mindset . 7 Center on the Customer Story . 7 Forget the Notion of ‘Back-Office’ . 7 FUNCTIONAL ACCELERATORS TO THE CONTINUOUS CUSTOMER™ . 8 Enable Dynamic Packaging for the Customer Optic . 8 Shift to Atomic Services in the Portfolio .. 9 Close the Innovation Gap between Product and Operational Services . 9 HIDDEN (OR NOT SO HIDDEN) BARRIERS TO THE CONTINUOUS CUSTOMER™ . 10 Siloed Approaches . 10 Internal Politics . 10 Maturity Curve Awareness . 11 Leadership Experience . 12 Fear of Big Projects Prevents Re-Think. 12 Change Management . 12 CONCLUSION . 13 NAVIGATE TO THE CONTINUOUS CUSTOMER™ WITH NAVINT .. 13 WWW.NAVINT.COM | 2 INTRODUCTION The cornerstone of any successful business is the ability to attract and retain customers. This is nothing new. What has changed is the digital nature of the new customer experience The shift is occurring for B2C and B2B businesses across all verticals and the resultant expectations of customers in exchange for their business. Businesses are and market segments: rapidly digitizing their customer experiences and simultaneously transforming their customer relationships to focus on recurring flows of provisioning, consumption, and revenue. -

State of Cloud Native Development Q4-2019
THE LATEST TRENDS FROM OUR Q4 2019 SURVEY OF 17,000+ DEVELOPERS Supported by TO BE PUBLISHED AUGUST 2020 We help the world understand developers We survey 40,000+ developers annually – across web, mobile, IoT, cloud, Machine Learning, AR/VR, games and desktop – to help companies understand who developers are, what they buy and where they are going next. WHO DEVELOPERS ARE WHAT THEY BUY WHERE THEY ARE GOING Developer population sizing Why developers are adopting Emerging platforms – augmented & Developer segmentation competitor products – and how you virtual reality, machine learning can fix that Trusted by the leading tech brands and media TABLE OF CONTENTS Key findings 1. Introduction A. Defining cloud native computing B. Market size C. Usage of cloud native technologies across regions 2. Where are cloud native developers running their code? A. Infrastructure usage by cloud native developers and non-cloud native developers B. Cloud native developers and their infrastructure usage by verticals 3. Usage of cloud service vendors A. Usage of cloud service vendors by cloud native, non-cloud native, and other developers B. Private cloud usage by cloud native and non-cloud native developers 4. Awareness and use of Kubernetes A. Kubernetes and containers: usage and awareness among backend developers B. Overlap of Kubernetes and CaaS users C. Solutions used by developers not indicating they use Kubernetes 5. Serverless usage and awareness A. Usage and awareness of serverless solutions B. Usage of serverless solutions by role Methodology License terms KEY INSIGHTS FOR THE CLOUD NATIVE COMPUTING FOUNDATION THE STATE OF CLOUD NATIVE DEVELOPMENT Q4 2019 4 KEY FINDINGS • 6.5 million cloud native developers exist around the globe, 1.8 million more than in Q2 2019.